Once again about OpenSSL
In my still small practice in the field of information security, I had to face some questions of cryptography, or more precisely, encryption, which I was able to find clear answers to with difficulty. So I decided to write a short article on the basics of working with OpenSSL.
This article will address the well-known issues of key generation, as well as the lesser-known issue of encrypting large files. About certification there will be no speech.
Let's start. In fact, for now, everything is simple.
Create a private key with the command.
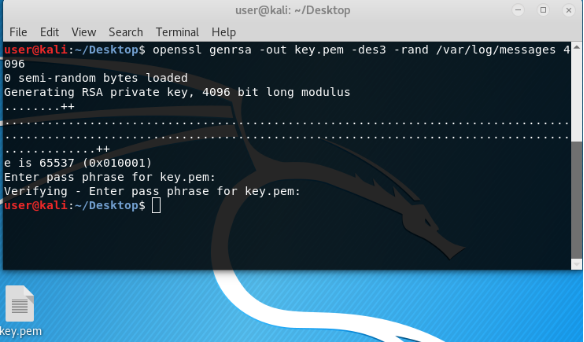
Here:
genrsa is a parameter indicating the creation of a key by the RSA encryption algorithm.
out - where to create the key.
4096 - key length.
In general, this is enough to create a key. But the private key is better to encrypt.
aes-256-cfb - algorithm and encryption mode.
rand / var / log / messages - random values from any folder, it is better to take logs, since with / dev / random or / dev / urandom can all hang tight, I was.
When creating a key, a password will be requested. The password is the basis of any protection, so try to tinker over it. And remember.
We have the key. Private Never show and hide to anyone according to the principle of Koshchey the Immortal.
On its basis we will make a public one, which can even be put on public display, at least glued to your forehead.
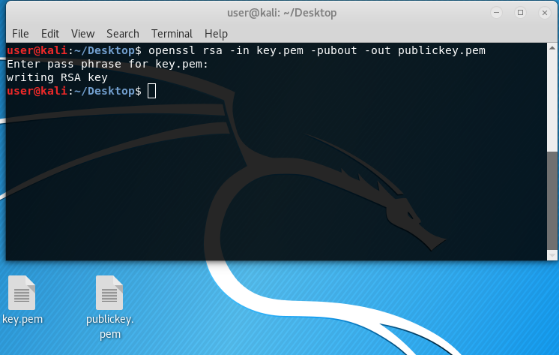
Now we have a pair of keys. Public can be thrown to the server to connect to it via ssh using your private key. Or to encrypt a small amount of data, such as a token or passphrase, etc.
The task of encrypting a large file has another solution.
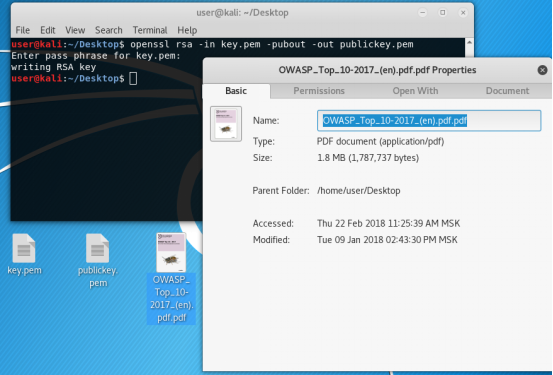
To encrypt a large amount of data, we use, for example, this pdf file of 1.8 Mbytes.
A large amount of data is encrypted with a symmetric encryption algorithm, for example, AES. Here we will apply asymmetric encryption to transmit a symmetric key, with which we will encrypt the text.
Let's start.
Create a symmetric session (one-time) key with a random sequence of characters and write to the file in the base64 view.
