Adams State University. How to hack websites. Part 1
- Transfer
Moderator: I thank everyone for coming to our first lecture in the series “Conversations about science and mathematics during the lunch break”. You have received emails; in addition, schedules of seven lectures will be posted around this campus building this semester. I want to introduce you to Dr. Susan Loveland from the Faculty of Computer Science, who will tell you how to hack sites.

Susan Loveland: At the beginning of the presentation, I want to mention that hackers come in all shades of black and white. Today I will play the role of a hacker in the Black Hat and act on the dark side of hacking because being bad is a lot more fun than good. There are hackers in White Hats who do work for computer security companies and investigate computer forensics. They try to find security vulnerabilities before the bad guys take advantage of them.
The task of such hackers is to find the vulnerability, without harming the application, compile a report on the security hole and forward it to the company. I myself have never thought about hacking the site, so I brought with me the co-rapporteur who prepared the slides of our presentation (puts on the Black Hat).
I'm Eve Hacker (Hackersha Eve), Dr. Loveland's alter ego, who will show you how to hack sites. I forgot to mention that Black Hat as a symbol of hackers came to us from old westerns, in which the bad guys usually wore such a hat. And I decided that in order to be an effective hacker, I need to choose an appropriate attire. So I can create an appropriate mood for myself, and you can be interested in watching this presentation. So I give the floor to Dr. Loveland (takes off his hat).
Susan Loveland: Thank you, Eva. Before we begin, I want to tell you how the Internet attracts hackers. First, the widespread availability and accessibility of applications - according to a report by the White Hat Association in 2009, approximately 80% of websites have serious vulnerabilities.
Secondly, profitability - attack automation reduces hacker expenses to a minimum, while simultaneously scaling profits to huge sizes. Thirdly, ease of use - smart, creative hackers love to brag about their exploits, and any bad guy can use the results of their work with the help of Google to find hundreds of tools for hacking the right application. Fourthly, anonymity - you can safely break the law, because it is very difficult to find out when the web application was hacked and track down the person who did it. When you physically rob a bank, you must be in the bank, but when you hack a web application, you can work from abroad, where there are no extradition laws and it is relatively safe from the point of view of hacking.
So what do you do first when trying to hack an app? The first step is the most difficult, because you need to understand what this application is, how it works, where its “inputs and outputs” are.

Application infrastructure research includes server identification and port scanning. Then you need to understand the composition of the application: strings and URL request parameters, authentication mechanism, using TLS / SSL, software that is used in the application (PHP, Java), directory structure and session management.
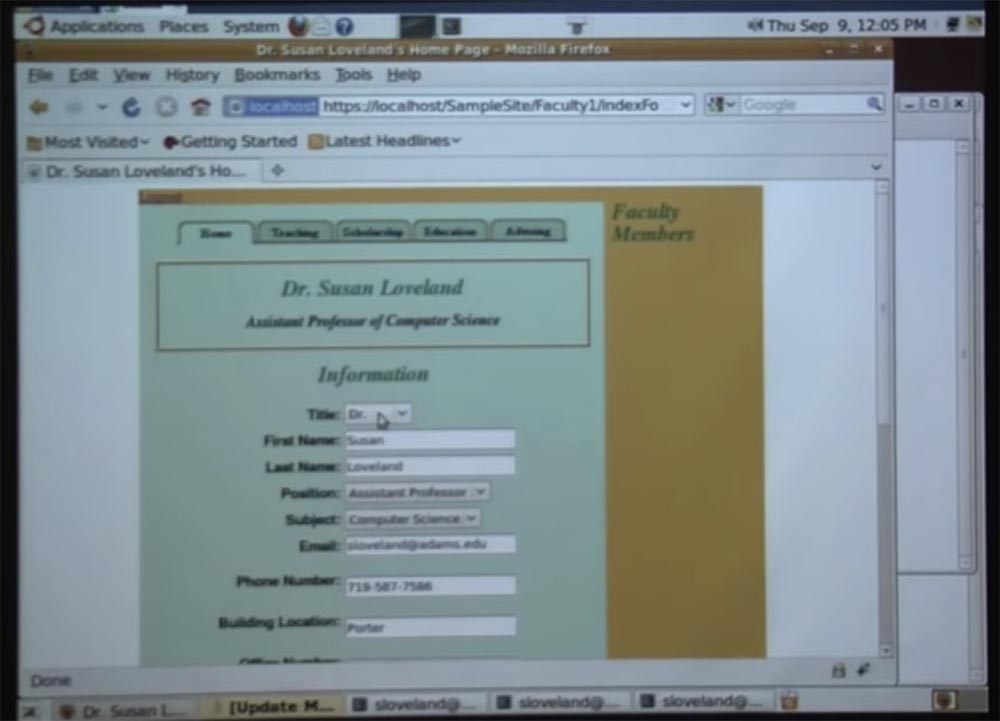
Therefore, I will simply introduce you to the application that will be hacked, and will take you through all the possible vulnerabilities that exist in it. The application that we hack today is called “Faculty Pages”. This project was developed in the classroom of my CS245 web programming course about a year and a half ago.

