Cybercrime as a service: services and prices
The cybercrime industry cost the world three trillion dollars in 2015 and is projected to increase to six trillion by 2021. All costs in the complex are assessed - for example, in an attack using an encoder, we consider not only the amount of the ransom, but also the costs of reduced productivity, the consequent enhancement of security measures, image damage and not only.
Cybercrime as a service is not something fundamentally new. Malware developers offer products or infrastructure on the black market. But what exactly do they sell and how much does it cost? We looked at several sites on the darknet to find answers to these questions.

In darknet available many packages of programs extortionists. Updates, technical support, access to C & C servers, tariff plans - everything is like that of the “white” software, with the exception of the legislative ban.
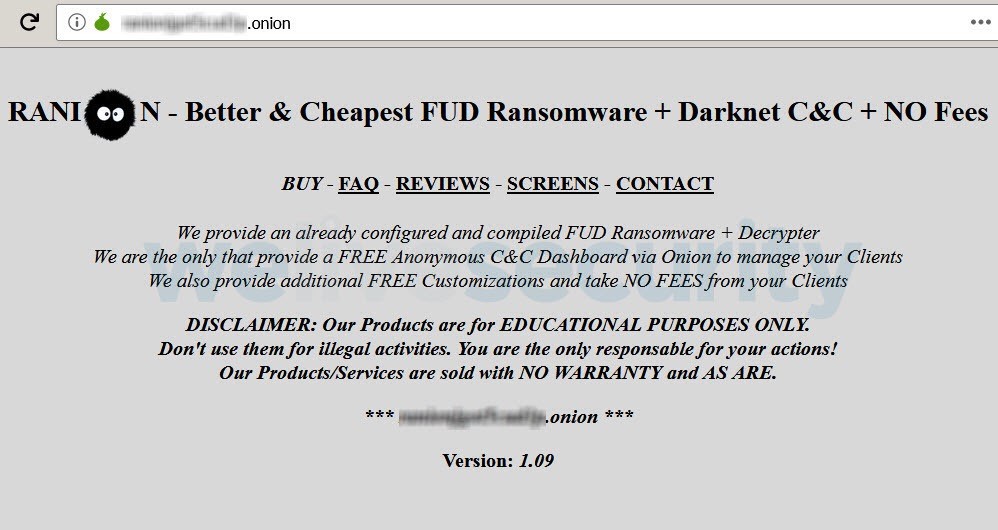
Figure 1. The program of the extortionator Ranion is available in the darknet.
As part of one of the packages, the extortioner Ranion is offered, it is available by subscription for a month and a year. There are several tariff plans, the minimum fee starts from $ 120 per month. Premium equipment - $ 900 per year or $ 1,900 if the customer wants to add additional functions to the executable file of the program.
