MIT course "Computer Systems Security". Lecture 5: "Where Security Errors Come From", Part 1
- Transfer
- Tutorial
Massachusetts Institute of Technology. Lecture course # 6.858. "Security of computer systems." Nikolai Zeldovich, James Mykens. year 2014
Computer Systems Security is a course on the development and implementation of secure computer systems. Lectures cover threat models, attacks that compromise security, and security methods based on the latest scientific work. Topics include operating system (OS) security, capabilities, information flow control, language security, network protocols, hardware protection and security in web applications.
Lecture 1: “Introduction: threat models” Part 1 / Part 2 / Part 3
Lecture 2: “Control of hacker attacks” Part 1 / Part 2 / Part 3
Lecture 3: “Buffer overflow: exploits and protection” Part 1 /Part 2 / Part 3
Lecture 4: “Privilege Separation” Part 1 / Part 2 / Part 3
Lecture 5: “Where Security System Errors Come From” Part 1 / Part 2
Professor Nikolai Zeldovich: Good afternoon, I want to introduce you to our guest from the company iSec Partners, who will tell you about the security of computer systems in the real world.
Paul Yang: good afternoon, my name is Paul Ian, I graduated from MIT in 2004, received a Master's degree in engineering and computer science and until 2010 I worked at Oracle. Now I work as a technical director at iSec Partners. Previously, I did not even know that such companies exist. Our company is engaged in computer security consulting, penetration testing (pentesting), network security, we study hacker programs, find various vulnerabilities and eliminate them.

I decided to tell you about it, because I know that many students of your specialization want to make a career in the field of computer systems security. The plan of today's lecture looks like this:
- What are “security bugs”?
- trusting relationship;
- examples of errors encountered in real life;
- Operation Aurora;
- Stuxnet;
- I like security issues, what should I do?
Let's see what the researchers think about vulnerabilities. I want you to fully understand where the vulnerability came from, after you discovered it. That is, you must find what caused it. It is important to understand how vulnerabilities affect a system and how it interacts with its other components.
So let's start by looking at what security mistakes are. But before we start talking about it, we first define what the very concept of security means.
Ivan Arch said: "The system is safe if it behaves exactly as intended and does nothing else." Systems are becoming more and more complex. If we are talking about operating systems, who can say what they are exactly intended for and what specifically allow to do?
Therefore, it is necessary to study all possible types of attacks. Knowing what attacks exist, you can develop key security goals. Therefore, the first steps in the field of security should be the definition of a security model and the definition of a threat model.
As an example, consider how the TSA Transport Security Administration defines a threat model. The security objective of Logan International Airport is to prevent the entry of prohibited items, such as shaving foam, onto the aircraft. The threat model consists of two points:
- What are the possible ways of penetration of prohibited items in the airport?
- Where are the “entry points” of these things to the airport?
How can you carry prohibited items past security? How do you try to attack their security system? You can carry them where there is no check, using the privileges of a VIP-passenger, hide them among other things or use the service of other airlines to deliver prohibited things to the airport.
I have always been shocked by the fact that in Logan the luggage arriving from other airports does not show through on the monitors. That is, you can send a prohibited substance or object from another airport, it will fly to Logan, and there you will receive it. Thus, airports with a less strict security system are threats to Logan’s advanced security system, and nothing can be done about it. Therefore, the critical point of building a threat model is understanding what you are specifically speaking against. I note that many engineers do not care properly.
Engineers create security bugs and find them. The goal of engineers is to find as many flaws as possible and minimize the possibility of damage to the system.
The approach to achieving this goal must be very careful - it is necessary to capture the attention of all the parameters of the security system, or at least to find elements easily accessible to criminals.
Ways to achieve the goal are to study the source code, use the tools for debugging the application and engineering. In addition, the necessary money for the tools and staff.
Usually, software developers are concerned about the functionality and capabilities of their product, rather than its security. Everyone buys software because of its capabilities, and not because of its security. Therefore, security always remains in second place and developers start to take care of it only after the product suffers from intruders. Usually, engineers see only a small part of the "mosaic", they do not pay attention to the technical details. Can you answer the question how many lines of code does Linux 2.6.32, Windows NT4, and Adobe Acrobat contain?
The correct answers in the order of listing programs - from 8 to 12.6 million lines, 11-12 million and 15 million. Indeed, it is usually surprising to everyone that Acrobat contains more lines of software code than “Linux” and “Windows”. Thus, even software that we consider simple is, in reality, extremely complex.
The following categories of people are interested in security issues:
- engineers;
- criminals;
- security researchers;
- penetration testers (pentesters);
- governments;
- hacktivists;
- representatives of academia.
I selected only 6 categories, but probably more. Consider what interests the first category of people - criminals.

