Safe and comfortable Internet access or how to protect your network from Internet threats without inconvenience
Listening to a recent interview with the respected Evgeny Kaspersky on RussiaToday , where he expressed the idea that most company employees will soon have no Internet access, I remembered the practice of many companies that completely separate the internal network from the Internet, providing access to the Internet only from separately allocated computers , and decided to express his thoughts on this aspect of information security.
The practice of completely separating the local network and Internet access is quite correct and, according to many IT experts, is the only 100% way to protect corporate data. However, this method, in addition to the large costs of its implementation, has another very significant drawback, namely the inconvenience of using the Internet. The lack of comfortable access to the Internet entails not only direct losses in the form of a decrease in the efficiency of employees, but also indirect ones, such as a decrease in employee loyalty and prestige of work, which is a direct reason for the growth of company costs.
A typical diagram of such a network looks like this:
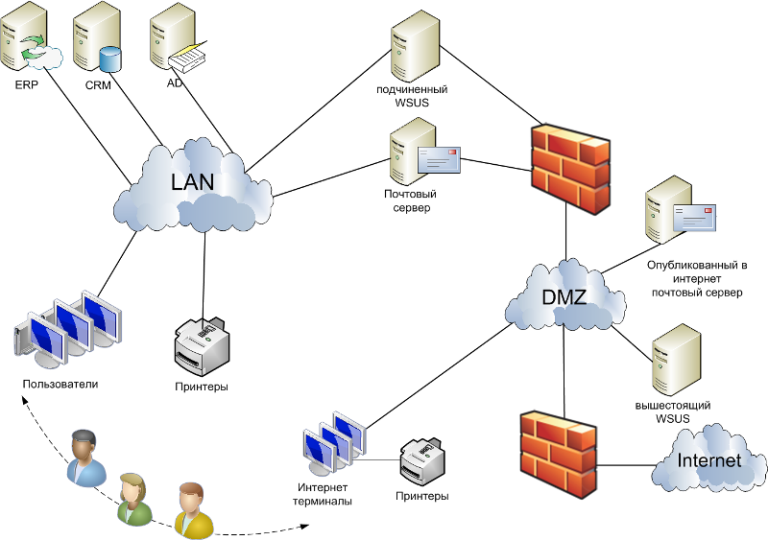
This scheme completely separates jobs from the Internet and even if a trojan gets onto an employee’s computer, it will not be able to transfer stolen information to the Internet. Also, a network built according to this scheme prevents the unauthorized distribution of confidential information by an employee of the company via the Internet.
And yet, with all the security, this scheme has a significant drawback - this is the lack of flexibility and comfortable operation, since only two conditions are possible: the employee either does not have Internet access at all, or he has it on a separate machine.
To solve these problems and allow the employee to work fully, there is an interesting solution in the form of application virtualization, Microsoft calls this technology App-V.
Microsoft Application Virtualization (App-V) technology allows you to make programs available to user computers without having to install them directly on these computers. Thanks to a process called application virtualization, which allows each application to run in its own stand-alone virtual environment on a client computer. Virtualized applications are isolated from each other. This avoids conflicts between applications, but they can still interact with the client computer .
This is done as follows: in the DMZ we install a terminal server on which we allow Internet traffic, configure the Internet browser as a virtual application, prohibit the use of a buffer and the use of local resources through RDP. We also set up Remote Desktop Gateway in DMZ and allow access to it via https from the company’s network.
Sample diagram:
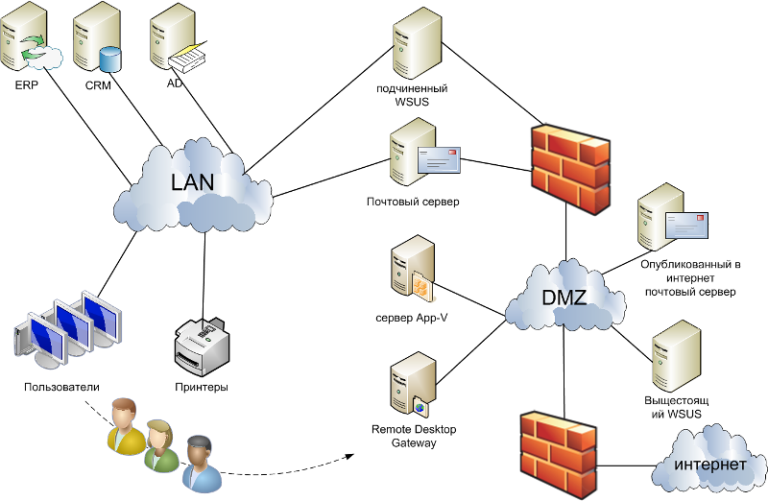
So, what do we have as a result:
Company users, isolated from the Internet by the internal network, go to the internal web page of the RDG service, on which an Internet browser is published or launch an RDP file.
After authentication, if there are sufficient rights, the user launches a browser, the operation of which is not different for the user from the browser on his local machine. In reality, the browser works on a terminal server, it can only display information on the monitor and receive commands from the keyboard and mouse, without access to other resources of the user computer or local network. Thus, with quite comfortable work, we get a browser completely isolated from the computer and the internal network with Internet access.
Related article links:
Application Virtualization
Remote Desktop Gateway
Regards, Servilon.ru Team
The practice of completely separating the local network and Internet access is quite correct and, according to many IT experts, is the only 100% way to protect corporate data. However, this method, in addition to the large costs of its implementation, has another very significant drawback, namely the inconvenience of using the Internet. The lack of comfortable access to the Internet entails not only direct losses in the form of a decrease in the efficiency of employees, but also indirect ones, such as a decrease in employee loyalty and prestige of work, which is a direct reason for the growth of company costs.
A typical diagram of such a network looks like this:

This scheme completely separates jobs from the Internet and even if a trojan gets onto an employee’s computer, it will not be able to transfer stolen information to the Internet. Also, a network built according to this scheme prevents the unauthorized distribution of confidential information by an employee of the company via the Internet.
And yet, with all the security, this scheme has a significant drawback - this is the lack of flexibility and comfortable operation, since only two conditions are possible: the employee either does not have Internet access at all, or he has it on a separate machine.
To solve these problems and allow the employee to work fully, there is an interesting solution in the form of application virtualization, Microsoft calls this technology App-V.
Microsoft Application Virtualization (App-V) technology allows you to make programs available to user computers without having to install them directly on these computers. Thanks to a process called application virtualization, which allows each application to run in its own stand-alone virtual environment on a client computer. Virtualized applications are isolated from each other. This avoids conflicts between applications, but they can still interact with the client computer .
This is done as follows: in the DMZ we install a terminal server on which we allow Internet traffic, configure the Internet browser as a virtual application, prohibit the use of a buffer and the use of local resources through RDP. We also set up Remote Desktop Gateway in DMZ and allow access to it via https from the company’s network.
Sample diagram:

So, what do we have as a result:
Company users, isolated from the Internet by the internal network, go to the internal web page of the RDG service, on which an Internet browser is published or launch an RDP file.
After authentication, if there are sufficient rights, the user launches a browser, the operation of which is not different for the user from the browser on his local machine. In reality, the browser works on a terminal server, it can only display information on the monitor and receive commands from the keyboard and mouse, without access to other resources of the user computer or local network. Thus, with quite comfortable work, we get a browser completely isolated from the computer and the internal network with Internet access.
Related article links:
Application Virtualization
Remote Desktop Gateway
Regards, Servilon.ru Team
