Security Week 05: Printers, Cameras, 7zip and Ethics Issues
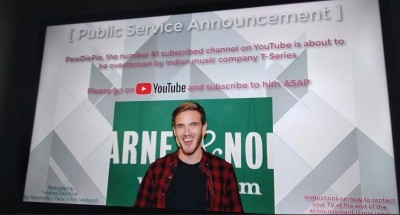 At the end of November 2018, office and home printers around the world printed a message calling to subscribe to YouTube PewDiePie. It happened, of course, without the knowledge of the owners of the printers, and most likely PewDiePie itself has nothing to do with it. The hacker, who calls himself TheHackerGiraffe, attacked more than 50,000 printers configured so that their printing services (Internet Printing Protocol and Line Printer Daemon) were available from the Internet. The list of vulnerable printers was compiled using the specialized search engine Shodan.io, the rest was a matter of technology.
At the end of November 2018, office and home printers around the world printed a message calling to subscribe to YouTube PewDiePie. It happened, of course, without the knowledge of the owners of the printers, and most likely PewDiePie itself has nothing to do with it. The hacker, who calls himself TheHackerGiraffe, attacked more than 50,000 printers configured so that their printing services (Internet Printing Protocol and Line Printer Daemon) were available from the Internet. The list of vulnerable printers was compiled using the specialized search engine Shodan.io, the rest was a matter of technology. Attacking the history of printers has not ended: smart TVs were hacked later, and recently Nest webcams, with similar links to PewDiePie. This generally meaningless idea led to the emergence of a purely criminal service.on "printer guerrilla marketing." Let's talk about these incidents in more detail, and at the same time we will discuss the differences between normal security researchers and such IoT-vandals.
The message, printed on tens of thousands of printers around the world, looked like this:
The hacker Giraffe responsible for hacking readily shared the details of the attack on his twitter (later all messages were deleted). He downloaded the IP list of vulnerable printers from Shodan to a five-dollar cloud server, where he used a combination of open source software to send PDFs to a printer and display a message about hacking on the printer screen. Just a week after this performance, researchers from GreyNoise intercepted another document, a request for which mass print was sent from a single IP, like this:
The document offered “guerilla marketing” services - an analogue of ads on asphalt, only, so to speak, in the digital space. Such events actually occur infrequently. You can compare the printer incident with the security of the routers - in their case, the hacking of the device is usually not advertised, just a quiet profit is derived. Interestingly, the very "Giraffe" was explained to the public by the terms of honest security researchers - such as he "informs the public" about the risks of incorrectly configured devices. The public, of course, was informed, but in an ideal world, the path to improving security lies through working with printer manufacturers and their installers — at least it’s worth finding out why the local print service looks to the Web.
Incidents involving the odious video blogger PewDiePie continued this year. In mid-January, with a similar message calling for subscribing to YouTube, the Atlas multiplayer game was attacked . And last week, the publication Motherboard published a video hacking network video cameras Nest. Vulnerabilities in the Nest infrastructure were not used. Instead, the credential stuffing method was used - an attempt to select a password for the personal account based on leaked databases. If you are wondering exactly how your password will be used from the next leak, - for example, like this. This is not a large-scale attack, but the hacker managed to hack about 300 accounts. Access to your Nest account allows you to control home IoT devices, and you can not only intercept the video stream from the cameras, but also communicate with the owners through them. Sound messages called to subscribe to ... Well, you get the idea.
Finally, immediately after the New Year, the same “Giraffe Hacker” scanned the network in order to search for unprotected devices that support the Chromecast protocol, TV set-top boxes or the smart TV itself. In total, several tens of thousands of devices were found, to which the command was transmitted to play the video, calling for all the same. There are two conclusions from these stories. First, it is advisable not to let the IoT out of the local network. This is so-so advice, since the decision to connect to external servers is usually made by the manufacturer of the smart device. Secondly, such hacker actionism can be used to destroy the reputation of people or companies. PewDiePie has a reputation for being doubtful, but this is not the case: after senseless actions for the sake of public relations, rediscovered methods are adopted by criminals. Especially so simple.
Finally, here's another thread from Twitter. The researcher decided to look at the 7-zip open-source archiver code, which is responsible for creating protected archives. Such archives can only be opened with passwords, and the content is encrypted using the AES algorithm. In extremely emotional expressions, the researcher reports the following: the implementation of the encryption algorithm is far from ideal, an unreliable random number generator is used. In addition, the reliability of open source software as a whole is questioned - after all, the incorrect algorithm was visible to everyone. The quality of developers who talk about paranoid backdoors in the encryption system is discussed, instead of completing their own code to minimum standards.
But, unlike all previous stories, this one seems to end well: the same researcherreported the bug to the developers and helps them correct the situation (which is actually not so bad). Speaking of ethics in the field of information security, we must not forget that people are different, and they react to certain problems in protecting software and devices in different ways, including this way - a bit unrestrained. Ethical hacking is primarily a desire to help fix a bug or vulnerability. But the use of vulnerabilities for the organization of clowning at the expense of unsuspecting victims is not ok.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
