Kismet
Kismet is a multi-functional free utility for working with wireless Wi-Fi networks. It is familiar to users mainly by articles on the topic of hacking, where the program is used to detect hidden networks or capture packets. Hacking other people's networks is bad, but meanwhile Kismet is much more than a master key in the hands of an attacker. In the arsenal of an information security engineer, this program is becoming an excellent tool for monitoring and analyzing 802.11 ether.
The Kismet project takes its start back in 2001. Originally released under the GNU GPL and regularly updated for nearly 10 years, the program has managed to grow its community and enter the top ten network analyzers. Despite the fact that Kismet is a cross-platform development, some functions are available only on Linux, and the developer declares the most complete support in this case, so all of the following is true when running under Linux itself.
Before installing Kismet, you need to make sure that the Wi-Fi card supports RFMON monitoring mode. This mode switches the 802.11 adapter into surveillance mode, in which it captures all packets passing on the air. It all depends on the specific case, some devices support this mode without problems, some can only be helped by a third-party driver, and individual instances do not have such an ability at all.
As always, packages in repositories lag behind current developments, therefore it is more reasonable to download the latest version of source codes and build a program. The procedure is no different from the standard one, no specific requirements for the system are presented, except that since the user interface is based on Curses, appropriate libraries may be required. Looking ahead, it is worth noting that for Kismet there is a separate QT graphical interface.
The developer provides various security configurations. Since some actions (for example, changing the network adapter's operating mode) require root access, you should approach the security settings during installation responsibly. The program is built on a client-server architecture, so distributing rights is not a tricky business, and the documentation details the nuances of this procedure.
If everything was done correctly, the program will be launched by the kismet command.
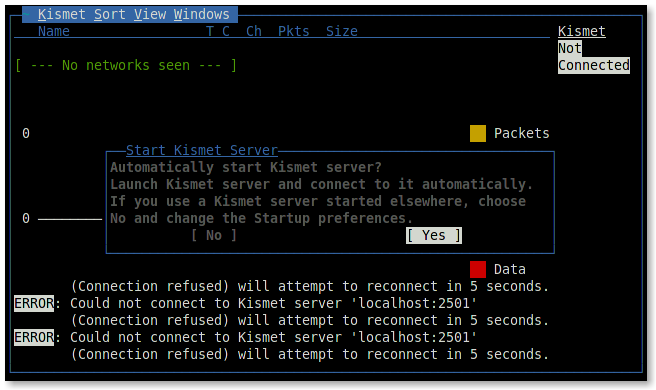
As mentioned earlier, Kismet is built on client-server technology, so when you start the client, you will be prompted to start the server or specify its address. This article assumes that the program is used on the same machine, so you should run the local one.
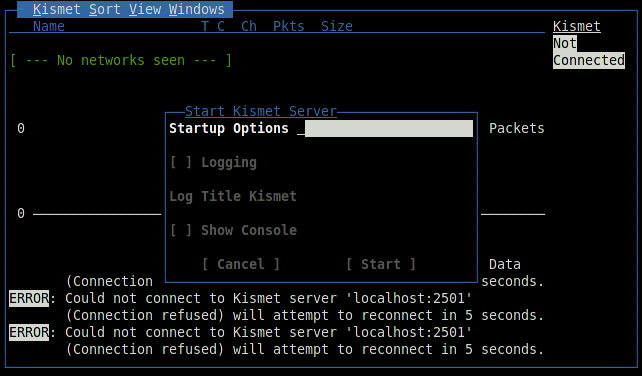
Depending on the task, you can pass start-up parameters to the server, enable or disable logging, and also observe the server console directly in the client interface.
