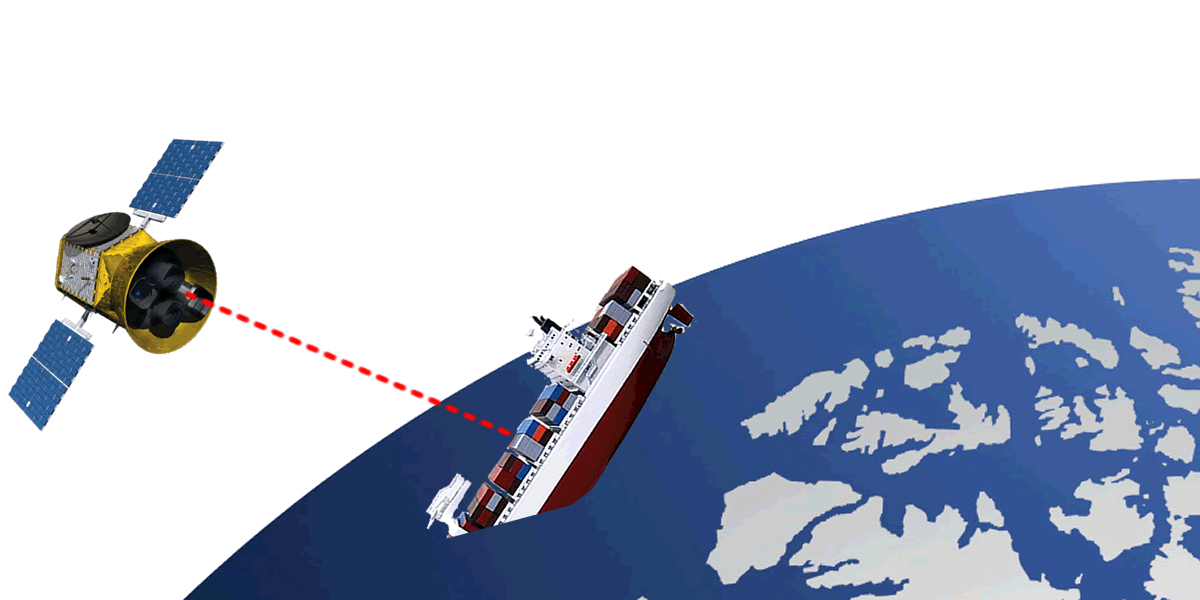
Can a hacker block the English Channel?
- Transfer

It turns out that shipping routes are seriously at risk from hackers: outdated IT systems on board ships, combined with modern IoT devices, give cyber-criminals a chance for success.
Updates to safety ecosystems in the shipping industry seem to be lost somewhere in the depths of the world's oceans. On the high seas, tools and security measures are still being applied, which in other industries became obsolete several years ago, which means that vessels can be robbed, hacked and even sunk. Ships, which were traditionally isolated, now, thanks to the Internet of Things and the development of information technology, are always online using VSAT, GSM / LTE and WiFi connections and have integrated electronic navigation systems.
Research Pen Test Partners(some of the developments presented in it were demonstrated at Infosecurity Europe) showed how easy it is to get access to the ship. Some of the access methods presented are of serious concern: open satellite terminals, user interfaces accessible through unprotected protocols, credentials set by default and never changed ... The list goes on and on. In this industry, a successful cyber attack will have enormous economic and commercial implications, since maritime transport throughout the world transports goods worth billions of euros.
Satellite communication: a threat in motion
Thanks to Shodan , a search engine for connected IoT devices, Pen Test researchers, after conducting various investigations, found that the configurations of some satellite antenna systems were easily identifiable through old firmware or unauthorized connections. To gain access to the systems, and eventually crack them, in some cases it was enough to use the default credentials or simple admin / 1234 combinations.

As part of this study, experts essentially created a tracker to track vulnerable ships by associating satellite terminal data with GPS real-time ship position data: ptp-shiptracker.herokuapp.com. Of course, the data displayed on this site is not intentionally updated so that they cannot be used by hackers to conduct real attacks.
