How to combine business with pleasure (anonymity and privacy) in an email
In this topic, I would like to give a short summary of how to set up a relatively anonymous and relatively private email correspondence system. Surely most of you will know at least some of the things that are written below, I just tried to "put everything together."
I want to say right away about the word “relative” in the first paragraph: no one can give absolute / protection / reliability / security in this world. You can pick up a keylogger, the police and special services absolutely free and democratic can for quite legitimate reasons insert “bugs” into the computer if you are suspected of serious crimes, etc.
If interested, then I ask for a cat.
1. Configure access to the Tor Network. There are several different packages that use Tor - Tor Browser Bundle, Whonix, Tails, etc. You can argue for a long time which one is better, I chose Whonix .
And here's why: Whonix is implemented as two Virtual Box virtual machines: Gateway, which wraps all traffic in Tor and Workstation, which can talk only with its gateway. This means, firstly, that any program on workstation by default works through Tor (at least in theory), and secondly, if you use javascript in a browser, then in case of a critical vulnerability (like the one that happened a few months ago) only the virtual workstation will be “deanonymized” and the attacker will receive “very valuable” information such as IP 192.168.0.1 and Mac address 02: 00: 01: 01: 01: 01
I repeat, no one gives a 100% guarantee, but still better than nothing.
2. So, we installed Whonix, now a few additional sweets that we will need on the Workstation (hereinafter, unless otherwise specified, Workstation means Virtual Box Whonix Workstation).
- Add the necessary keyboard layout (Zimbabwean, Guatemalan, North Korean, etc.): Start menu button -> Applications -> Settings -> System Settings -> input devices -> layout -> add yours and remove default one -> apply -> Done
- Optional step: Add Guest Addition. This step potentially reduces Whonix's security, but it’s very convenient to copy and paste from the main computer to the virtual machine and vice versa and work on the big screen.
sudo apt-get update && upt-get dist-upgrade
sudo apt-get install --no-install-recommends virtualbox-guest-dkms virtualbox-guest-utils
sudo apt-get install virtualbox-guest-x11
sudo init 6
Workstation restart required , As you can see. Default password: 'changeme' (without quotes)
- Install icedove email client - Thunderbird-a clone
sudo apt-get install icedove
- Install the enigmail extension for icedove
sudo apt-get install enigmail
- Chromium will not hurt (although not necessarily so , just in case)
sudo apt-get install chromium-browser chromium-browser-l10n
- Uncastrated firefox, which is called iceweasel in Whonix, will also not hurt, although, as in the case of Chromium,
sudo apt-get install iceweasel is not necessary
The last two steps do not significantly reduce the level of security, because all traffic is wrapped in Tor through the Whonix gateway. However, use these browsers only when the main Tor Browser for some reason is not good. In principle, the standard Tor Browser included in Whonix should be enough, but if you can’t live without any extension, for example, then Chromium or Iceweasel is at your service, do not forget to add 127.0.0.1:9150 to the iceweasel network settings SOCKS proxy a for Chromium - --proxy-server = "127.0.0.1:9150" in the launch settings (in the terminal or shortcut settings). I still did not understand why this is necessary, it seems that without these settings everything works fine. Well, enable anonymous mode if you do not want to save cookies, history, temp files.
- Register an email account that meets the following conditions:
a. Registration / login via https
b. There is support for SMTP and IMAP / POP3
c. It is desirable that the email address of the sender is not indicated in the email header. Even if the address of the Torah node is indicated there, then you do not need it. I can recommend openmailbox.org for this purpose. At least when I checked the last time, the address was not indicated there.
Remember to only enable JavaScript in Tor Browser-e during registration - otherwise registration is unlikely to succeed. Usually, turning on javaScript is considered a dangerous moment, but in this case, as I already wrote, this does not look like a big problem thanks to the two-level implementation of Whonix-a.
