Mini fraud to the maximum

The mixed reaction of the habro-community to my last article on WebMoney Keeper Mini Extension, published on Habré, prompted me to write the following ...
It turns out that many WebMoney users, having wallets in Classic or Light keepers, are simply afraid to connect WM Keeper Mini to themselves, which plays into the hands of fraudsters, not the users themselves. Why? This was under the cut ...
Anyone WM, having Keeper Classic or Light, is on the security of the system online in ways to manage your WMID to establish power of attorney to manage their existing purses from Classic or Light to WMID 128008643216 (mini.webmoney.ru). Simply put, plug in your Mini keeper ...
Now the problem itself is that most WM users either don’t know about it or do not knowingly do it! Well, those who do not know can still be understood, but others are difficult to understand! According to their personal conviction, they believe that they thereby ensure maximum security in the system (I understood this from the comments on the article and the pluses on them) that they do not need extra movements. So, ladies and gentlemen, I must disappoint you - this is not so! Now they are taking us away through Mini webmoney, and as much and as simple as possible!
Of course, I’ll give an explanation ...
I will not describe the entire process here in detail, I think no one will argue that they often steal a key file or WMID certificate on the network to access your money using trojans - this is a fact. And to protect yourself from this 100% is simply impossible - experienced programmers manage to catch Vinlokov (you can read it on Habré), and what to speak for others? But getting access is one thing, and withdrawing money from your wallet is completely different. How, for example, to withdraw your money if you have confirmation of transactions through Enum?
And here Mini Keeper comes to the aid of scammers, who they already with great dexterity and, I think, even with great love, connect to your WMID themselves, set an input password and use it for their own purposes, and do it instead of you ...
This is done simply - with the help of a key file or certificate, the fraudster authorizes on the security.webmoney.ru website, installs a power of attorney there for the required wallet for Mini, then through Mini, with a username and password, displays your money ...
I knowingly allocated what the scammers are doing instead of you, because you could easily preempt them and do it yourself , but for some reason some do not express such a desire.
But in Mini there is nothing complicated, you just need to configure everything yourself, because by default there are not quite the right settings, to put it mildly, that is, login via login and password. So why don’t we go there ourselves, ahead of scammers, and then install and configure everything through Enum? What is stopping us? Our laziness or misunderstanding of what is happening ?! After all, there has long been a choice:
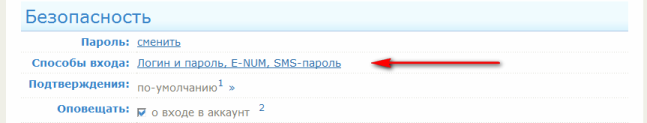
I understand that the “hole” is small, you need a key file or certificate in advance, but it is there and scammers use it, for example, using phishing, as I described in this article: Phishing emails from WebMoney
It's nice that the article made many WM users think too, after the recent actual mailing of the WebMoney themselves about the necessary replacement of the old root certificate, which expired, they began to write posts "Caution scammers!", Even on the official WebMoney forum.
By the way, also to say that after the publication of that article on the main Habr, the fraudster instantly made himself felt, see, carefully the Habr reads, and maybe hangs out here (my karma decently fell then). I hope that this article also gets to the main, therefore - hello, fellow countryman, someday you will be pierced and ruin your young years!
Fraudsters are already using new domains for phishing, but they have not changed the scheme of fraud, so why don’t we deprive them of the opportunity to withdraw our “money” by setting up authorization through Enum in our keeper, on WebMoney and Mini sites? They can’t get around Enum, and it’s unrealistic for them to do it!
Ahead of events, I’ll say right away that in the comments on the article Your WebMoney under E-NUM protection, the Gibarian user quite clearly described the situation with the theft of WM while protecting Enum by a well-known blogger (link at the beginning of the article), making a mistake in one moment, which does not change the essence, therefore , please, do not give this example here, it already affects me, like many BolgenOS. If there are other examples, we can consider them here, but I don’t know such yet ...
PS I hope I’m not very tired of everyone with my articles on WM security, but, as they say, warned, so armed!
