Continuing Spam Protection with Cisco IronPort c170
Foreword
 About IronPort c170 I wrote on a habr a year ago. And this was my first article that gave me an invite. Unfortunately, since that time, not a single (!) Article about this piece of iron has appeared on the hub, which, in my opinion, is not permissible for such a resource as the hub.
About IronPort c170 I wrote on a habr a year ago. And this was my first article that gave me an invite. Unfortunately, since that time, not a single (!) Article about this piece of iron has appeared on the hub, which, in my opinion, is not permissible for such a resource as the hub. To begin with, of course, I will remind you of my first article: habrahabr.ru/post/148317
It is a review and does not draw any conclusions. But over the course of the year, I figured out the hardware a bit, learned some tricks and met with a firmware error ... and now I am ready to tell you something more than nothing :)
First, I would like to show again how much spam in the world goes.
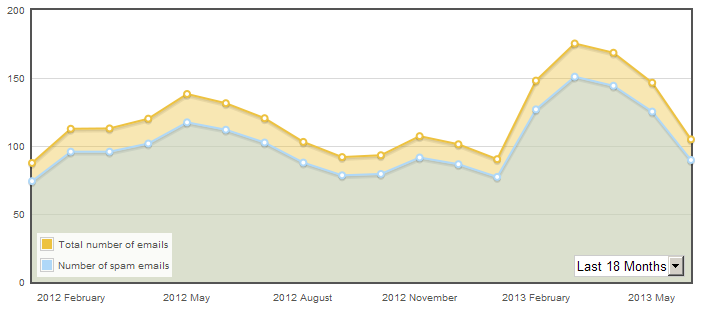
In a billion letters a day. Total spam accounts for approximately 85% of the total mail traffic in the world.
Despite the low efficiency, its amount is not going to decrease. Damn, who reads it at all? Do people really call these phones? Well, okay, distracted ...
So. Let's start by recalling the general default spam filtering methodology. First of all, IronPort does not care about the body of the letter, but its sender. The address, subnet for it has a large role and for each source the piece of iron puts points from -10 to +10. Points IronPort takes from senderbase.org. If you just go to the site and enter the address of your outgoing mail server, you can see only a short poor, good or neutral. But IronPort knows more than that and rates it down to tenths. By default, the system breaks the smtp session before transferring data if the server rating is less than -3.
How I improved the antispam filter
This section is more likely for those who already own a piece of iron.
It suited me, I saw what kind of letters come with such a rating and if the client has a negative rating at all, this definitely means that a lot of messages with bad content were noticed from this source and trust such a server it’s worth with caution, but it’s better not to trust at all.
So far ... the long-awaited letter to the director was not just dropped. And I found this an unpleasant event. I quickly added the server to the white list and carefully informed the director that somehow ... for spam they counted the letter and you can send it again! Everything worked out, the lightnings were not thrown, and I began to think how could I modernize the system so that spam would not come and the message would not drop.
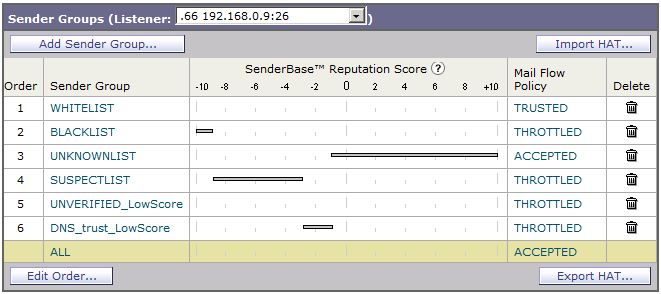
I started with a simple one: I separated traffic -3, but did not destroy it, but created a special quarantine into which I began to drop letters. It was the simplest, but most importantly, it protected me from the irretrievable destruction of letters. For quarantine, I allocated the maximum remaining disk space of 2.3 GB (I don’t know why it’s so small, but no longer possible) with a shelf life of 50 days. And now, on average, this quarantine is 55% full.
However, this was not enough. I noticed that it’s prohibitively a lot of spam with a negative rating somewhere from -0.5 to -3. It was sad, because you just can’t filter them out - a few percent of letters from them were benign. Since all the same, no one reads the entire text, I hasten to inform you that this post is a towel for me. However, I noticed that none of the spam emails contains the correct PTR records, however, all the correct letters with this rating contain the correct PTR-A bunch. However, my disappointment still knew no bounds. In standard filtering, there is no way to configure the filter according to the source of the sender group. You can immediately drop the letter, but you can’t filter it! Stupidity.

I had to go ahead and blow dust off the pdf instructions and see what else is in the settings. In order to solve the filtering problem for PTR-free sources, I had to delve into the bowels of the unfriendly command interface.
As a result, I had to create a special filtering rule. It looks pretty simple:
Config text
Num Active Valid Name
1 Y Y DNS_Fail_ToSpam
DNS_Fail_ToSpam: if sendergroup == "UNVERIFIED_LowScore" {
quarantine("trash");
}And it does just what it needs to do - if the letter comes from the group of senders UNVERIFIED_LowScore, then it goes to that very special quarantine.
As a result, compared with the initial setting, where letters less than -3 were simply destroyed, and almost all reach higher, my settings showed a higher level of filtering, as well as unsurpassed resistance to letter loss, even the most notorious trash will be stored ... just in case: ) Only letters with the wrong recipient are killed immediately.
