No entry for unauthorised people
Have you ever had the idea that the idea of using a username and password to enter the system is somewhat outdated? Why, having a USB flash drive in one pocket, a phone in the other, and installed SSH on the computer with configured authentication using keys, do we continue to enter these confusing passwords?
Passwords and accounts were invented in the era of large mainframes, hippies, the war in Afghanistan and large analog tape recorders, the most technological component of which were transistors. Back then, using passwords to enter the mainframe really looked cool. You could come up with a combination like sexhero or iamsuperman and really be proud of yourself.
Today, passwords look not only archaic, but also a terribly inconvenient thing, old pontoon combinations no longer work, and instead they have to come up with furious character sets that are not only unrealistic to remember, but also problematic to enter the first time. We live in the XXI century, we have access to a huge number of gadgets and technical tools that offer a much simpler and higher-quality authentication mechanism, but we continue to drive in passwords, swearing at the entire apartment with every unsuccessful attempt to enter the system. It's time to fix it.
In this article, I’ll talk about how to get rid of passwords once and for all and turn my computer into a truly technologically advanced device, to enter which you just need to insert a USB flash drive, look at a webcam or just put a cell phone on the table.
The key is the simplest and most effective method of protecting anything. We use keys daily: to turn on the car engine, to enter the apartment, to unlock drawers and cabinets. The keys are convenient and easy to manufacture, thanks to modern programmable locks they are not afraid to lose. Many times, humanity has tried to come up with a replacement for keys, but all attempts have failed (we all remember what the idea of using combination locks on access doors led to). Why do not we use such a good and time-tested technology to protect computers?
A modern analogue of the key is a USB flash drive. Regardless of the purpose for which you usually use a USB flash drive, you can always make a full-fledged high-tech key from it, using which entering the system will be as easy as unlocking the door to the apartment.
There are several ways to do this, but the simplest and most universal method is to use the pam_usb PAM module , which will check each USB flash drive inserted into the computer for compliance with the specified requirements and, depending on the result, unlock or block the user account.
No modification of the partition table or information stored on the flash drive is required. To identify the “correct” flash drive, its serial number, model, manufacturer, as well as a set of random data that is written to the backup area of the flash drive and changes with each successful authentication (if someone copies your flash drive, but you will be able to log in before the attacker) , the data will be changed, and its copy will no longer work). In case of loss, there will always be the opportunity to log in using the password and transcode pam_usb to a new USB flash drive. Also, as a key, you can use various memory cards (SD, MMC) and other removable drives.
Getting started with pam_usb is pretty simple. Complete system configuration consists of five steps.
1.We put the libpam_usb.so library and module management utilities:
2. We take the USB flash drive that we are going to use as the key, insert it into the USB port and execute the following command:
So pam_usb will collect all the necessary information about the flash drive, add it to its database and write 2 Kb random data. Udisks will be used to search for a flash drive in the system (the “name” argument is used here to give the flash drive an arbitrary name, and not to indicate its device file), so it is important that other external drives are disabled for the duration of this command.
3. Now let pam_usb understand that this flash drive is associated with the account we need (the path will be vasya):
4.We start checking the correctness of the collected data in case the flash drive was not correctly identified. Or we forgot to disconnect some other drive, and it was used instead of what we needed:
5. Add pam_usb to the list of modules necessary for successful user authentication. On Ubuntu and other Debian-based distributions, this is done by modifying the /etc/pam.d/common-auth file. It is necessary to find a line similar to the following (it may be different):
So we will tell PAM that before the login of any user you need to give control to the pam_usb module, which will check the presence of the desired flash drive, and only in case of failure of this operation to request a password. Therefore, if you want to let the user in only by flash drive, completely blocking the account in case of failure, the word "sufficient" should be replaced by the word "required".
In principle, all this should be enough for the system to just work (try to log out and log in to check this), however, the functionality of pam_usb can be slightly expanded if you use the pamusb-agent daemon.
The task of pamusb-agent is to automate the work of locking and unlocking a user account when removing and sticking a flash drive into a computer. For the agent to work, you need to add the following lines to the configuration file /etc/pamusb.conf: This is the recipe for Gnome. To use pamusb-agent with other environments, the gnome-screensaver-command --lock and gnome-screensaver-command --deactivate commands must be changed. Now you can run pamusb-agent and check its operability: If everything works fine, you can add it to autorun:
The pam_usb module is conveniently used as a protection method for laptops equipped with a card reader. You can carry a small SD card in your wallet or internal pocket and stick it into your laptop without worrying about the way it will interfere (as is the case with a USB flash drive). However, this approach will look somewhat archaic if the laptop is already equipped with a fingerprint scanner.