Their goal - the resources with which you can seize other people's money (botnet, CC # s, spamming the "letters of happiness") and at the same time do not fall behind the bars. To achieve the goal, they use the latest hacker exploits that exploit software vulnerabilities. They do not need data access privileges, but simply steal them using the vulnerabilities left by the developers. Most often, the objects of attack are credit cards and everything connected with them. Therefore, criminals get access to other people's money using money, buying data from hackers, or using the Black Box testing method. This method of testing "software" on the functional specifications and requirements, without using the internal structure of the code or access to the database. In this case, the source code is disassembled into components, which allows to detect gaps in the protection of the program.

This technique allows you to penetrate the database of credit cards, "hacking" payment systems of various stores.
The next category is voluntary security researchers, a certain kind of hackers.

Their goal is to make the public aware of them, to be printed about them in the newspapers, and friends to respect or admire them. Their occupation does not require thoroughness, no one will shame you if you have not found vulnerabilities or ways to overcome it. They gain access to security systems through amateur tools and casual communications with engineers working in large security companies or developing software, and lawyers are often the source of information.
The third category, which is most useful in security, is penetration testers (pentesters).

The point of their work is to ensure the safety of customers and users of the software. They find the vulnerabilities that criminals want to exploit before they are discovered by criminals, and help developers eliminate these vulnerabilities.
The thoroughness of their work is to cover all the details and nuances of the system, to find unprotected public places and vulnerabilities that are subject to the greatest interference, not corrected or hacked.
To do this work, they need access to developers, access to the source code, and all sorts of permissions.
Next come the governments of different countries. Security worries them in terms of attacks, espionage and the protection of their own country from such actions of the enemy. They are supported by reliable exploits that can detect and exploit vulnerabilities, and they use money, talent, and the time they can buy with money to gain access to security systems.
The next to last group is hacktivists. These are anonymous hackers, their activity is a mixture of hacking and protest, aimed against the infringement of the right to freely exchange any information. These are socially-oriented hackers, usually cracking systems not for the sake of their enrichment.
Their goal is to do “something good”, in their understanding of the word, and not to go to jail for it. Sometimes I agree with what they do, sometimes not.
They use the most advanced exploits and penetrate security systems thanks to their own talent and a wide variety of “goals” to apply their skills. They exploit all possible vulnerabilities, and if they can steal credit card numbers, they will steal them.
The last group is representatives of science. This is an interesting field of activity in which Professor Nikolai Zeldovich works. It examines the long-term features and functional problems of programs. People of science find common flaws and other common problems, such as errors in the use of firewalls or encryption, trying to make the software more secure. Usually they have enough time and talent for their research, and the thoroughness of their work is ensured by the depth of their approach.
They gain access to security systems through the creation of new things and the Black Box. There is a difference between theoretical developments and their implementation in practice, but for the most part they act in the same way as national governments, that is, they are engaged in very ambitious projects.
All these groups of people use a similar technique and are looking for the same thing: vulnerable systems. If they have access, they review the source code, use interviews with engineers, or perform testing in a controlled environment. If they don’t have access, they test the Black Box, do fuzzing technology (for example, enter random data and watch how the system reacts), do a technical copy of Reverse Engineering (using binary code files) and do social engineering.
"Fuzzing" are subject to many complex software systems, for example, the same Acrobat Reader- here the possibility of buffer overflow is checked with the help of specially created bulk documents in .pdf format. Such a document is “driven” into “Acrobat” to check whether it is capable of causing a system crash.
Social engineering is the easiest and fastest way to find security problems by hacking social media accounts.
So let's dive into the subject of the lecture and look at the vulnerabilities we are looking for.

