New Year's zip quest 2012 - walkthrough
So, enough time has passed since the launch of the quest , I post the passage and some answers to the “criticism”. In general, there are significantly more positive reviews than negative ones. After solving the last riddle, it was proposed to inform me of the passage of the quest. This was done by about 10 people. How many people downloaded the file - I don’t know.
Let me remind you that the default password is a number, and you can always guess what kind of number it is without getting into the deep jungle of ambiguities (as some participants might have thought). In addition, I warned in advance that participants should be a little familiar with programming.
Level 1A pdf-document with a story about the determinant of a 2x2 matrix and about raising it to the fifth degree is proposed. There is no point here, but you can pay attention to the letters in bold letters forming the word mcmxlviii, which is very similar to writing a number in Roman notation. This number is 1948, it is the password.
Level 2Of course, you can interpret the file from spaces and stars as you like. But how should a person who seeks hidden information in a file reason? He will surely check if there are any hidden characters that are not immediately visible. It will take any normal hex viewer and open a file in it, seeing immediately a 2x2 matrix consisting of numbers 4 7 1 8 in the style of simplified ASCII-art. You might think that the answer is the number 4718 or some other 23 numbers that can be obtained from these numbers. But this is a wrong train of thought, as it leads to ambiguities, and it is believed that there are none. You don’t think that I wrote in vain a text about the qualifier to the fifth degree at the previous level? The determinant is 25, and to the fifth degree it will be equal to 9765625.
Level 3.At this level, a hint. It should be clear that md5 hashes are written out. The first 6 of them have prototypes that are easy to find on the Internet. They form the expression "use your brain and chromosomal crossover". The following 2 hashes cannot be decrypted. Next, you need to look at what a “chromosomal crossover” is and guess that the md5 hashes were split in half, and then the first half of the first hash is connected to the second half of the second and vice versa. After performing the reverse operation, you will find that these hashes correspond to the numbers 1371454 and 131. These two numbers must be multiplied, as indicated by the “multiply them” hint from the following two md5 hashes.
Level 4At this level there was a jamb. Instead of uppercase letters, you must enter the password in lowercase. Despite this jamb, at least 4 people passed the level anyway. Words at this level are not a topic at all, you need to count how many letters are in each letter and do the indicated operations with these numbers. We get a sequence of numbers 21, 14, 7, 19, 5, 9, which corresponds to the letters of the Latin alphabet s, n, g, u, e, i. Obviously, from these letters you can make the word "genius". This is also confirmed by the fact that if the source words are arranged alphabetically, the letters will appear in the correct order.
Level 5. There is some kind of trouble with this level ... Almost everyone brute-force it (in the sense, they broke the password). In fact, from my point of view, it is the simplest. I warned you to be able to use search on the Internet. Find the sequenceA112676 in the encyclopedia of integer sequences. It says that this sequence gives the number of Hamiltonian cycles on a triangular lattice with n nodes on each side. For example, the following figure shows such a lattice for n = 4.
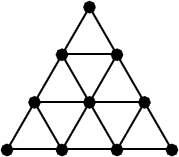
On it you can find 3 Hamiltonian cycles. It is seen that in the original sequence there is no answer for n = 8. It is not difficult to calculate it on a regular home computer by writing a simple program that calculates Hamiltonian cycles by exhaustive search. Of course, if you write anyhow, the program will work for several hours. If you implement simple clipping, then the operating time should not exceed 30 minutes. Many doubted that something needs to be considered, but the hint was that the post is in the section "Sports Programming". You don’t think it’s just that? Answer 1371454. By the way, this number has already met, right?
Although ... brute-force password was probably easier? This is not forbidden in the quest and fits into the category “ability to use some tools”.
Level 6This level (along with the 9th) was most liked, judging by the reviews that came to my mail or in the PM. It can be seen that the text devoted to the assembler yasm is formatted somehow crookedly and unnaturally, suggesting that the text is divided into 10 lines, and the hint says that the answer is 10 letters. If you look closely, you can see that in each line, spaces (code 32) and tabs (code 9) participate as separators between words. If we replace the spaces with the symbol “.”, And the tabs with the symbol “-”, we get a morse code. Armed with a table of correspondence of letters to the sequences of “dots” and “dashes”, we get the word rationlity (intentionally written with an error). This is the password.