Laptops with a fingerprint scanner are produced by many manufacturers. As a rule, they are not much more expensive than other models with similar characteristics, however, their fingerprint sensor works only in Windows. To fix this, freedesktop.org launched the fprint project., within the framework of which an open implementation of the library for fingerprint recognition and the corresponding PAM-module was developed, which allows you to use the library's capabilities during user login and other account manipulations.
Today, libfprint is in any distribution, so you can install it using any package manager:
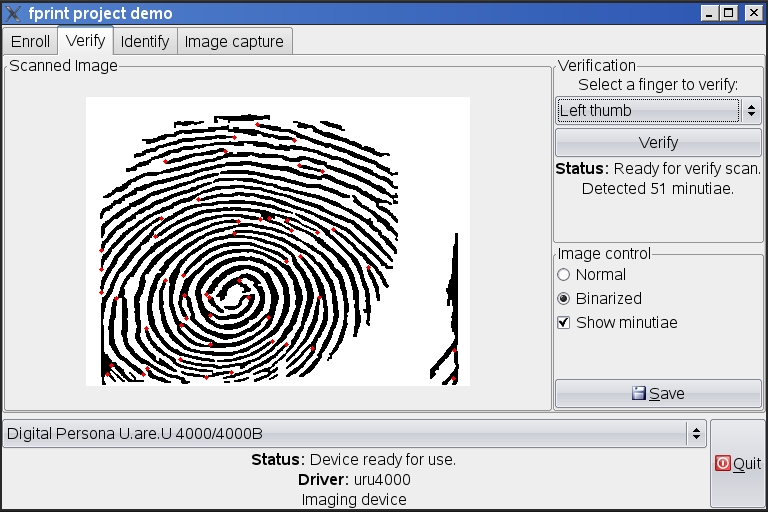
Next, the scanner can be checked using a special demo program with a graphical interface:
If everything works correctly and without failures, you can start setting up authentication. To do this, run the pam_fprint_enroll program, which will allow you to make a reference fingerprint cast, which will then be used to identify its owner:
The number 7 here means the index finger of the right hand. The fprint system numbers fingers from left to right, so that the number 1 will indicate the little finger of the left hand, and 10 - the little finger of the right.
When the cast is ready, add the pam_fprint module to the stack of PAM modules of all applications, for this, open the /etc/pam.d/common-auth file, find the same line “auth required pam_unix.so” and add the line directly in front of it, responsible for loading pam_fprint:
At the next login, everything should work.

Fingers are not the only thing that distinguishes people from each other. We all have different faces, so the system can use the face shot taken by the webcam to identify the user. This is not particularly security, since the attacker can show the camera a regular photo printed on paper, but will make a very strong impression on friends and acquaintances.
Linux distributions do not have built-in face recognition tools, but you can add them by installing a software package called pam-face-authentication , which includes a library that implements a face recognition algorithm, a PAM module for authentication and an application for generating a reference image .
All this can be collected from source or installed from third-party repositories in Ubuntu. Since the project is still raw, and the packages are not prepared for all distributions, we will consider both installation options. So, for installation from source we need packages with a compiler, linker and header files for all the dependencies. In Ubuntu (and in other distributors) you can install them by executing one command:
Next, download the source from the project page and unpack: To build, use cmake, so everything is simple: To install an already precompiled package in Ubuntu, you can use the antonio.chiurazzi repository: After the installation is complete, run the tutorial:
Turn your face in front of the camera, constantly pressing the “Capture” button. It is important to take at least a dozen photos so that the system learns to recognize your face from any angle. It will also be nice to take photos in different lighting conditions. Do not forget to test the system.
Now add the pam_face_authentication.so module to the stack of loaded PAM modules. To do this, open the file /etc/pam.d/gdm or /etc/pam.d/kdm (if you use KDE) and add the following line to its beginning:
The file /etc/pam.d/common-auth should not be changed , since it is used not only by graphical login managers, but also by the standard console / bin / login and / bin / su, and pam_face requires access to X's.
You also need to create a profile for the new PAM module. Open (create) the file / usr / share / pam-configs / face_authentication with the following contents: And activate it:
A cell phone is a symbol of the 21st century. We have long been accustomed to the fact that it can be used not only for calls, but also for Internet access, games, listening to music, watching videos and even paying bills. But can it be used as a key to enter a computer system?
Of course yes. Like a USB flash drive, the phone has many features that make it unique. These are all the same manufacturer and model identifiers, serial number, MAC addresses, IMEI, in the end. Any of them can be used to uniquely identify the device and its owner, but we will focus only on one of them - the MAC address of the Bluetooth interface.