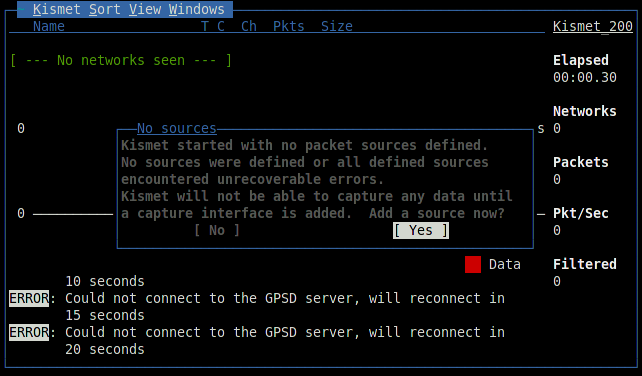
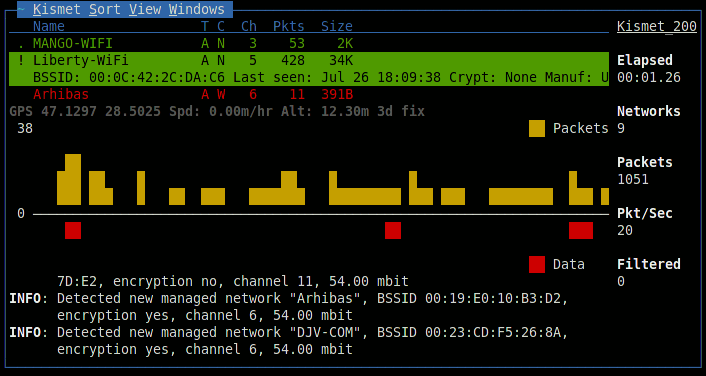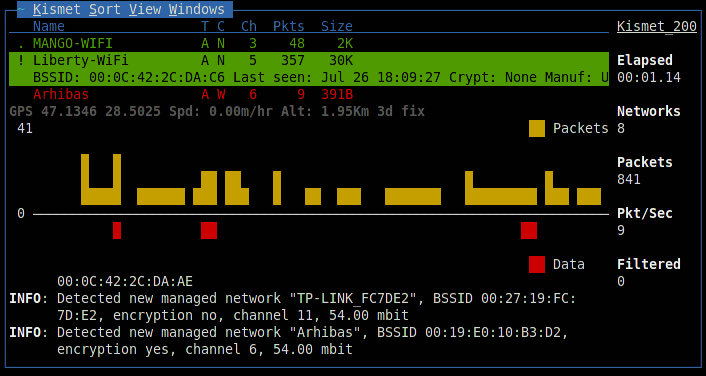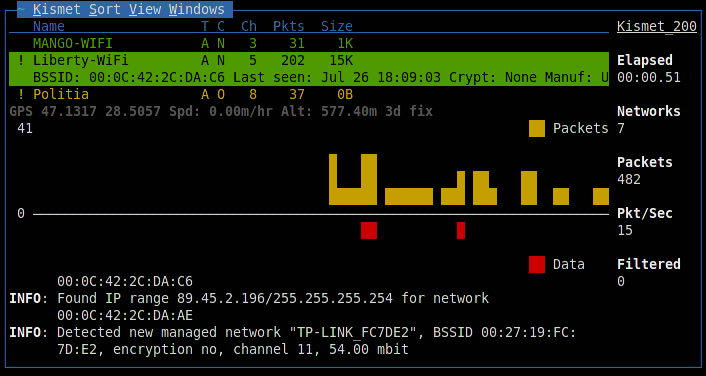
After connecting to the server and starting, scanning will begin. Kismet will display information about found networks. By default, networks with insecure WEP encryption are highlighted in red, networks without encryption are green, and WPA encryption is yellow.
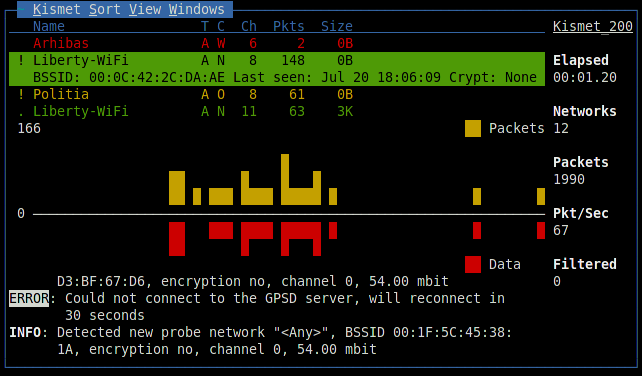
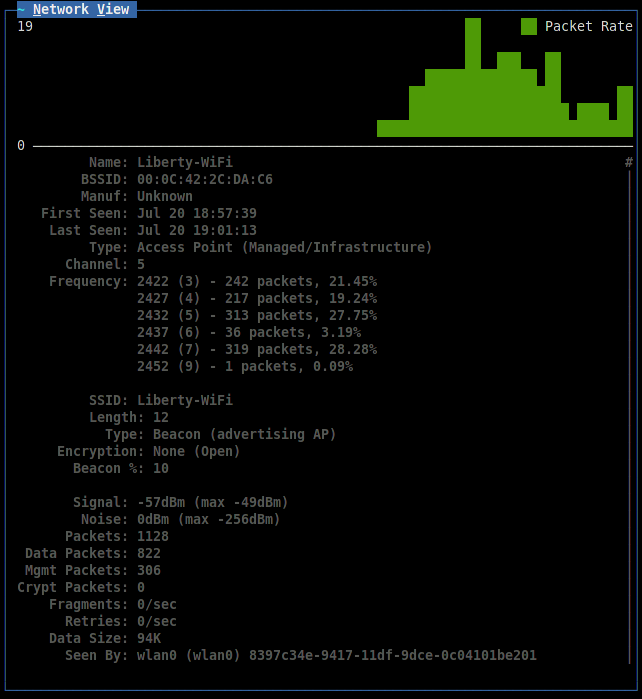
The figures under the list are a visual representation of the packets and data going on the air; similar graphs will also be found in other windows of the program. When a network is selected, additional information will appear in the line: identifier (BSSID), time of detection, encryption method, number of packets and amount of data transmitted after detection. An exclamation mark, a dot or a space in front of the network name indicates three levels of activity, column T - network type (A = Access point), C - encryption type (W = WEP, N = none, etc.). Data fields can be removed, just like adding new ones through the setup menu. On the right, general monitoring statistics are displayed, and the Filtered value shows the number of packets that fall under the created filters. In the lower part, a log is kept, an attentive reader might notice there an error in connecting to the GPSD server.
When you select a network, a window opens that displays more detailed information:
You can add two more graphic indicators: signal strength and number of repeats via the View menu. The command View → Clients displays a list of clients connected to the selected access point:
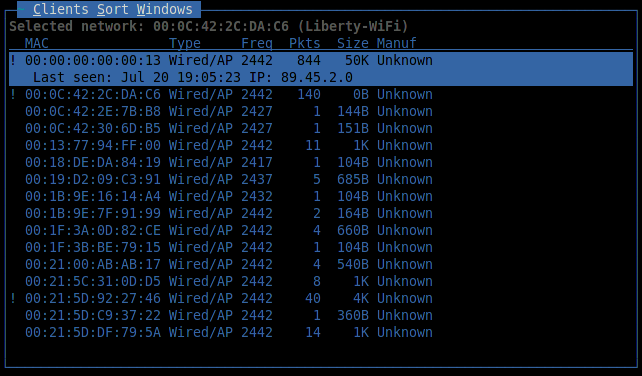
Here, in addition to the basic information, an important parameter is added: the IP address of the client.
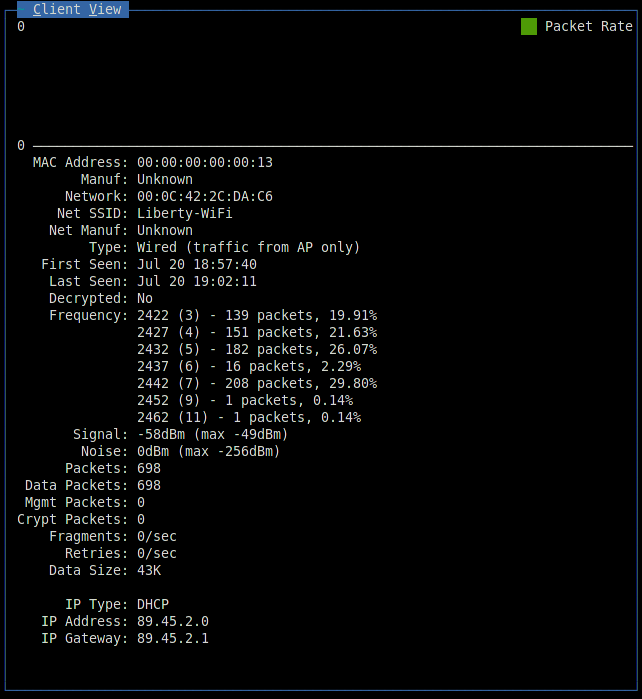
The last Kismet window displays customer information:
Conventionally, the tasks solved using Kismet can be divided into two areas: analytics and protection. In the first case, the accumulated information must be processed by third-party applications, and in the second Kismet works as a detector of various kinds of network attacks. It is better to consider both profiles with specific examples.
More recently, a scandal died out due to Google collecting information about Wi-Fi access points and capturing part of the traffic. Indeed, according to Raphael Leiteritz, Google’s brand manager, Street View cars collected the coordinates of Wi-Fi points and GSM base stations for the development of a navigation service and a whole list of good deeds. Their system worked like this: the Google Street View car used the Maxrad BMMG24005 antenna to receive 802.11 broadcasts and moved along the route, taking all the data in the Wi-Fi range around it. The received data was processed by Kismet, which in connection with the GPS-receiver allows you to build a high-quality interception station.