Hardware hacking satellite terminal
Researchers at Pen Test Partners have applied all of their experience in the field of IoT device security, in the automotive field and in matters of SCADA equipment security, to the Cobham satellite terminal (Thrane & Thrane) Fleet One. Before testing, they checked the results of similar checks in the public domain, but could not find any materials. The equipment is very expensive, perhaps this explains the absence of such tests before.
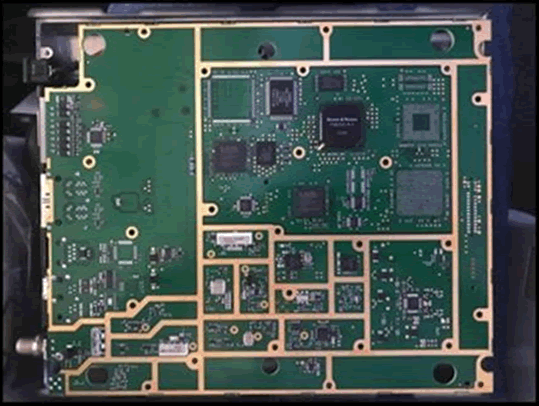
So, first, they found that the admin interfaces used telnet and HTTP. It was also found that the firmware did not have a signature, and the entire validation check was simply CRC.
Secondly, the researchers found that as a result of certain actions, you can edit all the web applications running on the terminal. And there are already possible different options for the attack.
In addition, there was no protection against rolling back the firmware. This means that a hacker, having a certain access, can elevate his privileges by installing an older, vulnerable version of the firmware.
Finally, the researchers found passwords to the administrator interface, embedded in the “configs”, hashed with MD5.
As you can see, there is hardly any thorough defense! But simple installation of a complex administrator password can significantly complicate access for hackers, even despite the indicated security flaws. The researchers reported that all of these violations were sent to Cobham for analysis by the manufacturer.
Ecdis paves the road to disaster
Electronic Chart Display and Information System ECDIS (Electronic Chart Display and Information System) is an electronic system used by ships for navigation, and it also warns the captain of the ship about any dangers on the ship's heading. This tool, which contains map and navigation information, is an alternative to old nautical charts that do not offer real-time information. According to the results of testing over 20 different ECDIS systems, analysts found that most of them used very old versions of operating systems (some were from Windows NT from 1993), and the built-in configuration interfaces had an extremely low level of protection.
