Vulnerability in MS Word exploited in-the-wild
Microsoft reports ( SA 2953095 ) that the new memory-corruption cross-Word (2003-2007-2010-2013) 0day vulnerability CVE-2014-1761 is used by cybercriminals for remote code execution in targeted attacks. Attackers use a specially prepared RTF file to execute code through a vulnerable version of MS Word, or when viewing a message with such a document in Microsoft Outlook. In the attacks, exploits for MS Word 2010 were noticed, although the vulnerability is present in all supported MS versions.
The company recommends using the released Fix it tool, which is available at this link . In addition, EMET users with configured protection on MS Word are protected from exploit actions to this vulnerability. EMET v4.1 Settings(latest release version) by default already include the Word process in the list of protected ones. This can be verified through the configuration of Apps. You can also use EMET v5 Technical Preview for protection.
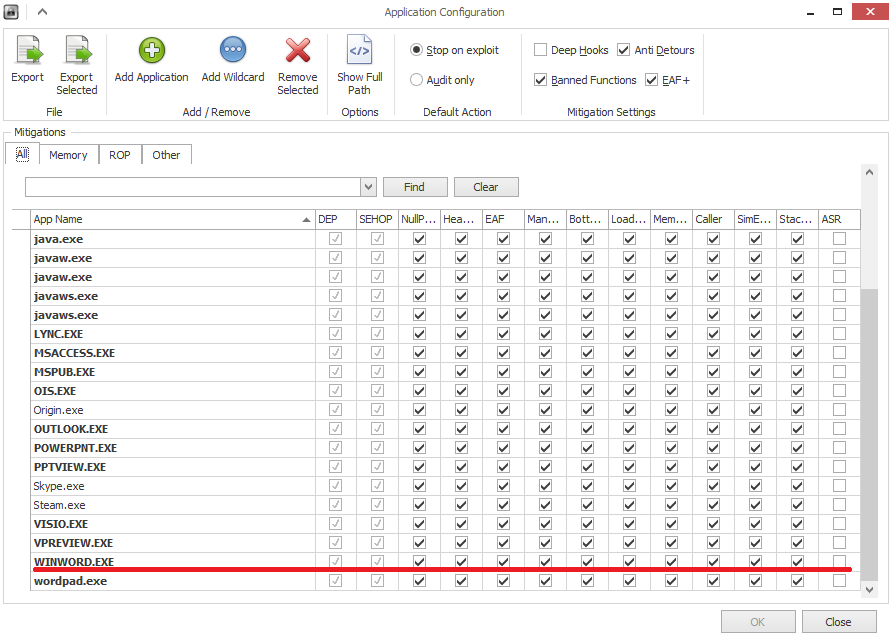
Fig. List of protected EMET processes (setting up Apps).
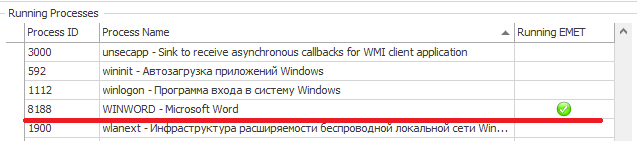
Fig. Marked as a protected Word process in the EMET process list.
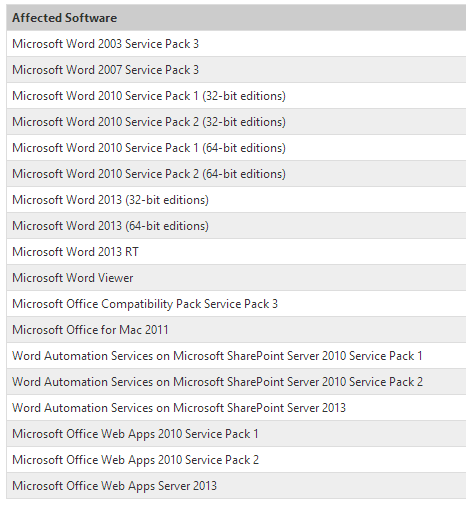
Fig. List of vulnerable software.

The company recommends using the released Fix it tool, which is available at this link . In addition, EMET users with configured protection on MS Word are protected from exploit actions to this vulnerability. EMET v4.1 Settings(latest release version) by default already include the Word process in the list of protected ones. This can be verified through the configuration of Apps. You can also use EMET v5 Technical Preview for protection.

Fig. List of protected EMET processes (setting up Apps).

Fig. Marked as a protected Word process in the EMET process list.

Fig. List of vulnerable software.