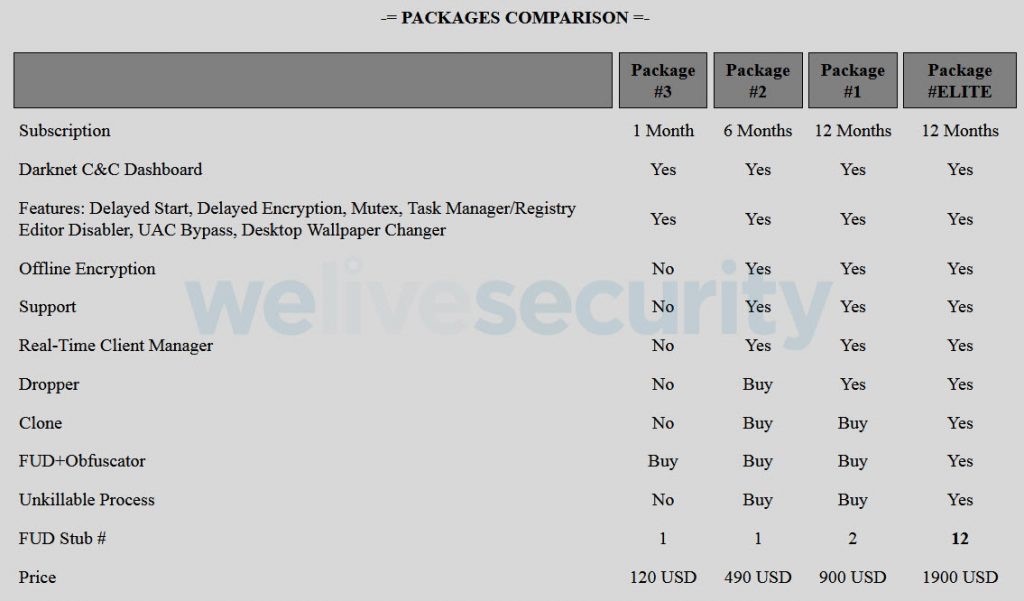
Figure 2. Options for a subscription to Ranion offered by cybercriminals
Another payment scheme is possible - cybercriminals provide malware or access to the C & C infrastructure for free, and then take away some of the funds received from victims.
Whatever strategy is used, we see that the tenant takes on further operations with malware. He needs to deliver the program to the victim's device, for example, using spam mailing or access to vulnerable servers via RDP .
In the darknet, you can find services that offer credentials for accessing servers through the RDP protocol. The price is in the range of 8-15 dollars for one server, they can be sorted by country, operating system, even according to which payment sites users came from these servers.
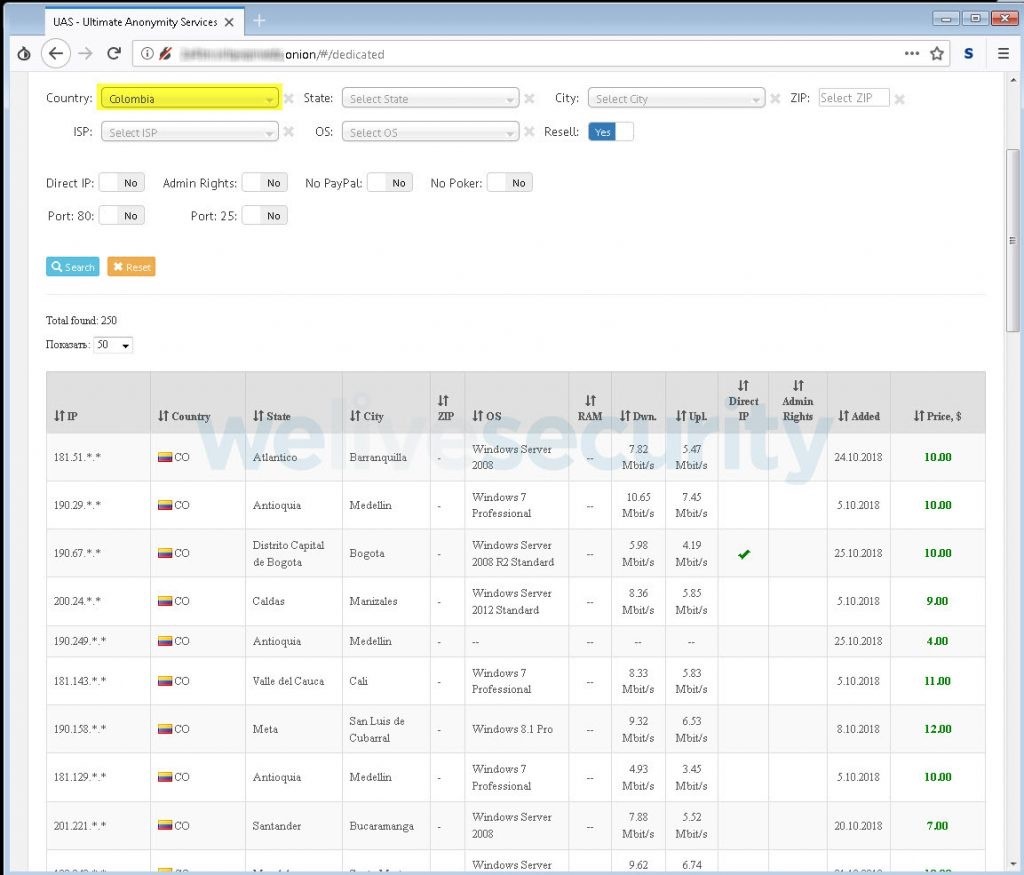
Figure 3. Selling access to servers in Colombia via RDP.
The figure above is a filter for 250 available servers located in Colombia. For each server, detailed information is provided, which can be seen in the following image.

