Why do you need Splunk? Security Event Analytics

Was there a breach of enterprise information security? What internal threats does the organization have? How and how quickly can we detect, block or stop an attack? In this article we will explain how Splunk can help you in finding answers to these questions.
With this article, we continue the series of articles about what tasks you can use Splunk for and today we will understand more about how you can use Splunk for analyzing security events.

In today's reality, enterprises are no longer simply monitoring traditional events, they need solutions that can adapt to modern threats, speed up the speed of response to incidents and make it possible to identify and eliminate known and unknown threats.

Let's take a closer look at what tasks Splunk solves for security:
Real time monitoring

Accelerating a response is challenging in today's complex IT environments. Splunk allows you to get a clear and visual idea of the security status of the organization at the moment, and also contains a convenient setting of views and data detailing up to basic events. Using continuous monitoring, static and dynamic searches, or visual correlations to determine malicious activity reduces response time. Splunk also provides analysts with tools to prioritize for a faster response to threats with higher priority.
Detection of complex threats

With Splunk, you can track the various stages of a complex threat and combine related events. Relationships are defined by any field, any data and at any time interval. Splunk allows security analysts to use advanced statistical analysis and machine learning methods to identify outliers and anomalies that can identify unknown and complex threats.
Internal threats

Splunk is used to detect malicious actions of employees and other internal threats before theft of confidential data, their damage or abuse of authority occurs. With Splunk, you can determine whether permissions are being misused, abnormal behavior, even when using legitimate accounts, access levels or sources. For example, excessively long sessions, non-standard time or entry. And the accumulated data on various user actions allow us to base the research on historical data. Splunk can integrate with Active Directory or HR databases for employee information.
Incident Investigation
Splunk allows you to analyze incidents to determine the circumstances and scope of an incident. This is achieved by searching for and finding correlations for keywords, terms or values for various network devices, hosts, readers, etc. For security analysts, this gives the broader context of the incident, which helps to quickly and better assess the level of threat, identify causes and effects.
Automation of heterogeneous systems
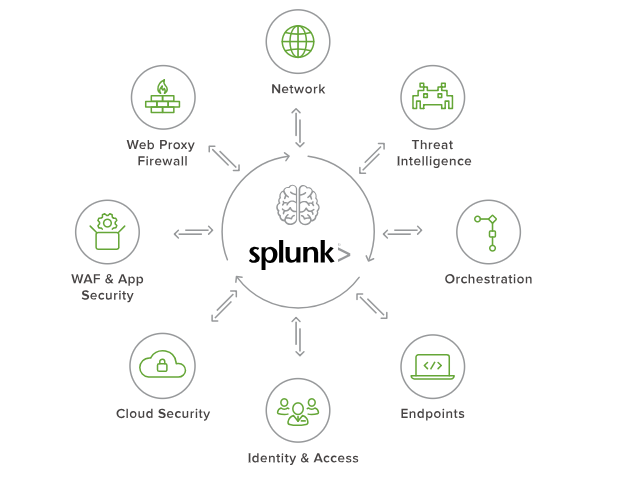
Security architectures typically include different levels of tools and products. As a rule, they are not intended to work together and contain gaps in the work of security specialists in establishing links between different domains. Splunk eliminates these gaps, providing a single interface for automatic data extraction, which allows you to build comprehensive analytics and respond to threats in environments with products from different vendors.
Fraud Detection
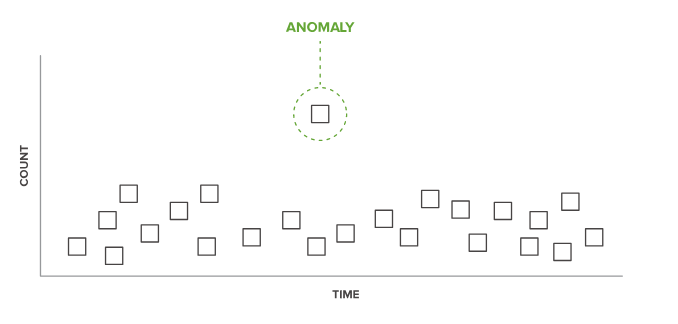
Through the search and analysis of real-time data, the detection and study of emissions and anomalies based on historical data, you can identify fraud, determine the impact and scope of fraud.
Overview of the main ready-made solutions:
Splunk Enterprise Security