His idea was that everyone on campus began to use a single set of web pages for each department, since this would look more professional than the pages of a different sample made by employees of individual departments. I spoke with Mark Schonecher to help me and my students with this matter. Mark sent emails to everyone asking what content they would like to see on the web pages of the faculty, and my class developed the “Faculty Pages” that are shown on this slide.
As you can see, there is a main page with content intended for students of the faculty, the “Learning” tab, where teachers can post links to individual courses, the “Scholarships” tab, where you can place the results of scientific activities, the “Education” tabs and “Consultations” .
My students wanted to make it so easy for the faculty members to maintain these pages, so they tied user authorization to the page. After clicking on the link in the upper left corner of the page, a registration form opens in which you need to enter the username of the campus network and the password identifier. After logging in, the same main page opens, but under the word “Information” an “Edit” button appears. After clicking on this button, the teacher can enter the editor panel and add or correct information on the page. These are the main characteristics of the application, which we will try to hack today.
Let's return to our presentation. In hacking, like any other profession, you need equipment, otherwise the work will be ineffective. In order to hack, we need a proxy server.

A proxy server speeds up access to cracking a web page, intercepting all messages between a client computer and a server. You can view all messages, this is very useful, because there is a lot of traffic between the client and the server, which is not visible from the outside. The proxy server allows not only to explore the contents of traffic, but also to change it. In fact, you can completely determine what goes to the server for students who study programming in the classroom.
I want to note that it does not matter how you manage your code on the client side, because a good hacker can always bypass your control by contacting the server that is associated with your browser. Thus, to hack our application, you need a proxy server. To get it is not difficult - you just download any proxy from the Internet.

On the slide, you see three popular proxy servers: WebScarab, BurpSuite, and Paros. You can download any of them for free, install like any other application, and in a few minutes configure your browser to work with a proxy.
The first type of attack that we use today is the Dictionary Attack, or a dictionary search. All attacks of this kind try to find someone's password by going through the list of the most popular passwords and passwords by default, using a set of password dictionaries. If you need such a dictionary, it can also be downloaded from the Internet, it is a public resource.
Before you initiate Dictionary Attack, you need to carefully study the password policy for the application that you are trying to attack. In our case, the “Faculty pages” are tied to the password of Adams University, so we need to find out what kind of password we will select for the hacking application.

The best way to find out what a password looks like is to use the password recovery function, because it gives you a hint. Look what I did - just entered the wrong password, and these guys were so kind that they posted a message at the top of the page describing what kind of passwords I could try. Thus, I find out that in my dictionary, which is used during the Dictionary Attack, I have to try any words not less than 8 characters long, with capital and small letters and numbers.
I must admit that they have worsened the service since the last time I visited the site. Now you can’t just check the functionality of their password, because they changed their policy towards hackers to less friendly, and now, as you can see, they don’t give you any hints when trying to reset the password.
Fortunately, I saved a screenshot of how it looked before, so we know which password to pick up. I think we are ready to give the floor to Eva, so that she shows how an attack is carried out using a dictionary-based search method.
Eve Hacker: thank you, Dr. Loveland! The first thing I'm going to do is go to the login window, which we need to send passwords to the server, and slightly change the URL string. Having done this, I get on the screen an authorization form in which you need to enter a username and password. I have to be able to distinguish the correct password from the wrong one, that is, to see which error the application reports when entering the wrong password.
Since I'm going to pick up Dr. Loveland's password, I type her login sloveland in the username bar, enter the wrong password of 3 characters and click the Login button. After that, the message "Error login" appears. It is very important to see how the application reacts to entering the wrong password.
Next, I need to configure my browser to use a proxy server, so I change the settings for Firefox. Open the tab "Advanced settings", remove the checkbox in the "Use system proxy settings" checkbox and check the "Use manual proxy configuration" checkbox. My proxy will “listen” to port 8080, so it can intercept all requests addressed to the server.

