ViPNet crypto-gateway implementation experience in ERIS
Hi, Habr! In this article we will talk about the implementation of ViPNet crypto-gateways to protect communication channels in the framework of the personal data protection project in the ERIS information system. We were lucky to become a part of such an important project for Moscow medicine, which takes radiation diagnostics to a new level.
ERIS (Unified Radiological Information Service) is an information system that combines high-tech medical equipment, workplaces of radiologists and a single archive of diagnostic images. Currently, ERIS combines magnetic resonance, digital devices of classical X-ray, devices for fluorography and computer tomographs in 64 polyclinics of the city of Moscow, including outpatient facilities of Zelenograd.
The main tasks of ERIS are to increase the efficiency of radiation diagnostics in Moscow, to create a single network uniting diagnostic equipment, to provide a modern and reliable system for storing the resulting images, descriptions and conclusions.
Since the patient's personal data is processed in the ERIS information system, it is necessary to comply with the requirements of the Federal Law “On Personal Data” and by-laws related to this law. One of the requirements for the protection of personal data is the organization of secure communication channels using the means of cryptographic protection of information (SKZI). In accordance with this requirement, we have begun to design a system for the protection of personal data in general and ICPT in particular.
Our company Elefus, the Customer represented by the company Laval, has put forward a number of requirements that the SKZI had to meet, among them the main ones:
Four products were tested:
We chose the most popular and well-proven software and hardware solutions (Continent and ViPNet) and purely software solutions (CryptoPro and MagPro). It was not intended to install additional software on computers of the radiological office, because often very specific and old versions of operating systems and special software are required for interaction with radiological equipment. Therefore, the protection of the communication channel had to be placed on the edge network equipment. Two schemes for installing the SKZI were considered: installation of hardware and software (Continent and ViPNet) at the perimeter, or installation of a computer serving as a gateway for the radiological office, on which the CMIS will be installed (CryptoPro and MagPro). In terms of costs, these options turned out to be comparable,