Splunk Enterprise Security (ES) is a security and information event management (SIEM) system that provides a detailed picture of the machine data created by various security technologies (network, endpoints, access, malware, vulnerability). With Splunk Enterprise Security, security professionals can quickly detect internal and external attacks and respond to them. This allows you to simplify operations to protect against threats, minimize risk and ensure business security. Splunk Enterprise Security optimizes all aspects of protection and is suitable for organizations of any size and professional level.
Video review can be found here.
Organizations around the world use Splunk Enterprise Security (ES) as a SIEM for security monitoring, advanced threat detection, incident response, and a wide range of security analysis applications.
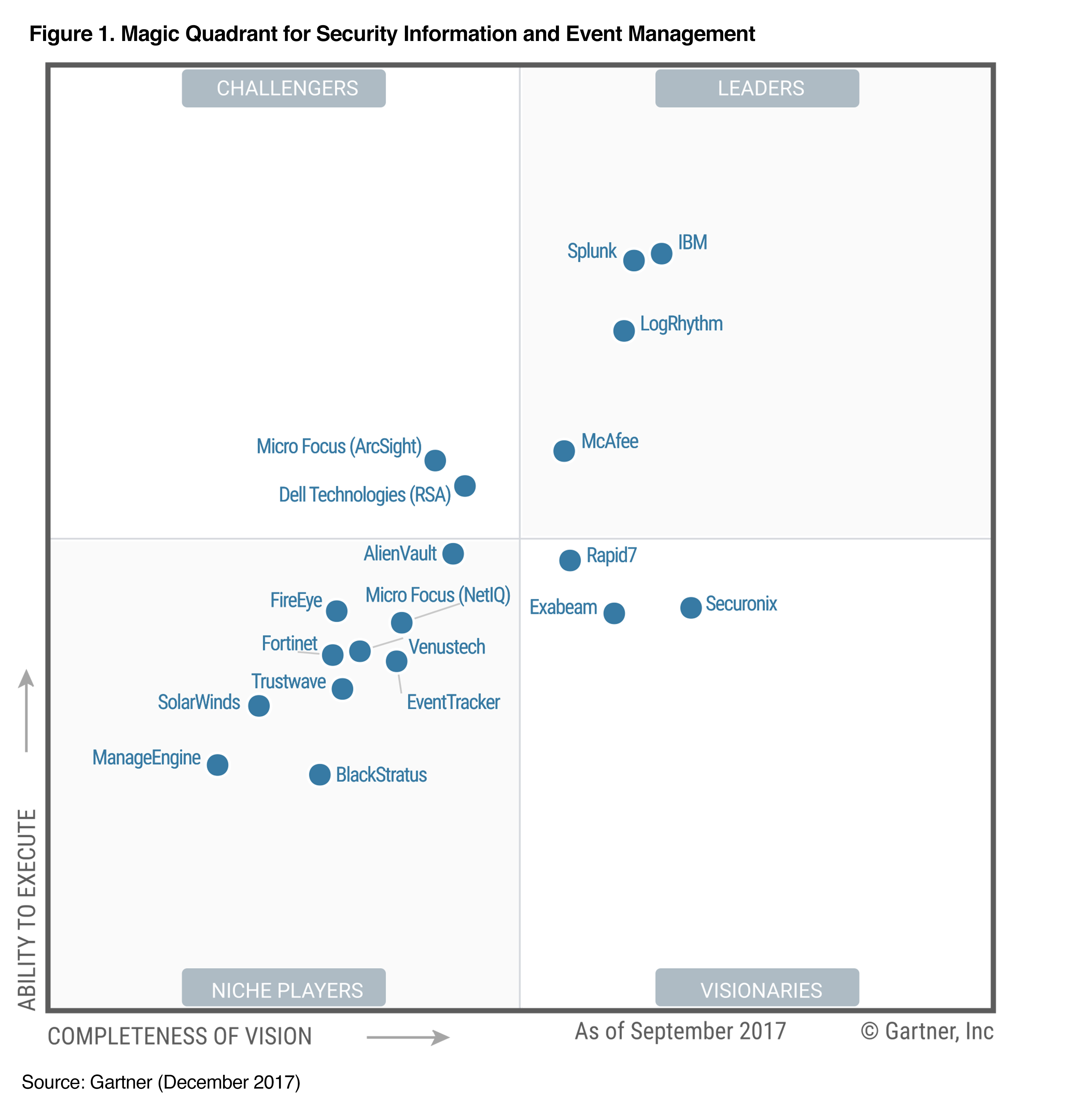
In the fall of 2017, Gartner published its magic quadrant on the market for information security management solutions and security events, where Splunk was named one of the leaders in this market.
Splunk User Behavior Analytics