The next thing I need to do is to install the downloaded proxy server, in my case it is Burp Suite. Now you see what this proxy window looks like, which I use during the attack. But I have to go back to the login page and resubmit it to the server. The fact is, there may be a problem due to the fact that I first launched the proxy without reloading the page. If you noticed, our application uses a secure HTTPS connection, and the proxy server does not have the appropriate security certificate. Therefore, I first have to confirm that the application can use an unprotected connection to the proxy and put its URL in the security policy exceptions.

What could have happened if I had not corrected this error? Let me go back and show you this. I again go to the browser settings, and this time I will not rush into setting manual proxy settings that intercept requests. I’ll activate the “Use system proxy settings” checkbox again, because I really need to get the original authorization page first, and, being on this page, I’ll enter my browser settings and again switch to the manual proxy settings.
So, now we have an authorization page that will “talk” to the proxy server. I again enter Dr. Loveland's login and the same incorrect password-fff, which are sent to my proxy server.
Next, I go to the server management page and click the tab, which opens a window for viewing the received request.

Let's see how this request looks in Spider - this is the next tab of the Burp Suite window. To do this, I use the command “send to Spider” and see what the authorization form looks like, it is really interesting. I click on the "Ignore form" button.

And back to the POST request that interests me. We see a request that contains an authorization form, that is, a request to enter user information.

We have several attack methods here - Scanner, Intruder, Repeater, Sequencer, Decoder, Comparer. I am going to use Intruder, so I send him this information using the send to intruder command, and it appears in the window on the “positions” tab. This is all the information that was sent to the proxy server.

It shows a lot of hidden things that cannot be seen on a web page, and highlighted the fields that hackers like to deal with: session ID, session ID, username username and password password used during our attack. The only thing that interests us for Dictionary Attack is the password, so I will clear most of the fields, select the password field and use the add § button to add this field to the dictionary.
This tab will really please you as a hacker, because on it you can select various attack methods using the drop-down menu - Sniper, Battering ram, Pitchfork or Cluster bomb. I will do just that and choose the sniper attack. Next, on the “Payloads” tab, a small setup is performed - we are going to make a replacement for the characters, because I will simply replace the characters in the password with words from the dictionary, after which I have to download the dictionary that I previously downloaded from the Internet. You see the opened dictionary, note that I have removed all words containing less than 8 characters from it, because I don’t want to waste time.

I want to draw your attention to the block on the right with the parameters a, b and e. Let me ask you: when you have to choose a password, where you have to enter either numbers or symbols, have you ever chosen numbers or symbols that look like corresponding letters who are you going to replace them with? You may be tempted to use this method to make it easier to remember your password, but hackers are well aware of this. For example, people often use 4 for A, 8 for B, or 3 for E. Sometimes the letter A is replaced by the symbol @, and the letter b by the number 6, because it resembles it. Thus, in this block, you can configure such matches.
I also know that university passwords require the use of uppercase letters, and since my dictionary contains only lowercase letters, I use the menu below to change the password guessing process rules and modify the key words that will be sent to this hacker tool. I also note that you can use proper names. Since this computer belongs to a scientist, she certainly likes to use punctuation marks, and I provide for this option, noting that you are a drop-down menu.
The last thing to do is to enter the Options tab and enter the address of the site that we want to hack, so here I specify the address of the authorization page.
At the very end, I need to use a tool that will let me know if the password is correct or not, so I’m typing the Login Error parameter so that this phrase appears on the screen to report an error when trying to log in.

Now I can start my attack. I note that being a companion of Dr. Loveland for many years was not a very profitable occupation, so I could not buy the professional version of Burp Suite and used the free version, which was reported by the window that appeared on the screen. So, in the Intruder window, you can see how the hacking process is going on and the substitution of various letters and symbols into the tested password options takes place.

