Microsoft and Adobe Released Update Set, May 2014
The company has released a series of updates for its products that fix 13 unique vulnerabilities in Windows, Internet Explorer, .NET Framework, Office, and SharePoint products. Two fixes are Critical and six are Important. The critical update MS14-029 fixes two memory-corruption vulnerabilities in all versions of Internet Explorer 6-11 on all operating systems from Windows Server 2003 to Windows 8 / 8.1. Attackers can execute remote code in a browser through a specially formed web page (drive-by downloads). To apply the hotfix, a reboot is required.

Note that a week ago, Microsoft released an unscheduled update KB2962140 for Windows 8.1 & RT 8.1, which closes the vulnerability Heartbleed(CVE-2014-0160) in the Juniper Networks Junos Pulse VPN Client component. This VPN client is supplied by a third-party company and is used by Microsoft as part of the latest OS. This update, like all other security fixes for Windows 8.1, can be installed on the system only with the mandatory update KB2919355 .
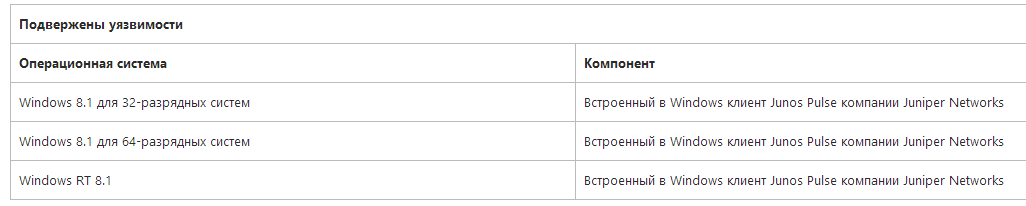
Fig. OS to be fixed with Heartbleed using KB2962140. See 2014-04 Out of Cycle Security Bulletin: Multiple products affected by OpenSSL "Heartbleed" issue (CVE-2014-0160) .
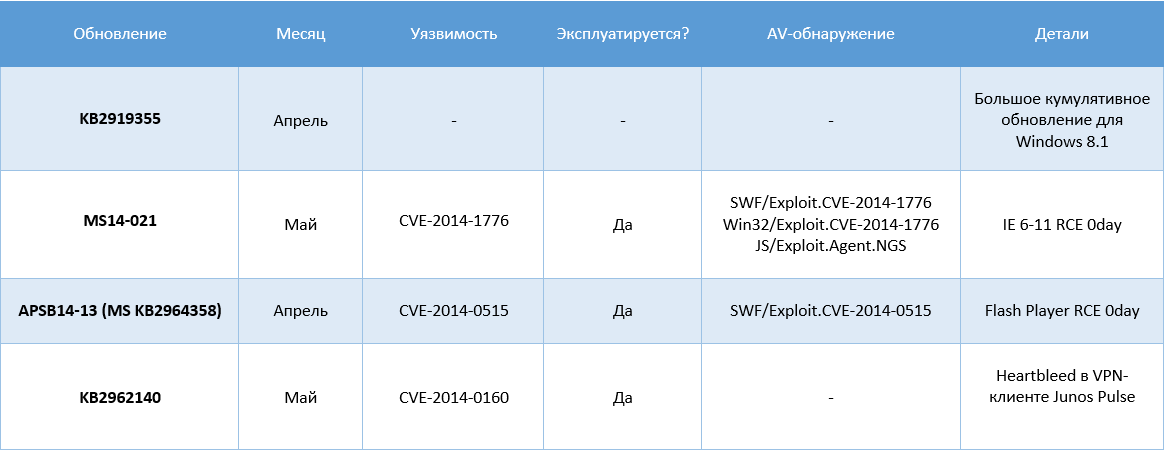
In early May, the company released another unscheduled security update MS14-021for all operating systems, starting with Windows XP (no longer supported) and ending with Windows 8 / 8.1. We wrote more about him here . The update closes the 0day vulnerability CVE-2014-1776 (in mshtml.dll and some other files), which is present in all versions of Internet Explorer and was used by attackers in targeted attacks to install malicious code.
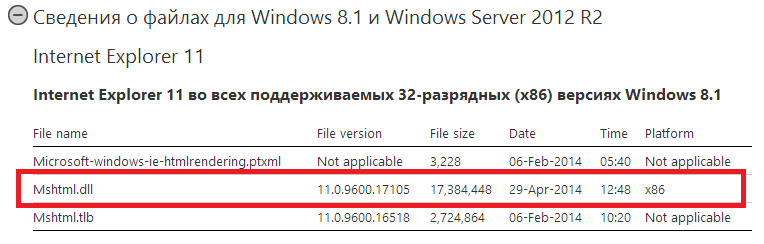
Fig. Files corrected by the MS14-021 update for the latest Windows 8.1 & IE11, see KB2964358 " File Information" Section.
Update MS14-029closes two vulnerabilities in all versions of Internet Explorer: CVE-2014-0310 and CVE-2014-1815. Both vulnerabilities are of the Remote Code Execution type and can be used by attackers to remotely execute arbitrary code in the system. Vulnerability CVE-2014-1815 is exploited by cybercriminals . Critical.
The MS14-022 update fixes three vulnerabilities in a SharePoint Server 2007-2010-2013 product: CVE-2014-0251 (SharePoint Page Content Vulnerability), CVE-2014-1754 (SharePoint XSS Vulnerability), CVE-2014-1813 (Web Applications Page Content Vulnerability). Using these vulnerabilities, an attacker could execute arbitrary code by sending specially crafted content to a server with SharePoint. Critical. Exploit code likely.
