HackBattle 2.0 competition at Positive Hack Days: how the school cafeteria attacked ICO

Last May, the HackBattle competition was held at Positive Hack Days VII for the first time. Our booth attracted a lot of attention from the audience. Then, almost 100 information security specialists took part in the competition, and so many spectators came to see the final in the large hall that it was impossible to push the stage (for more details see last year’s report ). Inspired by such interest from the professional community, we decided to run HackBattle 2.0 on PHDays 8. We tell how the competition went this year, and also publish the tasks from the competition so that you can try to solve them.
Contest format and rules
Competitions were held throughout the PHDays. On the first day there were qualifying tests: we chose two of the
Selection
Like a year ago, at the qualifying stage, we suggested that participants solve the CTF format problem for speed. For the solution of 10 problems 35 minutes were given. For each task, a certain number of points were awarded depending on the difficulty. Participation in the selection could only once.
This time we took into account the wishes of the participants of the first HackBattle and provided an opportunity to work not only on pre-prepared workstations, but also on our laptops.

A separate table with blackjack and patch cords for those who came with laptops.

Qualifying test participants
It was not easy to determine the people who will reach the final and will be able to adequately cope with the solution of the problem under pressure from the audience. Until the end of the qualifying rounds it was absolutely unclear who would be the finalist - the struggle was very sharp. The difference between the leaders of the scorbord was only 50-100 points, and in cases when the score was equal, it was only a few seconds! And only at six o'clock in the evening, having closed the qualifying competitions, we were able to determine the finalists: they were Vladislav “W3bPwn3r” Lazarev and Arthur “inviz @ penis” Khashaev.
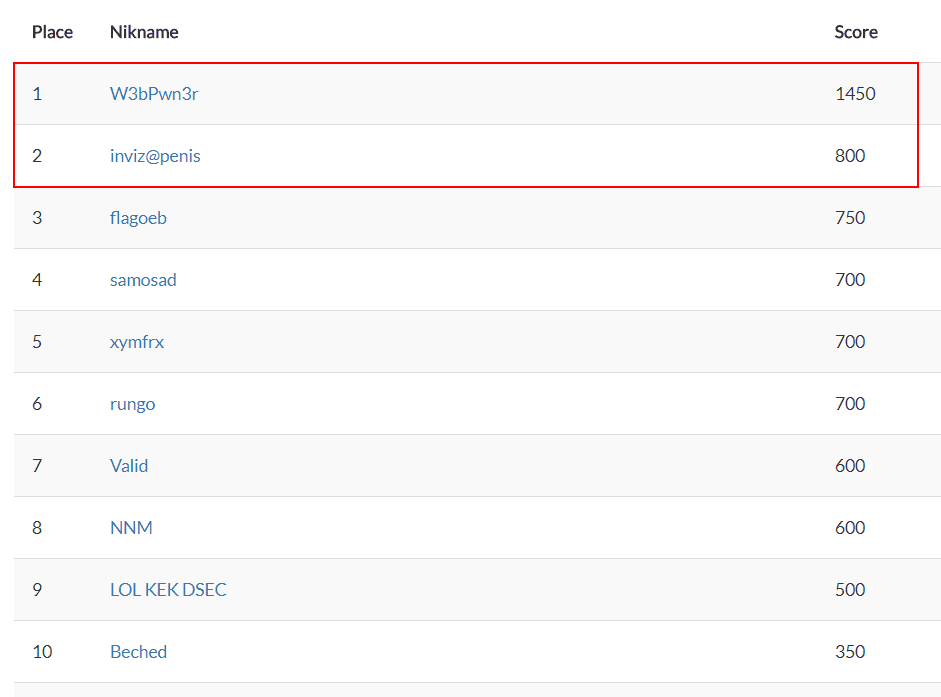
Standings

Problems solved by a finalist W3bPwn3r

Problems solved by a finalist inviz @ penis
The final
On May 16, at 14:00 sharp, the final stage HackBattle 2.0 took place on the main stage in the congress hall. Like a year ago, everything that happened on the hacker monitors was streamed to the big screen and commented on by Positive Technologies experts. For the convenience of the spectators, the monitor of each of the finalists was separately duplicated on the screens of televisions standing on the sides of the main stage.