Figure 4. Description of the server, access to which is sold in the darknet.
After buying access, a cybercriminal can use it to launch an ransomware program or install more hidden malware, a trojan or spyware.
Some botnet operators rent their computing power to send spam or DDoS attacks.
The cost of such attacks varies depending on the duration (ranging from 1 to 24 hours) and how much traffic a botnet can generate at this time. The figure below is a variant with a three-hour attack for $ 60.
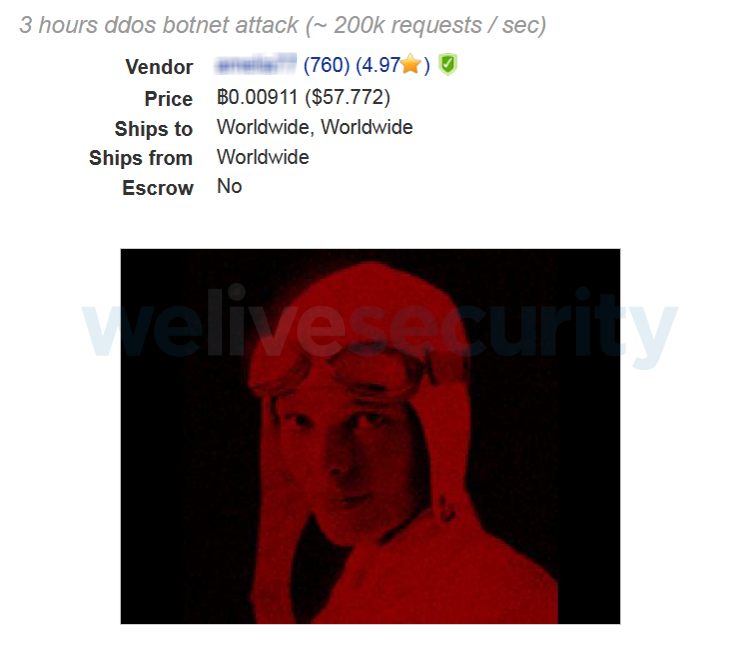
Figure 5. An example of a proposal for renting infrastructure for DDoS attacks
Some offer renting their (usually small) botnets for attacks on online game servers, for example, Fortnite. They often sell stolen accounts. Social networks are used to promote “services”, account holders are not particularly worried about anonymity.