Next, encrypt the file with this key:
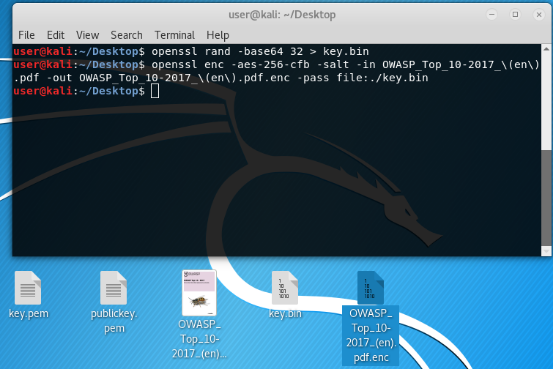
aes-256-cfb - algorithm and encryption mode. About the modes here I will not talk. This one is the best.
salt - salt for greater robustness.
pass file: ./ key.bin - encryption key.
Next, we encrypt the symmetric key with our public "asymmetric" key.
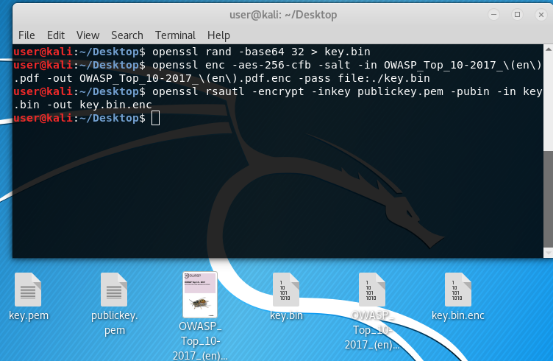
Received an encrypted file and a symmetric key. You can send your friend to decrypt. But we will send to ourselves, for this is homework with ourselves.
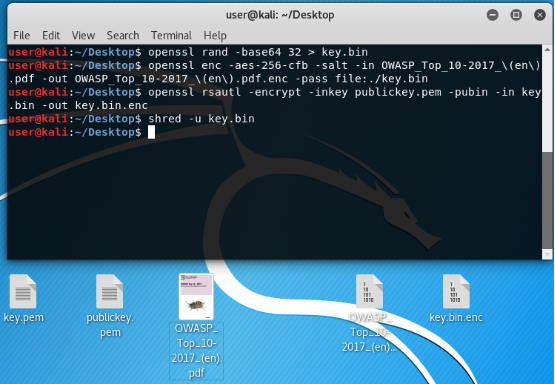
Now remove the original symmetric key! So that no one ever finds it.
In the picture below it is no longer.
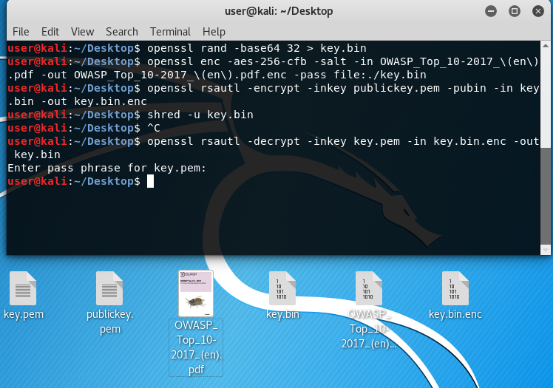
Now decipher the symmetric key with our private asymmetric key.
And we, the lucky ones, again have a symmetric key to decrypt our text, which is still encrypted.
The picture is again below, there is a key again.
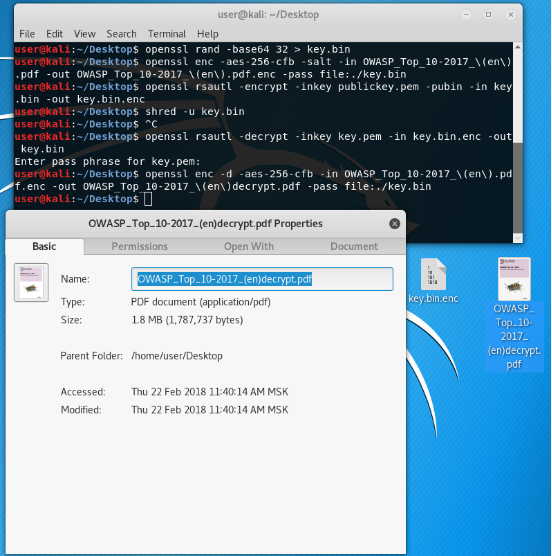
Now we will decrypt the file encrypted with the symmetric encryption cipher by our newly encrypted, but then decrypted with the asymmetric encryption cipher symmetric key.