Engineers often make mistakes about how systems should work and how they will work after creation. An example of a catastrophic software error leading to the death of people is a program for a Therac-25 radiation therapy device .The incorrect operation of the security system of the apparatus led to the fact that at least 6 people received huge doses of radiation, two people fatal. I will tell you about it in general, without mentioning the details and principles of operation of this feed.
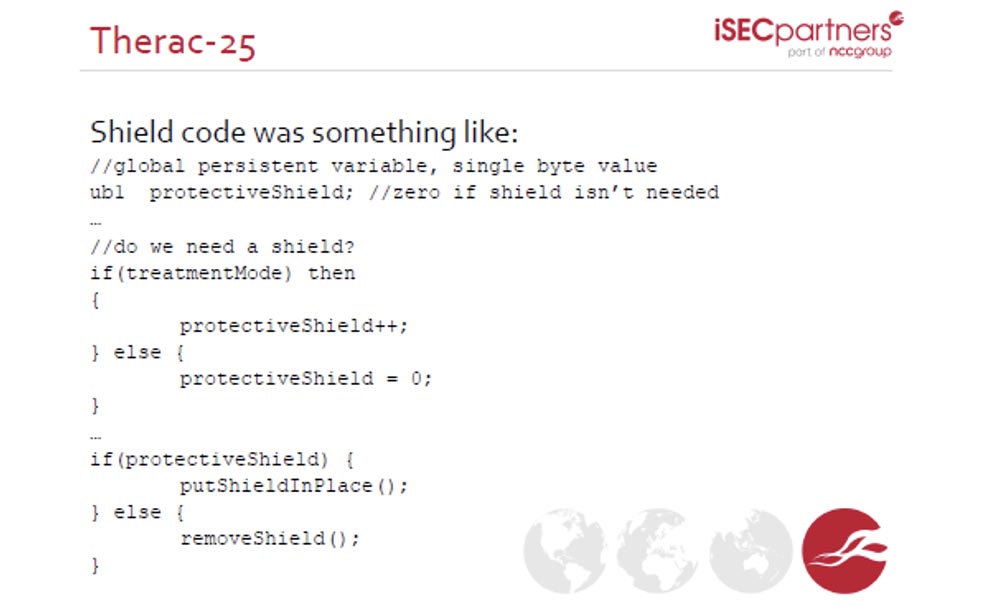
The software of this medical device provided for two modes of use of the irradiator. The first, X-Ray image , the mode of electron scattering, in which radiation exposure was minimal, did not involve the use of a protective focusing screen. The second mode, Radiation Treatment, provided a powerful irradiation regime in which the sore spot was subjected to a directed 25 MeV radiation beam. For this, a protective focusing screen was placed between the patient and the radiator.
The next slide shows what the program code that controls the protective screen looked like. You see that in one line were single-byte data telling whether or not to install a protective screen in place. If this value was 1, the screen was set; if it was 0, the screen was removed. The problem was that inside the program, when entering a parameter equal to 0, for example, if the doctor manually adjusted the radiation power to 0, the radiation value was divided by 0. Since the division by 0 is an invalid operation, a buffer overflow occurred, the program crashed and radiation power automatically took the maximum possible value in the absence of a protective screen.
Here, the developers used the erroneous assumption that in the Radiation Treatment mode the parameter of using a protective screen will always take a non-zero value, a buffer overflow will never occur and the program will never fail. As a result of this incorrect assumption, people died because they received a fatal radiation burn during a screenless session in Radiation Treatment mode.
Upon learning of this case, my classmate said: "I have concluded for myself that I will never write medical software."
Wrong prerequisites for software development can bring great harm, for example, the amazon.com account system.
This online store allows the following:
- You can add a credit card or an electronic mailbox with a name and physical address to your account;
- Amazon gives you the ability to change your account password through a registered mailbox;
- Amazon allows you to see the last 4 digits of your credit card number;
- Apple gives you the ability to log into your account using the last 4 digits of your credit card number;
- Gmail allows you to change your Apple account through a Twitter account.
What wrong prerequisites allowed to create this vicious chain? Incorrect security policies, expressed in the first and fourth paragraphs. The conclusion from here follows: the components affecting your system are often beyond your attention (Facebook, Amazon, Apple). Therefore, an attacker can capture your credit card information through an account on amazon.com using the capabilities of these three independent systems. This can be considered a complete threat model.
Therefore, answer the question: is your password to your personal mailbox stronger or weaker than the password you use for online banking?
I see how many people raised their hands. And now raise those who have a password for banking operations stronger than the password from the mail. I see that there are more. And this is wrong.
People believe that online banking is a serious matter, and a stronger password is needed here. But they forget that access to the payment account is carried out through an electronic mailbox. It is the mail that should have the most reliable password, and not vice versa.
If you want to become an engineer who develops computer systems, you need to think like a security researcher thinks:
- What prerequisites should be used to ensure safety when developing a system design?
- what prerequisites are wrong?
- What can you break if the premise is wrong?
The last point helps to develop the system design in such a way that even if the system fails, your kernel will be protected.
Managing memory is difficult.