- Create an appropriate account in icedove
- In icedove:
OpenPGP -> Key management -> Generate OpenPGP Key generate a pair of private-public pgp key
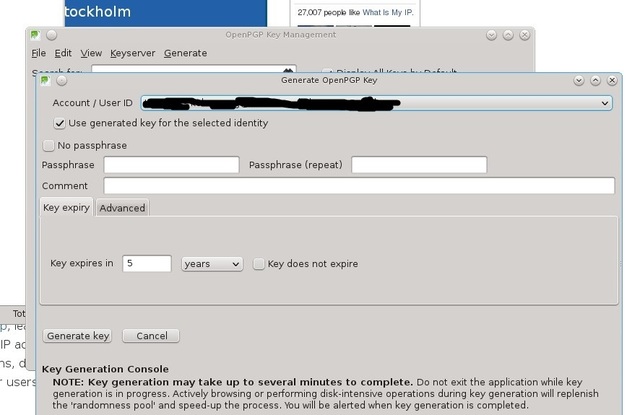
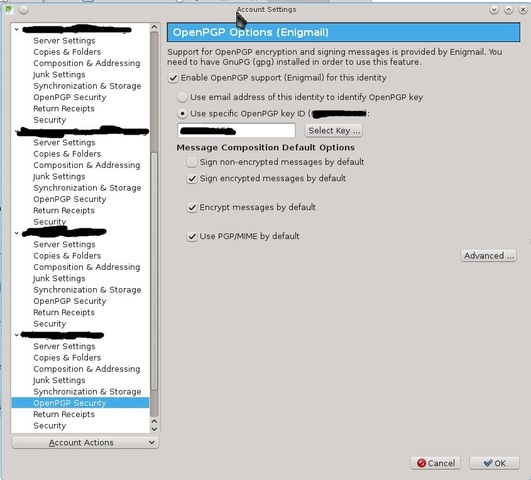
Account Settings -> Open PGP Security: set the key for the account and check the boxes in the right places
Import the public keys of the recipients: OpenPGP -> Key management- -> File -> Import
- Done! Now you can send your beloved girl photos of cats absolutely anonymously and privately - no one except you and your girl will see these cats.
Or, in the framework of the test, you can send me: gpgtest@openmailbox.org
the Public key:
----- the BEGIN of PGP the PUBLIC the KEY BLOCK -----
mQENBFPe01kBCADOsHAro2aaoo / NaTDQLggVtzidXKWVOnBF51WC + DuunOSunvlE
qg0EK5aOJrZYMABpVQpG6uxRW8vV2sUL7kQP78D JpCxFmCk3T5J0y3l8vyK0l + / j
ZYAg7f6YUuL7Tnn7r74dDTPkXz4Ca1xGZOzaPWfY / v / weHzUoLTCD26Rxu + 8u / pI of
3BZPnrDBYzZso5RdNC65wvTg4dc0By9ujDlb76fpfs9zUEs5gaVHYRRIMu / deHwU
Piu9DYkdQEzhH80 / hSocBYqIrsESck4TFzLpvqH9QfOSaFhVgIkzHORA + 6H68pOX
Y8FAhlHC7C7pQo3RO3zBlD3 + c0L0P1EREMajABEBAAG0IkdwZyBUZXN0IDxncGd0
ZXN0QG9wZW5tYWlsYm94Lm9yZz6JAT0EEwEKACcFAlPe01kCGyMFCQlmAYAFCwkI
BwMFFQoJCAsFFgIDAQACHgECF4AACgkQ1a0RRffjWoYO8wgAhO4CQUesD7EoCvPw
LTPY9Mc3p0zjrxcC8nJiqEdqA6vMRadqyQuExlfSZ3duiT9qCIXndb2bxwiC4F6q
SvrYuW1H5n2dtHmwNurgHPlAZVkLxRuYBInQU9x3wh2uBtSCeLHJlKFtixsKb the ZC +
wGepu9Rev7xFFby5mfJ / gV7nPSHN8hvubdO88TezINN0mqxOzRYusE3vG1seOh78
bYiDLvWp6jSdrmD8Yvd75nBtt8EOHqP3IQ9 / y9k8CA5ujzX59qh5vcA7Al7xaSmp
xTze / YEBfPBUyshKCs9V5cacvfAfk0KzoD9NO / yUVrTvxtEal7wBTWvfzQRQWJpc
yz / H37kBDQRT3tNZAQgA5e40XSpCU2iJpKv0ei / xVrJO / Bs6D7x08tjIFrOLcHJT
wLB3BiNnQVd5ZYUsIP4yBFUhx526XutXdL3Ic5aUFlDCboQ9m9s0IqNOQ0KCzsx5
Sdt3oixySw98sxoamu2 + 4pcYt86CoINafzVnhZfstMkb9CFUHfuJPhr / hrC9raMO
7V0JWmQQ3xXLYV1 + yxbiEUHY / 8OADWDFShQpEwdLqpTOnTail3ThzQ / a3wNiy833
ryZnra / LWfb0wSGFb0nXH5HdclUt0BWcF + aoFxlVgc0i8PQrL3VBZWx9OsvXx3eV
wWkoNN4WwdNheBbHknJXpC4L843B / NZ + dVgWmfM3FQARAQABiQElBBgBCgAPBQJT
3tNZAhsMBQkJZgGAAAoJENWtEUX341qG9PwH / 3LdIhK20NB5qiVVmtfKU8GLYEbT
x4diZIPYqqvululueWhQwwwoT + hNiNGfAIaGBjkz0 / cDNT9sZDraXkEkOlv73tG4
3P / bl4bmi0HOEG0yQtQxRfJy7bcdi5rpdzFQHWqjPKa8puA6U1MZ7q3h4DF9zBjn
ua9IwGMk2HhE / 7anupL12EGV2p3k4ZfwNzFljzdpg5 + QBG9ke16Coz81KBf4BD + c
iNf95DWj4MnghiTqLwXMmLkDSoOaCZUnqgO + 5ohYIYuvHt6ETsb0n9GfvyHYpd + t
ILjNnuwcEM0lFCa7uTxubW8 / vzVZbY2SmT68EzN7K / 5bwBZZNOpEZvTNLhw =
= eyg /
----- END PGP PUBLIC KEY BLOCK -----
I want to say right away about the word “relative” in the first paragraph: no one can give absolute / protection / reliability / security in this world. You can pick up a keylogger, the police and special services absolutely free and democratic can for quite legitimate reasons insert “bugs” into the computer if you are suspected of serious crimes, etc.