Proof below.
Now: Why is it so difficult? Why it is impossible to take and do everything using asymmetric encryption?
We try, we go straight to the rake;)
We have!
File and keys.
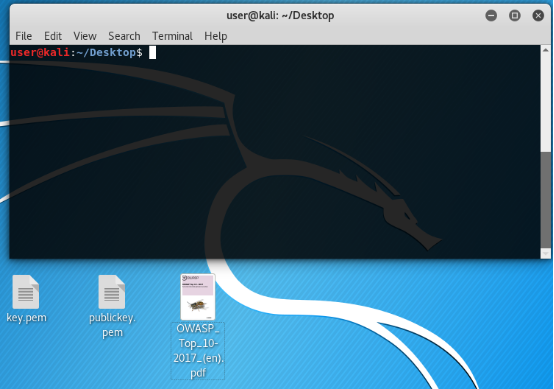
We encrypt.
Pou - Pou - pooooouuuuu. Mistake. Too much data for key size. For in asymmetric encryption, the key size must be greater than or equal to plaintext.
OpenSSL, as in the deal with the devil, gave you what you asked for, but not what you wanted. True, the encrypted file was empty.
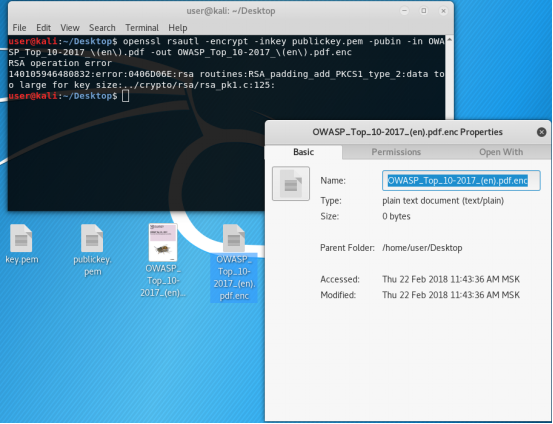
But you can encrypt a smaller than the key file. Let's try.
Create a small file.
For example, I did this:
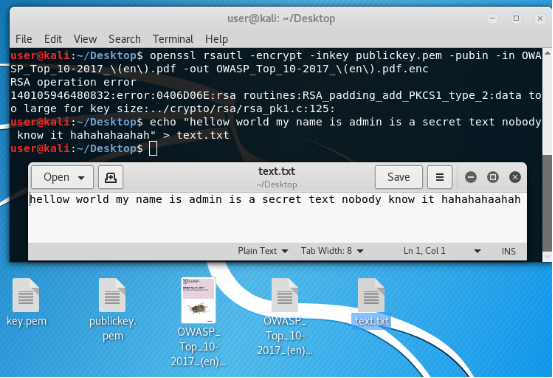
Encrypt it with our public key that everyone knows!
As you can see on the bottom of the picture file is encrypted. Nothing is clear! Who understands who you are?