The testing scheme was as follows:
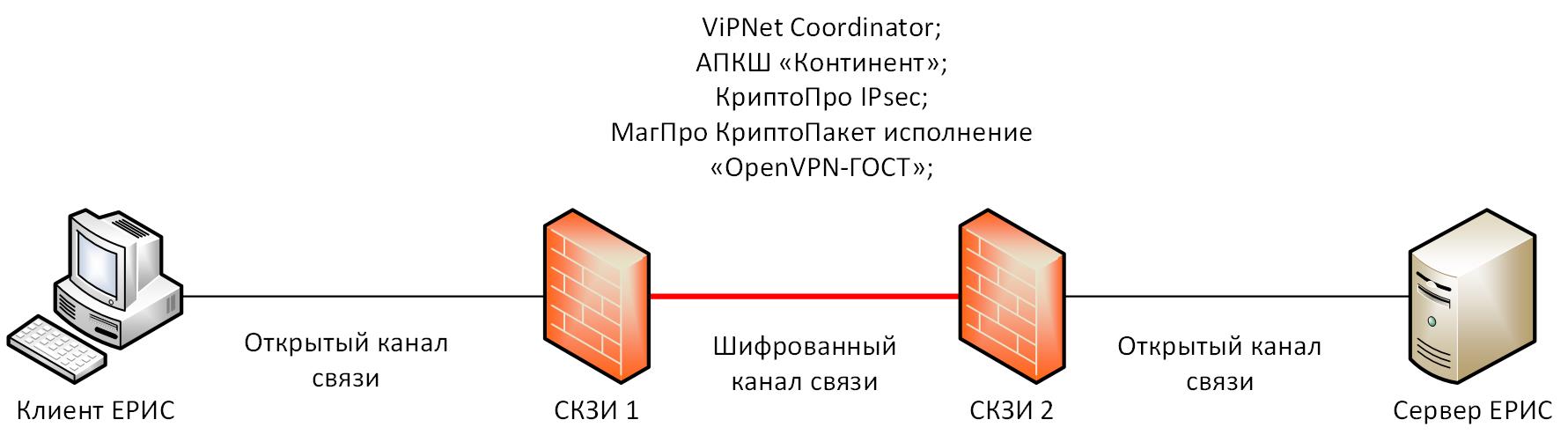
Figure 1 - Testing scheme
During testing, three types of images were transmitted: CT, MMG, PETKT (they differ in file sizes, client-server interaction frequency), various image variants allowed simulating various types of loads on crypto-gateways. Measurements of delays and speed in the channel were made using WinMTR and iperf3.
According to the results of testing, Continent and ViPNet were in the lead, their results were comparable, CryptoPro lagged slightly, and MagPro strongly influenced both the speed and the delays in the channel.
Further, after interacting with vendors, the Customer made the final decision in favor of ViPNet. Let's leave the final choice beyond the brackets of this article, from a technical point of view, the Continent and ViPNet are almost the same.
InfoTeKS (manufacturer ViPNet) provided the following equipment for pilot testing:
The equipment was tested for a month in combat conditions. The tests showed that our calculations were correct, and the tests were fairly accurate. The equipment worked in a regular mode, without any significant restrictions on the work of medical workers. As a result, the final specification turned out to be just this equipment, the HW50 was installed in radiology cabinets, a cluster of two crypto-gateways HW1000 of the updated model with increased bandwidth - in the data center).
We needed to approach the implementation with the utmost care. As I said above, the medical workers of the radiology rooms are constantly loaded, so we had 15 minutes to implement the CIPF at the facility. We carried out the implementation together with Laval engineers who knew the local equipment well.
The implementation consisted of the following stages:
Next we will show screenshots from the monitoring system, where you can view the load on the equipment separately for six months and separately for one working day (CPU, RAM, network). The names of network devices are hidden, in terms of semantic load, this does not affect anything.
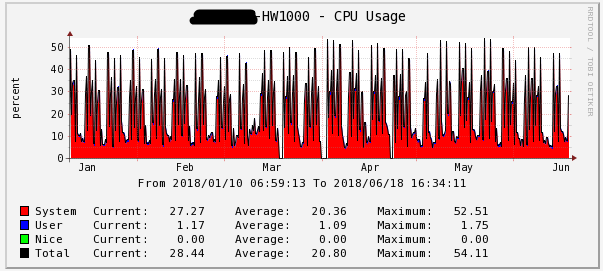
Figure 2 - CPU load for half a year HW1000
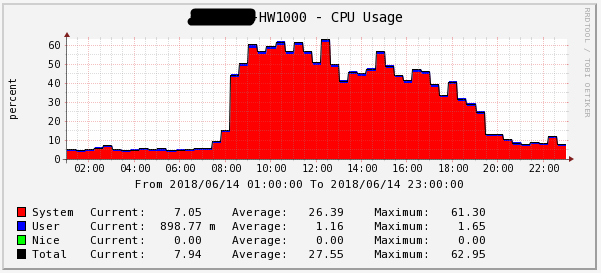
Figure 3 - CPU load for 1 day HW1000
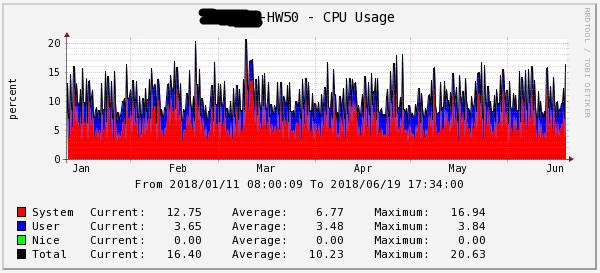
Figure 4 - CPU load for half a year HW50
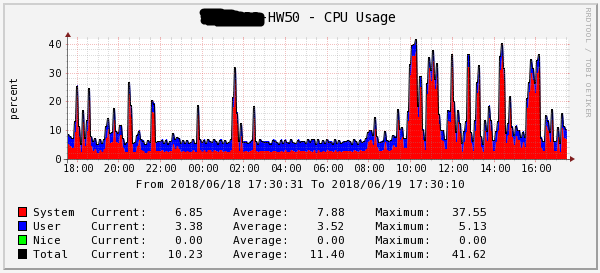
Figure 5 - CPU load for 1 day HW50
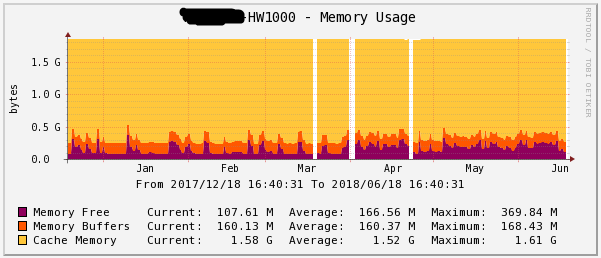
Figure 6 - Loading RAM for half a year HW1000
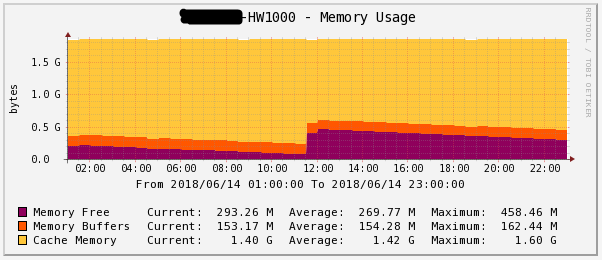
Figure 7 - Loading RAM for 1 day HW1000