Thus, the researchers showed that cyber-attackers could have caused a shipwreck by gaining access to ECDIS and reconfiguring the database to resize the ship. If the ship is of a different size (wider or longer) than it actually is, then electronic systems will offer incorrect information for the crews of other, nearby ships. They also showed that hackers could cause a collision by falsifying the position of the ship, which is displayed on the GPS receiver. This may seem implausible, but in the case of particularly busy shipping routes or in places with poor visibility, falsification of this kind can actually lead to a catastrophe. Plus, the human factor must also be taken into account: young crews too often “get hung up” on data from monitors,
The researchers looked at one interesting example with a ship that had a badly protected configuration interface. With it, you could "move" the boat, replacing the position of the GPS-receiver on the ship. This is not a GPS spoofing: ECDIS itself says that GPS is in a different position. Such a technique is similar to that of having introduced a GPS offset (although, the researchers claim that they could have done that too!). Here is an example of how a ship “jumps” from one side of Dover’s harbor to the other:
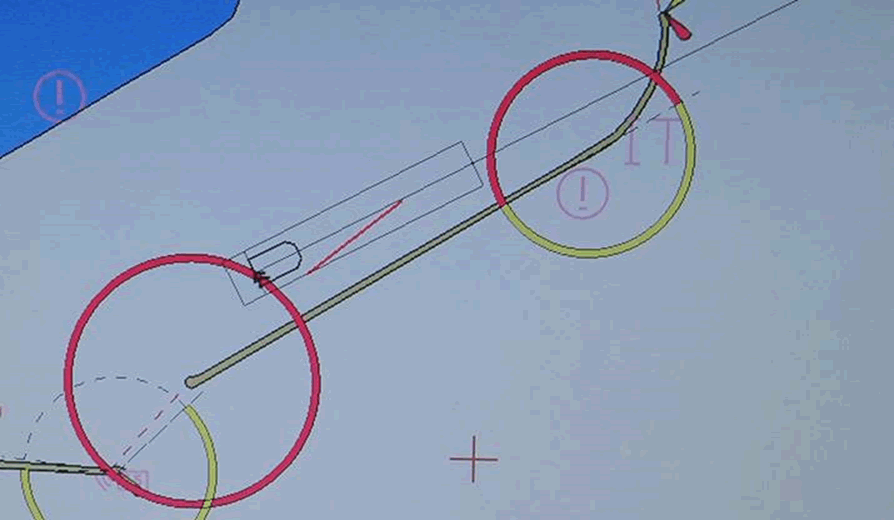
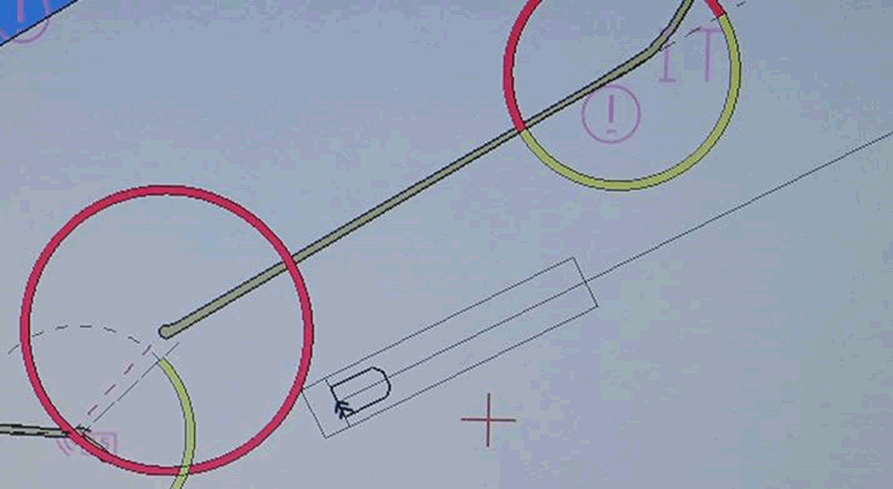
Even if the vulnerabilities shown by analysts are not exploited in such an extreme way, it is crucial to know that ship security flaws can lead to significant damage to both national industries and the maritime infrastructure, including ports, canals and docks. Analysts stressed that using ECDIS, you can also get access to systems that warn ship captains about possible collision scenarios. By controlling these collision warning systems, attackers can close off important shipping arteries such as the English Channel, putting at risk the export and import of a number of countries.
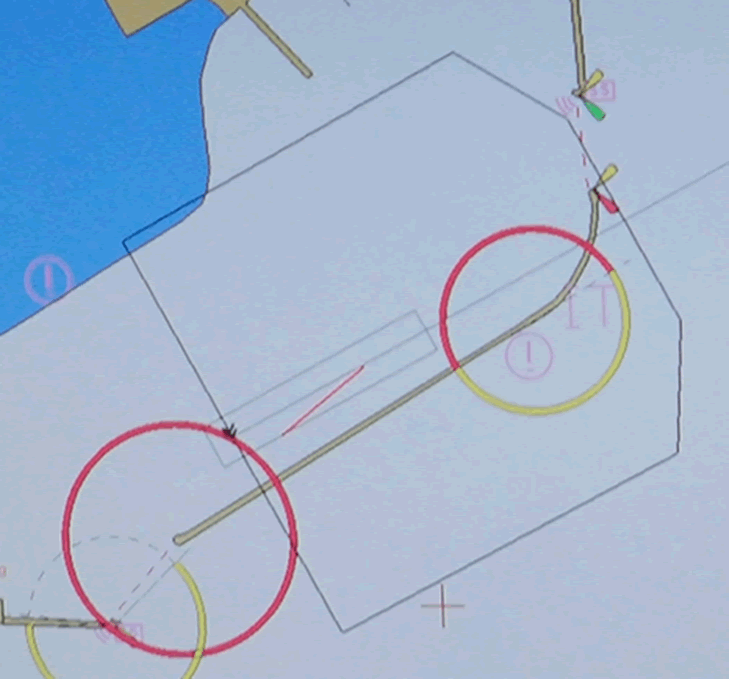
Researchers say they can reconfigure the ECDIS so that another ship can “appear” within a kilometer from the ship. The fact is that ECDIS transmits data to an AIS transceiver - a special system that is used on ships to avoid colliding with each other. Therefore, by making changes to the ECDIS output using the vulnerable configuration interface, the ship’s dimensions and location may change.