Splunk User Behavior Analytics (Splunk UBA) helps companies find hidden threats and anomalous behavior of users, devices, and applications using machine learning algorithms, analytics of baseline behavior of users and peer groups. In this way, organizations can detect persistent threats of advanced complexity (advanced persistent threat, APT), malware infections, and internal threats. Splunk UBA provides security analytics and development workflows, requires minimal administration and integrates with existing infrastructure to detect hidden threats.
Video review of this link
PCI Compliance
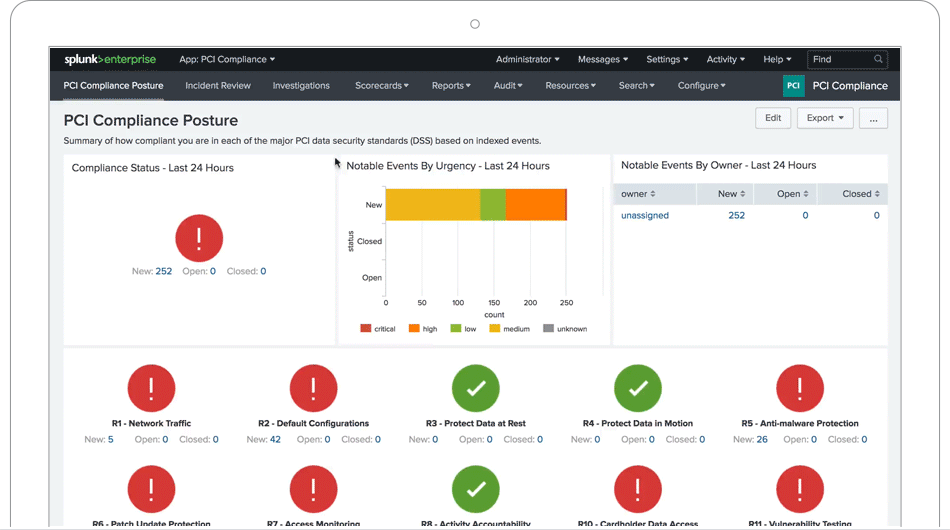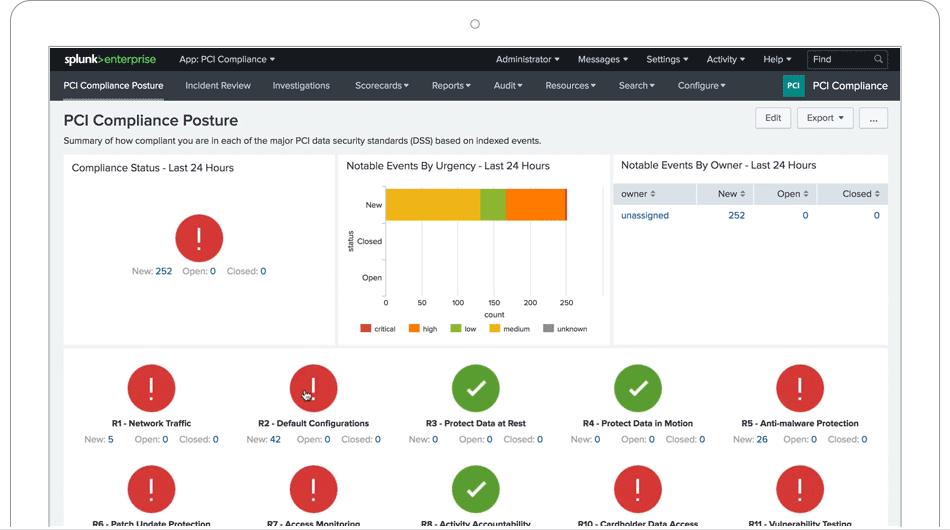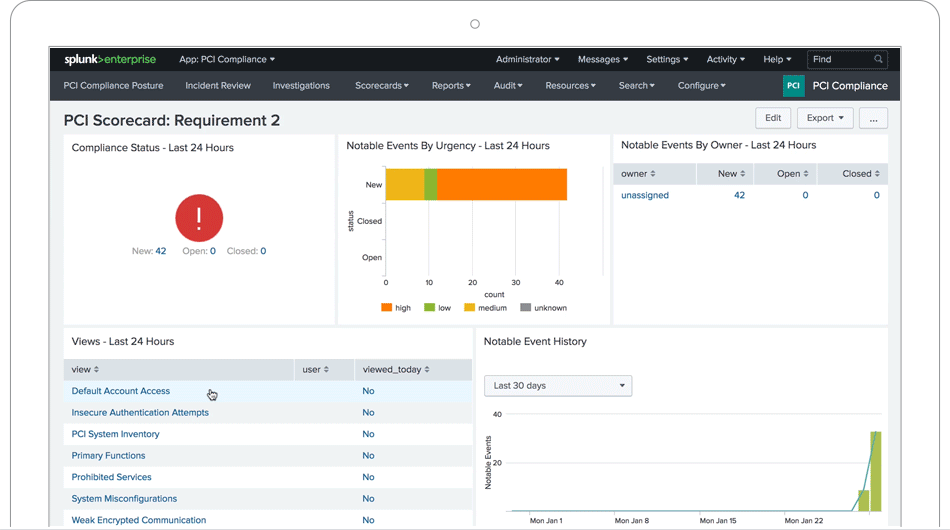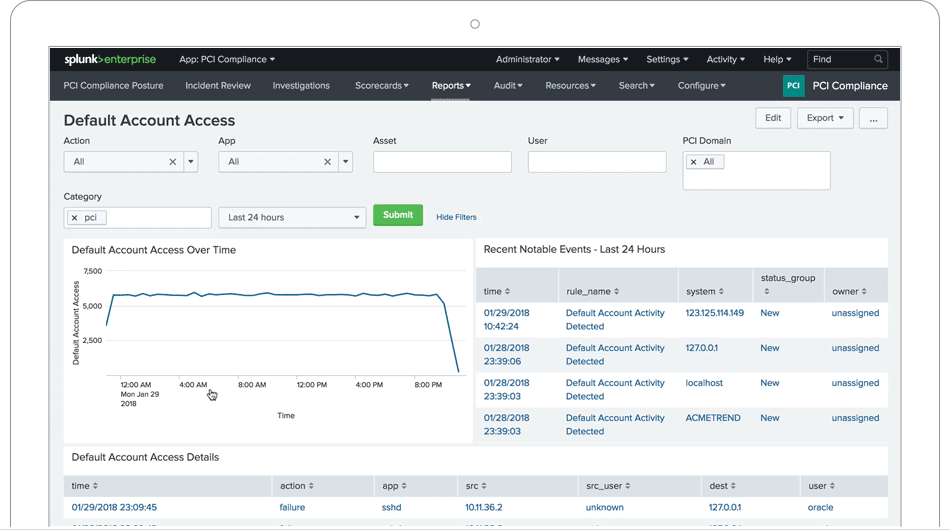
The Splunk PCI Compliance application (for Splunk Enterprise) is an application that Splunk has developed and is supported to help organizations meet PCI DSS 3.2 requirements. The application analyzes and measures the performance and compliance status of PCI in real time. It can also define and set priorities in any areas of management that may be required, and you can also quickly access any report or data request.
The app provides out-of-the-box search queries, dashboards, reports, incident response infrastructure, and integration with employee and device information to give you visibility of system activity, applications, and devices related to PCI compliance.
Video review can be found here.