Usually at this time I go to have a cup of coffee or even return to the computer the next day, because it is a rather slow process - as you can see, it started from the very first letter of the alphabet. However, we were lucky - you see the seventh line with the result.

Dr. Loveland chose the password A @ rdv @ rk using characters and letters, so this password fully complies with the requirements of the university and was easy to guess using Dictionary Attack. Therefore, you should be very, very careful when choosing your password.
So, I give the floor to Dr. Loveland, but please note that now I know your password and can access the site on your behalf at any time (takes off the Black Hat).
Susan Loveland: thank you, Eva. I want to ask the audience: how do you think, how common are password attacks? The answer is very, very common! According to experts, about 70% of sites have authorization vulnerabilities. This means that the application developer has made some kind of mistake in the login mechanism, which facilitates hacking the site. But Dictionary Attack attacks are in any case very popular among hackers, and on January 5 last year this method of hacking was used against the Twitter administrator account, which allowed hacking accounts of 33 very famous people, including Obama, and posting hacker jokes on their pages.
I'll tell you about such an anecdote case: when last year I launched a web server for my course, there were only four students, however, in theory, this is a very, very important server, so that over the course of two weeks after its launch, it underwent attacks like dictionary search ”from two different sources. So these attacks are very, very common.
21:35 min
. Adams State University. How to hack websites. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

Susan Loveland: At the beginning of the presentation, I want to mention that hackers come in all shades of black and white. Today I will play the role of a hacker in the Black Hat and act on the dark side of hacking because being bad is a lot more fun than good. There are hackers in White Hats who do work for computer security companies and investigate computer forensics. They try to find security vulnerabilities before the bad guys take advantage of them.
The task of such hackers is to find the vulnerability, without harming the application, compile a report on the security hole and forward it to the company. I myself have never thought about hacking the site, so I brought with me the co-rapporteur who prepared the slides of our presentation (puts on the Black Hat).
I'm Eve Hacker (Hackersha Eve), Dr. Loveland's alter ego, who will show you how to hack sites. I forgot to mention that Black Hat as a symbol of hackers came to us from old westerns, in which the bad guys usually wore such a hat. And I decided that in order to be an effective hacker, I need to choose an appropriate attire. So I can create an appropriate mood for myself, and you can be interested in watching this presentation. So I give the floor to Dr. Loveland (takes off his hat).
Susan Loveland: Thank you, Eva. Before we begin, I want to tell you how the Internet attracts hackers. First, the widespread availability and accessibility of applications - according to a report by the White Hat Association in 2009, approximately 80% of websites have serious vulnerabilities.
Secondly, profitability - attack automation reduces hacker expenses to a minimum, while simultaneously scaling profits to huge sizes. Thirdly, ease of use - smart, creative hackers love to brag about their exploits, and any bad guy can use the results of their work with the help of Google to find hundreds of tools for hacking the right application. Fourthly, anonymity - you can safely break the law, because it is very difficult to find out when the web application was hacked and track down the person who did it. When you physically rob a bank, you must be in the bank, but when you hack a web application, you can work from abroad, where there are no extradition laws and it is relatively safe from the point of view of hacking.
So what do you do first when trying to hack an app? The first step is the most difficult, because you need to understand what this application is, how it works, where its “inputs and outputs” are.

Application infrastructure research includes server identification and port scanning. Then you need to understand the composition of the application: strings and URL request parameters, authentication mechanism, using TLS / SSL, software that is used in the application (PHP, Java), directory structure and session management.
Therefore, I will simply introduce you to the application that will be hacked, and will take you through all the possible vulnerabilities that exist in it. The application that we hack today is called “Faculty Pages”. This project was developed in the classroom of my CS245 web programming course about a year and a half ago.

His idea was that everyone on campus began to use a single set of web pages for each department, since this would look more professional than the pages of a different sample made by employees of individual departments. I spoke with Mark Schonecher to help me and my students with this matter. Mark sent emails to everyone asking what content they would like to see on the web pages of the faculty, and my class developed the “Faculty Pages” that are shown on this slide.
As you can see, there is a main page with content intended for students of the faculty, the “Learning” tab, where teachers can post links to individual courses, the “Scholarships” tab, where you can place the results of scientific activities, the “Education” tabs and “Consultations” .
My students wanted to make it so easy for the faculty members to maintain these pages, so they tied user authorization to the page. After clicking on the link in the upper left corner of the page, a registration form opens in which you need to enter the username of the campus network and the password identifier. After logging in, the same main page opens, but under the word “Information” an “Edit” button appears. After clicking on this button, the teacher can enter the editor panel and add or correct information on the page. These are the main characteristics of the application, which we will try to hack today.