If interested, then I ask for a cat.
1. Configure access to the Tor Network. There are several different packages that use Tor - Tor Browser Bundle, Whonix, Tails, etc. You can argue for a long time which one is better, I chose Whonix .
And here's why: Whonix is implemented as two Virtual Box virtual machines: Gateway, which wraps all traffic in Tor and Workstation, which can talk only with its gateway. This means, firstly, that any program on workstation by default works through Tor (at least in theory), and secondly, if you use javascript in a browser, then in case of a critical vulnerability (like the one that happened a few months ago) only the virtual workstation will be “deanonymized” and the attacker will receive “very valuable” information such as IP 192.168.0.1 and Mac address 02: 00: 01: 01: 01: 01
I repeat, no one gives a 100% guarantee, but still better than nothing.
2. So, we installed Whonix, now a few additional sweets that we will need on the Workstation (hereinafter, unless otherwise specified, Workstation means Virtual Box Whonix Workstation).
- Add the necessary keyboard layout (Zimbabwean, Guatemalan, North Korean, etc.): Start menu button -> Applications -> Settings -> System Settings -> input devices -> layout -> add yours and remove default one -> apply -> Done
- Optional step: Add Guest Addition. This step potentially reduces Whonix's security, but it’s very convenient to copy and paste from the main computer to the virtual machine and vice versa and work on the big screen.
sudo apt-get update && upt-get dist-upgrade
sudo apt-get install --no-install-recommends virtualbox-guest-dkms virtualbox-guest-utils
sudo apt-get install virtualbox-guest-x11
sudo init 6
Workstation restart required , As you can see. Default password: 'changeme' (without quotes)
- Install icedove email client - Thunderbird-a clone
sudo apt-get install icedove
- Install the enigmail extension for icedove
sudo apt-get install enigmail
- Chromium will not hurt (although not necessarily so , just in case)
sudo apt-get install chromium-browser chromium-browser-l10n
- Uncastrated firefox, which is called iceweasel in Whonix, will also not hurt, although, as in the case of Chromium,
sudo apt-get install iceweasel is not necessary
The last two steps do not significantly reduce the level of security, because all traffic is wrapped in Tor through the Whonix gateway. However, use these browsers only when the main Tor Browser for some reason is not good. In principle, the standard Tor Browser included in Whonix should be enough, but if you can’t live without any extension, for example, then Chromium or Iceweasel is at your service, do not forget to add 127.0.0.1:9150 to the iceweasel network settings SOCKS proxy a for Chromium - --proxy-server = "127.0.0.1:9150" in the launch settings (in the terminal or shortcut settings). I still did not understand why this is necessary, it seems that without these settings everything works fine. Well, enable anonymous mode if you do not want to save cookies, history, temp files.
- Register an email account that meets the following conditions:
a. Registration / login via https
b. There is support for SMTP and IMAP / POP3
c. It is desirable that the email address of the sender is not indicated in the email header. Even if the address of the Torah node is indicated there, then you do not need it. I can recommend openmailbox.org for this purpose. At least when I checked the last time, the address was not indicated there.
Remember to only enable JavaScript in Tor Browser-e during registration - otherwise registration is unlikely to succeed. Usually, turning on javaScript is considered a dangerous moment, but in this case, as I already wrote, this does not look like a big problem thanks to the two-level implementation of Whonix-a.