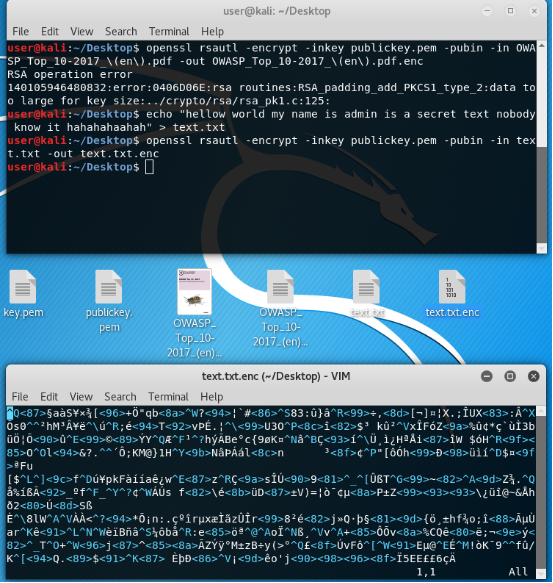
Now decrypt, having previously deleted the source file for the purity of the experiment.
We have the decrypted file. All perfectly.
To transfer all this encrypted good, it is better to encode the latter in base64. Accordingly, before deciphering, you must first decode.
Coded.
Decoded.

And again we have a beaberd that is not clear to anyone! If you understand, then this document is not for you!
This is approximately how encryption works when creating keys and data encryption using the example of the OpenSSL utility.
Later I am going to describe the encryption modes of symmetric block ciphers.
This article will address the well-known issues of key generation, as well as the lesser-known issue of encrypting large files. About certification there will be no speech.
Let's start. In fact, for now, everything is simple.
Create a private key with the command.
openssl genrsa -out key.pem -aes-256-cfb -rand /var/log/messages 4096
Here:
genrsa is a parameter indicating the creation of a key by the RSA encryption algorithm.
out - where to create the key.
4096 - key length.
In general, this is enough to create a key. But the private key is better to encrypt.
aes-256-cfb - algorithm and encryption mode.
rand / var / log / messages - random values from any folder, it is better to take logs, since with / dev / random or / dev / urandom can all hang tight, I was.
When creating a key, a password will be requested. The password is the basis of any protection, so try to tinker over it. And remember.
We have the key. Private Never show and hide to anyone according to the principle of Koshchey the Immortal.
On its basis we will make a public one, which can even be put on public display, at least glued to your forehead.
openssl rsa -in privatkey.pem -pubout -out publickey.pem
Now we have a pair of keys. Public can be thrown to the server to connect to it via ssh using your private key. Or to encrypt a small amount of data, such as a token or passphrase, etc.
The task of encrypting a large file has another solution.
To encrypt a large amount of data, we use, for example, this pdf file of 1.8 Mbytes.

A large amount of data is encrypted with a symmetric encryption algorithm, for example, AES. Here we will apply asymmetric encryption to transmit a symmetric key, with which we will encrypt the text.
Let's start.
Create a symmetric session (one-time) key with a random sequence of characters and write to the file in the base64 view.
openssl rand -base64 32 > key.binNext, encrypt the file with this key:
openssl enc -aes-256-cfb -salt -in OWASP_Top_10-2017_\(en\).pdf -out OWASP_Top_10-2017_\(en\).pdf.enc -pass file:./key.bin
aes-256-cfb - algorithm and encryption mode. About the modes here I will not talk. This one is the best.
salt - salt for greater robustness.
pass file: ./ key.bin - encryption key.
Next, we encrypt the symmetric key with our public "asymmetric" key.
opensslrsautl-encrypt-inkeypublickey.pem-pubin-inkey.bin-outkey.bin.enc
Received an encrypted file and a symmetric key. You can send your friend to decrypt. But we will send to ourselves, for this is homework with ourselves.
Now remove the original symmetric key! So that no one ever finds it.
shred -u key.binIn the picture below it is no longer.

Now decipher the symmetric key with our private asymmetric key.
opensslrsautl-decrypt-inkeyprivatkey.pem-inkey.bin.enc-outkey.binAnd we, the lucky ones, again have a symmetric key to decrypt our text, which is still encrypted.
The picture is again below, there is a key again.

