Hardware Trojans: Now With Doping
A long time ago there were stories about spyware modules in electronic circuits, special codes that made the potential enemy’s electronics unusable, and other echoes of an invisible front war. Those tales are gone, and the problem of insecurity of iron remains and is undergoing a deep study. A group of scientists from the USA, Switzerland and Germany proposed a special type of hardware trojans that are almost impossible to detect either visually, using tests, or outside the laboratory.
Becker, Regazzoni, Paar, and Burleson investigated the possibility and consequences of deliberately disturbing the doping process, namely changing the polarity of the dopant. In fact, only the doping mask changes; even the amount of impurities consumed can remain the same. Scientists believe that such an intervention is invisible even when scanned with an electron microscope and compared with a reference (not to mention that the reference can also be “attacked”).
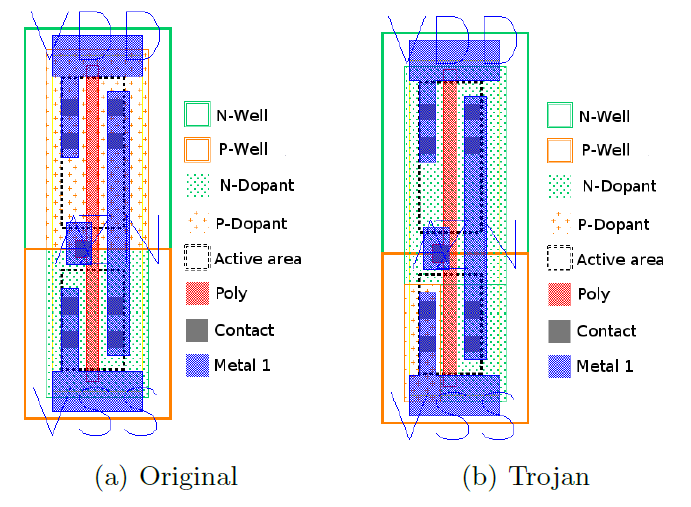
The result is a defective transistor, which can always have a fixed output voltage or create a leakage current. As an example of how such sabotage can affect security, scientists cited the random number generator in Intel's Ivy Bridge, in particular because its design and testing method are publicly available.
The Ivy Bridge random number generator stores two 128-bit constants: key K and state C. In normal operation, these constants are updated quite often, but with a few changes, you can achieve a fixed value of the key K and an almost fixed value of C (this is “almost »Necessary for passing internal and external tests). The difficulty of guessing the value of C is thus reduced to the desired number of bits; Scientists believe that 32 is enough to pass the external NIST test. Since the random number is generated using AES state encryption C with the key K, the entropy does not suffer; cyclicity is also not observed: the state is seated quite often. The built-in test (Built-In Self-Test) checks the checksum of random numbers for the given initial parameters (changes do not affect this area) and entropy,
The ability to create a leakage current was used in another example to determine the secret keys of an encrypted channel while maintaining the protection of the channel as a whole. In fairness, it should be noted that so far no samples of hardware trojans have been detected, but still ahead.
Study original
Becker, Regazzoni, Paar, and Burleson investigated the possibility and consequences of deliberately disturbing the doping process, namely changing the polarity of the dopant. In fact, only the doping mask changes; even the amount of impurities consumed can remain the same. Scientists believe that such an intervention is invisible even when scanned with an electron microscope and compared with a reference (not to mention that the reference can also be “attacked”).

The result is a defective transistor, which can always have a fixed output voltage or create a leakage current. As an example of how such sabotage can affect security, scientists cited the random number generator in Intel's Ivy Bridge, in particular because its design and testing method are publicly available.
The Ivy Bridge random number generator stores two 128-bit constants: key K and state C. In normal operation, these constants are updated quite often, but with a few changes, you can achieve a fixed value of the key K and an almost fixed value of C (this is “almost »Necessary for passing internal and external tests). The difficulty of guessing the value of C is thus reduced to the desired number of bits; Scientists believe that 32 is enough to pass the external NIST test. Since the random number is generated using AES state encryption C with the key K, the entropy does not suffer; cyclicity is also not observed: the state is seated quite often. The built-in test (Built-In Self-Test) checks the checksum of random numbers for the given initial parameters (changes do not affect this area) and entropy,
The ability to create a leakage current was used in another example to determine the secret keys of an encrypted channel while maintaining the protection of the channel as a whole. In fairness, it should be noted that so far no samples of hardware trojans have been detected, but still ahead.
Study original