Battle of the strongest
As a final test, we offered participants to attack the same goal: this year the hackers fell victim to the server on which the school canteen's ICO was held.
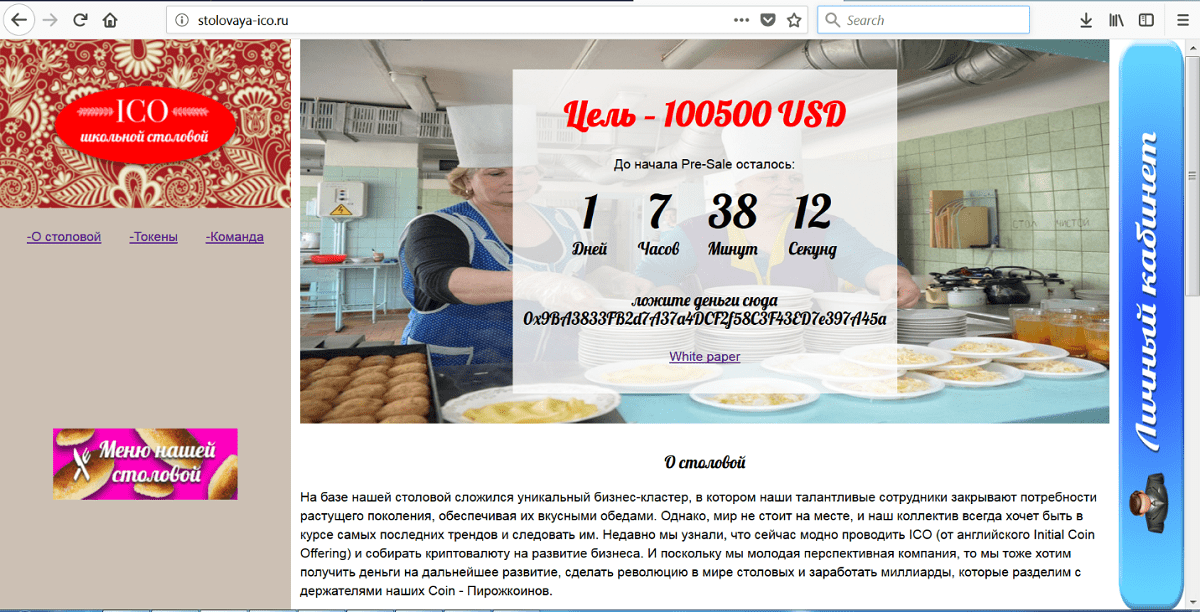
ICO school cafeteria website
According to the legend, hackers should have time to replace the purse placed on the main page of the website with any other one before the start of the ICO presale-stage (you can download the task at the end of the article). Note that the task consisted of several stages and could be solved in various ways.
Over the past six months, experts from Positive Technologies have conducted many ICO pentests and in each project discovered vulnerabilities of varying degrees of danger. Information about the compromise of the ICO is increasingly appearing in the media. It is obvious that in this area the issue of information security is clearly not a priority. We decided to dedicate the final to this topic in order to draw attention to the security of cryptocurrency services.
The fight lasted 20 minutes (the full version of the final, as well as other video materials of the conference, can be viewed on the PHDays websitephdays.com/ru/broadcast/ ). The victory in a tense battle was won by Vladislav “W3bPwn3r” Lazarev, who was the first to cope with the task.

