More than DDOS protection
Hello everybody!
DDOS attacks are constantly coming to the sites of our users, and to our services. All this time we have been working on each problem in semi-manual mode, but attacks are becoming more complicated and more frequent, and artillery of a different level is needed to further repel attacks.
Over the past year, we have studied in detail the issue of means of protection against DDOS attacks. This post is about how we looked for a reliable, effective and convenient solution “out of the box”.

Like all curious people, we started by exploring the market for existing protection devices. We have chosen the main, most famous manufacturers:

As we chose,
we are not backbone providers and we did not want to waste time digging through hundreds of DDOS protection parameters, so one of the most important qualities was the ease of configuration and management.
In addition, we need high quality filtration. Needless to say, the quality of the work of sites directly depends on this, and in general, this is the main task of the device.
We contacted representatives of development companies in Russia, described our tasks and requested test samples. We have no problems with the “necessary” traffic - DDOS “comes” to us every day in one form or another.

Arbor is the first thing we turned our attention to. At the beginning of the year at one of the international conferences, we received a boost of marketing data in their sections. At first glance, everything looked too beautiful =), let's see what happens next.
Just at that time, they had a Pravail product for the corporate segment (before that there was only Peakflow for backbone providers). That was exactly what we needed.
In April, Kirill Kasavchenko came to us , who works with clients at EMEA, showed us Peakflow in action (which strengthened our opinion about the redundancy of the system for us), told us a lot of interesting things about DDOS attacks, and we parted while waiting for the Pravail test.

Two months later he arrived! In fact, this is an Intel 2U chassis with tricky bolts, curious of course, but we won’t break anything.
Immediately taken to the data center, screwed, connected, raised the IP and it worked. Our system has a server (Protos), where we protect users from attacks by our own methods, there is always spurious traffic, or rather, before we did not let all the server traffic through Pravail. Works!
To protect systems, groups are created to which the corresponding rules apply and that's it. It remains only to follow the charts. There is a typical setting and a little more detailed, but as a rule - basic values are enough to work. We tested its operation on one of our DNS servers, on MX and of course the web. We were satisfied with his work on all services.
Perhaps the most important minus is the price. Pravail dear, Peakflow - space dear (almost like Curiosity =).

The system that was sent to us consisted of three devices: ADS 6000 (the protection module itself), ADS-M1600 (control device) and NTA-2000 (analyzer).
Together with three devices, three people came from China and two from Moscow (not translators). Then the first suspicions began to creep in.
We met at the data center on the morning of May 16, exchanged greetings and went to do the installation of the equipment. Before installation - a brief meeting was held, where we drew a wiring diagram, agreed on the details and went to the hall.
To begin with, we decided to make the usual simple protection scheme, nothing special:
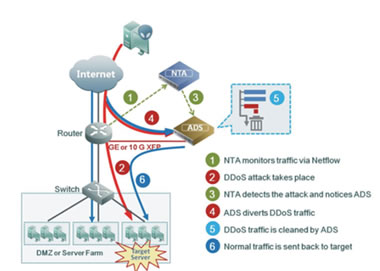
After three hours of hard work, our friends started to run out of batteries due to the Great Wall, and the charge was one for three. Two hours later they connected their colleague “from there” and there were six of our guests.
As a result, after 6 hours after various manipulations with the optical modules (they have everything with them =) and flashing the iron with different firmware, the lights blinked as it should and the circuit still rose. Confused only the Chinese flag on the front side of the buildings. But against the background of the first victory - these thoughts departed.
Hurrah. To the office, adjust and enjoy the results!
In the office. It's time to get to know the interface face to face. Sucks. Some windows with text in chinese. The graphics are terrible. In half an hour I already wanted to finish everything, but out of respect (solidarity?), We carefully studied all aspects of this system. Things never got to traffic analysis. Also an experience.
The first impression is the most important, we understand this - they apparently do not.
A smile ofhorror of joy on my face - everything will be fine!

Honestly, I don’t understand why he looks at me like that, he can be hungry.
The next day, we removed all the equipment and sent back.

The perimeter came to us in the form of an HP 1U server on two opton,shamehonestly, we couldn’t even figure out its interface, so a more or less detailed story will not work. According to rumors - rewritten by "our" programmers Peakflow, it is also used in RT.

We were sent a fairly powerful DefensePro 12412 device (comparisons here ).

He is so harsh that we could not even guess what exactly is inside. Installation and connection to our system went smoothly.
To manage the device, you must deploy the virtual machine to VMWare, through which access is made. At the time of testing, the ability to work with the device was only through a Java client ( APsolute Vision ).
It seems that everything is fine, but when we started to deal with its interface, we felt bad =) And the point is not even the number of settings, which, due to the functions and purpose of the device, turned out to be a lot - the matter is the speed of the control interface. It turned out to be sooooo slow. When switching between sections, you could pour yourself coffee, then there was a lot of coffee.
In addition, the interface constantly fell off at some mythical timeouts and, unfortunately, turned out to be not at all beautiful. Even experts from Moscow and Tel Aviv who arrived to help us were surprised at the brakes of “our” system, agreed that it needed to be updated and we had the “wrong” VMWare image, but it didn't matter much.
Conclusion
We will not talk about what is worse or better; we have made a decision for ourselves. And only you can draw conclusions.
DDOS attacks are constantly coming to the sites of our users, and to our services. All this time we have been working on each problem in semi-manual mode, but attacks are becoming more complicated and more frequent, and artillery of a different level is needed to further repel attacks.
Over the past year, we have studied in detail the issue of means of protection against DDOS attacks. This post is about how we looked for a reliable, effective and convenient solution “out of the box”.

