Anonymity methods on the net. Part 3. Firefox

Hello!
Few people are puzzled by the detailed settings of the browser, although the browser is the most popular program for working on the Internet. Using Firefox as an example, I will show how you can make your browser as secure and slightly more “anonymous” as compared to its default setting, while preserving even some functionality! :) Opera or Chrome have similar settings, but, in my opinion, the most flexible from the point of view of security is still Firefox.
The purpose of the article is not to provide a high level of anonymity, but to effectively filter out a lot of identifying, superfluous, and even potentially dangerous data that is, one way or another, transmitted or received by the browser.
All parts are here:
Part 1: Methods of anonymity on the net. Just about complicated .
Part 2: Methods of anonymity on the web. Data leaks .
Part 3: Methods of anonymity on the web. Firefox .
Part 4: Methods of anonymity on the web. Tor & VPN. Whonix .
Cookies
Cookies are text files with any values stored by the application (often the browser) for various tasks, for example, authentication.
If you completely disable the acceptance of cookies, then some sites may have problems with authorization, but Firefox allows you to accept cookies and clear them after it is closed. The option “Accept cookies from third-party sites” is also desirable to disable, however, for example, logging on to Habr with disabled 3rd party cookies, we will not get access to habrastorage.org, so I prefer to accept cookies from the sites visited.
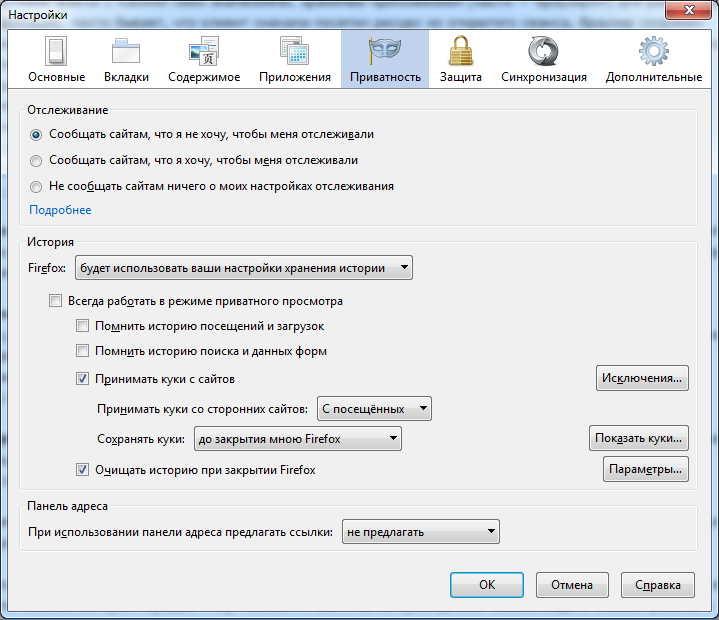
Moreover, Firefox allows you to maintain a white and black list of sites with cookies.
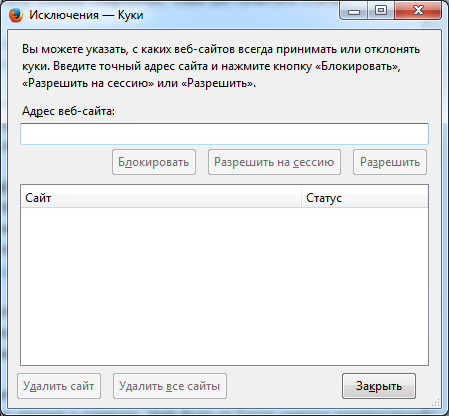
If we want privacy, then when you close Firefox, you need to clear everything. Yes, it’s not very convenient, but there are no traces left.
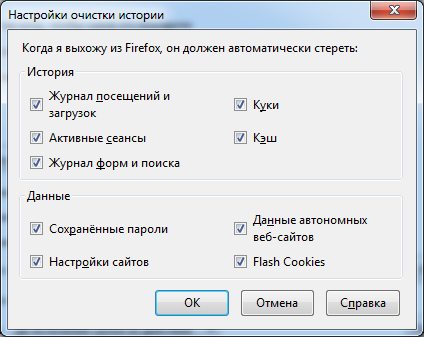
Pay attention to the “Flash Cookies” checkbox, this is not the default Firefox checkmark, we will talk about it a little later when we touch the LSO or Flash cookies.
Here, in the settings, special attention should be paid to clearing the browser cache. In the article: " Cookies without cookies ", the need to clear the cache is justified.