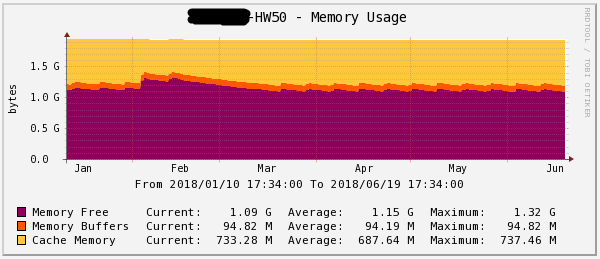
Figure 8 - Loading RAM for half a year HW50 Figure 9 - Loading RAM for 1 day
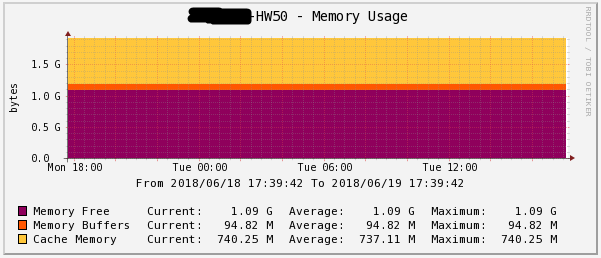
HW50
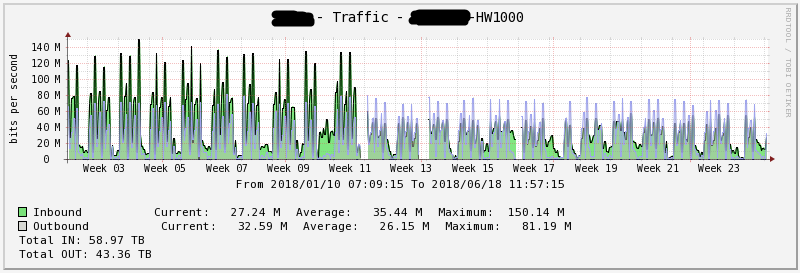
Figure 10 - Network load for six months HW1000
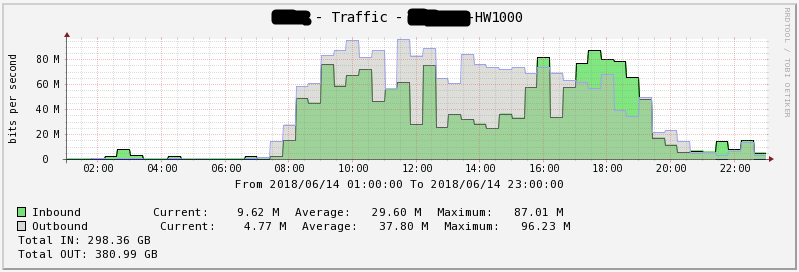
Figure 11 - Network download for 1 day HW1000
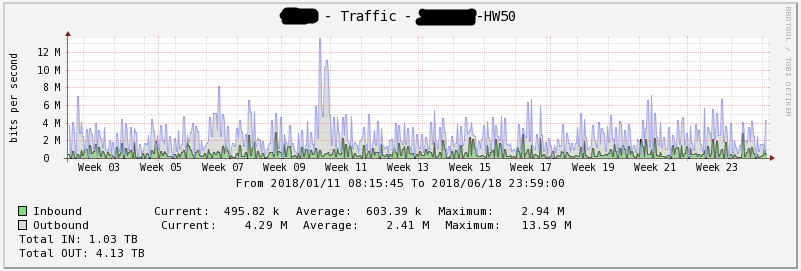
Figure 12 - Network download for six months HW50
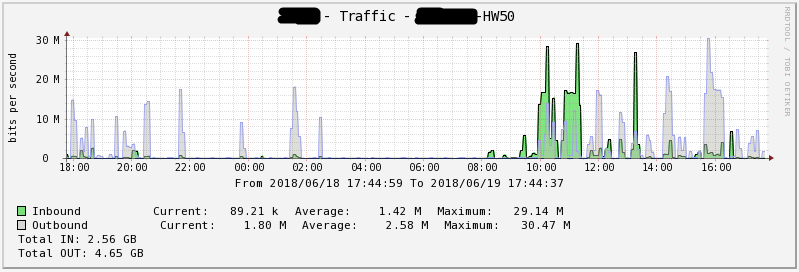
Figure 13 - Network download for 1 day HW50
It has been about a year since the implementation of the project, all CIPPs work in a regular mode, not a single crypto-gateway has failed. ERIS works in a regular mode with the information security tools installed, ensuring the necessary level of information security of the personal data of patients in Moscow polyclinics.
Briefly about ERIS
ERIS (Unified Radiological Information Service) is an information system that combines high-tech medical equipment, workplaces of radiologists and a single archive of diagnostic images. Currently, ERIS combines magnetic resonance, digital devices of classical X-ray, devices for fluorography and computer tomographs in 64 polyclinics of the city of Moscow, including outpatient facilities of Zelenograd.
The main tasks of ERIS are to increase the efficiency of radiation diagnostics in Moscow, to create a single network uniting diagnostic equipment, to provide a modern and reliable system for storing the resulting images, descriptions and conclusions.
The need for crypto-gateway
Since the patient's personal data is processed in the ERIS information system, it is necessary to comply with the requirements of the Federal Law “On Personal Data” and by-laws related to this law. One of the requirements for the protection of personal data is the organization of secure communication channels using the means of cryptographic protection of information (SKZI). In accordance with this requirement, we have begun to design a system for the protection of personal data in general and ICPT in particular.
Selection criteria, testing scheme, pilot, final selection
Our company Elefus, the Customer represented by the company Laval, has put forward a number of requirements that the SKZI had to meet, among them the main ones:
- channel delays (this was the most important criterion because the medical staff using the client application at the workplace connects to the server side in the data center, and the channel delays strongly affect the system performance and patient work speed);
