The principle of dominoes or XSS on large sites Runet
On the registration page of the new Mail.ru account, the fields 'First Name' and 'Last Name' were not filtered, as a result of which it was possible to insert scripts and register the user whose name the script was (up to 80 characters). On Mail.ru itself, this vulnerability was not reflected in any way, but manifested itself on those sites that used authorization through Mail.ru, and on those sites that used authorization of sites that used authorization through Mail.ru :)
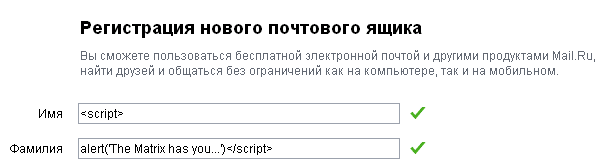
That's how it was before fixing the vulnerability :
So after:

And so during (set 1080p for comfortable viewing):
So it goes.
It seems that at the time of writing this post Mail.ru already fixed this bug.
My previous XSS
UPD post : Received an email from the caliper. Vulnerability closed, thanked.
That's how it was before fixing the vulnerability :

So after:

And so during (set 1080p for comfortable viewing):
So it goes.
It seems that at the time of writing this post Mail.ru already fixed this bug.
My previous XSS
UPD post : Received an email from the caliper. Vulnerability closed, thanked.