The MS14-023 update fixes two vulnerabilities in Office 2007-2010. The CVE-2014-1756 RCE vulnerability is present in the Office 2007-2010 Chinese Language Check component (Chinese Grammar Checker). Another CVE-2014-1808 vulnerability is of type Information Disclosure and is present in some versions of Microsoft Office 2013 (MSO). Important Exploit code likely .
Update MS14-024Corrects a defect in the "Security Feature Bypass" type for Office. We already wrote earlier that attackers use Office libraries compiled without ASLR support to implement exploits. This update corrects the situation through the release of secure versions (with ASLR support) of the mscomct2, mscomctl (CVE-2014-1809), msaddndr, msstdfmt libraries for Office 2007-2010-2013. Important It is operated in-the-wild .
The MS14-025 update fixes one CVE-2014-1812 vulnerability like Elevation of Privilege for Windows Vista SP2 - Windows 8 / 8.1 (client versions with Remote Server Administration Tools). The vulnerability is present in the Active Directory Group Policy component. Important Exploit code likely .
Update MS14-026fixes one Elevation of Privilege vulnerability CVE-2014-1806 in all versions of the .NET Framework for all OS. An attacker can elevate his privileges on the system by sending a specially crafted request to a home computer or server that uses .NET Remoting . Important Exploit code likely .
The MS14-027 update fixes one Elevation of Privilege vulnerability CVE-2014-1807 for all supported OS. The vulnerability is present in the mechanism of file associations (Windows Shell File Associations), and more specifically in the Windows Shell API and its ShellExecute function . An attacker can elevate his system privileges using a special application that calls the ShellExecute functionin a special way. Important Exploit code likely .
The MS14-028 update fixes two vulnerabilities CVE-2014-0255, CVE-2014-0256 in server editions of Windows Server 2008 & 2012. The vulnerabilities are of the Denial of Service type and can be used by attackers to provoke the target system to freeze by sending a large number of specially crafted iSCSI packets. Important Exploit code unlikely .
Unscheduled updates to
EMET 5.0 TP & Attack Surface Reduction
Speaking of EMET and CVE-2014-1776, which made a lot of noise last month, it can be noted that EMET 5.0 TP (and TP2) users are protected by default from exploit actions to this vulnerability. In our recent postdedicated to the ASR (Attack Surface Reduction) option in this version of EMET, we indicated that the option blocks the download of VGX.DLL for Internet Explorer (the very library that MS recommended manually disconnecting before MS14-021 as workaround - SA2963983 ). Vulnerability is not contained in VGX.DLL, however, its disabling helped prevent the exploit from performing its functions.