- availability of a certificate by the FSB of Russia for cryptographic instruments (a requirement of regulatory documents relating to the protection of personal data (FSB Order No. 378 dated July 10, 2014 “On Approving the Composition and Content of Organizational and Technical Measures for Ensuring the Security of Personal Data when Processing Information in Personal Information Systems using the means of cryptographic protection of information necessary for the fulfillment of the requirements for the protection of personal data established by the Government of the Russian Federation for each level of her protection "));
- scalability of the solution (the system is supposed to be expanded to additional objects, therefore, we initially had to install equipment with a margin and the ability to scale both horizontal and vertical);
- resiliency (if you were in Moscow polyclinics, then you know perfectly well that there is always a queue in radiology rooms, therefore an important factor was ensuring the resiliency of the solution);
- sufficient performance (it was necessary to install equipment of small capacity to radiology cabinets, but sufficient to ensure a good communication channel to the data center, our reference was a bandwidth of 20 mb / s);
- monitoring (since the infrastructure is distributed throughout Moscow, it is necessary to ensure continuous monitoring of equipment and monitor the network load);
- simplicity of service (general engineers, who do not have deep knowledge of ViPNet (because this is not their main task), must go to the facilities, should solve the problem on site according to the instructions).
Four products were tested:
- ViPNet Coordinator;
- APKSh "Continent";
- CryptoPro IPsec;
- MagPro CryptoPacket OpenVPN-GOST version
We chose the most popular and well-proven software and hardware solutions (Continent and ViPNet) and purely software solutions (CryptoPro and MagPro). It was not intended to install additional software on computers of the radiological office, because often very specific and old versions of operating systems and special software are required for interaction with radiological equipment. Therefore, the protection of the communication channel had to be placed on the edge network equipment. Two schemes for installing the SKZI were considered: installation of hardware and software (Continent and ViPNet) at the perimeter, or installation of a computer serving as a gateway for the radiological office, on which the CMIS will be installed (CryptoPro and MagPro). In terms of costs, these options turned out to be comparable,
The testing scheme was as follows:

