Principles for the successful implementation of IDM. Business cases
The market for information security systems, namely IDM solutions, is growing at a tremendous pace according to the latest trends in the West. This trend has been observed, in the last few years, in the countries of Eastern Europe and Russia. Today, IDM solutions are in demand by both large and medium-sized businesses.

There are both western and domestic vendors on the Russian IDM market. The most common IDM systems today are Oracle Identity Manager, IBM Security Identity Manager, Microsoft Forefront Identity Manager, CMS, Avanpost. They have a lot in common, but there are also functional features and when choosing a solution, the customer undoubtedly needs to get acquainted with each of them in order to understand which of the systems most fully meets his requirements. What is IDM? This is an account management system. Typically, IDM has two ways of providing access: based on personnel changes (job access) and through the self-service web portal (individual access). The entities that IDM manages are accounts. IDM creates accounts and manages preset group memberships.
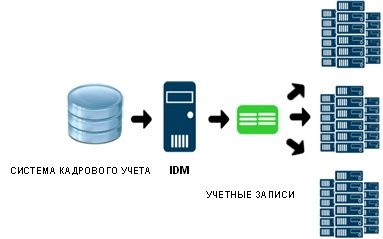
All existing IDM systems have much wider functionality, and some of them allow you to manage “granular rights”, configure standard access (create groups and associate them with resources) and even create new resources.
Until recently, the use of IDM by Russian companies was the prerogative of industry giants, representative offices of Western companies and major banks. These are companies with a staff of several thousand people, a huge "zoo" of information systems, many of which are created specifically for these companies and are not used anywhere else, and with a budget measured in tens or even hundreds of millions. Why?
The fact is that most IDM solutions in the Russian market are represented by market leaders, trendsetters, such as Oracle, IBM, Microsoft.
These solutions are designers, they have the ability to customize for any business processes. In fact, western IDMs are platforms. But the cost of licenses for these systems is quite high, and implementation can take years. At the same time, if the customer’s business processes are changing, then the solution needs to be practically rewritten again.
Recently, the market situation is changing. Companies of over 200-500 people are willing to reduce the risks of illegitimate access to their information resources and use IDM systems to automate the processes of providing and controlling access. What has changed?
But the IDM market in Russia still does not have the same volume as in the West (in the USA, 4 out of 5 companies over 1000 people use IDM solutions). What needs to be done in order for an IDM class product to be successful in Russia?
TrustVers is a domestic developer of IDM solutions successfully implemented both in large organizations and in companies with a staff of up to 1000 people. We have formed several theses, which, in our opinion, can be the key to the successful implementation of IDM in a Russian company.
1. An IDM implementation project should last, on average, 3 months. This can be achieved in several ways:
2. IDM should work in conjunction with other systems that ensure the information security of the company. It is rare for which companies to start using IDM from scratch. In the vast majority of cases, the company already uses one of the systems of the class ITSM, SIEM, SSO, PKI, ACS. Let's take a closer look at how you can use the Identity Management class system in conjunction with related solutions.
3. IDM solution should be profitable to use. Unfortunately, due to overstated expectations, the lack of corporate ethics of using application creation rules, the inexperience of an integrator, the project to implement an IDM solution does not always bring the expected effects to the company. How to achieve the maximum effect from the implementation of IDM?
The acquisition of an IDM solution is a crucial step for the successful implementation and subsequent operation of the system, it is necessary to carefully understand the functional features of various IDMs, select an experienced integrator and conduct training for specialists. The decision on implementation should be taken collectively, with the participation of business, IT and NIS staff.
Alexey Pavlov, Presale Manager
TrustWers LLC
http://trustverse.ru

There are both western and domestic vendors on the Russian IDM market. The most common IDM systems today are Oracle Identity Manager, IBM Security Identity Manager, Microsoft Forefront Identity Manager, CMS, Avanpost. They have a lot in common, but there are also functional features and when choosing a solution, the customer undoubtedly needs to get acquainted with each of them in order to understand which of the systems most fully meets his requirements. What is IDM? This is an account management system. Typically, IDM has two ways of providing access: based on personnel changes (job access) and through the self-service web portal (individual access). The entities that IDM manages are accounts. IDM creates accounts and manages preset group memberships.