Create your own Street View car, which will deal with the so-called Wardriving is not as difficult as it seems at first glance. Of the additional equipment, you only need a GPS receiver to bind data to a geographic location.
To start collecting information, the GPS device must be connected and configured to work through the GPSD daemon. It should be noted that Kismet works with the JSON format and therefore it is not possible to use GPS emulators for tests, unless the gpsfake utility included in the GPSD kit can play existing navigation logs. However, setting up GPS is beyond the scope of the Kismet discussion.
This time, the server must be started in logging mode to begin collecting information. By default, 5 types of logs will be available: alarm protocol, geographical XML log, text list of detected networks, network XML log and dump packets in Pcap format . It was because of the latter that Google was harassed by the public, since theoretically this file could contain personal data flying over the air.
If everything is done correctly, now in the main window data on the current geographical position will be displayed. Contrary to popular belief, Kismet does not know the coordinates of a Wi-Fi point, and geographic data is nothing more than the coordinates of a GPS receiver. And although in the presence of a large amount of information it is quite possible to locate a point, the program does not set itself such a task - it is a matter of third-party products.
In the process of moving the logs will grow rapidly, so you should think about free memory.
The data received by the program is saved in a simple understandable format. So, for example, the geographic XML log that interests us consists of many such elements:
All attributes are intuitive and dealing with data is not difficult for any programmer. How to use this data is the decision of the developer. You can build a Wi-Fi map of access points in your area, you can develop a direction finding system. Google announced the collection of this data for pseudo-GPS navigation, when base stations are not used as a guide. By combining data from various logs, you can collect statistics, analyze, draw maps and graphs - everything is limited only by imagination. Anyone can build part of Google Street View in their car and do some useful research.
Kismet also has more serious, albeit less popular functionality. It is no secret that many enterprises use Wi-Fi for internal communications. Information on such networks is often not intended for the general public. Wireless protection is no less important measure than any other aimed at maintaining the level of internal security. Kismet can detect a large list of network attacks at the link and network level. To do this, the program implements a mechanism for alarm alerts, or simply put, alerts.
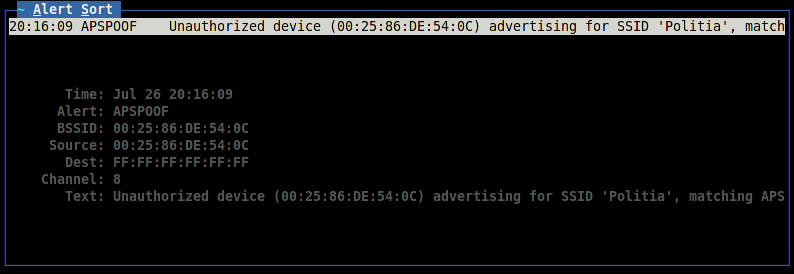
Alarm rules for a specific case are specified in the configuration file. Consider the operation of an intrusion detection system using the example of the APSPOOF rule. This is perhaps one of the simplest methods - it allows you to recognize an attack.in which an attacker acts as a fake access point.
The configuration of this rule looks like this:
Validmacs - valid MAC address values for the access point with the name "Politia", which must be protected. A Karma Tools-triggered attack, Kismet detects it instantly and reports it in the Alerts window and log.
Other alarm rules are configured in exactly the same way. Using Kismet to protect wireless networks is no more difficult than capturing packets, and in conjunction with other measures, the overall level of security becomes much higher.
From the stories of a former employee of the Information and Security Service of the Republic of Moldova. In 2005, a certain company turned to the management with a request for help. For almost a year, the company regularly had money transfers in the wrong direction. The internal security service shrugged: accountants were checked from and to, there was no bank error, but payment orders appeared in some way, in which account numbers were changed. Everything turned out to be more than trivial: some enterprising guys rented an office a floor below, found out the password for the Wi-Fi network and sometimes changed the data in payments, which the accountants meticulously saved in a shared folder, and then printed on the printer in some important office at a time. During the work, the scammers managed to steal a fairly large amount of money.
Whether this is true or not is unknown, but such a story could well have happened, and it is designed to once again remind information security engineers about an important and vulnerable component of a modern corporate network - Wi-Fi wireless data technology.