The winner is Vladislav Lazarev.
After the contest, we interviewed the finalists and found out about their impressions.
“First of all I want to note the high level of organization of the infrastructure and the quality of the tasks themselves. It was pleasantly surprised by the attention of a large number of people, although it seemed that it was more difficult to carry out seemingly familiar actions when the crowd looked at your monitor. It would be more fun if the qualifying stage was held in the same format as the final, ”said Vladislav Lazarev .
“HackBattle is definitely the very event that allowed us to shake things up during the conference,” said Arthur Khashayev . - From surprises: in the final round, the Internet did not work right away, I had to spend some time importing the certificate from the proxy. At the same time, the ICO website of the school canteen was made famous. I would like to especially note the work of commentators who made this battle truly dynamic and did not let the audience get bored. ”
The technical details of organizing the stream, the work of the scorbord and its synchronization with the workstations provided by the organizers are outlined in the blog of Anatoly Ivanov .
Tasks from the competition
Все задачи, кроме десятой, являются виртуальными машинами в формате OVA. Десятая задача — бинарный файл для Unix. Все виртуальные машины имеют статические адреса из подсети 172.30.0.0/24, шлюз 172.30.0.1, DNS 8.8.8.8. Для переконфигурирования указаны доступы к виртуальным машинам.
NotSoEvil corp has developed a clone application with blackjack and Brian Crépes. Can you find the sensitive information there?
static.ptsecurity.com/phdays/2018/hackbattle/1.ova
phd:ckjyktnbnyfpfgfl
172.30.0.15
Our rate changer is rocket science, can you make it through to the secret info?
static.ptsecurity.com/phdays/2018/hackbattle/2.ova
phd:cfvsqkexibqgfhfljrc
172.30.0.16
Bet you can't beat me! Prove different.
Unix user would know what is going on here:
static.ptsecurity.com/phdays/2018/hackbattle/3.ova
phd:vjzgeirfnsxtndpfgfl
172.30.0.17
Are you good enough at source code analysis?
static.ptsecurity.com/phdays/2018/hackbattle/4.ova
phd:zboegjlheuelheue
172.30.0.18
This NES games search engine seems to have some vulnerabilities. Unfortunately they claim to have bought a new age firewall, can you make it through and get the private game.
static.ptsecurity.com/phdays/2018/hackbattle/5.ova
ssh: task:13372018
172.30.0.13
Find out what this meme is hiding.
Note that this tasks has two flags. Send the second flag to The Meme's Mystery (hard part)
The meme's intelligence has increased, but the flag still seems to be reachable
Note that this is the second flag of the task
static.ptsecurity.com/phdays/2018/hackbattle/6.ova
ssh: task:13372018
172.30.0.12
In memorial of old JWT bugs, the task we solve…
static.ptsecurity.com/phdays/2018/hackbattle/7.ova
ssh: task:13372018
172.30.0.11:5000/
Robots are back, defeat them again and save the princess, mighty warrior!
static.ptsecurity.com/phdays/2018/hackbattle/8.ova
dev;V3ryHardP@ssw0rd12345
172.30.0.20
We have developed a nice website to get you some comfortable tickets, is it secure enough?
static.ptsecurity.com/phdays/2018/hackbattle/9.ova
dev;V3ryHardP@ssw0rd12345
172.30.0.19
This program prints flag, go get it. Oops, nearly forgot to say that it is ouputed to stdout. Hope you are still able to get it
static.ptsecurity.com/phdays/2018/hackbattle/10
static.ptsecurity.com/phdays/2018/hackbattle/Final.ova
dev;V3ryHardP@ssw0rd12345
IP-address 172.30.0.21
In hosts file add strings:
172.30.0.21 stolovaya-ico.ru
172.30.0.21 www.stolovaya-ico.ru
172.30.0.21 blog.stolovaya-ico.ru
172.30.0.21 www.blog.stolovaya-ico.ru
Entry point: stolovaya-ico.ru
1. WhiteHub (150)
NotSoEvil corp has developed a clone application with blackjack and Brian Crépes. Can you find the sensitive information there?
static.ptsecurity.com/phdays/2018/hackbattle/1.ova
phd:ckjyktnbnyfpfgfl
172.30.0.15
2. Rates (350)
Our rate changer is rocket science, can you make it through to the secret info?
static.ptsecurity.com/phdays/2018/hackbattle/2.ova
phd:cfvsqkexibqgfhfljrc
172.30.0.16
3. Mine is bigger (150)
Bet you can't beat me! Prove different.
Unix user would know what is going on here:
static.ptsecurity.com/phdays/2018/hackbattle/3.ova
phd:vjzgeirfnsxtndpfgfl
172.30.0.17
4. PHP Power (100)
Are you good enough at source code analysis?
static.ptsecurity.com/phdays/2018/hackbattle/4.ova
phd:zboegjlheuelheue
172.30.0.18
5. Too Smart (450)
This NES games search engine seems to have some vulnerabilities. Unfortunately they claim to have bought a new age firewall, can you make it through and get the private game.
static.ptsecurity.com/phdays/2018/hackbattle/5.ova
ssh: task:13372018
172.30.0.13
6. The Meme's Mystery — ez part (100)
Find out what this meme is hiding.
Note that this tasks has two flags. Send the second flag to The Meme's Mystery (hard part)
The Meme's Mystery — ez part (350)
The meme's intelligence has increased, but the flag still seems to be reachable
Note that this is the second flag of the task
static.ptsecurity.com/phdays/2018/hackbattle/6.ova
ssh: task:13372018
172.30.0.12
7. JWT strikes back (50)
In memorial of old JWT bugs, the task we solve…
static.ptsecurity.com/phdays/2018/hackbattle/7.ova
ssh: task:13372018
172.30.0.11:5000/
8. Robots Strike Back (100)
Robots are back, defeat them again and save the princess, mighty warrior!
static.ptsecurity.com/phdays/2018/hackbattle/8.ova
dev;V3ryHardP@ssw0rd12345
172.30.0.20
9. Ticket to ride (250)
We have developed a nice website to get you some comfortable tickets, is it secure enough?
static.ptsecurity.com/phdays/2018/hackbattle/9.ova
dev;V3ryHardP@ssw0rd12345
172.30.0.19
10. Trace Me (50)
This program prints flag, go get it. Oops, nearly forgot to say that it is ouputed to stdout. Hope you are still able to get it
static.ptsecurity.com/phdays/2018/hackbattle/10
Final
static.ptsecurity.com/phdays/2018/hackbattle/Final.ova
dev;V3ryHardP@ssw0rd12345
IP-address 172.30.0.21
In hosts file add strings:
172.30.0.21 stolovaya-ico.ru
172.30.0.21 www.stolovaya-ico.ru
172.30.0.21 blog.stolovaya-ico.ru
172.30.0.21 www.blog.stolovaya-ico.ru
Entry point: stolovaya-ico.ru
Authors : Dmitry Galecha, Anatoly Ivanov, Alexander Morozov, Positive Technologies.