Now we will decrypt the file encrypted with the symmetric encryption cipher by our newly encrypted, but then decrypted with the asymmetric encryption cipher symmetric key.
openssl enc -d -aes-256-cfb -in OWASP_Top_10-2017_\(en\).pdf.enc -out OWASP_Top_10-2017_\(en\)decrypt.pdf -pass file:./key.binProof below.

Now: Why is it so difficult? Why it is impossible to take and do everything using asymmetric encryption?
We try, we go straight to the rake;)
We have!
File and keys.

We encrypt.
opensslrsautl-encrypt-inkeypublickey.pem-pubin-inOWASP_Top_10-2017_\(en\).pdf-outOWASP_Top_10-2017_\(en\).pdf.encPou - Pou - pooooouuuuu. Mistake. Too much data for key size. For in asymmetric encryption, the key size must be greater than or equal to plaintext.
OpenSSL, as in the deal with the devil, gave you what you asked for, but not what you wanted. True, the encrypted file was empty.

But you can encrypt a smaller than the key file. Let's try.
Create a small file.
For example, I did this:
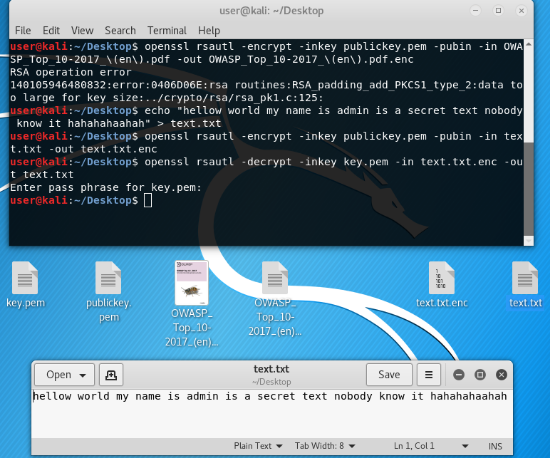
echo "hellow world my name is admin is a secret text nobody know it hahahahaahah" > text.txt
Encrypt it with our public key that everyone knows!
openssl rsautl -encrypt -inkey publickey.pem -pubin -intext.txt -outtext.txt.encAs you can see on the bottom of the picture file is encrypted. Nothing is clear! Who understands who you are?

Now decrypt, having previously deleted the source file for the purity of the experiment.
openssl rsautl -decrypt -inkey privatkey.pem -intext.txt.enc -outtext.txt
We have the decrypted file. All perfectly.
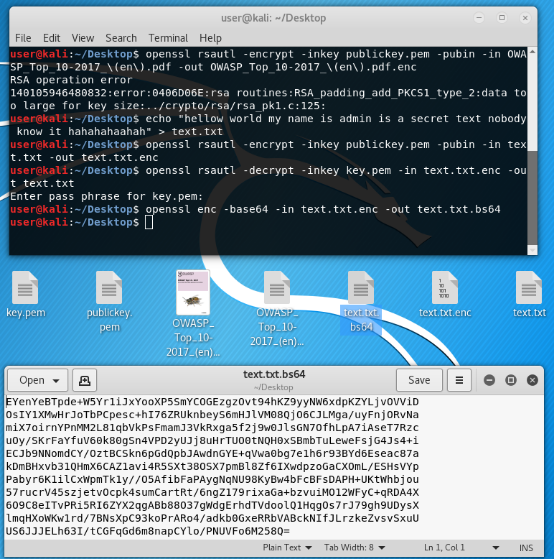
To transfer all this encrypted good, it is better to encode the latter in base64. Accordingly, before deciphering, you must first decode.
Coded.
openssl enc -base64 -intext.txt.enc -outtext.txt.bs64
Decoded.
openssl enc -base64 -d -intext.txt.bs64 -outtext.txt.enc
And again we have a beaberd that is not clear to anyone! If you understand, then this document is not for you!
This is approximately how encryption works when creating keys and data encryption using the example of the OpenSSL utility.
Later I am going to describe the encryption modes of symmetric block ciphers.