Observation: From the moment I started taking everythingsmtp sessions and letters with them, the number of connections has decreased dramatically! And decreased several times. From which I concluded that spammers do not care what kind of time delays you have in sessions, drops, and everything else, they will try to send a letter many times, and not one, as it is considered.
Problem with firmware
At some point, very strange letters began to be sent to the mail from the piece of iron. Something like this:
Text of the letter
The Critical message is:
An application fault occurred: ('egg / coro_postgres.py _simple_query | 756', "", '_simple_query (ERROR 53000: could not write block 14 of 17144/17171 blind: Too many open files in system)', '[egg / quarantine_hermes.py _expiration_main | 1980] [egg / quarantine.py expire_all_messages | 771] [ egg / quarantine.py _process_transaction | 871] [egg / quarantine.py _expire_messages | 1355] [egg / quarantine.py _query | 1669] [egg / quarantine.py _call_db | 1643] [egg / quarantine.py _db_query | 1726] [ egg / coro_postgres.py query | 346] [egg / coro_postgres.py _simple_query | 756] ')
Version: 7.6.1-022
Serial Number: 5057A8E1583B-FGL161740BG
Timestamp: 13 Dec 2012 00:32:18 +0400
To learn more about about alerts, please visit our Knowledge Base. In many cases, you can find further information about this specific alert. Please click the Knowledge Base link after logging into our Support Portal at:
www.cisco.com/web/ironport/index.html
If you desire further information, please contact your support provider.
To open a support request for this issue, access the IronPort C170 and issue the "supportrequest" command. The command sends an email with diagnostic information directly to Cisco IronPort Customer Support to facilitate a rapid diagnosis of the problem.
Thank you.
An application fault occurred: ('egg / coro_postgres.py _simple_query | 756', "
Version: 7.6.1-022
Serial Number: 5057A8E1583B-FGL161740BG
Timestamp: 13 Dec 2012 00:32:18 +0400
To learn more about about alerts, please visit our Knowledge Base. In many cases, you can find further information about this specific alert. Please click the Knowledge Base link after logging into our Support Portal at:
www.cisco.com/web/ironport/index.html
If you desire further information, please contact your support provider.
To open a support request for this issue, access the IronPort C170 and issue the "supportrequest" command. The command sends an email with diagnostic information directly to Cisco IronPort Customer Support to facilitate a rapid diagnosis of the problem.
Thank you.
The text is constantly changing. For some time I did not pay special attention to them and thought that while letters were being filtered, you should not worry. Everything was fine until the letters were filtered out :) IronPort at some point simply stopped assigning points to the servers of the senders and it turned out that “astrologers announced a week of a long MPH. The amount of spam has grown 10 times. "
Well, I did as it is written: I contacted technical support.
At first, a certain Ahmed Aaref started a conversation with me. Probably from sunny India. But then, when they opened the case, an employee from Germany contacted me. Then, there was a long ordeal to configure a special security channel for technical support. It all didn’t work out and agreed that I would just give them full SSH access :) It’s not very safe, I thought, but it is impossible to go beyond IronPort by standard means. After that, the engineer began to poke around. And, lo and behold, it all worked.
However, to the core, I was struck by the reason for the failure:
Technical Support Solution
I have investigated the issue further and can confirm that the appliance encountered known defect 86843 after upgrade to AsyncOS version 7.6.1-022, where a subfolder for the reputation engine was not created. This did not cause any issue at the time after the upgrade, but in the morning of December 12, an update of the reputation engine has taken place, causing the engine not being able to restart properly due to the missing folder.
In order to solve the issue, I have created the missing subfolder on the appliance. In order to restart the reputation engine properly, the appliance needs to be rebooted. Could you please go ahead and reboot the unit gracefully? After the reboot, the appliance should work properly again and retrieve the SenderBase Reputation Scores!
In order to solve the issue, I have created the missing subfolder on the appliance. In order to restart the reputation engine properly, the appliance needs to be rebooted. Could you please go ahead and reboot the unit gracefully? After the reboot, the appliance should work properly again and retrieve the SenderBase Reputation Scores!
Tons of terrible mistakes, and the reason is ... subfolder. Nevertheless, in the end I want to say that I liked the communication with technical support. Although they behaved to some extent stereotyped, it was still felt that there were people there and they wanted to help. They understood my crooked English and I understood them at the same time)
What I did not like after a year of operation
- Still, the web interface is not well thought out, which forces you to come up with crutches. This can be done on purpose, to attract engineers to perform more complex tasks.
- Lack of LACP link aggregation support.
- Inability to do reverse sender verification.
- Not flexible rules. I would like to independently manage the grades, add new verification tools to increase or decrease grades.
What pleased you? Is it worth it?
I do not know if it is worth the money) The cost is still rather big. About $ 20-30 per user per year. Maybe now I would look for other solutions, but for all the time there was only one real problem. And it is described above. If I had not updated the firmware, it would not have appeared in everything. There were no more problems with the device. It stands buzzing in the server room, it doesn’t ask. Sometimes I forget which ports I set up the administrative part and generally forget where what is located, when something needs to be tightened up. In this regard, everything is gorgeous :)
Spam filters quite qualitatively, and personal quarantine allows you to save the administrator from manual actions to extract letters, the user can unblock the letter in the weekly report on his quarantine.
Thanks to everyone who read it. If someone has questions about a piece of iron, I will answer everyone. Within the limits of what I know, of course :)
Well, I add a screen with my statistics.