Figure 1 - Testing scheme
During testing, three types of images were transmitted: CT, MMG, PETKT (they differ in file sizes, client-server interaction frequency), various image variants allowed simulating various types of loads on crypto-gateways. Measurements of delays and speed in the channel were made using WinMTR and iperf3.
According to the results of testing, Continent and ViPNet were in the lead, their results were comparable, CryptoPro lagged slightly, and MagPro strongly influenced both the speed and the delays in the channel.
Further, after interacting with vendors, the Customer made the final decision in favor of ViPNet. Let's leave the final choice beyond the brackets of this article, from a technical point of view, the Continent and ViPNet are almost the same.
InfoTeKS (manufacturer ViPNet) provided the following equipment for pilot testing:
- HW50 - 2 pcs. for radiology rooms
- HW1000 - 1 pc. for data center
The equipment was tested for a month in combat conditions. The tests showed that our calculations were correct, and the tests were fairly accurate. The equipment worked in a regular mode, without any significant restrictions on the work of medical workers. As a result, the final specification turned out to be just this equipment, the HW50 was installed in radiology cabinets, a cluster of two crypto-gateways HW1000 of the updated model with increased bandwidth - in the data center).
How to implement? Scheme, complexity, presetting
We needed to approach the implementation with the utmost care. As I said above, the medical workers of the radiology rooms are constantly loaded, so we had 15 minutes to implement the CIPF at the facility. We carried out the implementation together with Laval engineers who knew the local equipment well.
The implementation consisted of the following stages:
- Pre-configuration (the equipment was pre-configured by our engineers (release and installation of dst-on PAK, setting up network interfaces, setting up a snmp-agent, setting up PAK in ViPNet Administrator);
- Installation of crypto-gateways in the data center (setting up an alternative channel in order not to interrupt the work of ERIS);
- Installation of crypto-gateways in the clinics (the engineer needed to plug equipment into the 15-minute interval and make sure that the tunnel in the data center was raised. Naturally, in ideal cases, everything happened in minutes, but there is always some time to correct the problems that arise. In general, 15 minutes is enough to complete the work);
- Connecting crypto-gateways to the monitoring system (at this stage, revealed a system bug that was reported to the vendor, periodically the snmp agent spontaneously fell off, it had to be restarted. Since we know that ViPNet runs on Linux (Debian), we wrote a script that automatically restarted the process. In the new version, InfoTeX fixed this moment).
Monitoring The load on the processor, RAM, network
Next we will show screenshots from the monitoring system, where you can view the load on the equipment separately for six months and separately for one working day (CPU, RAM, network). The names of network devices are hidden, in terms of semantic load, this does not affect anything.
CPU load

Figure 2 - CPU load for half a year HW1000

Figure 3 - CPU load for 1 day HW1000

Figure 4 - CPU load for half a year HW50

Figure 5 - CPU load for 1 day HW50
Load on RAM

Figure 6 - Loading RAM for half a year HW1000

Figure 7 - Loading RAM for 1 day HW1000

Figure 8 - Loading RAM for half a year HW50 Figure 9 - Loading RAM for 1 day

HW50
Network load

Figure 10 - Network load for six months HW1000

Figure 11 - Network download for 1 day HW1000

Figure 12 - Network download for six months HW50

Figure 13 - Network download for 1 day HW50
Conclusion
It has been about a year since the implementation of the project, all CIPPs work in a regular mode, not a single crypto-gateway has failed. ERIS works in a regular mode with the information security tools installed, ensuring the necessary level of information security of the personal data of patients in Moscow polyclinics.