Let's return to our presentation. In hacking, like any other profession, you need equipment, otherwise the work will be ineffective. In order to hack, we need a proxy server.

A proxy server speeds up access to cracking a web page, intercepting all messages between a client computer and a server. You can view all messages, this is very useful, because there is a lot of traffic between the client and the server, which is not visible from the outside. The proxy server allows not only to explore the contents of traffic, but also to change it. In fact, you can completely determine what goes to the server for students who study programming in the classroom.
I want to note that it does not matter how you manage your code on the client side, because a good hacker can always bypass your control by contacting the server that is associated with your browser. Thus, to hack our application, you need a proxy server. To get it is not difficult - you just download any proxy from the Internet.

On the slide, you see three popular proxy servers: WebScarab, BurpSuite, and Paros. You can download any of them for free, install like any other application, and in a few minutes configure your browser to work with a proxy.
The first type of attack that we use today is the Dictionary Attack, or a dictionary search. All attacks of this kind try to find someone's password by going through the list of the most popular passwords and passwords by default, using a set of password dictionaries. If you need such a dictionary, it can also be downloaded from the Internet, it is a public resource.
Before you initiate Dictionary Attack, you need to carefully study the password policy for the application that you are trying to attack. In our case, the “Faculty pages” are tied to the password of Adams University, so we need to find out what kind of password we will select for the hacking application.

The best way to find out what a password looks like is to use the password recovery function, because it gives you a hint. Look what I did - just entered the wrong password, and these guys were so kind that they posted a message at the top of the page describing what kind of passwords I could try. Thus, I find out that in my dictionary, which is used during the Dictionary Attack, I have to try any words not less than 8 characters long, with capital and small letters and numbers.
I must admit that they have worsened the service since the last time I visited the site. Now you can’t just check the functionality of their password, because they changed their policy towards hackers to less friendly, and now, as you can see, they don’t give you any hints when trying to reset the password.
Fortunately, I saved a screenshot of how it looked before, so we know which password to pick up. I think we are ready to give the floor to Eva, so that she shows how an attack is carried out using a dictionary-based search method.
Eve Hacker: thank you, Dr. Loveland! The first thing I'm going to do is go to the login window, which we need to send passwords to the server, and slightly change the URL string. Having done this, I get on the screen an authorization form in which you need to enter a username and password. I have to be able to distinguish the correct password from the wrong one, that is, to see which error the application reports when entering the wrong password.
Since I'm going to pick up Dr. Loveland's password, I type her login sloveland in the username bar, enter the wrong password of 3 characters and click the Login button. After that, the message "Error login" appears. It is very important to see how the application reacts to entering the wrong password.
Next, I need to configure my browser to use a proxy server, so I change the settings for Firefox. Open the tab "Advanced settings", remove the checkbox in the "Use system proxy settings" checkbox and check the "Use manual proxy configuration" checkbox. My proxy will “listen” to port 8080, so it can intercept all requests addressed to the server.

The next thing I need to do is to install the downloaded proxy server, in my case it is Burp Suite. Now you see what this proxy window looks like, which I use during the attack. But I have to go back to the login page and resubmit it to the server. The fact is, there may be a problem due to the fact that I first launched the proxy without reloading the page. If you noticed, our application uses a secure HTTPS connection, and the proxy server does not have the appropriate security certificate. Therefore, I first have to confirm that the application can use an unprotected connection to the proxy and put its URL in the security policy exceptions.

What could have happened if I had not corrected this error? Let me go back and show you this. I again go to the browser settings, and this time I will not rush into setting manual proxy settings that intercept requests. I’ll activate the “Use system proxy settings” checkbox again, because I really need to get the original authorization page first, and, being on this page, I’ll enter my browser settings and again switch to the manual proxy settings.
So, now we have an authorization page that will “talk” to the proxy server. I again enter Dr. Loveland's login and the same incorrect password-fff, which are sent to my proxy server.
Next, I go to the server management page and click the tab, which opens a window for viewing the received request.