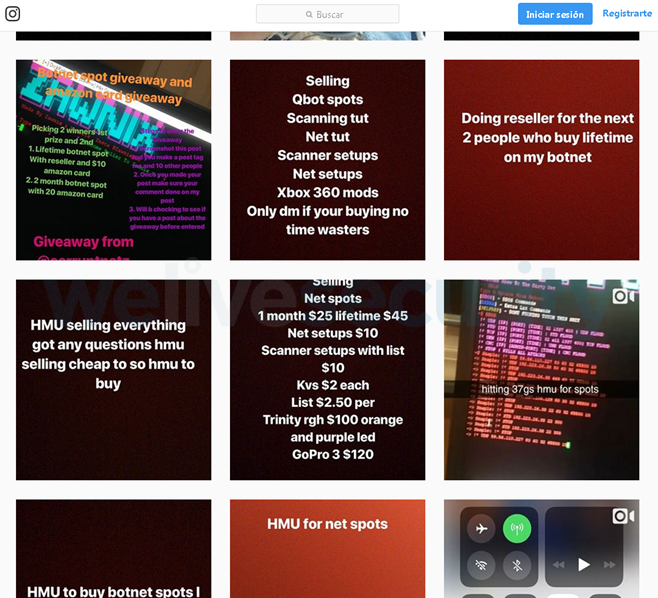
Figure 6. Suggestions for renting botnets to Instagram
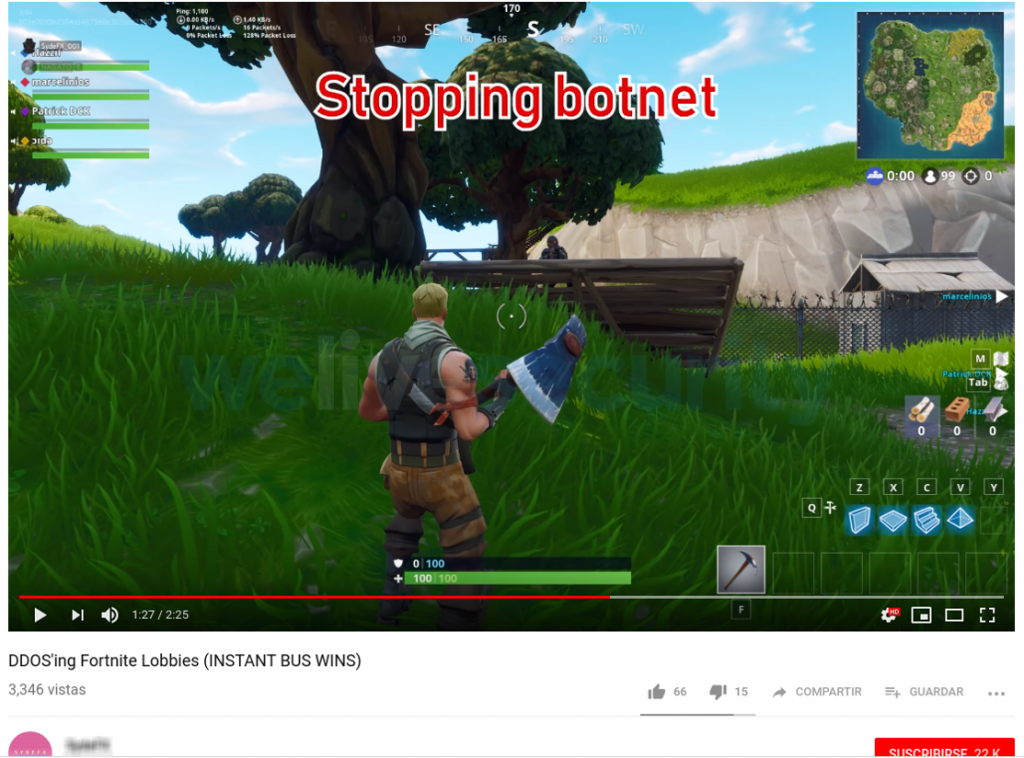
Рисунок 7. Пользователи YouTube демонстрируют DDoS-атаки на серверы Fortnite
Operators of successful phishing attacks are often not at risk of using stolen accounts on their own. It is safer and more profitable to resell the prey to other cybercriminals. As can be seen in the table below, they take about 10% of the funds in the compromised account.
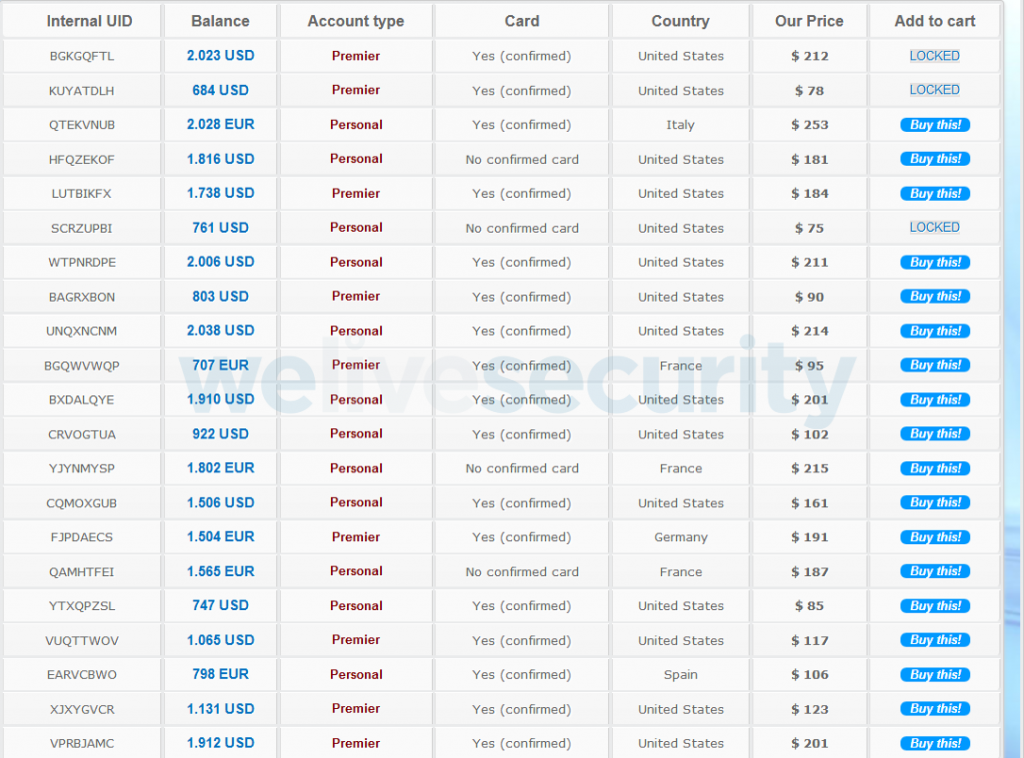
Figure 8. Selling PayPal accounts and credit cards
Some sellers proudly display fake sites and other phishing tools.
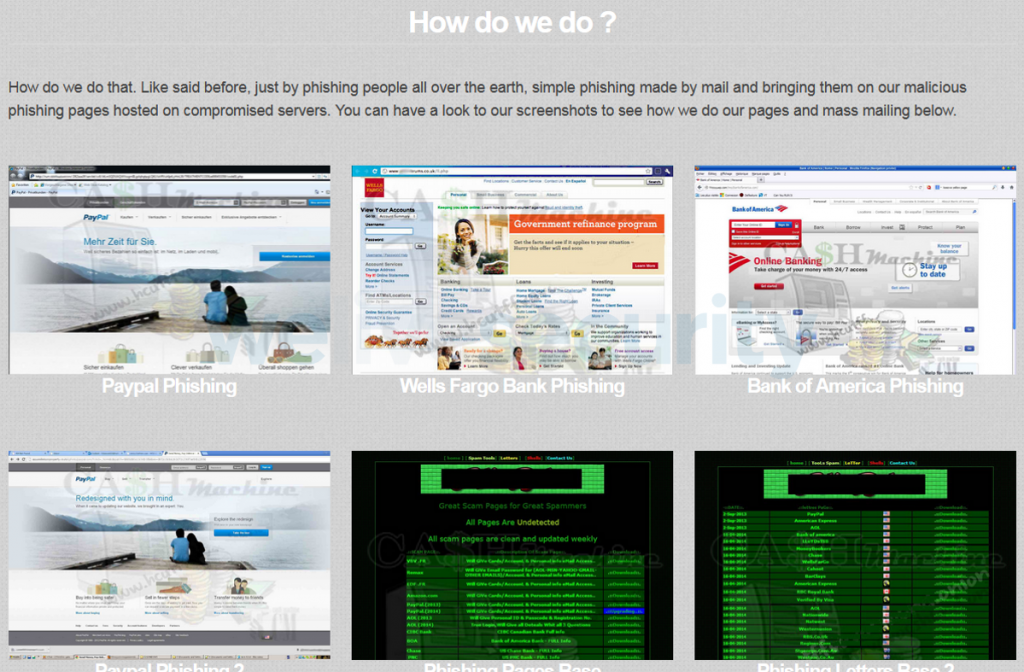
Figure 9. Step-by-step process description
In the presentation on Segurinfo 2018, ESET evangelist Tony Enscombe noted that the malware development industry now resembles a software company. Software offered by cybercriminals, products and services successfully use schemes borrowed from "legal" sales and distribution.
The darknet has a full-fledged industry with sales, marketing, after-sales service, software updates and manuals. In the ecosystem there are a lot of domestic buyers, and the main profit goes to the big players with the most developed infrastructure network and assortment. As a result of the development of the "industry" - the wider availability of malware, combined with their technological complication.
Cybercrime as a service is not something fundamentally new. Malware developers offer products or infrastructure on the black market. But what exactly do they sell and how much does it cost? We looked at several sites on the darknet to find answers to these questions.