All existing IDM systems have much wider functionality, and some of them allow you to manage “granular rights”, configure standard access (create groups and associate them with resources) and even create new resources.
Until recently, the use of IDM by Russian companies was the prerogative of industry giants, representative offices of Western companies and major banks. These are companies with a staff of several thousand people, a huge "zoo" of information systems, many of which are created specifically for these companies and are not used anywhere else, and with a budget measured in tens or even hundreds of millions. Why?
The fact is that most IDM solutions in the Russian market are represented by market leaders, trendsetters, such as Oracle, IBM, Microsoft.
These solutions are designers, they have the ability to customize for any business processes. In fact, western IDMs are platforms. But the cost of licenses for these systems is quite high, and implementation can take years. At the same time, if the customer’s business processes are changing, then the solution needs to be practically rewritten again.
Recently, the market situation is changing. Companies of over 200-500 people are willing to reduce the risks of illegitimate access to their information resources and use IDM systems to automate the processes of providing and controlling access. What has changed?
- The competence of integrators has grown, which formed “standard” replicable solutions, increased the competence of their engineers, which led to lower project costs.
- Western companies from the Big Three have changed their pricing policy, offering significant discounts, reaching up to 70% of the initial cost. This is caused, inter alia, by the appearance of competitors of domestic vendors with significantly more advantageous offers.
- The complexity and quantity of information systems used and the qualifications of employees of Russian companies are increasing.
But the IDM market in Russia still does not have the same volume as in the West (in the USA, 4 out of 5 companies over 1000 people use IDM solutions). What needs to be done in order for an IDM class product to be successful in Russia?
TrustVers is a domestic developer of IDM solutions successfully implemented both in large organizations and in companies with a staff of up to 1000 people. We have formed several theses, which, in our opinion, can be the key to the successful implementation of IDM in a Russian company.
1. An IDM implementation project should last, on average, 3 months. This can be achieved in several ways:
- Connectors to target systems should work out of the box. Any integrator who has implemented Oracle will tell you that most of the connectors are “finished” at the implementation stage and their replication is conditional, which leads to an increase in the time and cost of implementation.
- The system should be tuned, not programmed, that is, there should be an interface for tuning the system core. This reduces the flexibility of the system, but allows you to configure it much faster. Need a balance.
- It is desirable to have an analytic module in the IDM system that creates and optimizes the role model based on the current state of information systems and the current IS policy. The principle of inventory optimization operation. This will allow you to integrate the stage of mandatory pre-project analytics into the system implementation process, which will significantly reduce time costs and automate the process.
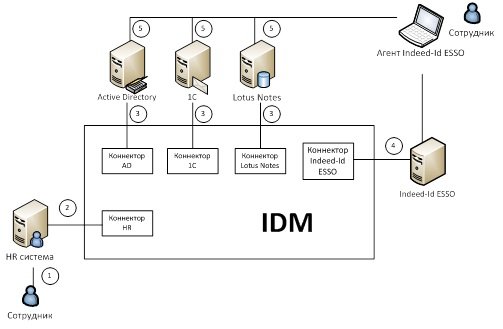
2. IDM should work in conjunction with other systems that ensure the information security of the company. It is rare for which companies to start using IDM from scratch. In the vast majority of cases, the company already uses one of the systems of the class ITSM, SIEM, SSO, PKI, ACS. Let's take a closer look at how you can use the Identity Management class system in conjunction with related solutions.
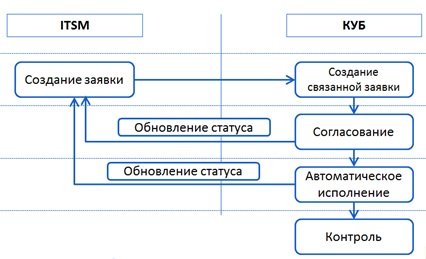
- Integration with ITSM is interesting, as with a “single entry point”. Employees of the organization create applications in the service desk and, if it is an application for providing access, it is automatically transmitted to IDM, where it is agreed, executed (also automatically) and subsequently monitored.

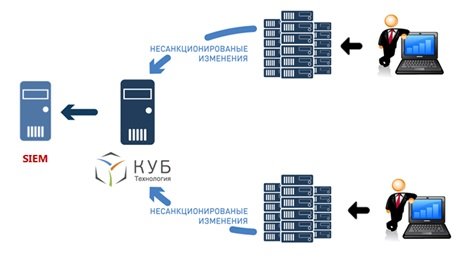
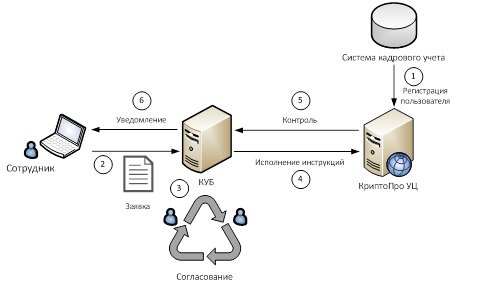
- Integration of KUB with SIEM is organized according to the following scheme: IDM KUB monitors target systems for changes in security settings (changing access rights, creating, deleting accounts, new resources) and compares them with the requirements of applications. In the event that changes occurred directly in the target system, bypassing the application mechanism, IDM notifies the responsible person of the non-compliance, and also sends a report to SIEM. The advantage of this integration is that SIEM does not distinguish between events that occurred bypassing the application system from those agreed upon, therefore the IS officer receives a “heap” of changes that are difficult to understand.

