Practical techniques of working in Wireshark
- Transfer
Julia Evans, the author of the material, the translation of which we are publishing today, decided to tell about one of her favorite network tools, which is called Wireshark . This is a powerful and complex program equipped with a graphical interface, designed to analyze traffic on computer networks. Julia says that in practice, only a few Wireshark features are used, but they usually turn out to be very useful. Here she wants to share with everyone the story about the most useful techniques for working with the program and hopes that they will be useful not only for her, but also for everyone who has to solve network problems.

Wireshark distributions for various operating systems can be found here . To install the program, you can download and install the appropriate file. In addition, if you are using Linux distributions based on Debian, you can use the command
This is what the program interface looks like.
Interface Wireshark
At first glance, all this may seem too complicated: a long list of packets, a mysterious field for entering some requests ... How to work with Wireshark?
I usually use Wireshark to find out the causes of network problems. The sequence of actions performed in the course of solving such problems is as follows:
As you can see, everything is very simple. However, after the pcap file is open in the program, you may have a logical question about what to do with all this. Let's talk about it.
Often, when I analyze a situation in Wireshark, I need to check for a specific TCP connection with which, for some reason, something is wrong. Thanks to Wireshark, you can analyze the entire life cycle of a single TCP connection and find out the reasons for incorrect system behavior.
You can do this by clicking the right mouse button on the package you are interested in and selecting the command from the context menu

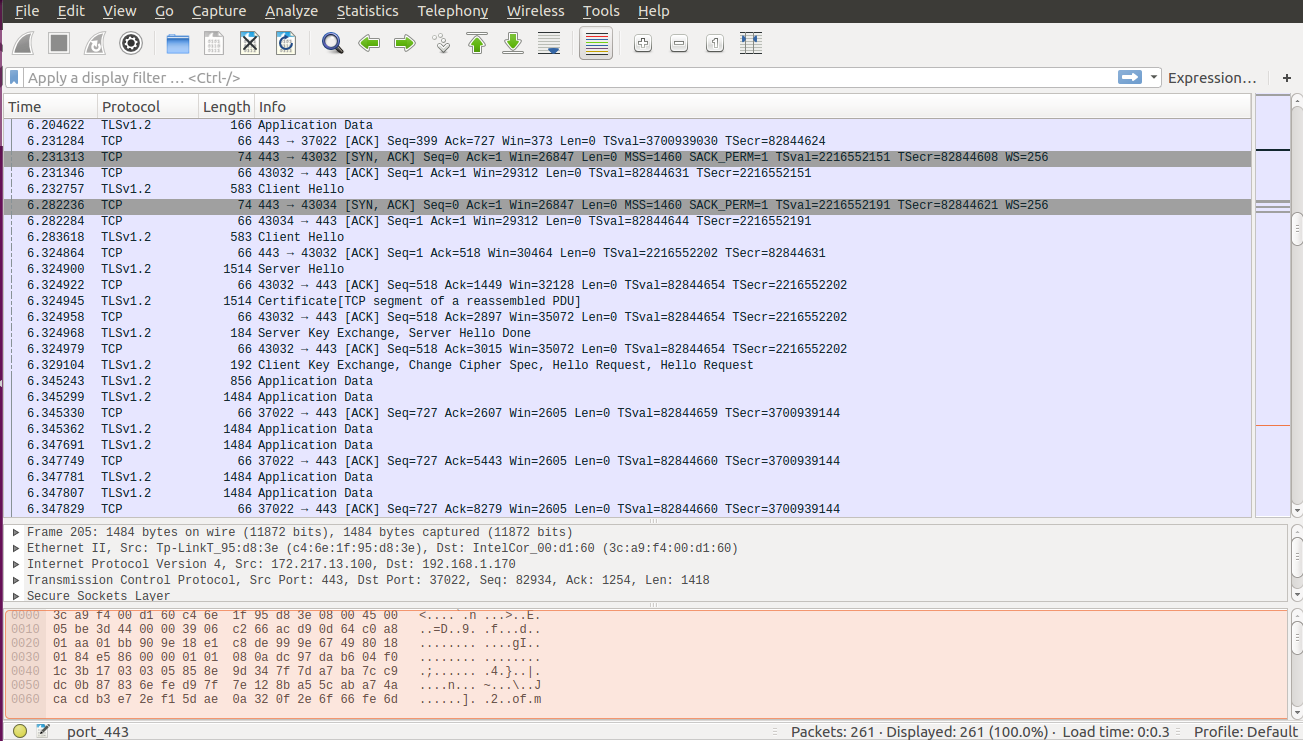
Starting TCP connection analysis
After this, Wireshark will show other packets from the same TCP connection to which the packet you clicked belongs to. In the image below you can see an example of a successful SSL-connection - here there are bags