Like all curious people, we started by exploring the market for existing protection devices. We have chosen the main, most famous manufacturers:

- Arbor Networks - USA
- NSFocus - China
- MFI-software - Russia
- Radware - Israel
As we chose,
we are not backbone providers and we did not want to waste time digging through hundreds of DDOS protection parameters, so one of the most important qualities was the ease of configuration and management.
In addition, we need high quality filtration. Needless to say, the quality of the work of sites directly depends on this, and in general, this is the main task of the device.
We contacted representatives of development companies in Russia, described our tasks and requested test samples. We have no problems with the “necessary” traffic - DDOS “comes” to us every day in one form or another.

Arbor is the first thing we turned our attention to. At the beginning of the year at one of the international conferences, we received a boost of marketing data in their sections. At first glance, everything looked too beautiful =), let's see what happens next.
Just at that time, they had a Pravail product for the corporate segment (before that there was only Peakflow for backbone providers). That was exactly what we needed.
In April, Kirill Kasavchenko came to us , who works with clients at EMEA, showed us Peakflow in action (which strengthened our opinion about the redundancy of the system for us), told us a lot of interesting things about DDOS attacks, and we parted while waiting for the Pravail test.

Two months later he arrived! In fact, this is an Intel 2U chassis with tricky bolts, curious of course, but we won’t break anything.
Immediately taken to the data center, screwed, connected, raised the IP and it worked. Our system has a server (Protos), where we protect users from attacks by our own methods, there is always spurious traffic, or rather, before we did not let all the server traffic through Pravail. Works!
To protect systems, groups are created to which the corresponding rules apply and that's it. It remains only to follow the charts. There is a typical setting and a little more detailed, but as a rule - basic values are enough to work. We tested its operation on one of our DNS servers, on MX and of course the web. We were satisfied with his work on all services.
Perhaps the most important minus is the price. Pravail dear, Peakflow - space dear (almost like Curiosity =).

The system that was sent to us consisted of three devices: ADS 6000 (the protection module itself), ADS-M1600 (control device) and NTA-2000 (analyzer).
Together with three devices, three people came from China and two from Moscow (not translators). Then the first suspicions began to creep in.
We met at the data center on the morning of May 16, exchanged greetings and went to do the installation of the equipment. Before installation - a brief meeting was held, where we drew a wiring diagram, agreed on the details and went to the hall.
To begin with, we decided to make the usual simple protection scheme, nothing special:

After three hours of hard work, our friends started to run out of batteries due to the Great Wall, and the charge was one for three. Two hours later they connected their colleague “from there” and there were six of our guests.
As a result, after 6 hours after various manipulations with the optical modules (they have everything with them =) and flashing the iron with different firmware, the lights blinked as it should and the circuit still rose. Confused only the Chinese flag on the front side of the buildings. But against the background of the first victory - these thoughts departed.
Hurrah. To the office, adjust and enjoy the results!
In the office. It's time to get to know the interface face to face. Sucks. Some windows with text in chinese. The graphics are terrible. In half an hour I already wanted to finish everything, but out of respect (solidarity?), We carefully studied all aspects of this system. Things never got to traffic analysis. Also an experience.
The first impression is the most important, we understand this - they apparently do not.
A smile of

Honestly, I don’t understand why he looks at me like that, he can be hungry.
The next day, we removed all the equipment and sent back.

The perimeter came to us in the form of an HP 1U server on two opton,

We were sent a fairly powerful DefensePro 12412 device (comparisons here ).

He is so harsh that we could not even guess what exactly is inside. Installation and connection to our system went smoothly.
To manage the device, you must deploy the virtual machine to VMWare, through which access is made. At the time of testing, the ability to work with the device was only through a Java client ( APsolute Vision ).
It seems that everything is fine, but when we started to deal with its interface, we felt bad =) And the point is not even the number of settings, which, due to the functions and purpose of the device, turned out to be a lot - the matter is the speed of the control interface. It turned out to be sooooo slow. When switching between sections, you could pour yourself coffee, then there was a lot of coffee.
In addition, the interface constantly fell off at some mythical timeouts and, unfortunately, turned out to be not at all beautiful. Even experts from Moscow and Tel Aviv who arrived to help us were surprised at the brakes of “our” system, agreed that it needed to be updated and we had the “wrong” VMWare image, but it didn't matter much.
Conclusion
We will not talk about what is worse or better; we have made a decision for ourselves. And only you can draw conclusions.