Any, even a very ancient and simple phone has support for the Bluetooth protocol and, as a result, a unique MAC address that transmits to the network in response to any request to search for devices with another Bluetooth adapter. Many modern laptops have such an adapter on board, and its external USB option costs a penny, so for us a blue tooth would be an ideal option for setting password-free and wireless authentication. I went into the room - access was open, went out - the system is locked.
We take the phone, turn on Bluetooth, make it so that it is "visible" to other devices. We sit down at the computer and run the hcitool utility (included in the bluez-utils package) in the device search mode:
We get the name of our device and its MAC address, copy the latter to the clipboard. Install the libpam_blue package (or pam_blue, where as):
We create the configuration file /etc/security/bluesscan.conf and write the following into it: Save the file, open the familiar /etc/pam.d/common-auth config and add a line before the line containing "pam_unix.so". Now to enter the system it will be enough to put the phone next to the laptop and enter a name. Next, control will be transferred to the pam_blue module, which will scan the network, find the MAC address of the phone and let the user in. Otherwise, you will have to enter a password.
Setting up passwordless authentication using alternative methods on Linux is pretty simple. To do this, you do not need to be a seasoned geek, be able to write code or have deep knowledge in the field of security, everything is done in a few minutes and works amazingly efficiently. You can say that most of these methods are potentially unsafe and easily bypassed, but before you do this, think about how secure ordinary passwords are.
The safety of a machine that can be accessed by outsiders is pure myth. Getting around standard password protection is easy. There are a huge number of ways to do this, and all of them are known even to children. A password is just a small sign that carries information that the computer has an owner and does not want to see uninvited guests. Applying the methods described in the article, we will not make the system more vulnerable, but we will be able to make our life easier and more convenient.

Hacker Magazine, September (09) 152
Evgeny Zobnin ( execbit.ru ) .
Subscribe to Hacker

Passwords and accounts were invented in the era of large mainframes, hippies, the war in Afghanistan and large analog tape recorders, the most technological component of which were transistors. Back then, using passwords to enter the mainframe really looked cool. You could come up with a combination like sexhero or iamsuperman and really be proud of yourself.
Today, passwords look not only archaic, but also a terribly inconvenient thing, old pontoon combinations no longer work, and instead they have to come up with furious character sets that are not only unrealistic to remember, but also problematic to enter the first time. We live in the XXI century, we have access to a huge number of gadgets and technical tools that offer a much simpler and higher-quality authentication mechanism, but we continue to drive in passwords, swearing at the entire apartment with every unsuccessful attempt to enter the system. It's time to fix it.
In this article, I’ll talk about how to get rid of passwords once and for all and turn my computer into a truly technologically advanced device, to enter which you just need to insert a USB flash drive, look at a webcam or just put a cell phone on the table.
High tech key
The key is the simplest and most effective method of protecting anything. We use keys daily: to turn on the car engine, to enter the apartment, to unlock drawers and cabinets. The keys are convenient and easy to manufacture, thanks to modern programmable locks they are not afraid to lose. Many times, humanity has tried to come up with a replacement for keys, but all attempts have failed (we all remember what the idea of using combination locks on access doors led to). Why do not we use such a good and time-tested technology to protect computers?
A modern analogue of the key is a USB flash drive. Regardless of the purpose for which you usually use a USB flash drive, you can always make a full-fledged high-tech key from it, using which entering the system will be as easy as unlocking the door to the apartment.
There are several ways to do this, but the simplest and most universal method is to use the pam_usb PAM module , which will check each USB flash drive inserted into the computer for compliance with the specified requirements and, depending on the result, unlock or block the user account.
No modification of the partition table or information stored on the flash drive is required. To identify the “correct” flash drive, its serial number, model, manufacturer, as well as a set of random data that is written to the backup area of the flash drive and changes with each successful authentication (if someone copies your flash drive, but you will be able to log in before the attacker) , the data will be changed, and its copy will no longer work). In case of loss, there will always be the opportunity to log in using the password and transcode pam_usb to a new USB flash drive. Also, as a key, you can use various memory cards (SD, MMC) and other removable drives.
Getting started with pam_usb is pretty simple. Complete system configuration consists of five steps.
1.We put the libpam_usb.so library and module management utilities:
$ sudo apt-get install libpam-usb pamusb-tools2. We take the USB flash drive that we are going to use as the key, insert it into the USB port and execute the following command:
$ sudo pamusb-conf --add-device имяSo pam_usb will collect all the necessary information about the flash drive, add it to its database and write 2 Kb random data. Udisks will be used to search for a flash drive in the system (the “name” argument is used here to give the flash drive an arbitrary name, and not to indicate its device file), so it is important that other external drives are disabled for the duration of this command.