As an example, I will give you a simplified scheme for establishing a secure communication protocol:
- avoid reviewing, or re-establishing contact;
- Alice: “Bob, if you are here, say“ boo ”!
- Bob: “Boo!”
- as a result, Alice and Bob believe they know each other very well.
Technically, this protocol looks like this:
- Alice sends a packet containing ping;
- the packet has a certain data length;
- Bob returns a packet of the same length back.
In this case, Bob parses the data sent by Alice:

Looks at the length of the data and their location in the buffer. He then prepares Alice for a response, adding 2 bytes to the length of Alice's request, copies the new length of Alice's request to the response and sends it back to her:
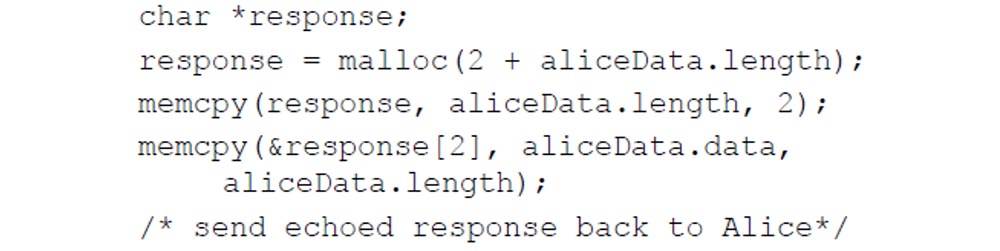
Do you see any problem here? Where is the vulnerability here?