- Create an appropriate account in icedove
- In icedove:
OpenPGP -> Key management -> Generate OpenPGP Key generate a pair of private-public pgp key

Account Settings -> Open PGP Security: set the key for the account and check the boxes in the right places

Import the public keys of the recipients: OpenPGP -> Key management- -> File -> Import
- Done! Now you can send your beloved girl photos of cats absolutely anonymously and privately - no one except you and your girl will see these cats.
Or, in the framework of the test, you can send me: gpgtest@openmailbox.org
the Public key:
----- the BEGIN of PGP the PUBLIC the KEY BLOCK -----
mQENBFPe01kBCADOsHAro2aaoo / NaTDQLggVtzidXKWVOnBF51WC + DuunOSunvlE
qg0EK5aOJrZYMABpVQpG6uxRW8vV2sUL7kQP78D JpCxFmCk3T5J0y3l8vyK0l + / j
ZYAg7f6YUuL7Tnn7r74dDTPkXz4Ca1xGZOzaPWfY / v / weHzUoLTCD26Rxu + 8u / pI of
3BZPnrDBYzZso5RdNC65wvTg4dc0By9ujDlb76fpfs9zUEs5gaVHYRRIMu / deHwU
Piu9DYkdQEzhH80 / hSocBYqIrsESck4TFzLpvqH9QfOSaFhVgIkzHORA + 6H68pOX
Y8FAhlHC7C7pQo3RO3zBlD3 + c0L0P1EREMajABEBAAG0IkdwZyBUZXN0IDxncGd0
ZXN0QG9wZW5tYWlsYm94Lm9yZz6JAT0EEwEKACcFAlPe01kCGyMFCQlmAYAFCwkI
BwMFFQoJCAsFFgIDAQACHgECF4AACgkQ1a0RRffjWoYO8wgAhO4CQUesD7EoCvPw
LTPY9Mc3p0zjrxcC8nJiqEdqA6vMRadqyQuExlfSZ3duiT9qCIXndb2bxwiC4F6q
SvrYuW1H5n2dtHmwNurgHPlAZVkLxRuYBInQU9x3wh2uBtSCeLHJlKFtixsKb the ZC +
wGepu9Rev7xFFby5mfJ / gV7nPSHN8hvubdO88TezINN0mqxOzRYusE3vG1seOh78
bYiDLvWp6jSdrmD8Yvd75nBtt8EOHqP3IQ9 / y9k8CA5ujzX59qh5vcA7Al7xaSmp
xTze / YEBfPBUyshKCs9V5cacvfAfk0KzoD9NO / yUVrTvxtEal7wBTWvfzQRQWJpc
yz / H37kBDQRT3tNZAQgA5e40XSpCU2iJpKv0ei / xVrJO / Bs6D7x08tjIFrOLcHJT
wLB3BiNnQVd5ZYUsIP4yBFUhx526XutXdL3Ic5aUFlDCboQ9m9s0IqNOQ0KCzsx5
Sdt3oixySw98sxoamu2 + 4pcYt86CoINafzVnhZfstMkb9CFUHfuJPhr / hrC9raMO
7V0JWmQQ3xXLYV1 + yxbiEUHY / 8OADWDFShQpEwdLqpTOnTail3ThzQ / a3wNiy833
ryZnra / LWfb0wSGFb0nXH5HdclUt0BWcF + aoFxlVgc0i8PQrL3VBZWx9OsvXx3eV
wWkoNN4WwdNheBbHknJXpC4L843B / NZ + dVgWmfM3FQARAQABiQElBBgBCgAPBQJT
3tNZAhsMBQkJZgGAAAoJENWtEUX341qG9PwH / 3LdIhK20NB5qiVVmtfKU8GLYEbT
x4diZIPYqqvululueWhQwwwoT + hNiNGfAIaGBjkz0 / cDNT9sZDraXkEkOlv73tG4
3P / bl4bmi0HOEG0yQtQxRfJy7bcdi5rpdzFQHWqjPKa8puA6U1MZ7q3h4DF9zBjn
ua9IwGMk2HhE / 7anupL12EGV2p3k4ZfwNzFljzdpg5 + QBG9ke16Coz81KBf4BD + c
iNf95DWj4MnghiTqLwXMmLkDSoOaCZUnqgO + 5ohYIYuvHt6ETsb0n9GfvyHYpd + t
ILjNnuwcEM0lFCa7uTxubW8 / vzVZbY2SmT68EzN7K / 5bwBZZNOpEZvTNLhw =
= eyg /
----- END PGP PUBLIC KEY BLOCK -----