3. Now let pam_usb understand that this flash drive is associated with the account we need (the path will be vasya):
$ sudo pamusb-conf --add-user vasya4.We start checking the correctness of the collected data in case the flash drive was not correctly identified. Or we forgot to disconnect some other drive, and it was used instead of what we needed:
$ sudo pamusb-check vasya5. Add pam_usb to the list of modules necessary for successful user authentication. On Ubuntu and other Debian-based distributions, this is done by modifying the /etc/pam.d/common-auth file. It is necessary to find a line similar to the following (it may be different):
auth required pam_unix.so. And right in front of her to add the following line: auth sufficient pam_usb.so.So we will tell PAM that before the login of any user you need to give control to the pam_usb module, which will check the presence of the desired flash drive, and only in case of failure of this operation to request a password. Therefore, if you want to let the user in only by flash drive, completely blocking the account in case of failure, the word "sufficient" should be replaced by the word "required".
In principle, all this should be enough for the system to just work (try to log out and log in to check this), however, the functionality of pam_usb can be slightly expanded if you use the pamusb-agent daemon.
The task of pamusb-agent is to automate the work of locking and unlocking a user account when removing and sticking a flash drive into a computer. For the agent to work, you need to add the following lines to the configuration file /etc/pamusb.conf: This is the recipe for Gnome. To use pamusb-agent with other environments, the gnome-screensaver-command --lock and gnome-screensaver-command --deactivate commands must be changed. Now you can run pamusb-agent and check its operability: If everything works fine, you can add it to autorun:
имя_устройства
...
gnome-screensaver-command --lock
gnome-screensaver-command --deactivate
...$ pamusb-agent$ cd ~/.config/autostart
$ ln -s /usr/bin/pamusb-agent pamusb-agentWill we run fingers around?
The pam_usb module is conveniently used as a protection method for laptops equipped with a card reader. You can carry a small SD card in your wallet or internal pocket and stick it into your laptop without worrying about the way it will interfere (as is the case with a USB flash drive). However, this approach will look somewhat archaic if the laptop is already equipped with a fingerprint scanner.
Laptops with a fingerprint scanner are produced by many manufacturers. As a rule, they are not much more expensive than other models with similar characteristics, however, their fingerprint sensor works only in Windows. To fix this, freedesktop.org launched the fprint project., within the framework of which an open implementation of the library for fingerprint recognition and the corresponding PAM-module was developed, which allows you to use the library's capabilities during user login and other account manipulations.
Today, libfprint is in any distribution, so you can install it using any package manager:
$ sudo apt-get install libfprint0 libpam-fprint fprint-demoNext, the scanner can be checked using a special demo program with a graphical interface:
$ fprint_demoIf everything works correctly and without failures, you can start setting up authentication. To do this, run the pam_fprint_enroll program, which will allow you to make a reference fingerprint cast, which will then be used to identify its owner:
# pam_fprint_enroll –enroll-finger 7The number 7 here means the index finger of the right hand. The fprint system numbers fingers from left to right, so that the number 1 will indicate the little finger of the left hand, and 10 - the little finger of the right.
When the cast is ready, add the pam_fprint module to the stack of PAM modules of all applications, for this, open the /etc/pam.d/common-auth file, find the same line “auth required pam_unix.so” and add the line directly in front of it, responsible for loading pam_fprint:
auth sufficient pam_fprint.so. At the next login, everything should work.

Add pam_usb and pam_fprint modules to the PAM stack
Facial memory
Fingers are not the only thing that distinguishes people from each other. We all have different faces, so the system can use the face shot taken by the webcam to identify the user. This is not particularly security, since the attacker can show the camera a regular photo printed on paper, but will make a very strong impression on friends and acquaintances.
Linux distributions do not have built-in face recognition tools, but you can add them by installing a software package called pam-face-authentication , which includes a library that implements a face recognition algorithm, a PAM module for authentication and an application for generating a reference image .