Fig. Mitigating factors for exploiting the vulnerability, for example, CVE-2014-1776. EMET 5.0 EAF + blocks access to the page with ntdll.dll exports from ActionScript code, this feature is not available in EAF (allows access to the page with exports to the ocx module code). See here for more details .
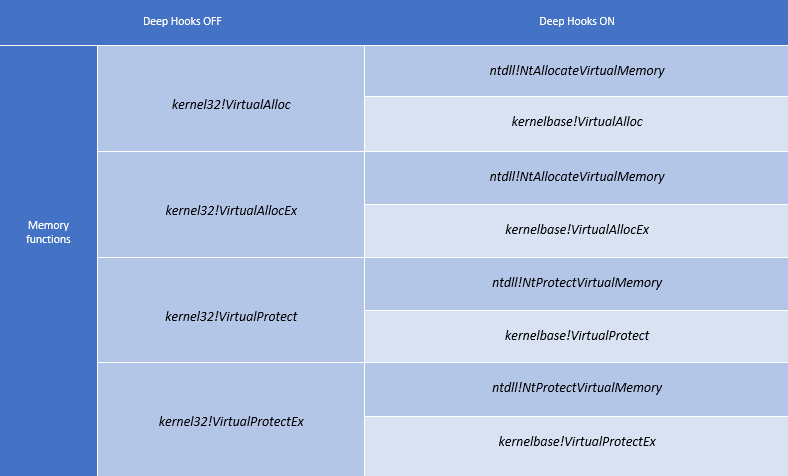
Fig. EMET uses the Deep Hooks option to control underlying kernel32.dll libraries (using memory functions as an example). APIs are controlled to block their call from ROP code. With this option enabled, calls to kernel32, kernelbase, and ntdll are controlled. Actual for CVE-2014-1776.
1 - Exploit code likely The
probability of exploiting the vulnerability is very high, attackers can use the exploit, for example, to remotely execute code.
2 - Exploit code would be difficult to build The
likelihood of exploitation is medium, since attackers are unlikely to be able to achieve a sustainable exploitation situation, as well as due to the technical features of the vulnerability and complexity of the exploit development.
3 - Exploit code unlikely
The probability of exploitation is minimal and attackers are unlikely to be able to develop successfully working code and use this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).
Adobe also released APSB14-15for their Reader and Acrobat products. In total, 11 vulnerabilities were fixed in them. Nine of the eleven vulnerabilities are of the Remote Code Execution type and can be used by attackers to execute their code in the system: CVE-2014-0511, CVE-2014-0522, CVE-2014-0523, CVE-2014-0524, CVE-2014- 0526, CVE-2014-0525, CVE-2014-0527, CVE-2014-0528, CVE-2014-0529.
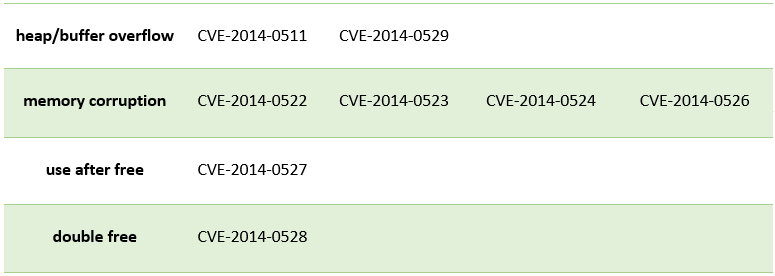
Fig. RCE vulnerabilities fixed by APSB14-15.