TCP connection
analysis The TCP packet analysis method I was considering here I had to use on the day of this writing, at work. Some connections were reset, and I noticed that after sending the packet, the
The above is a very typical pattern of working with Wireshark. Usually the client and the server are involved in the connection, and something goes wrong either on the client or on the server. This may be, for example, some kind of failure or an error in the system settings. As a result, Wireshark just gives me invaluable help in identifying the culprit of the problems, helping me to find out whether this is a client or a server.
To understand exactly what a particular packet is, Wireshark uses port numbers, and usually this approach works. For example, if a program sees some traffic on port 80, it decides that it is HTTP traffic and usually it is.
However, sometimes HTTP connections use unusual ports, as a result, Wireshark needs prompts in order to recognize them. Such prompts can be given to the program by calling the context menu of the package and selecting the command there
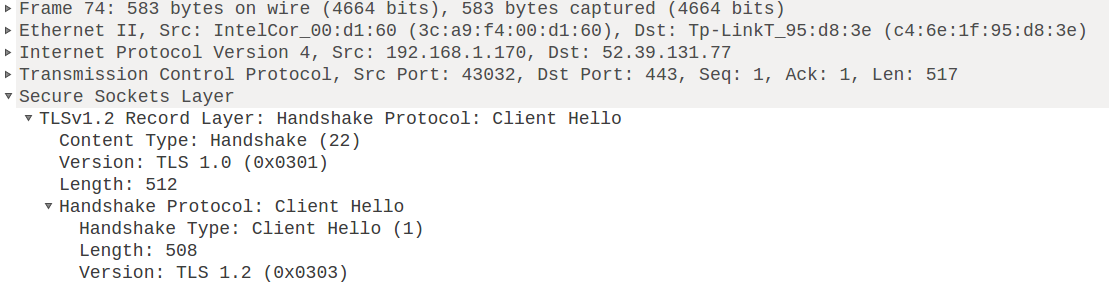
In Wireshark there is just a delightful view of the details of the package, with which you can understand the contents of any package. Take, for example, the packet with the message
Wireshark gives the network administrator two incredibly useful tools for examining the contents of packets. The first is the browse mode in which you can open the headers of the packet (for example, the Ethernet header, IP header, TCP header) and view their contents.
Package Header Analysis The
second packet scan mode is a true miracle. Here you can see the raw packet data as a sequence of bytes. And, which is especially nice if you hover the mouse over some byte (for example, in the figure below the pointer is pointed at the byte included in

Analysis of raw packet data
Wireshark supports powerful query language. This makes it much easier to find specific packages in lists. Usually, when working with a program, I use very simple queries. Here are some examples:
The query language Wireshark has much greater capabilities than the query language
Sometimes I need to pay special attention to the study of slow TCP connections. How to do this, provided that in my file there are records of thousands of packages? How to find slow TCP connections?
If you select an item in the main menu of the program

Statistical information
In particular here, in the column
If you haven’t updated Wireshark for a long time, it’s worth it. For example, recently I, on a working laptop, was engaged in the study of HTTP / 2 packets. I then had a hard time, and I decided to see the documentation. As it turned out, I had an old version of the program. In the update I installed, HTTP / 2 support was seriously improved, that is, there was just what I needed then.
In this material there are some terms that can be attributed to something like a jargon of network specialists. For example - frame (frame), TCP port (TCP port), DNS response (DNS response), source IP address,
Such orientation of Wireshark to low-level network mechanisms, however, has a serious plus. The fact is that by working with this program, you can learn something new about network protocols. For example, I do not know much about the internal mechanisms of the TLS / SSL protocol. However, analyzing the traffic in Wireshark, I noticed that the first two packets of the SSL connection are
Wireshark has great features. Here we told only about some of them. However, those methods of work that are considered here, according to the author of the material, are used in about 95% of situations when the need for Wireshark arises. Therefore, we hope that even the little that you have learned today will be useful to you.
Dear readers! Do you use Wireshark?


Install Wireshark
Wireshark distributions for various operating systems can be found here . To install the program, you can download and install the appropriate file. In addition, if you are using Linux distributions based on Debian, you can use the command
sudo apt install wireshark. If you wish, in order to find the latest version of the program, you can refer to the personal archive of packages wireshark-dev . This is what the program interface looks like.