Level 7. borrowed the idea from Maria. Remembering the connection between levels 1 and 2, someone will think that once in level 6 it is written about assembler, then the file Level7.asm needs to be compiled. If someone understands assembler and was able to run the program in DOS emulation mode, he received the inscription “You didn't think that it would be as easy as downloading the compiler and running the program, did you? It would be too easy! Use out of the box thinking. ”, In which there isn’t just a malicious emoticon. In fact, I’m sure that many found the answer without this, just by looking at the comments. If we align the comments with the “;” symbol, as is usually done in beautiful programs, we get the numbers 3 5 9 0 2 6. You can smash your head for whatever it means, or you can simply enter 359026 as a password :)
Level 8.For some reason, too brute force. There, in the task file it is written that you need to draw a chessboard and build some convex figure stretched to some points, then calculate the perimeter, area, multiply them, round down and translate into the binary system (why is it so difficult? Inspiration ended, apparently ) At the same time, there are 6 files in the task folder, according to which it was necessary to guess which points on the chessboard should be marked. So,
a.pdf - This is vitamin b5, which is easy to find on the Internet for the phrase that is in this document. So one of the points on the board will be b5.
b.pdf - “Almost 200” is 199. It is easy to guess what the 16th number system is, where there are letters (after all, coordinates on a chessboard are set by letters and numbers). 199 = 0xC7. So this refers to cell c7.
c.pdf - Absolutely dumb rebus. Means E3. This rebus appeared in my perplexity. Initially, the idea was different - in the numerator to depict a picture from Wikipedia, which shows a method of encoding a fractional number with single precision in the IEEE-754 format. But for some reason I thought and forgot about this idea. And still, they would have guessed :)
d.png - This is a major seventh chord from the note “e”. The figure depicts one of the options for staging it on a guitar. It is designated in music through E7.
e.png - The F5 button on the keyboard is encrypted here, which in some cases is used to copy files.
f.jpg - This is Nokia-C3. You can see it in the picture.
Now draw a shape. It is intentionally made simple and symmetrical. In order to be able to guess one or two points if the tips didn’t give in (in fact, how many of the music lessons at school remember what a major seventh chord is and how the chords on a guitar are depicted?).
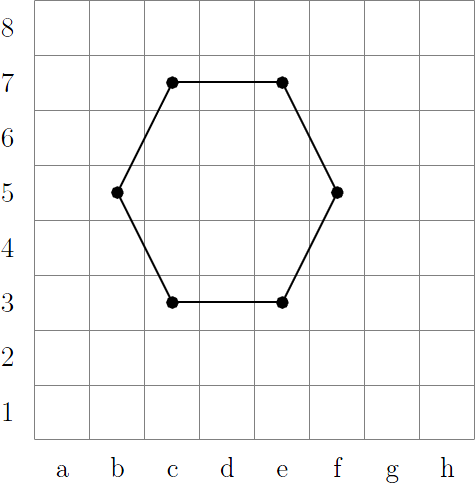
the area of the figure is 12, and the perimeter is 4 + 4 * sqrt (5). We multiply, round down, we get 155. We need to write this number in the binary system as a password.
Level 9The idea was also taken from Mary - I liked the idea of encoding the message in the form of hidden pixels in the image. Before you are 4 squares with flowers. Three of them hint at RGB, and the fourth hints that if you connect them, there will be a shade of gray (in this case, white). But before connecting the squares, you need to make visible the hidden pixels on each of them. This is done by almost any image editing tool that is able to select pixels of a given color. By combining the pieces of the puzzle, we get the password "nsvjkjltw", in which, with certain skills, you can guess the phrase "you're done." This level (along with the 6th) was also liked by many.
Then comes the final picture, in which I asked to inform me about the passage of the quest. There are about 10 people who have done this at the moment. I am sure that many passed and did not bother with notifications.
Now the answer to some "criticism" that has taken place. It is clear that there are always dissatisfied. Obviously, you will not please everyone. People are different and give different tasks to everyone. However, I cannot accept the observation that there are many ambiguities in the tasks. Remember the game “What? Where? When?". There are such tasks when experts get some object or a black box into the hall. Sometimes (though not always) a phrase is said, and then a question is asked such as “name the phrase you entered.” Anything fits into the handed-over subject and hint, absolutely any phrase, but experts still call the hidden phrase correctly (sometimes they are mistaken, true). Why do they guess? Because they know how to see something in the assignment that clearly indicates the answer. Something that makes it almost obvious what exactly “this” is made up, and not “that”. Let's analyze examples of dissatisfied.
I am told that in the first task I wanted to count the letters a, b, c, d, and count something according to the above formula. With such reasoning, you may find that other attempts to combine the letters in any way and other counting options with any complexity are suitable. And I warned that there are NO serious ambiguities. So this logic is obviously wrong, as it leads to too many options. And what's the point then in bold letters? Is it really that simple? From here it was necessary to dance, and not think that your pdf viewer has glitches.
