About 500 million IoT devices are susceptible to attacks through DNS spoofing.

Information security researchers at Armis recently reported that about 500 million IoT devices are susceptible to attacks through DNS re-binding. In the course of this attack, the attacker binds the victim’s device to the malicious DNS, which subsequently allows a variety of operations to be performed. So, the attack allows you to subsequently launch malicious processes, collect confidential information or use the IoT device as an intermediate link.
In short, the attack itself occurs in the following scenario:
- The attacker sets up his own DNS server for the malicious domain.
- The attacker provides the victim with a link to the malicious domain (at this stage phishing, IM spam, XSS or masking the malicious link in advertisements on popular and completely “white” sites is used).
- The user browser makes a request to obtain the DNS parameters of the requested domain.
- The malicious DNS server responds, the browser caches the address.
- According to the TTL parameter within the primary response of the DNS server in one second, the user's browser performs a repeated DNS request to obtain an IP address.
- The attacker's DNS responds with a target IP address.
- The attacker repeatedly uses a malicious DNS server to access all IP addresses of interest in the attacked network to achieve its goals (data collection, execution of malicious code, and so on).
Also, the attack mechanism will be explained in detail in the video from Armis experts:
The most vulnerable to attack the IP camera. According to experts, such an attack can be carried out on 160 million such devices. In addition, through the DNS substitution, you can get access to 165 million printers, 124 million IP-telephony points, 28 million Smart TVs, 14 million switches, routers and Wi-Fi access points and 5 million media streaming devices.
According to Statista.com, the number of IoT devices connected to the network from 2009 to 2017 increased from 0.9 billion units to 8.4 billion units. In 2018, growth is projected to 11.2 billion devices. By 2020, projected 20 billion smart devices connected to the network.
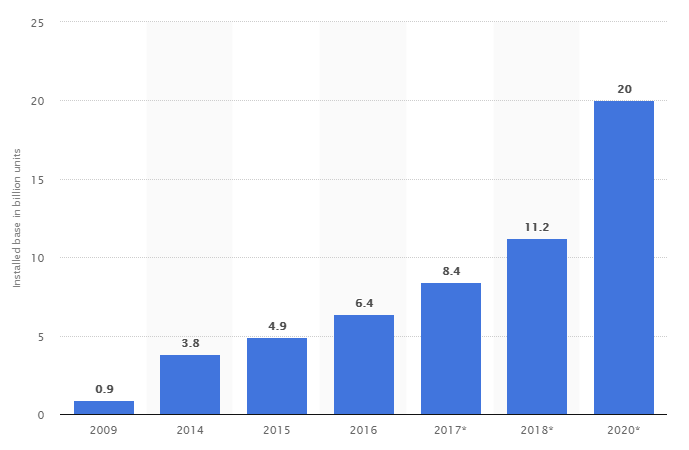
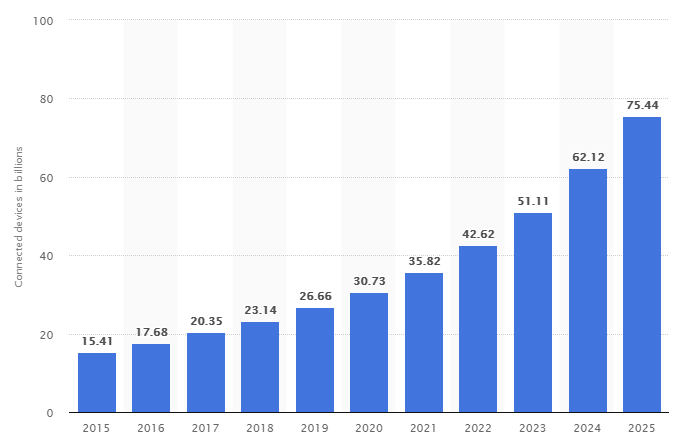
It is important to understand that the given data concern only really used devices.. If you look at the data and forecasts for the total number of IoT devices connected to the network at least once, then the numbers become even more impressive:
The problem with the security of IoT devices is not new. Back in 2015 and 2017 , relevant articles on the creation of botnets from surveillance cameras were published on Habré, and the most famous of them was Mirai, a botnet that brought together more than 1 million IoT devicesinto a single network for DDoS attacks. Several years have passed since those events, but it is still impossible to single out a particular vulnerable one or vice versa: the most secure equipment manufacturer: devices like technological giants are subject to attack, regardless of their orientation to the consumer or business segment, or devices of less popular companies .
It is physically impossible to correct the situation through rolling out fixes on devices, since there are already too many devices and manufacturers simply cannot cope with this task. In addition, vendors are not interested in such events, as they entail exclusively costs, the size of which is not comparable with the profit from the sale of a number of devices (the same IP cameras, whose cost is extremely far from transcendental heights).
Of course, to solve the described problem, it is necessary to build a complete information protection around IoT devices, as well as to control their activity by administrators in the field.