On the Firefox settings page: about: config, there is a parameter: browser.cache.disk.enable , which is responsible for using the disk cache. A value of false means that the cache will not be used at all. For the rest of the browser.cache.disk settings, do not bother; after disabling the cache, they are no longer important.
A convenient and free program, CCleaner, helps you clean up all the already accumulated traces of Internet activity stored even in the farthest corners of the hard drive.
Java, Flash, Adobe Reader ...
All of these plugins are separate applications that run on behalf of the user. They can bypass the proxy settings, store their separate long-lived cookies (Flash - Local Shared Objects), etc.
All plugins should ideally be disabled or deleted. Without Java and Adobe Reader, it’s quite possible to live in a browser, but there are situations when Flash still has to be enabled, otherwise the site simply won’t work. In this case, you need to ensure regular updates to Flash and the prohibition of the storage of Local Shared Objects (LSO) or Flash cookies.
It is also recommended that you enable Flash only upon request. So you allow to run exactly the Flash element that you really want. You can do this in the settings of plugins (add-ons).

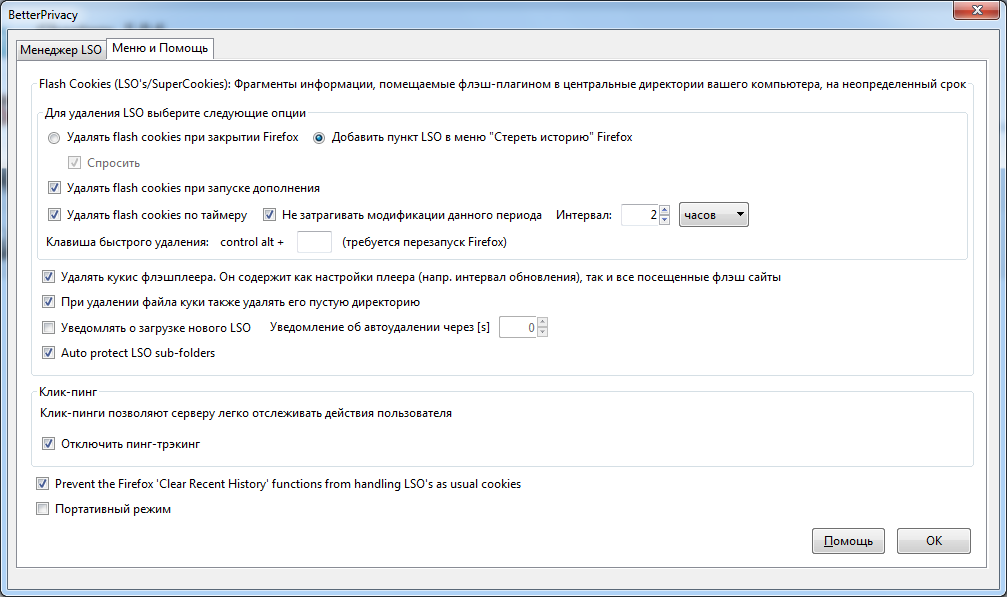
To ban LSO storage, a Firefox add-on, Better privacy , has been specifically designed . I prefer that the checkmark for clearing LSO be added to the Firefox menu “Erase History”, as in the previous figure.
Browser fingerprint
The browser provides the server with dozens of categories of data, including the so-called user agent . All this can form a rather unique “digital fingerprint of the browser”, by which it can be found among many others already in an anonymous session.
There are many additions to replacing the browser user agent , I'm used to using User Agent Overrider . The add-on is stable, convenient, constantly updated, is in the official Firefox repositories.
Javascript Scripts
Client-side Javascripts can collect many categories of identifying data for the server. Moreover, if the visited site is subject to XSS , then the included Javascript scripts will help the attacker to conduct a successful attack with all the ensuing consequences.
In order to prohibit these scripts, NoScript add-on is best suited .
