A short story about the study of one botnet
For several years now, a trigger has been hanging on our website that works for a certain combination of words in requests, in particular, such as: union, eval, passthru, alert, javascript, cookie, etc. In case of operation, soap is sent. This allows you to see most attempts to do SQL injection, use PHP include or XSS. Hacking attempts are carried out quite often, but in the last month of reports, about a hundred began to arrive. All of the same type. We are looking for a vulnerability in some standard module of contacts, in which, as I understand it, there is a pseudo-tag [php] with all the consequences. The exploit, using this pseudo-tag, is trying to load the Perl script on the victim's server and transfer control to it. HereYou can find a list of links to bots (these are text files with Perl code), although some files are already lost. Exploits are different and try to load different bots, possibly from different groups, some of these bots are triggered by antivirus and silently delete. It is safer to download the code with the help of rockers, and not through the browser. Accordingly, if the code runs on the victim’s server (basically it is a regular web server on a cheap hosting with a million sites), then the bot immediately connects to the IRC channel, where it is already waiting. Having downloaded one of the bots at random, I decided to see how everything is arranged there.
A quick look at the file shows that in the settings of this bot, the administrator with the right to work with bots is the person with the Conficker login. The bot immediately connects to the IRC server: irc.planetwork.tk:6667, on the channel #autorun. The bots have several logins to choose from ( it seems all women) I decided not to think too long and logged in as admin. But then a little-known service for storing photos played a bad service with me, and instead of the correct nickname, I logged in as Conflicker. But I did not notice this right away and at first I tried to steer some of the bots with the expected result. On the main channel, there were about 120 bots, some of them crawled sites for vulnerabilities and periodically wrote the results to the general chat. From time to time, they found various vulnerabilities, in particular SQL Injection, with which, apparently, people will already deal with manually. Search for victims is standard, through search engines. I tried via chat to give commands to the bots, but only the PING test worked, since this did not require any login. And here I was very surprised by the channel administrator.
Stepping aside a little, I want to talk about how I “explored” one of the botnets a couple of years ago. The story is quite short, I went to the channel in the same way, the channel administrator opened the chat and first did ls –al. Accordingly, repeating the operation on one of our servers in a nonsignificant directory, I threw back the list of files (the real bot should have done the same, but somewhat quicker). Thus, acting as a proxy, I downloaded the rest of the botnet files (the basis was, unfortunately, compiled httpd). Realizing that I couldn’t squeeze out more, in one of the requests I just said “hi”, asked how are you, got the answer that it was all some kind of mistake, my interlocutor was generally by chance here, was kicked from the channel and banned.
I expected something similar here, in case they consider me human. But the administrator, seeing the Conflicker login, said “wow” and gave me an oops. Since I’m not particularly fond of IRC, I just thought that it’s a good moment to just kick the administrator from the channel and change login, take his place, but so far decided to do nothing. It took some time to research the possibility of changing the nickname so that the bots would perceive me as an admin. And then a miracle happened - Conficker wrote that he needed to reboot and fell off. Having changed my login to Conficker, I got full access.
There are two types of bots:
- "newbie", he submits to the administrator without question and, I think, serves mainly to load bots of the second type. A command written in the chat of such a bot will be executed on the server as if it were typed in the terminal, the result will also be displayed in the terminal;
- “working,” then the administrator needs to enter a password for more or less important operations. However, the help command works for everyone.
The body of the "worker" was able to download. The main functions are to check for vulnerabilities in other sites, DDoS, download exploits from the service, etc. There were already two logins in this version of the bot: Conficker and ikhy (the second login didn’t work for everyone, though). Password dor. After the “auth dor” command in the chat with a specific bot (it’s better not to do this in the general channel), an extended help appears and access to all the commands.