It is enclosed in the second and fourth lines of Bob’s answer. The size of the data transmitted by the user may not coincide with the actual size of the data. A TSL handshake protocol uses SSL open encryption protocol. About 60% of servers available on the Internet work this way. Bob, that is, the server, never checks the actual length of the received data. Due to the fact that the server adds 2 bytes, the user can read about 64 KB of server memory data, including private keys.
Now that we have found this error, how can I fix it? The more people know about it, the more information is leaked. Therefore, as soon as information about vulnerability is disclosed, it will be immediately used. So, to protect the need to correct the situation as soon as possible.
Sometimes companies turn to us and say that they have discovered such a vulnerability and how it can be fixed. We answer them: “No, you just need to change the encryption keys immediately.” Therefore, it is imperative to monitor differences arising in Open SSL.when sharing data.
From this we can conclude that it is not too smart to use the keys of the TSL security level protocols for equipment that is constantly exposed to external influences, and that fundamental protocols have security problems.
I would like to note that the largest state funds and organizations dealing with security issues often consider the consequences of the zero-day threat, that is, the threat of vulnerability, for which no patches exist.
And now we will consider a question of unexpected, unforeseen interaction. This is what allows attackers to receive money in several unexpected ways.
In 2014, the attackers managed to create add-ons of the Yahoo browser.that botnet infected users' computers with malware. They used specific errors of Java-scripts that allow installing 6 types of malicious code on computers.
One of the vulnerabilities was that incorrectly isolated user input data was executed by the browser as java-scripts that redirected users to a set of malicious programs called Magnitude through the XSS vulnerability . This Magnitude used the latest zero-day vulnerabilities at Yahoo , which caused the virus to infect 27000 computers per hour from December 30, 2013 to January 3, 2014. In this case, the use of a botnet was very effective.
The solution to the problem was the mechanism for disabling the execution of java-scripts on the browser page and the introduction of the click-to-play function in the Chrome browser.
Another type of attack uses the principle of Confused Deputy - this is a suspicious trust of applications to received data. Under this definition falls quite a wide range of security issues. This type of vulnerability is called Cross-Site Request Forgery (abbreviated as CSRF or XSRF ), which means “cross-site request forgery”. Faking an authorization request forces you to do what you are not going to do.
Security researchers from Microsoft and people of science have considered making free purchases on the Internet. This feature appears when using a third party acting as a payment system with the cashier service Cashier as a Service . You know many sites that offer to make a payment through “foo ...”, you click on such a link, and you are redirected to the payment system site.
Three people are involved in the purchase process: the seller, the CaaS payment system provider and the buyer cheater. Relations between the three parties pass through the user. The next slide shows the scheme of such a purchase.
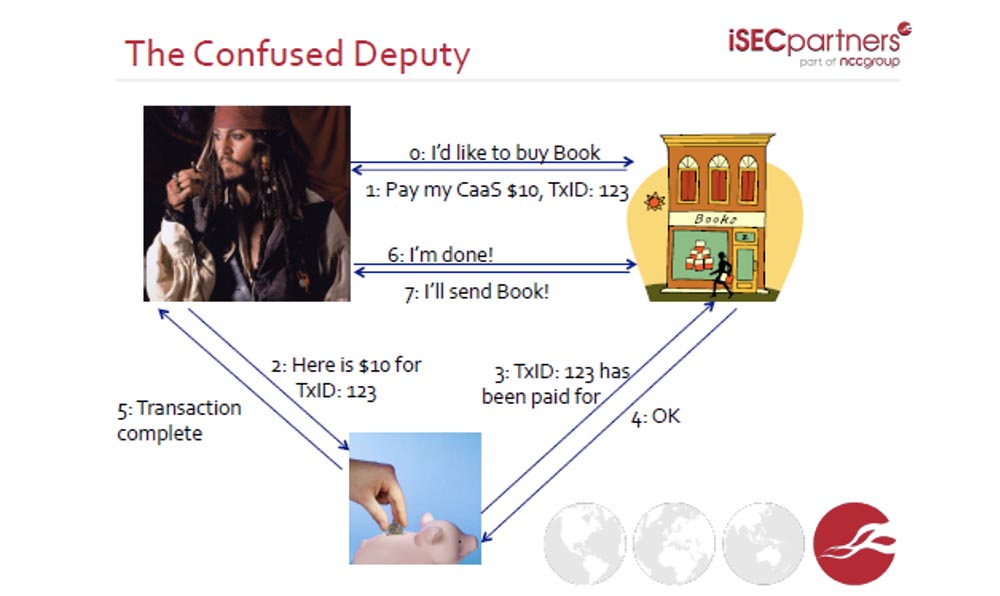
You contact the owner of the online store and say you want to buy the book. He answers to you that for this you need to pay $ 10 to his CaaS payment service for operation 123. You call the “cashier” and say: “that's $ 10 for TxID: 123”. CaaS informs the store: "payment made." The store says, “OK.” The transaction is complete.
Does anyone see how you can attack this payment system? What is the vulnerability? That's right, there is no evidence that the amount of the payment made is the same as the cost of the goods! If you pay attention to operations 3 and 4, you will see that there is no information about what amount was actually transferred. The next slide shows how you can make a virtually free purchase using a system vulnerability - instead of $ 10, the buyer transfers only $ 1, and the transaction is still considered confirmed.