In fact, this small program can be discussed further. The article does not touch on the topic of plugins that significantly expand its capabilities. Not so long ago, Kismet switched to a new core, so the number of plug-ins is not large, but there is also a decent instance among them - DECT Sniffer, which allows you to use Kismet to work with telephone networks, there is a plug-in for Bluetooth. But this is a topic for a separate publication. And this article, I hope, coped with its task - to introduce Russian-speaking users to another good network development. Perhaps Kismet will help someone in my work as she once helped me.
In preparing the article, Kismet documentation was used , which describes in great detail about working with the program; interesting letters to the Google ; site materialswve.org , which contains all kinds of network attacks on wireless networks; GPSD project website (very good GPS documentation on Linux), personal experience, stories of friends and veteran advocates of the network front.
The latest version of the program is always available at https://www.kismetwireless.net/download.shtml
UPD: Moved to the Information Security blog.
The Kismet project takes its start back in 2001. Originally released under the GNU GPL and regularly updated for nearly 10 years, the program has managed to grow its community and enter the top ten network analyzers. Despite the fact that Kismet is a cross-platform development, some functions are available only on Linux, and the developer declares the most complete support in this case, so all of the following is true when running under Linux itself.
Installation
Before installing Kismet, you need to make sure that the Wi-Fi card supports RFMON monitoring mode. This mode switches the 802.11 adapter into surveillance mode, in which it captures all packets passing on the air. It all depends on the specific case, some devices support this mode without problems, some can only be helped by a third-party driver, and individual instances do not have such an ability at all.
As always, packages in repositories lag behind current developments, therefore it is more reasonable to download the latest version of source codes and build a program. The procedure is no different from the standard one, no specific requirements for the system are presented, except that since the user interface is based on Curses, appropriate libraries may be required. Looking ahead, it is worth noting that for Kismet there is a separate QT graphical interface.
The developer provides various security configurations. Since some actions (for example, changing the network adapter's operating mode) require root access, you should approach the security settings during installation responsibly. The program is built on a client-server architecture, so distributing rights is not a tricky business, and the documentation details the nuances of this procedure.
Preparation for work
If everything was done correctly, the program will be launched by the kismet command.

As mentioned earlier, Kismet is built on client-server technology, so when you start the client, you will be prompted to start the server or specify its address. This article assumes that the program is used on the same machine, so you should run the local one.

Depending on the task, you can pass start-up parameters to the server, enable or disable logging, and also observe the server console directly in the client interface.

Introducing Kismet
After connecting to the server and starting, scanning will begin. Kismet will display information about found networks. By default, networks with insecure WEP encryption are highlighted in red, networks without encryption are green, and WPA encryption is yellow.

The figures under the list are a visual representation of the packets and data going on the air; similar graphs will also be found in other windows of the program. When a network is selected, additional information will appear in the line: identifier (BSSID), time of detection, encryption method, number of packets and amount of data transmitted after detection. An exclamation mark, a dot or a space in front of the network name indicates three levels of activity, column T - network type (A = Access point), C - encryption type (W = WEP, N = none, etc.). Data fields can be removed, just like adding new ones through the setup menu. On the right, general monitoring statistics are displayed, and the Filtered value shows the number of packets that fall under the created filters. In the lower part, a log is kept, an attentive reader might notice there an error in connecting to the GPSD server.
When you select a network, a window opens that displays more detailed information:

You can add two more graphic indicators: signal strength and number of repeats via the View menu. The command View → Clients displays a list of clients connected to the selected access point:

Here, in addition to the basic information, an important parameter is added: the IP address of the client.
The last Kismet window displays customer information:

Using the program in practice
Conventionally, the tasks solved using Kismet can be divided into two areas: analytics and protection. In the first case, the accumulated information must be processed by third-party applications, and in the second Kismet works as a detector of various kinds of network attacks. It is better to consider both profiles with specific examples.
Geographic statistics collection
More recently, a scandal died out due to Google collecting information about Wi-Fi access points and capturing part of the traffic. Indeed, according to Raphael Leiteritz, Google’s brand manager, Street View cars collected the coordinates of Wi-Fi points and GSM base stations for the development of a navigation service and a whole list of good deeds. Their system worked like this: the Google Street View car used the Maxrad BMMG24005 antenna to receive 802.11 broadcasts and moved along the route, taking all the data in the Wi-Fi range around it. The received data was processed by Kismet, which in connection with the GPS-receiver allows you to build a high-quality interception station.