Someone said that in the second task, stars and spaces can be interpreted as numbers in the binary system, and then add them up or do anything with them. Does something in the assignment indicate this? Is it somewhere proposed to add (and why not multiply, divide or subtract?)? Not. So this logic is obviously wrong, as it leads to a mass of options, each of which does not explicitly follow from the task.
Well and so on. I believe that the tasks turned out to be successful in general, if you do not focus on any idea, but try to think more broadly. Therefore, criticism of the ambiguities is not accepted. If there were ambiguities, then they were not so extensive that you could get lost in the options. Those who completed the quest did it calmly and did not seem to complain.
Thank you all for your interest! It was very interesting for me to observe the development of events. Whose turn is next to do puzzles?
Let me remind you that the default password is a number, and you can always guess what kind of number it is without getting into the deep jungle of ambiguities (as some participants might have thought). In addition, I warned in advance that participants should be a little familiar with programming.
Level 1A pdf-document with a story about the determinant of a 2x2 matrix and about raising it to the fifth degree is proposed. There is no point here, but you can pay attention to the letters in bold letters forming the word mcmxlviii, which is very similar to writing a number in Roman notation. This number is 1948, it is the password.
Level 2Of course, you can interpret the file from spaces and stars as you like. But how should a person who seeks hidden information in a file reason? He will surely check if there are any hidden characters that are not immediately visible. It will take any normal hex viewer and open a file in it, seeing immediately a 2x2 matrix consisting of numbers 4 7 1 8 in the style of simplified ASCII-art. You might think that the answer is the number 4718 or some other 23 numbers that can be obtained from these numbers. But this is a wrong train of thought, as it leads to ambiguities, and it is believed that there are none. You don’t think that I wrote in vain a text about the qualifier to the fifth degree at the previous level? The determinant is 25, and to the fifth degree it will be equal to 9765625.
Level 3.At this level, a hint. It should be clear that md5 hashes are written out. The first 6 of them have prototypes that are easy to find on the Internet. They form the expression "use your brain and chromosomal crossover". The following 2 hashes cannot be decrypted. Next, you need to look at what a “chromosomal crossover” is and guess that the md5 hashes were split in half, and then the first half of the first hash is connected to the second half of the second and vice versa. After performing the reverse operation, you will find that these hashes correspond to the numbers 1371454 and 131. These two numbers must be multiplied, as indicated by the “multiply them” hint from the following two md5 hashes.
Level 4At this level there was a jamb. Instead of uppercase letters, you must enter the password in lowercase. Despite this jamb, at least 4 people passed the level anyway. Words at this level are not a topic at all, you need to count how many letters are in each letter and do the indicated operations with these numbers. We get a sequence of numbers 21, 14, 7, 19, 5, 9, which corresponds to the letters of the Latin alphabet s, n, g, u, e, i. Obviously, from these letters you can make the word "genius". This is also confirmed by the fact that if the source words are arranged alphabetically, the letters will appear in the correct order.
Level 5. There is some kind of trouble with this level ... Almost everyone brute-force it (in the sense, they broke the password). In fact, from my point of view, it is the simplest. I warned you to be able to use search on the Internet. Find the sequenceA112676 in the encyclopedia of integer sequences. It says that this sequence gives the number of Hamiltonian cycles on a triangular lattice with n nodes on each side. For example, the following figure shows such a lattice for n = 4.

On it you can find 3 Hamiltonian cycles. It is seen that in the original sequence there is no answer for n = 8. It is not difficult to calculate it on a regular home computer by writing a simple program that calculates Hamiltonian cycles by exhaustive search. Of course, if you write anyhow, the program will work for several hours. If you implement simple clipping, then the operating time should not exceed 30 minutes. Many doubted that something needs to be considered, but the hint was that the post is in the section "Sports Programming". You don’t think it’s just that? Answer 1371454. By the way, this number has already met, right?
Although ... brute-force password was probably easier? This is not forbidden in the quest and fits into the category “ability to use some tools”.
Level 6This level (along with the 9th) was most liked, judging by the reviews that came to my mail or in the PM. It can be seen that the text devoted to the assembler yasm is formatted somehow crookedly and unnaturally, suggesting that the text is divided into 10 lines, and the hint says that the answer is 10 letters. If you look closely, you can see that in each line, spaces (code 32) and tabs (code 9) participate as separators between words. If we replace the spaces with the symbol “.”, And the tabs with the symbol “-”, we get a morse code. Armed with a table of correspondence of letters to the sequences of “dots” and “dashes”, we get the word rationlity (intentionally written with an error). This is the password.