The wrong premise in this scheme is that the seller believes that something is linking the amount of the payment to the transaction, but in reality it is not. The solution to this problem can be one thing: read the paper, check every operation, because a lot of things can and do not happen correctly.
Even more instances of unforeseen interaction arise when managing passwords.
The number of successful user password attacks is constantly growing due to an increase in computing abilities of computers, an increase in the speed of calculations and the use of a large number of real passwords for hacker user dictionaries. This does not mean that users use passwords like “aaaaaa” or “aaaaab”, but often different users use the same passwords. There is a situation when a large number of cracked passwords allows hackers to create more voluminous dictionaries for hacker software, which, in turn, contributes to cracking even more passwords. Here there is a feedback, and the technique of password cracking is constantly being improved.
Two-step authorization is good, but it is not used everywhere. On the Internet, there are still hundreds of applications that do not use this approach. You can generate a really strong password, but not use it everywhere. You need to create a strong, unique password for each site you work with. Password managers can create really strong passwords. Some browsers' plugins are a good way to ensure security, allowing the user to manage login and password generation.
Browser extensions themselves are interesting things.

Some plugins allow you to securely interact with different domains, and if you switch from one domain to another, they automatically clear the cookies and stop the data exchange with an unfamiliar domain. An example would be the Cloud To Butt Plus plugin for the Chrome browser . It is located on the browser panel and allows you to securely interact with any domain.
Creating a secure browser is a difficult task, because all the components that make it work, such as java-script or Flash-player, must implement the same original security policy. Browser components should eliminate the possibility of uncontrolled interaction and the impact of one domain on another. An example is our website www.isecpartners.com , which does not allow us to read your email address when you log in to the site, and does not impose our cookies on you.
However, many browser extensions do not provide security because they interact with all Internet pages without preventing the consequences of the impact of these web pages on your computer. Therefore, the security vulnerability of extensions can “break” your browser.
Browsers are created by leading engineers of large companies, for example, Googletherefore, they are very expensive. And extensions for browsers are created by third-party developers. Extensions are becoming increasingly popular, and attackers are taking advantage of this. They contact the developers and say: "hey, sell me this $ 10,000 extension"! After that, the attacker turns the add-on into malware by modifying the web page scripts, and then distributes or sells this modified extension to users for free. After the user installs such an extension, he will be attacked. An example is the fact that thousands of Chrome users suffered in January 2014 after spammers bought the extension and turned it into an exploit.
Returning to the discussion of browser extensions that manage passwords. They provide security by pursuing the following goals:
- secure sending of passwords to third parties;
- general user application security;
- ease of use;
- generating strong passwords;
- secure password storage.
Our company is engaged in research of the first three goals. Answer, which of you is using password managers? Just a couple of people. And how many of you use the program to store passwords 1password or LastPass and the service to hide the address of your email mailbox Mask Me ? Let's look at these programs.
The 1password program does not really provide application security, because it offers a silent update feature over HTTP using unsigned packages. In addition, it runs as a privileged computer user.
At the same time, the LastPass feature only provides the auto-complete and auto-fill functions for filled-in forms., Mask Me has only the form auto-complete function, and 1password does not have these functions at all. Automation functions greatly facilitate the ease of use of the program, since the user does not need to enter a lot of data each time, but also increases the possibility of using malicious exploits if the system has a vulnerability.
Next, I will tell you about the known areas of application of attacks, that is, about the components and phenomena that are attacked most often. These include:
- differences between HTTP and HTTPS;
- filling in credentials in iframes;
- cross-domain requests;
- differences between subdomains (subdomains);
- login page identification.
The difference between an unsecured HTTP connection and secure HTTPS plays a big role in ensuring security. If you do not pay attention to the address appearing in the browser line, you can easily get to the phishing site instead of a secure site. At the same time SSL stripping attacks can easily “unlock” your password.
You can also use redirection attacks when you are redirected from https: // example.com to a dangerous site http: // example.com . If the password manager uses forms auto-complete, then you can register on the fake page. Mask Me Programhas a vulnerability, because it uses not only autofill, but also sending a completed form, which will help an attacker to steal your password.
33:35 min.
Continued:
Course MIT "Security of computer systems." Lecture 5: "Where Security Errors Come From", Part 2
Full version of the course is available here .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read aboutHow to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
