How to buy the illusion of safety in the form of children's smart watches
This story is about how I wanted to make my child's life a little safer with the help of new technologies and what came of it. Although the title, I think, you already guessed what will be discussed.
September 1 was approaching, and I, as the father of the future first-grader, wondered how to make the first days of my child in school go as calmly as possible for him and for my wife and I.
I think that there is no person who has not heard of such a new gadget as a children's smart watch. The market is simply flooded with numerous device options, usually made in China. The prices and functionality of these devices vary, but the best of them include such a wide range of functions as a phone, GPS tracker, instant messenger, camera, pedometer, and of course the clock. According to manufacturers, this gadget is designed specifically for children and includes child safety features. So I thought, so I began to choose the appropriate option on the Internet. As a result, I bought a FixiTime 3 watch from Elari .
The functionality of this watch was impressive:
- GPS / LBS / Wi-Fi tracking
- 2 cameras, access to the watch camera from a connected smartphone
- support for incoming and outgoing voice calls, including hidden
- voice chat
- pedometer
- Well, Fixies inside, as without them

All this rich set of watch features convinces parents that they get, if not complete, then quite substantial control over their child. But, on the other hand, devices with such functionality should reliably protect the data of their users. Moreover, such users are children. It is scary to imagine what could happen if an attacker gains access to a child’s device and can monitor it.
Tormented by such thoughts, I decided to check how safe it is to use the watches I bought.
After I installed the Elari SafeFamily application from the Apple Store and added the watch via QR code to it, I launched Fiddler on my laptop and started analyzing traffic. The application sent data to the server http://wherecom.com . The first thing I noticed was that the usual HTTP protocol was used, there was no traffic encryption, neither HTTPS nor SSL Pinning . An alarming thought crept in me that the matter would not end there.
And so it turned out. Continuing to analyze requests and substituting parameters in them, I discovered the first vulnerability. So, request at
http://api.wherecom.com:8099/umeox/api/holder/detail.json?holderId=111111&monitorId=222222 He returned detailed information about the child: his name, date of birth, height, weight, what class he goes to, phone number, parents' email, photo of the child, and most importantly - the QR code of his watch. Knowing the latter, anyone could add this child’s clock to their application and follow him in the same way as his parents do. The essence of the vulnerability was that by changing the value of the monitorId parameter in the request up or down, we get the data of another child.
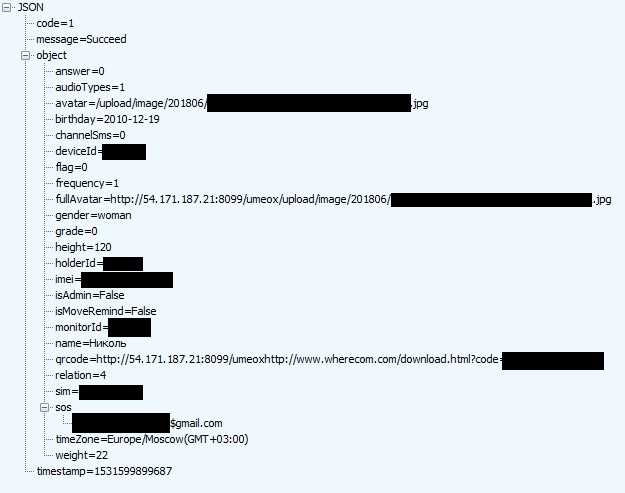
So, in terms of experiment, I managed to add several devices of other children to my application.

Continuing to analyze traffic, I found a few more queries, the substitution of which allowed us to get various user data, such as GPS history, parent data (names, phones, emails). But all this information was already available thanks to the first vulnerability with a QR code. The only difference was that by adding a QR code to the application, the attacker would give himself away, since this information was displayed in the parents application. Fulfilling other vulnerable requests, the attacker could go unnoticed.
Among other things, the operation of these vulnerabilities was simplified by the fact that all this data was accessible without any authorization to the API from any device, which says a lot about the quality of the developed software and its relation to security issues in general.
It turns out that the manufacturer, while developing a device designed to increase the safety of the child, does not really care about her, as such. Thus, several hundred thousand devices, not only from Elari, but from all devices manufactured by the Chinese company Wherecom, were threatened.
Further analysis showed that service pages with server statistics are sticking out, admin panel phpMyAdmin, page phpinfo.
Therefore, I stopped further analysis and began to look for ways to inform the application developers and the watch manufacturer about the vulnerabilities found. After all, if you do not close them, using a watch becomes unsafe, to say the least. And if I can return the watch to the seller, then what should the other users do, not even suspecting what is happening? I will not be able to inform all owners that their children are not adequately protected. More precisely, I can do this, because I have access to all the phones and emails of my parents, but this path is illegal, unethical and quite time-consuming.
The manufacturer of watches, as you might have guessed, was the Chinese company Wherecom technology limited . According to the information posted on their website, they are located on the territory of the Science & Technology Development Institute of China. You can think a lot about how it turned out that such an important product designed for child safety and developed on the territory of a scientific institute turned out to be of such poor quality. In fact, we all know how cheap, and sometimes free, is student labor. As a result, we have what we have.
Further, I began numerous attempts to convey information about existing vulnerabilities to responsible persons. First, I sent a letter to the support of the Russian representative office of Elari. But there, having created an application automatically, it was closed the next day without any explanation.

Sending a letter to Wherecom support, I also did not receive a response after a few days. Then there were Facebook messages on the Wherecom official page, negative feedback on the online store website, Linkedin messages to Wherecom employees. As a result, both the manufacturer and the vendor heard me, though I had to spend more effort than on the vulnerability search itself.
So they began to gradually eliminate weaknesses and close vulnerabilities. Enabled authorization to the API. It turns out that it was disabled for some reason, which made exploiting vulnerabilities as simple as possible.
At the moment, a little more than a month after the first contact, all the vulnerabilities I found have been fixed, it remains to switch to HTTPS and add SSL Pinning to the application. But this is only that part of the gaps that I was able to discover as a result of a not very lengthy analysis. And who knows how many more such vulnerabilities in their devices. Yes, and how many such low-quality devices are sold all over the world and no one conducts a security audit. Except black hackers of course.
Upd. 09/04/2018
Now the application works through HTTPS, but SSL Pinning has not yet been added.
