MS12-020: Breeding RDP Worms
On Tuesday, Microsoft released the next batch of patches, and among them our attention was especially attracted by MS12-020 , which has a critical status. The vulnerability allows arbitrary code to be executed on a remote system with the power of a specially crafted RDP package. This vulnerability affects all versions of MS Windows, including 64-bit versions. In fact, within the scope of patch MS12-020, two vulnerabilities CVE-2012-0002 (RCE in RDP) and CVE-2012-0152 (DoS in Terminal Server) were closed. We are more interested in the first vulnerability, since it is much more dangerous and can lead to the appearance of network worms that will actively exploit it (at the moment I do not know about its use in malicious programs).
By the way, the vulnerability was relatively recently closed.MS11-065 (August 2011), which allowed DoS (WinXP / 2003) and was seen in the same rdpwd.sys driver, in which CVE-2012-0002 was found. These changes can be tracked by timestamps in rdpwd.sys before and after the patch. And also in the official change lists for MS11-065 and for MS12-020 .
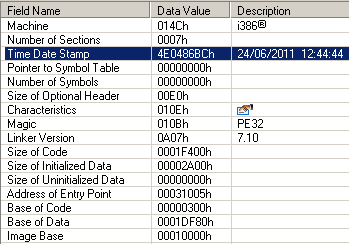
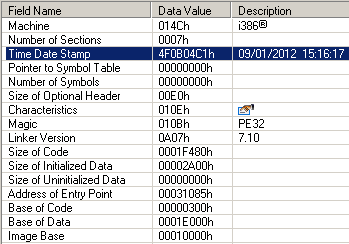
Actually, the main changes were noticed in the HandleAttachUserReq () function , the decompiled version of which looks like this:

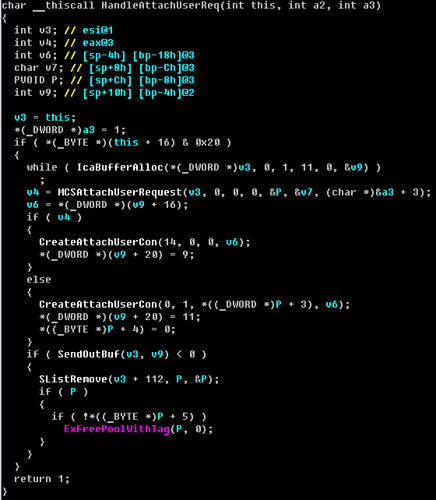
When comparing the corrected driver and driver before the patch, it is clear that there were not so many changes.

It can be seen that an additional check and freeing of memory was added using ExFreePoolWithTag () :

Now let's look at a decompiled version of these changes:


It is the absence of this check that may entail the possibility of remote memory capture and the possibility of unauthorized code execution. Moreover, code execution occurs in the kernel.
A good analysis of CVE-2012-0152 (DoS in Terminal Server) can be found here .
There is an opinion that a working exploit already exists:

Perhaps this is just a fake, but, according to our forecasts, a public exploit will most likely appear next week as part of Metasploit, which will cause a chain reaction of its appearance in malicious programs.
By the way, the vulnerability was relatively recently closed.MS11-065 (August 2011), which allowed DoS (WinXP / 2003) and was seen in the same rdpwd.sys driver, in which CVE-2012-0002 was found. These changes can be tracked by timestamps in rdpwd.sys before and after the patch. And also in the official change lists for MS11-065 and for MS12-020 .


Actually, the main changes were noticed in the HandleAttachUserReq () function , the decompiled version of which looks like this:


When comparing the corrected driver and driver before the patch, it is clear that there were not so many changes.

It can be seen that an additional check and freeing of memory was added using ExFreePoolWithTag () :

Now let's look at a decompiled version of these changes:


It is the absence of this check that may entail the possibility of remote memory capture and the possibility of unauthorized code execution. Moreover, code execution occurs in the kernel.
A good analysis of CVE-2012-0152 (DoS in Terminal Server) can be found here .
There is an opinion that a working exploit already exists:

Perhaps this is just a fake, but, according to our forecasts, a public exploit will most likely appear next week as part of Metasploit, which will cause a chain reaction of its appearance in malicious programs.