All this can be collected from source or installed from third-party repositories in Ubuntu. Since the project is still raw, and the packages are not prepared for all distributions, we will consider both installation options. So, for installation from source we need packages with a compiler, linker and header files for all the dependencies. In Ubuntu (and in other distributors) you can install them by executing one command:
$ sudo apt-get install build-essential cmake qt4-qmake libx11-dev libcv-dev libcvaux-dev libhighgui4 libhighgui-dev libqt4-dev libpam0g-devNext, download the source from the project page and unpack: To build, use cmake, so everything is simple: To install an already precompiled package in Ubuntu, you can use the antonio.chiurazzi repository: After the installation is complete, run the tutorial:
$ cd
$ wget goo.gl/dpD1s
$ tar -xzf pam-face-authentication-0.3.tar.gz$ cd pam-face-authentication-0.3
$ cmake && make
$ sudo make install$ sudo add-apt-repository ppa:antonio.chiurazzi/ppa
$ sudo apt-get update
$ sudo apt-get install pam-face-authentication$ qt-facetrainerTurn your face in front of the camera, constantly pressing the “Capture” button. It is important to take at least a dozen photos so that the system learns to recognize your face from any angle. It will also be nice to take photos in different lighting conditions. Do not forget to test the system.
Now add the pam_face_authentication.so module to the stack of loaded PAM modules. To do this, open the file /etc/pam.d/gdm or /etc/pam.d/kdm (if you use KDE) and add the following line to its beginning:
auth sufficient pam_face_authentication.so enableX/ The file /etc/pam.d/common-auth should not be changed , since it is used not only by graphical login managers, but also by the standard console / bin / login and / bin / su, and pam_face requires access to X's.
You also need to create a profile for the new PAM module. Open (create) the file / usr / share / pam-configs / face_authentication with the following contents: And activate it:
Name: Manually installed face_authentication profile
Default: yes
Priority: 900
Auth-Type: Primary
Auth:
[success=end default=ignore] pam_face_authentication.so enableX$ sudo pam-auth-update --package face_authenticationPhone key
A cell phone is a symbol of the 21st century. We have long been accustomed to the fact that it can be used not only for calls, but also for Internet access, games, listening to music, watching videos and even paying bills. But can it be used as a key to enter a computer system?
Of course yes. Like a USB flash drive, the phone has many features that make it unique. These are all the same manufacturer and model identifiers, serial number, MAC addresses, IMEI, in the end. Any of them can be used to uniquely identify the device and its owner, but we will focus only on one of them - the MAC address of the Bluetooth interface.
Any, even a very ancient and simple phone has support for the Bluetooth protocol and, as a result, a unique MAC address that transmits to the network in response to any request to search for devices with another Bluetooth adapter. Many modern laptops have such an adapter on board, and its external USB option costs a penny, so for us a blue tooth would be an ideal option for setting password-free and wireless authentication. I went into the room - access was open, went out - the system is locked.
We take the phone, turn on Bluetooth, make it so that it is "visible" to other devices. We sit down at the computer and run the hcitool utility (included in the bluez-utils package) in the device search mode:
$ hcitool scanWe get the name of our device and its MAC address, copy the latter to the clipboard. Install the libpam_blue package (or pam_blue, where as):
$ sudo apt-get install libpam_blueWe create the configuration file /etc/security/bluesscan.conf and write the following into it: Save the file, open the familiar /etc/pam.d/common-auth config and add a line before the line containing "pam_unix.so". Now to enter the system it will be enough to put the phone next to the laptop and enter a name. Next, control will be transferred to the pam_blue module, which will scan the network, find the MAC address of the phone and let the user in. Otherwise, you will have to enter a password.
# Общие настройки
general {
# Продолжительность сканирования в секундах (от 3 до 15)
timeout = 15;
}
# Настройки пользователей и их устройств
mylogin = {
name = Имя устройства;
bluemac = MAC-адрес устройства;
}auth sufficient pam_blue.soconclusions
Setting up passwordless authentication using alternative methods on Linux is pretty simple. To do this, you do not need to be a seasoned geek, be able to write code or have deep knowledge in the field of security, everything is done in a few minutes and works amazingly efficiently. You can say that most of these methods are potentially unsafe and easily bypassed, but before you do this, think about how secure ordinary passwords are.
The safety of a machine that can be accessed by outsiders is pure myth. Getting around standard password protection is easy. There are a huge number of ways to do this, and all of them are known even to children. A password is just a small sign that carries information that the computer has an owner and does not want to see uninvited guests. Applying the methods described in the article, we will not make the system more vulnerable, but we will be able to make our life easier and more convenient.
The analogue of the /etc/pam.d/common-auth file in Gentoo and Mandriva is named /etc/pam.d/system-auth, in FreeBSD it uses /etc/pam.d/system instead. In ArchLinux, you will have to edit PAM-configs separately for each application.
Another way to protect your machine from intrusion is to remotely create the / etc / nologin file using any mobile SSH client. To unlock, you will have to log in as root and delete this file.

Hacker Magazine, September (09) 152
Evgeny Zobnin ( execbit.ru ) .
Subscribe to Hacker
