Gap in iOS 4 PDF
- Transfer

Now, if you visit a web page and upload a simple PDF file, you can give an attacker full access to your iPhone, iPod touch or iPad. A security vulnerability affects all iOS 4 and iPad devices.
Vulnerability is easy to use. By the way, the last, easiest way to jailbreak , which does not require a computer, uses the same method to crack Apple protection (but already in a non-hazardous mode for the user).
How it works?
It is enough for the user to visit a certain page using Safari. A page can automatically download a simple PDF document that contains a font hiding a special program. When your iOS device tries to display a PDF file, that font causes a stack overflow - a technical condition that allows the secret code inside the font to gain full control over the device.
As a result, without any user intervention, this program can do whatever it wants on your iPhone, iPod touch or iPad. All you can imagine: delete files, transfer files, install background programs to track your actions ... everything can be done.
This is not the first time this has happened. At the beginning of the life of the iPhone, there was a problem with TIFF files, which was a similar security flaw. Apple soon fixed the vulnerability, but before there were very few iPhones compared to today's numbers. Apple claims that more than one hundred million iPhones, iPod touch and iPad have been sold worldwide. Obviously, hackers are trying to gain access to such a large device market.
How can this be avoided?
At the moment, the easiest way to avoid this problem is to not click on any PDF links directly and not download PDF files from untrusted sources. Here, the author could have made a mistake by not saying that other web pages could also harm your iPhone.
You can also jailbreak your iPhone and install a program that will ask for permission every time your browser encounters a PDF (look for “PDF loading warner” in Cydia ).
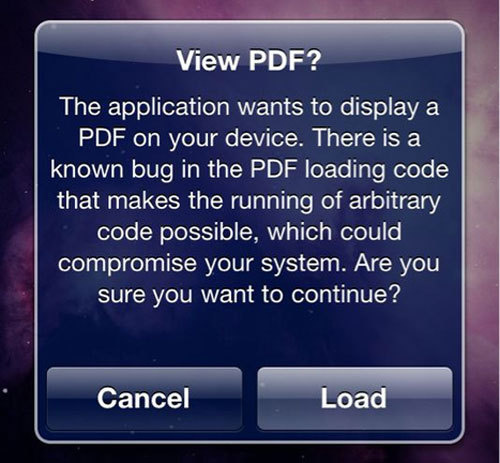
Although this does not solve the security problem, at least the program will warn you about the danger.
Apple has not yet commented on the situation.