Extortionist as a service
In darknet available many packages of programs extortionists. Updates, technical support, access to C & C servers, tariff plans - everything is like that of the “white” software, with the exception of the legislative ban.

Figure 1. The program of the extortionator Ranion is available in the darknet.
As part of one of the packages, the extortioner Ranion is offered, it is available by subscription for a month and a year. There are several tariff plans, the minimum fee starts from $ 120 per month. Premium equipment - $ 900 per year or $ 1,900 if the customer wants to add additional functions to the executable file of the program.

Figure 2. Options for a subscription to Ranion offered by cybercriminals
Another payment scheme is possible - cybercriminals provide malware or access to the C & C infrastructure for free, and then take away some of the funds received from victims.
Whatever strategy is used, we see that the tenant takes on further operations with malware. He needs to deliver the program to the victim's device, for example, using spam mailing or access to vulnerable servers via RDP .
Selling access to servers
In the darknet, you can find services that offer credentials for accessing servers through the RDP protocol. The price is in the range of 8-15 dollars for one server, they can be sorted by country, operating system, even according to which payment sites users came from these servers.

Figure 3. Selling access to servers in Colombia via RDP.
The figure above is a filter for 250 available servers located in Colombia. For each server, detailed information is provided, which can be seen in the following image.

Figure 4. Description of the server, access to which is sold in the darknet.
After buying access, a cybercriminal can use it to launch an ransomware program or install more hidden malware, a trojan or spyware.
Infrastructure rental
Some botnet operators rent their computing power to send spam or DDoS attacks.
The cost of such attacks varies depending on the duration (ranging from 1 to 24 hours) and how much traffic a botnet can generate at this time. The figure below is a variant with a three-hour attack for $ 60.

Figure 5. An example of a proposal for renting infrastructure for DDoS attacks
Some offer renting their (usually small) botnets for attacks on online game servers, for example, Fortnite. They often sell stolen accounts. Social networks are used to promote “services”, account holders are not particularly worried about anonymity.

Figure 6. Suggestions for renting botnets to Instagram

Рисунок 7. Пользователи YouTube демонстрируют DDoS-атаки на серверы Fortnite
Продажа аккаунтов PayPal и кредитных карт
Operators of successful phishing attacks are often not at risk of using stolen accounts on their own. It is safer and more profitable to resell the prey to other cybercriminals. As can be seen in the table below, they take about 10% of the funds in the compromised account.

Figure 8. Selling PayPal accounts and credit cards
Some sellers proudly display fake sites and other phishing tools.

Figure 9. Step-by-step process description
In the presentation on Segurinfo 2018, ESET evangelist Tony Enscombe noted that the malware development industry now resembles a software company. Software offered by cybercriminals, products and services successfully use schemes borrowed from "legal" sales and distribution.
The darknet has a full-fledged industry with sales, marketing, after-sales service, software updates and manuals. In the ecosystem there are a lot of domestic buyers, and the main profit goes to the big players with the most developed infrastructure network and assortment. As a result of the development of the "industry" - the wider availability of malware, combined with their technological complication.