Create your own Street View car, which will deal with the so-called Wardriving is not as difficult as it seems at first glance. Of the additional equipment, you only need a GPS receiver to bind data to a geographic location.
To start collecting information, the GPS device must be connected and configured to work through the GPSD daemon. It should be noted that Kismet works with the JSON format and therefore it is not possible to use GPS emulators for tests, unless the gpsfake utility included in the GPSD kit can play existing navigation logs. However, setting up GPS is beyond the scope of the Kismet discussion.
This time, the server must be started in logging mode to begin collecting information. By default, 5 types of logs will be available: alarm protocol, geographical XML log, text list of detected networks, network XML log and dump packets in Pcap format . It was because of the latter that Google was harassed by the public, since theoretically this file could contain personal data flying over the air.
If everything is done correctly, now in the main window data on the current geographical position will be displayed. Contrary to popular belief, Kismet does not know the coordinates of a Wi-Fi point, and geographic data is nothing more than the coordinates of a GPS receiver. And although in the presence of a large amount of information it is quite possible to locate a point, the program does not set itself such a task - it is a matter of third-party products.

In the process of moving the logs will grow rapidly, so you should think about free memory.
The data received by the program is saved in a simple understandable format. So, for example, the geographic XML log that interests us consists of many such elements:
All attributes are intuitive and dealing with data is not difficult for any programmer. How to use this data is the decision of the developer. You can build a Wi-Fi map of access points in your area, you can develop a direction finding system. Google announced the collection of this data for pseudo-GPS navigation, when base stations are not used as a guide. By combining data from various logs, you can collect statistics, analyze, draw maps and graphs - everything is limited only by imagination. Anyone can build part of Google Street View in their car and do some useful research.
Intrusion detection
Kismet also has more serious, albeit less popular functionality. It is no secret that many enterprises use Wi-Fi for internal communications. Information on such networks is often not intended for the general public. Wireless protection is no less important measure than any other aimed at maintaining the level of internal security. Kismet can detect a large list of network attacks at the link and network level. To do this, the program implements a mechanism for alarm alerts, or simply put, alerts.
Alarm rules for a specific case are specified in the configuration file. Consider the operation of an intrusion detection system using the example of the APSPOOF rule. This is perhaps one of the simplest methods - it allows you to recognize an attack.in which an attacker acts as a fake access point.
The configuration of this rule looks like this:
apsproof=Rule1:ssid="Politia", validmacs="70:3A:02:01:CE:AF"Validmacs - valid MAC address values for the access point with the name "Politia", which must be protected. A Karma Tools-triggered attack, Kismet detects it instantly and reports it in the Alerts window and log.

Other alarm rules are configured in exactly the same way. Using Kismet to protect wireless networks is no more difficult than capturing packets, and in conjunction with other measures, the overall level of security becomes much higher.
From the stories of a former employee of the Information and Security Service of the Republic of Moldova. In 2005, a certain company turned to the management with a request for help. For almost a year, the company regularly had money transfers in the wrong direction. The internal security service shrugged: accountants were checked from and to, there was no bank error, but payment orders appeared in some way, in which account numbers were changed. Everything turned out to be more than trivial: some enterprising guys rented an office a floor below, found out the password for the Wi-Fi network and sometimes changed the data in payments, which the accountants meticulously saved in a shared folder, and then printed on the printer in some important office at a time. During the work, the scammers managed to steal a fairly large amount of money.
Whether this is true or not is unknown, but such a story could well have happened, and it is designed to once again remind information security engineers about an important and vulnerable component of a modern corporate network - Wi-Fi wireless data technology.
Conclusion
In fact, this small program can be discussed further. The article does not touch on the topic of plugins that significantly expand its capabilities. Not so long ago, Kismet switched to a new core, so the number of plug-ins is not large, but there is also a decent instance among them - DECT Sniffer, which allows you to use Kismet to work with telephone networks, there is a plug-in for Bluetooth. But this is a topic for a separate publication. And this article, I hope, coped with its task - to introduce Russian-speaking users to another good network development. Perhaps Kismet will help someone in my work as she once helped me.
In preparing the article, Kismet documentation was used , which describes in great detail about working with the program; interesting letters to the Google ; site materialswve.org , which contains all kinds of network attacks on wireless networks; GPSD project website (very good GPS documentation on Linux), personal experience, stories of friends and veteran advocates of the network front.
The latest version of the program is always available at https://www.kismetwireless.net/download.shtml
UPD: Moved to the Information Security blog.