Interface Wireshark
At first glance, all this may seem too complicated: a long list of packets, a mysterious field for entering some requests ... How to work with Wireshark?
Parsing pcap files
I usually use Wireshark to find out the causes of network problems. The sequence of actions performed in the course of solving such problems is as follows:
- Packet capture with help
tcpdump(usually with a command likesudo tcpdump port 443 -w output.pcap). - Copy pcap file to work laptop (
scp host:~/output.pcap .). - Opening a pcap file with Wireshark (
wireshark output.pcap).
As you can see, everything is very simple. However, after the pcap file is open in the program, you may have a logical question about what to do with all this. Let's talk about it.
TCP connection analysis
Often, when I analyze a situation in Wireshark, I need to check for a specific TCP connection with which, for some reason, something is wrong. Thanks to Wireshark, you can analyze the entire life cycle of a single TCP connection and find out the reasons for incorrect system behavior.
You can do this by clicking the right mouse button on the package you are interested in and selecting the command from the context menu
Conversation filter > TCP.
Starting TCP connection analysis
After this, Wireshark will show other packets from the same TCP connection to which the packet you clicked belongs to. In the image below you can see an example of a successful SSL-connection - here there are bags
client hello,service hello,certificate,server key exchangewhich are used for established SSL-connection.
TCP connection
analysis The TCP packet analysis method I was considering here I had to use on the day of this writing, at work. Some connections were reset, and I noticed that after sending the packet, the
client helloclient sent a packetFIN ACKthat terminated the TLS connection. What I found out turned out to be useful, since it became clear that the client is terminating the connections, not the server. As a result, I immediately learned that the problem lies with the client, and I need to pay attention to him.The above is a very typical pattern of working with Wireshark. Usually the client and the server are involved in the connection, and something goes wrong either on the client or on the server. This may be, for example, some kind of failure or an error in the system settings. As a result, Wireshark just gives me invaluable help in identifying the culprit of the problems, helping me to find out whether this is a client or a server.
Team Decode as
To understand exactly what a particular packet is, Wireshark uses port numbers, and usually this approach works. For example, if a program sees some traffic on port 80, it decides that it is HTTP traffic and usually it is.
However, sometimes HTTP connections use unusual ports, as a result, Wireshark needs prompts in order to recognize them. Such prompts can be given to the program by calling the context menu of the package and selecting the command there
Decode as. Further, you can tell Wireshark which protocol is used to transfer packets using a certain port. These tips simplify data analysis.View package contents
In Wireshark there is just a delightful view of the details of the package, with which you can understand the contents of any package. Take, for example, the packet with the message
client hellofrom the previous example. This is the first packet of the SSL connection, the client says: “Hello! Here I am!". Wireshark gives the network administrator two incredibly useful tools for examining the contents of packets. The first is the browse mode in which you can open the headers of the packet (for example, the Ethernet header, IP header, TCP header) and view their contents.

Package Header Analysis The
second packet scan mode is a true miracle. Here you can see the raw packet data as a sequence of bytes. And, which is especially nice if you hover the mouse over some byte (for example, in the figure below the pointer is pointed at the byte included in
tiles.services.mozilla.com), the program in the status bar will inform you which field this byte belongs to (in this case it’s - fieldServer Name), and the code name used by Wireshark for this field (in this case, -ssl.handshake.extensions_server_name)
Analysis of raw packet data
Search for packages
Wireshark supports powerful query language. This makes it much easier to find specific packages in lists. Usually, when working with a program, I use very simple queries. Here are some examples:
- The query
frame contains "mozilla"allows you to search for a stringmozillaanywhere in the package and display a list of found packages. - The request
tcp.port == 443displays packets using TCP port 443. - The query
dns.resp.len > 0displays all DNS responses. - The request
ip.addr == 52.7.23.87displays the packets whose IP address of the source or recipient is 52.7.23.87.
The query language Wireshark has much greater capabilities than the query language
tcpdump(and, in addition, supports completion by pressing the TAB key). As a result, I often use the following sequence of actions: I capture a large amount of packets using tcpdump(say, something like all packets from port 443), and then I carefully study them using Wireshark.View the duration of TCP connections
Sometimes I need to pay special attention to the study of slow TCP connections. How to do this, provided that in my file there are records of thousands of packages? How to find slow TCP connections?
If you select an item in the main menu of the program
Statistics, and a command in it Conversations, Wireshark will provide us with a wonderful set of statistical information.
Statistical information
In particular here, in the column
Duration, you can see the duration of TCP connections, identify the longest of them and carefully study them. This is a very useful feature.Wireshark Update
If you haven’t updated Wireshark for a long time, it’s worth it. For example, recently I, on a working laptop, was engaged in the study of HTTP / 2 packets. I then had a hard time, and I decided to see the documentation. As it turned out, I had an old version of the program. In the update I installed, HTTP / 2 support was seriously improved, that is, there was just what I needed then.
Using Wireshark to study network protocols
In this material there are some terms that can be attributed to something like a jargon of network specialists. For example - frame (frame), TCP port (TCP port), DNS response (DNS response), source IP address,
client helloSSL connection packet (SSL client hello). One of the reasons for their use is the fact that Wireshark is definitely not trying to protect the user from the intricacies of the internal design of network technologies. For a beginner, this state of affairs can, at first, make one think that Wireshark is not a program for it, but only for experienced network specialists.Such orientation of Wireshark to low-level network mechanisms, however, has a serious plus. The fact is that by working with this program, you can learn something new about network protocols. For example, I do not know much about the internal mechanisms of the TLS / SSL protocol. However, analyzing the traffic in Wireshark, I noticed that the first two packets of the SSL connection are
client helloand server hello. As a result, the protocol, which, if not to delve into the details of his work, seems to be something mysterious and inaccessible for understanding, begins to take a more understandable form, turns into something that can be understood and analyzed.Results
Wireshark has great features. Here we told only about some of them. However, those methods of work that are considered here, according to the author of the material, are used in about 95% of situations when the need for Wireshark arises. Therefore, we hope that even the little that you have learned today will be useful to you.
Dear readers! Do you use Wireshark?