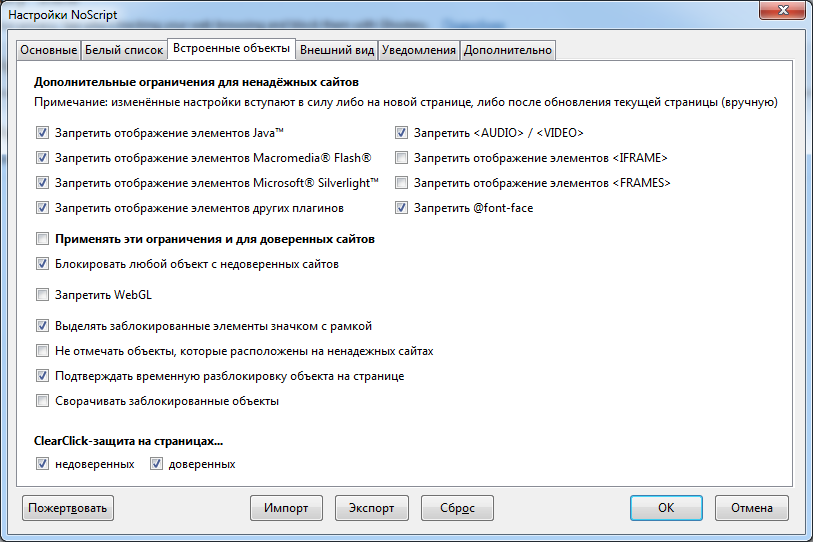
In addition to Javascript, the add-on can block many more different elements: Java, Flash, etc. The user can temporarily allow all active content on the page to be executed or do it on an ongoing basis.
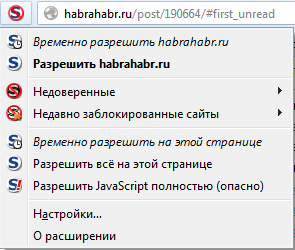
In the same section, I will describe another addon that goes side-by-side with NoScript: RequestPolicy .
The RequestPolicy addon is needed to control cross-site requests and protect against CSRF . Cross-site requests are made when you go to one site, he has already requested from another site the desired resource, for example, a picture, and showed it to you. Similar mechanisms are most often used for advertising purposes. I note that in this way malicious sites can do really bad things, for example, under certain conditions, perform unauthorized actions on the third site with your saved cookies. Imagine what this could threaten.
The author of RequestPolicy recommends using it in conjunction with NoScript, as each add-on is tailored for its own purposes, and together they provide flexible and comprehensive protection. In the picture, RequestPolicy blocks the picture from habrastorage.org.
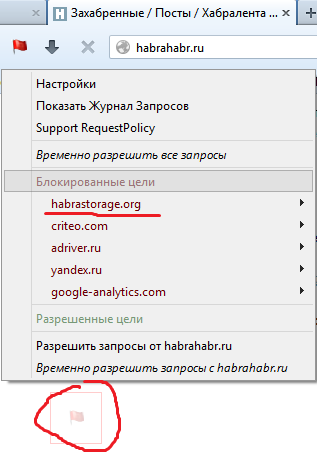
It is worth noting that some sites do not like blocking Javascript and cross-site requests at all. Some time must pass in the "training" mode to form a trusted list of regularly visited resources. What to do, safety and convenience have always stood on different scales.
Web bugs
Web Bugs are invisible details of web pages used to monitor site visits; they are also able to send different client information to the server.
There are two main add-ons to block web bugs: Ghostery and DoNotTrackMe .
The principle is similar for them, when I compared them, I settled on my subjective feelings on Ghostery, and I will describe it. It is important to note that during default configuration Ghostery does not block all bugs and trackers, it must be done manually in its settings at the local address: resource: //firefox-at-ghostery-dot-com/ghostery/data/options.html.

When you visit a site where there are similar elements, Ghostery will block them and issue the following notification.
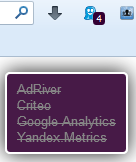
Over time, you will notice that Ghostery and RequestPolicy intersect in blocking some elements, for example, Google Analytics, Yandex.Metrics, etc.
HTTP referer
An HTTP referer is an http header with which a website can determine where traffic is coming from. If you clicked on the link that http-referer passes, then the site to which this link leads will be able to find out from which particular site you went to it.
Firefox has an interesting setting in about: config: network.http.sendRefererHeader . This clause determines in which cases an HTTP referer will be sent. There are three options:
- 0 - never send an HTTP referer
- 1 - send only by clicked links
- 2 - send for links and pictures (by default)
Let's do an experiment. There is a website: www.whatismyreferer.com , the purpose of which is to show our HTTP referer.
We use the default value network.http.sendRefererHeader = 2 .
We click on the link: www.whatismyreferer.com , we see our referrer highlighted in red (in your case it will be slightly different):

Do the same: www.whatismyreferer.com , but with network.http.sendRefererHeader = 0 . Oops!

Set network.http.sendRefererHeader = 0 , and the referrer will not be transmitted.
There is another similar parameter in the settings, network.http.sendSecureXSiteReferrer, he is responsible for transferring the referrer between two https sites. However, do not bother, it does not work after disabling the previous setting.