AIS systems on other ships will warn captains of a possible collision. Now imagine: the loaded channel of the English Channel with limited visibility. It is unlikely that in such a situation a reasonable captain will continue to move his huge vessel with thousands of tons of cargo, while he constantly has an AIS alarm. Result: shipping traffic in the English Channel will be stopped indefinitely. And this already causes damage to the shipping company, shippers, etc. all the way down to the final customer.
Go ahead: hacking NMEA 0183 messages
Another technique is the operation of serial networks (serial networks) on board, which control Operation Technology (OT). Ethernet and serial networks are often “connected” at several points, including GPS, satellite terminal, ECDIS, etc.
OT systems are used to monitor the operation of the steering wheel gear, motors, ballast pumps, and much more. They "communicate" with the help of messages NMEA0183.
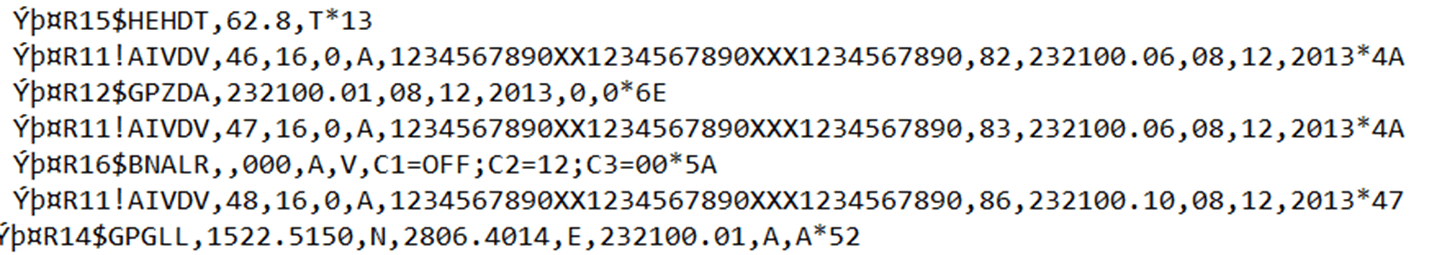
The problem is that these messages do not have authentication, encryption or verification: everything goes in plain text! Therefore, all you need to do is implement “man-in-the-middle” and change the data. Again, this is not about GPS spoofing, which is well known and easily detected. Researchers say that with the help of this technique you can "embed" subtle errors in order to slowly but surely knock the ship off course.
If autopilot is turned on, you can change the steering command by changing the GPS autopilot command as follows:

Change R to L (ie, change the command from the right steering to the left!), And then change the 2 bytes of the XOR checksum at the end.
Simple solutions for complex systems
In addition to updating systems and ensuring that confidential information is not disclosed on the network, the shipping industry must also maintain an adequate level of protection that is required for Internet devices, as we considered in the case of satellite communication systems. To ensure the confidentiality of the connection, TLS (Transport Layer Security) protocols must be installed on such devices, since failure on just one device can compromise the security of the entire network.
Analysts reported that the first step to alleviate most of the problems mentioned in their research should be the use of complex passwords for administrator profiles and the mandatory change of default credentials. In order to avoid serious problems such as sabotage and sabotage, the death of a ship and goods transported by it, collisions and loss of infrastructure, it is essential to have protection systems for the entire perimeter of the network, including transportation of goods, in order to introduce a modern level of information security in all international waters.
The emergence of permanent satellite connections has exposed shipping hacker attacks. Therefore, shipowners and operators need to quickly solve these problems, otherwise there will be more and more safety incidents in shipping. As a result of this, what we can now see in the movies will become a reality on the ocean lines.
// By materials