Let's see how this request looks in Spider - this is the next tab of the Burp Suite window. To do this, I use the command “send to Spider” and see what the authorization form looks like, it is really interesting. I click on the "Ignore form" button.

And back to the POST request that interests me. We see a request that contains an authorization form, that is, a request to enter user information.

We have several attack methods here - Scanner, Intruder, Repeater, Sequencer, Decoder, Comparer. I am going to use Intruder, so I send him this information using the send to intruder command, and it appears in the window on the “positions” tab. This is all the information that was sent to the proxy server.

It shows a lot of hidden things that cannot be seen on a web page, and highlighted the fields that hackers like to deal with: session ID, session ID, username username and password password used during our attack. The only thing that interests us for Dictionary Attack is the password, so I will clear most of the fields, select the password field and use the add § button to add this field to the dictionary.
This tab will really please you as a hacker, because on it you can select various attack methods using the drop-down menu - Sniper, Battering ram, Pitchfork or Cluster bomb. I will do just that and choose the sniper attack. Next, on the “Payloads” tab, a small setup is performed - we are going to make a replacement for the characters, because I will simply replace the characters in the password with words from the dictionary, after which I have to download the dictionary that I previously downloaded from the Internet. You see the opened dictionary, note that I have removed all words containing less than 8 characters from it, because I don’t want to waste time.

I want to draw your attention to the block on the right with the parameters a, b and e. Let me ask you: when you have to choose a password, where you have to enter either numbers or symbols, have you ever chosen numbers or symbols that look like corresponding letters who are you going to replace them with? You may be tempted to use this method to make it easier to remember your password, but hackers are well aware of this. For example, people often use 4 for A, 8 for B, or 3 for E. Sometimes the letter A is replaced by the symbol @, and the letter b by the number 6, because it resembles it. Thus, in this block, you can configure such matches.
I also know that university passwords require the use of uppercase letters, and since my dictionary contains only lowercase letters, I use the menu below to change the password guessing process rules and modify the key words that will be sent to this hacker tool. I also note that you can use proper names. Since this computer belongs to a scientist, she certainly likes to use punctuation marks, and I provide for this option, noting that you are a drop-down menu.
The last thing to do is to enter the Options tab and enter the address of the site that we want to hack, so here I specify the address of the authorization page.
At the very end, I need to use a tool that will let me know if the password is correct or not, so I’m typing the Login Error parameter so that this phrase appears on the screen to report an error when trying to log in.

Now I can start my attack. I note that being a companion of Dr. Loveland for many years was not a very profitable occupation, so I could not buy the professional version of Burp Suite and used the free version, which was reported by the window that appeared on the screen. So, in the Intruder window, you can see how the hacking process is going on and the substitution of various letters and symbols into the tested password options takes place.

Usually at this time I go to have a cup of coffee or even return to the computer the next day, because it is a rather slow process - as you can see, it started from the very first letter of the alphabet. However, we were lucky - you see the seventh line with the result.

Dr. Loveland chose the password A @ rdv @ rk using characters and letters, so this password fully complies with the requirements of the university and was easy to guess using Dictionary Attack. Therefore, you should be very, very careful when choosing your password.
So, I give the floor to Dr. Loveland, but please note that now I know your password and can access the site on your behalf at any time (takes off the Black Hat).
Susan Loveland: thank you, Eva. I want to ask the audience: how do you think, how common are password attacks? The answer is very, very common! According to experts, about 70% of sites have authorization vulnerabilities. This means that the application developer has made some kind of mistake in the login mechanism, which facilitates hacking the site. But Dictionary Attack attacks are in any case very popular among hackers, and on January 5 last year this method of hacking was used against the Twitter administrator account, which allowed hacking accounts of 33 very famous people, including Obama, and posting hacker jokes on their pages.
I'll tell you about such an anecdote case: when last year I launched a web server for my course, there were only four students, however, in theory, this is a very, very important server, so that over the course of two weeks after its launch, it underwent attacks like dictionary search ”from two different sources. So these attacks are very, very common.
21:35 min
. Adams State University. How to hack websites. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