Level 7. borrowed the idea from Maria. Remembering the connection between levels 1 and 2, someone will think that once in level 6 it is written about assembler, then the file Level7.asm needs to be compiled. If someone understands assembler and was able to run the program in DOS emulation mode, he received the inscription “You didn't think that it would be as easy as downloading the compiler and running the program, did you? It would be too easy! Use out of the box thinking. ”, In which there isn’t just a malicious emoticon. In fact, I’m sure that many found the answer without this, just by looking at the comments. If we align the comments with the “;” symbol, as is usually done in beautiful programs, we get the numbers 3 5 9 0 2 6. You can smash your head for whatever it means, or you can simply enter 359026 as a password :)
Level 8.For some reason, too brute force. There, in the task file it is written that you need to draw a chessboard and build some convex figure stretched to some points, then calculate the perimeter, area, multiply them, round down and translate into the binary system (why is it so difficult? Inspiration ended, apparently ) At the same time, there are 6 files in the task folder, according to which it was necessary to guess which points on the chessboard should be marked. So,
a.pdf - This is vitamin b5, which is easy to find on the Internet for the phrase that is in this document. So one of the points on the board will be b5.
b.pdf - “Almost 200” is 199. It is easy to guess what the 16th number system is, where there are letters (after all, coordinates on a chessboard are set by letters and numbers). 199 = 0xC7. So this refers to cell c7.
c.pdf - Absolutely dumb rebus. Means E3. This rebus appeared in my perplexity. Initially, the idea was different - in the numerator to depict a picture from Wikipedia, which shows a method of encoding a fractional number with single precision in the IEEE-754 format. But for some reason I thought and forgot about this idea. And still, they would have guessed :)
d.png - This is a major seventh chord from the note “e”. The figure depicts one of the options for staging it on a guitar. It is designated in music through E7.
e.png - The F5 button on the keyboard is encrypted here, which in some cases is used to copy files.
f.jpg - This is Nokia-C3. You can see it in the picture.
Now draw a shape. It is intentionally made simple and symmetrical. In order to be able to guess one or two points if the tips didn’t give in (in fact, how many of the music lessons at school remember what a major seventh chord is and how the chords on a guitar are depicted?).

the area of the figure is 12, and the perimeter is 4 + 4 * sqrt (5). We multiply, round down, we get 155. We need to write this number in the binary system as a password.
Level 9The idea was also taken from Mary - I liked the idea of encoding the message in the form of hidden pixels in the image. Before you are 4 squares with flowers. Three of them hint at RGB, and the fourth hints that if you connect them, there will be a shade of gray (in this case, white). But before connecting the squares, you need to make visible the hidden pixels on each of them. This is done by almost any image editing tool that is able to select pixels of a given color. By combining the pieces of the puzzle, we get the password "nsvjkjltw", in which, with certain skills, you can guess the phrase "you're done." This level (along with the 6th) was also liked by many.
Then comes the final picture, in which I asked to inform me about the passage of the quest. There are about 10 people who have done this at the moment. I am sure that many passed and did not bother with notifications.
Now the answer to some "criticism" that has taken place. It is clear that there are always dissatisfied. Obviously, you will not please everyone. People are different and give different tasks to everyone. However, I cannot accept the observation that there are many ambiguities in the tasks. Remember the game “What? Where? When?". There are such tasks when experts get some object or a black box into the hall. Sometimes (though not always) a phrase is said, and then a question is asked such as “name the phrase you entered.” Anything fits into the handed-over subject and hint, absolutely any phrase, but experts still call the hidden phrase correctly (sometimes they are mistaken, true). Why do they guess? Because they know how to see something in the assignment that clearly indicates the answer. Something that makes it almost obvious what exactly “this” is made up, and not “that”. Let's analyze examples of dissatisfied.
I am told that in the first task I wanted to count the letters a, b, c, d, and count something according to the above formula. With such reasoning, you may find that other attempts to combine the letters in any way and other counting options with any complexity are suitable. And I warned that there are NO serious ambiguities. So this logic is obviously wrong, as it leads to too many options. And what's the point then in bold letters? Is it really that simple? From here it was necessary to dance, and not think that your pdf viewer has glitches.
Someone said that in the second task, stars and spaces can be interpreted as numbers in the binary system, and then add them up or do anything with them. Does something in the assignment indicate this? Is it somewhere proposed to add (and why not multiply, divide or subtract?)? Not. So this logic is obviously wrong, as it leads to a mass of options, each of which does not explicitly follow from the task.
Well and so on. I believe that the tasks turned out to be successful in general, if you do not focus on any idea, but try to think more broadly. Therefore, criticism of the ambiguities is not accepted. If there were ambiguities, then they were not so extensive that you could get lost in the options. Those who completed the quest did it calmly and did not seem to complain.
Thank you all for your interest! It was very interesting for me to observe the development of events. Whose turn is next to do puzzles?