By the way, have everyone heard about the DuckDuckGo search engine ? That he did not send referrers, I was sure. But left-clicking on the first link (after advertising) in its search results for: duckduckgo.com/?q=www.whatismyreferer.com with network.http.sendRefererHeader = 2 installed , I saw the following:
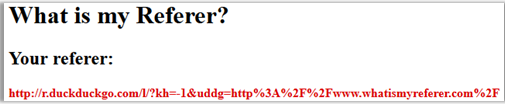
If you click with the middle mouse button (open a new tab), then everything is OK, the referrer does not really appear.
be careful: referrers are used in the work of many Internet resources, their disconnection can lead to the most unexpected consequences, for example, after disconnecting the referrer, I was not allowed to log in to TM ID.
Other
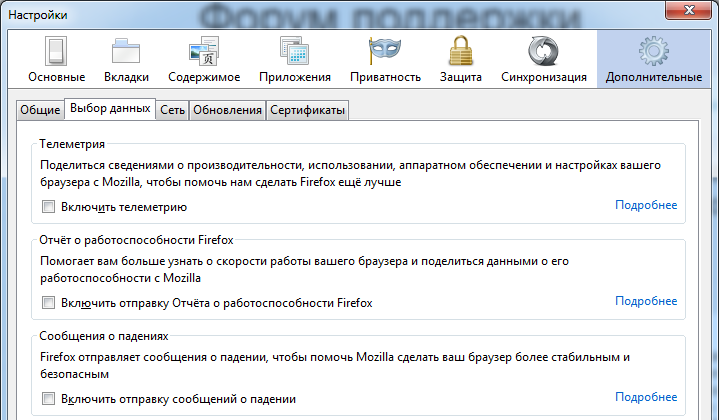
It will be completely superfluous to send any service information to Mozilla.
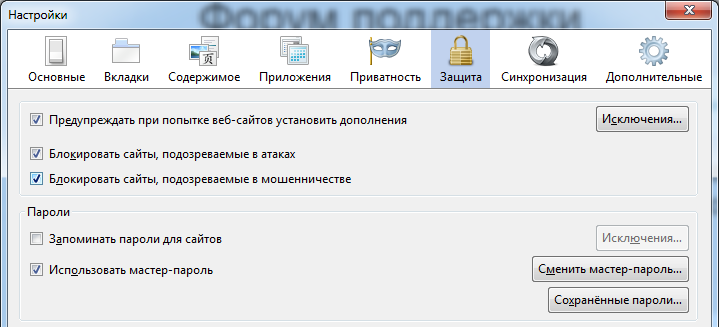
For the sake of anonymity, I would advise you not to store passwords at all, although Firefox has the ability to use a master password with which all other passwords are encrypted, so you can’t remove them in clear text.
HTTPS Everywhere
This add-on is needed in order to force only use https-connection for sites that support it.

Adblock Plus
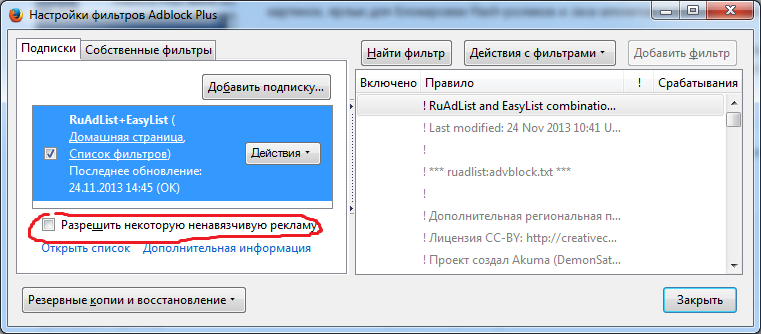
Not so much safe as just useful. Adblock Plus is needed to block all possible advertising while it has a regularly updated list of filters. I note that in the settings there is a checkmark: "Allow some unobtrusive advertising", which can be removed if desired.
The last tip for those who actively use SOCKS when surfing the web. The network.proxy.socks_remote_dns setting determines where DNS queries will be executed when using SOCKS5. The value “true” sets that they will be executed through the SOCKS proxy, and not on the client itself. So we will be protected from DNS-leaks .
You can read more about each setting from about: config Firefox here . And at this link part of them is painted in Russian.
Ufff, like that! I myself use the described configuration of Firefox. At first it was necessary to get used to it a little, but I understand why all this is necessary.
Thanks! Ready to answer all questions.