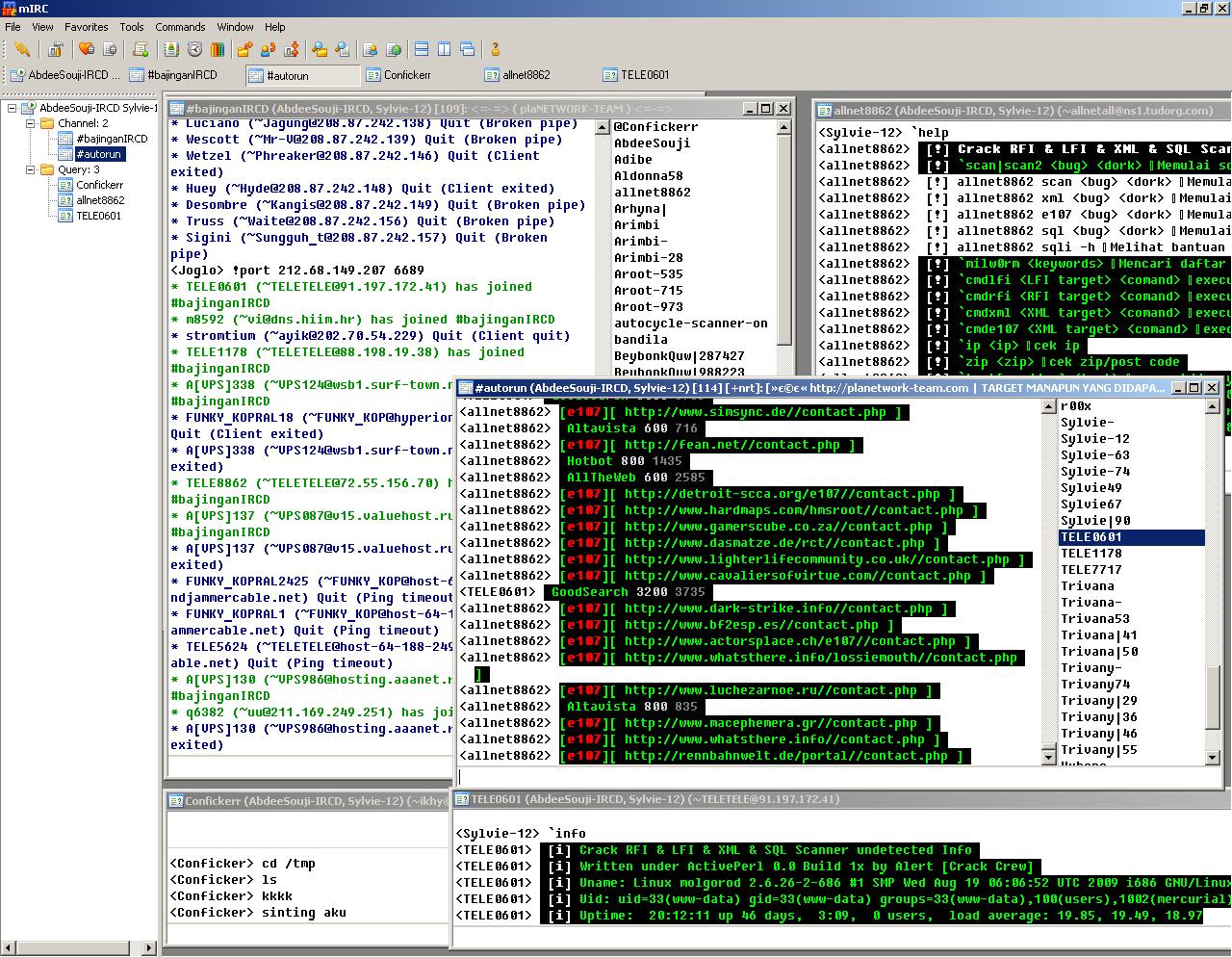
If you select a login from the “newbie” bot predefined, add a random number to the end and then go to the IRC server, then the channel #bajinganIRCD opens automatically. How it all looks (I logged in as “Sylvie-12“) can be seen in the screenshot. The body of the “worker” lies in /temp/.logs. The "worker" is started with the rights of "apache".