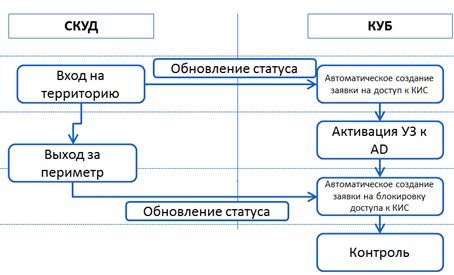
- Integration with ACS. How often do you encounter a situation where company employees use other people's data to work in the system? How acceptable is this situation? Each of you can answer this question independently, but, in most cases, they try to fight this problem. The joint use of IDM and ACS will allow you to control user access to the target system, including the domain. Until a person passes the control system, does not enter the ACS perimeter, the AD account is blocked, as soon as the employee comes to work, he has the opportunity to log in to the domain. Of course, there are many restrictions, including those with loss of a pass and remote access, but this can also be realized through IDM (for example, through an application drawn up by the head of an employee who has forgotten a card).

- Manage PKI infrastructure using IDM. The most popular scenario is the automatic issuance and revocation of a certificate when accepting / dismissing an employee. But IDM can issue a certificate upon request, for example, when an employee has requested access to a system that requires a security certificate. PKI-IDM can significantly reduce the load on NIB and IT in terms of certificate management, their automatic issuance and revocation, as well as transportation. The second, no less demanded functional is the use of ES at the stage of creation and approval of an application, including the use of qualified ES (e.g. crypto pro).

- The SSO . When a new employee comes to work, on the basis of data in the personnel system IDM gives him privileges based on the position, generates a one-time password.
When you first access your computer, the user specifies the domain account name and password. After a successful login, the user can configure for subsequent use alternative authenticators (smart card, token, one-time password generators, biometric authentication tools, etc.). At CUB, this procedure is performed using Indeed-Id Enterprise SSO Agent funds. The full range of authenticators available for use is determined by the Indeed-Id Enterprise SSO settings. After all the necessary settings are completed, the user can use the selected authenticators to access the domain and all applications. There is no need to remember passwords for IP.

3. IDM solution should be profitable to use. Unfortunately, due to overstated expectations, the lack of corporate ethics of using application creation rules, the inexperience of an integrator, the project to implement an IDM solution does not always bring the expected effects to the company. How to achieve the maximum effect from the implementation of IDM?
- One of the most important factors is usability for business units. The access matrix and the structure of roles should be understandable, they should be searched for according to several criteria, it is necessary to be able to adjust the application by coordinators. At the same time, the very process of requesting roles must be minimized by setting job privileges. Employees should be able to request credentials, like colleagues.
- Formalized regulations for the interaction of automation services and information security, as well as the operation of IDM. If employees of the IT service act bypassing the application system, for example, fulfilling the oral requests of employees, then the IS officers will be overwhelmed with “inconsistencies” and the work of the IS service will be paralyzed. The focus on the use of IDM is to put electronic document flow of applications. Make IDM a single access request system. In some cases, it makes sense to use operators to interpret requests in the CUB or designate responsible persons in departments so that they create applications for access by their colleagues.
- Participation in the project, fulfillment of obligations to replace employees, work of non-staff employees requires the formation of a certain set of business roles, consisting of typical privileges in various target systems. The use of sets of roles, combining child and parent roles, greatly simplifies the access request procedure and allows simplifying control and recertification of authority.
- A detailed study of the functionality, advanced training of IDM administrators, training ordinary staff to work with the self-service portal will minimize the difficulties of switching to a new solution in any organization.
The acquisition of an IDM solution is a crucial step for the successful implementation and subsequent operation of the system, it is necessary to carefully understand the functional features of various IDMs, select an experienced integrator and conduct training for specialists. The decision on implementation should be taken collectively, with the participation of business, IT and NIS staff.
Alexey Pavlov, Presale Manager
TrustWers LLC
http://trustverse.ru