Fig. Current versions of Adobe Reader & Acrobat.
Vulnerabilities CVE-2014-0511 and CVE-2014-0512 were discovered by the VUPEN team at Pwn2Own 2014 .
Users can update the specified products through the built-in mechanism for checking for updates (Adobe Updater).

be secure.

Note that a week ago, Microsoft released an unscheduled update KB2962140 for Windows 8.1 & RT 8.1, which closes the vulnerability Heartbleed(CVE-2014-0160) in the Juniper Networks Junos Pulse VPN Client component. This VPN client is supplied by a third-party company and is used by Microsoft as part of the latest OS. This update, like all other security fixes for Windows 8.1, can be installed on the system only with the mandatory update KB2919355 .

Fig. OS to be fixed with Heartbleed using KB2962140. See 2014-04 Out of Cycle Security Bulletin: Multiple products affected by OpenSSL "Heartbleed" issue (CVE-2014-0160) .
In early May, the company released another unscheduled security update MS14-021for all operating systems, starting with Windows XP (no longer supported) and ending with Windows 8 / 8.1. We wrote more about him here . The update closes the 0day vulnerability CVE-2014-1776 (in mshtml.dll and some other files), which is present in all versions of Internet Explorer and was used by attackers in targeted attacks to install malicious code.

Fig. Files corrected by the MS14-021 update for the latest Windows 8.1 & IE11, see KB2964358 " File Information" Section.
Update MS14-029closes two vulnerabilities in all versions of Internet Explorer: CVE-2014-0310 and CVE-2014-1815. Both vulnerabilities are of the Remote Code Execution type and can be used by attackers to remotely execute arbitrary code in the system. Vulnerability CVE-2014-1815 is exploited by cybercriminals . Critical.
The MS14-022 update fixes three vulnerabilities in a SharePoint Server 2007-2010-2013 product: CVE-2014-0251 (SharePoint Page Content Vulnerability), CVE-2014-1754 (SharePoint XSS Vulnerability), CVE-2014-1813 (Web Applications Page Content Vulnerability). Using these vulnerabilities, an attacker could execute arbitrary code by sending specially crafted content to a server with SharePoint. Critical. Exploit code likely.
The MS14-023 update fixes two vulnerabilities in Office 2007-2010. The CVE-2014-1756 RCE vulnerability is present in the Office 2007-2010 Chinese Language Check component (Chinese Grammar Checker). Another CVE-2014-1808 vulnerability is of type Information Disclosure and is present in some versions of Microsoft Office 2013 (MSO). Important Exploit code likely .
Update MS14-024Corrects a defect in the "Security Feature Bypass" type for Office. We already wrote earlier that attackers use Office libraries compiled without ASLR support to implement exploits. This update corrects the situation through the release of secure versions (with ASLR support) of the mscomct2, mscomctl (CVE-2014-1809), msaddndr, msstdfmt libraries for Office 2007-2010-2013. Important It is operated in-the-wild .
The MS14-025 update fixes one CVE-2014-1812 vulnerability like Elevation of Privilege for Windows Vista SP2 - Windows 8 / 8.1 (client versions with Remote Server Administration Tools). The vulnerability is present in the Active Directory Group Policy component. Important Exploit code likely .
Update MS14-026fixes one Elevation of Privilege vulnerability CVE-2014-1806 in all versions of the .NET Framework for all OS. An attacker can elevate his privileges on the system by sending a specially crafted request to a home computer or server that uses .NET Remoting . Important Exploit code likely .
The MS14-027 update fixes one Elevation of Privilege vulnerability CVE-2014-1807 for all supported OS. The vulnerability is present in the mechanism of file associations (Windows Shell File Associations), and more specifically in the Windows Shell API and its ShellExecute function . An attacker can elevate his system privileges using a special application that calls the ShellExecute functionin a special way. Important Exploit code likely .
The MS14-028 update fixes two vulnerabilities CVE-2014-0255, CVE-2014-0256 in server editions of Windows Server 2008 & 2012. The vulnerabilities are of the Denial of Service type and can be used by attackers to provoke the target system to freeze by sending a large number of specially crafted iSCSI packets. Important Exploit code unlikely .
Unscheduled updates to

EMET 5.0 TP & Attack Surface Reduction
Speaking of EMET and CVE-2014-1776, which made a lot of noise last month, it can be noted that EMET 5.0 TP (and TP2) users are protected by default from exploit actions to this vulnerability. In our recent postdedicated to the ASR (Attack Surface Reduction) option in this version of EMET, we indicated that the option blocks the download of VGX.DLL for Internet Explorer (the very library that MS recommended manually disconnecting before MS14-021 as workaround - SA2963983 ). Vulnerability is not contained in VGX.DLL, however, its disabling helped prevent the exploit from performing its functions.

Fig. Mitigating factors for exploiting the vulnerability, for example, CVE-2014-1776. EMET 5.0 EAF + blocks access to the page with ntdll.dll exports from ActionScript code, this feature is not available in EAF (allows access to the page with exports to the ocx module code). See here for more details .

Fig. EMET uses the Deep Hooks option to control underlying kernel32.dll libraries (using memory functions as an example). APIs are controlled to block their call from ROP code. With this option enabled, calls to kernel32, kernelbase, and ntdll are controlled. Actual for CVE-2014-1776.
1 - Exploit code likely The
probability of exploiting the vulnerability is very high, attackers can use the exploit, for example, to remotely execute code.
2 - Exploit code would be difficult to build The
likelihood of exploitation is medium, since attackers are unlikely to be able to achieve a sustainable exploitation situation, as well as due to the technical features of the vulnerability and complexity of the exploit development.
3 - Exploit code unlikely
The probability of exploitation is minimal and attackers are unlikely to be able to develop successfully working code and use this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

Adobe also released APSB14-15for their Reader and Acrobat products. In total, 11 vulnerabilities were fixed in them. Nine of the eleven vulnerabilities are of the Remote Code Execution type and can be used by attackers to execute their code in the system: CVE-2014-0511, CVE-2014-0522, CVE-2014-0523, CVE-2014-0524, CVE-2014- 0526, CVE-2014-0525, CVE-2014-0527, CVE-2014-0528, CVE-2014-0529.

Fig. RCE vulnerabilities fixed by APSB14-15.

Fig. Current versions of Adobe Reader & Acrobat.
Vulnerabilities CVE-2014-0511 and CVE-2014-0512 were discovered by the VUPEN team at Pwn2Own 2014 .
Users can update the specified products through the built-in mechanism for checking for updates (Adobe Updater).

be secure.
