Fake URL reduction services - Runet innovation
These sites are similar to regular URL shortening services, but there are some oddities in their behavior. In particular, they are almost impossible to find through search engines - the only thing they would be noticed in is spamming. And we have every reason to believe that these sites were created by spammers themselves.
Our analysts identified several such sites at once, and all of them are affiliated with the same spam resources and work on the same principle. All of them use domain names in the .ru zone, and many use hosting in Russia and Ukraine.
The scheme of their work is as follows: shortened links created with the help of fake sites are “shortened” once again on other legitimate URL reduction services. And after that they are sent to spam recipients. The ability to use an ID that looks like a real one to redirect multiple links to the same site eliminates the need to generate real IDs with a low reuse rate. In addition, such a scheme can help go unnoticed by many spam filters.
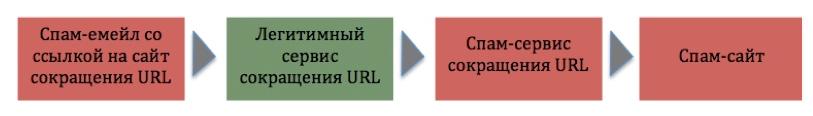
Using the above method, spammers sometimes create long chains in which one abbreviated URL redirects to the second, the second to the third - sometimes this is repeated more than ten times until the link leads to the spammer’s site.
Interestingly, these new domains were registered a few months before the start of use - it is quite possible that this is another way to avoid exposure of legitimate URL reduction services, since the age of the domain can be used as an indicator of legitimacy - it will be much more difficult for an authentic URL reduction service to identify potential violations.
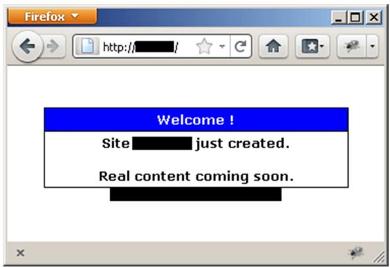
The main page of the site pretends that there is nothing here.
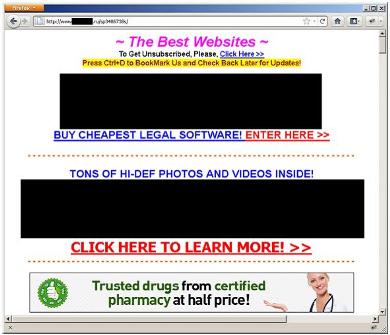
This is how the spam resource looks like to which traffic is being translated.
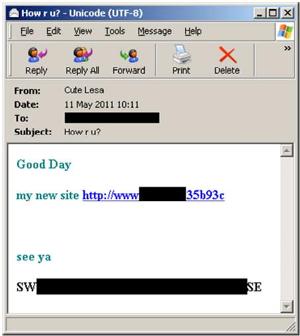
This is how the spam mail looks.
As you can see from the pictures, this is done in this example for an English-speaking user. There
has been a lot of spam in Russia already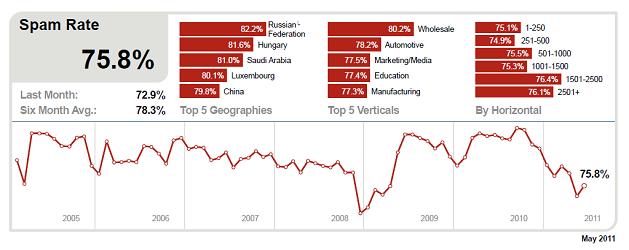
Our analysts identified several such sites at once, and all of them are affiliated with the same spam resources and work on the same principle. All of them use domain names in the .ru zone, and many use hosting in Russia and Ukraine.
The scheme of their work is as follows: shortened links created with the help of fake sites are “shortened” once again on other legitimate URL reduction services. And after that they are sent to spam recipients. The ability to use an ID that looks like a real one to redirect multiple links to the same site eliminates the need to generate real IDs with a low reuse rate. In addition, such a scheme can help go unnoticed by many spam filters.

Using the above method, spammers sometimes create long chains in which one abbreviated URL redirects to the second, the second to the third - sometimes this is repeated more than ten times until the link leads to the spammer’s site.
Interestingly, these new domains were registered a few months before the start of use - it is quite possible that this is another way to avoid exposure of legitimate URL reduction services, since the age of the domain can be used as an indicator of legitimacy - it will be much more difficult for an authentic URL reduction service to identify potential violations.
The main page of the site pretends that there is nothing here.

This is how the spam resource looks like to which traffic is being translated.

This is how the spam mail looks.

As you can see from the pictures, this is done in this example for an English-speaking user. There
has been a lot of spam in Russia already