Hijacking such a botnet is not difficult. Firstly, all “workers” have the same password. It is enough to get the body of one of them (you can sit and handle emulating a “newbie” or use honeypot), rewrite it by putting a trigger on the administrator’s exit from the channel, at the time of exit change your nickname and overtake the rest of the herd on a new server. Secondly, in this particular case, it’s enough to just wait, as the administrator is constantly falling off. Another thing is why this is needed.
Actually on this my curiosity ran out. If someone is interested in picking up a botnet, then at the moment it works and passwords, I think no one has changed.
Bot
A quick look at the file shows that in the settings of this bot, the administrator with the right to work with bots is the person with the Conficker login. The bot immediately connects to the IRC server: irc.planetwork.tk:6667, on the channel #autorun. The bots have several logins to choose from ( it seems all women) I decided not to think too long and logged in as admin. But then a little-known service for storing photos played a bad service with me, and instead of the correct nickname, I logged in as Conflicker. But I did not notice this right away and at first I tried to steer some of the bots with the expected result. On the main channel, there were about 120 bots, some of them crawled sites for vulnerabilities and periodically wrote the results to the general chat. From time to time, they found various vulnerabilities, in particular SQL Injection, with which, apparently, people will already deal with manually. Search for victims is standard, through search engines. I tried via chat to give commands to the bots, but only the PING test worked, since this did not require any login. And here I was very surprised by the channel administrator.
A few years ago
Stepping aside a little, I want to talk about how I “explored” one of the botnets a couple of years ago. The story is quite short, I went to the channel in the same way, the channel administrator opened the chat and first did ls –al. Accordingly, repeating the operation on one of our servers in a nonsignificant directory, I threw back the list of files (the real bot should have done the same, but somewhat quicker). Thus, acting as a proxy, I downloaded the rest of the botnet files (the basis was, unfortunately, compiled httpd). Realizing that I couldn’t squeeze out more, in one of the requests I just said “hi”, asked how are you, got the answer that it was all some kind of mistake, my interlocutor was generally by chance here, was kicked from the channel and banned.
Bot. Continuation
I expected something similar here, in case they consider me human. But the administrator, seeing the Conflicker login, said “wow” and gave me an oops. Since I’m not particularly fond of IRC, I just thought that it’s a good moment to just kick the administrator from the channel and change login, take his place, but so far decided to do nothing. It took some time to research the possibility of changing the nickname so that the bots would perceive me as an admin. And then a miracle happened - Conficker wrote that he needed to reboot and fell off. Having changed my login to Conficker, I got full access.
What were able to find out and some thoughts
There are two types of bots:
- "newbie", he submits to the administrator without question and, I think, serves mainly to load bots of the second type. A command written in the chat of such a bot will be executed on the server as if it were typed in the terminal, the result will also be displayed in the terminal;
- “working,” then the administrator needs to enter a password for more or less important operations. However, the help command works for everyone.
The body of the "worker" was able to download. The main functions are to check for vulnerabilities in other sites, DDoS, download exploits from the service, etc. There were already two logins in this version of the bot: Conficker and ikhy (the second login didn’t work for everyone, though). Password dor. After the “auth dor” command in the chat with a specific bot (it’s better not to do this in the general channel), an extended help appears and access to all the commands.
If you select a login from the “newbie” bot predefined, add a random number to the end and then go to the IRC server, then the channel #bajinganIRCD opens automatically. How it all looks (I logged in as “Sylvie-12“) can be seen in the screenshot. The body of the “worker” lies in /temp/.logs. The "worker" is started with the rights of "apache".

Hijacking such a botnet is not difficult. Firstly, all “workers” have the same password. It is enough to get the body of one of them (you can sit and handle emulating a “newbie” or use honeypot), rewrite it by putting a trigger on the administrator’s exit from the channel, at the time of exit change your nickname and overtake the rest of the herd on a new server. Secondly, in this particular case, it’s enough to just wait, as the administrator is constantly falling off. Another thing is why this is needed.
Actually on this my curiosity ran out. If someone is interested in picking up a botnet, then at the moment it works and passwords, I think no one has changed.
