MiTM for GPRS
Everyone has their secrets ... someone has a secret correspondence with a loved one, someone has multimillion-dollar banking operations, someone has Privat'y pictures on their mobile :)
Yes, it doesn’t really matter what secrets the main thing is that they almost everyone has it. With today's frantic pace of life, more and more have to use data transfer on the road, often through mobile devices. It’s good if a relatively “safe” BlackBerry is used as a mobile terminal, but what if it is a “regular” phone with access via GPRS / EDGE.
Have you ever wondered how safe is the data transfer via GPRS / EDGE technologies through the operator’s mobile network?
We will not say that the operator can disable interface encryption for the duration of the tests, or the operator can use the weaker encryption protocol [GEA - GPRS Encryption Algorithm], which will allow the use of flaws in the encryption of the radio interface and intercept and analyze data transmission. In this article, we will talk about one at first glance unlikely, but in a completely realistic threat - an insider invasion.
So what do we have ...
A simplified connection diagram for the GPRS / EDGE packet architecture is presented in the diagram below:
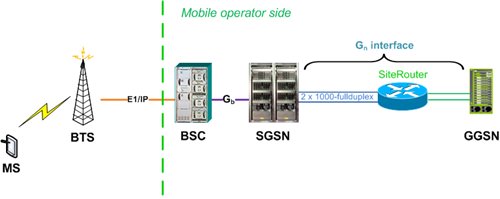
Suppose, purely hypothetically, that the operator has an “insider” who is very interested in collecting confidential information from users of mobile data transmission.
We also admit. that our insider has access to the Gn interface. The Gn interface is a direct link from SGSN to the GGSN , the bandwidth is selected based on the current load, usually these are two (to provide duplication) 1000-fullduplex Ethernet links.
For more specificity, we set additional initial conditions:
Let’s now consider a non-trivial situation in order to understand what an insider can do in the operator’s network, having access to one or more network elements and taking into account the initial conditions set by us.
The insider connection diagram for the operator’s network is presented in the diagram below (the diagram shows several insider laptop connection diagrams, but only one connection will be sufficient to collect confidential information):

Let's say that our insider will use the console utility from Wireshak'a - tshark.
An approximate filter, “concocted” in a hurry to intercept subscriber packages intended for one of the popular social networks, will look like this:
Describe the parameters of the tshark.exe utility, I think it makes no sense who can be found here . We’ll clean the file a little:
If the insider has access to one of the SGSN or GGSN network elements, then after completing all the above steps, he can carry out a kind of MITMattack, duplicating part of the stream to another port, connecting the laptop to this port. Thus, having carried out such an attack, our insider will collect logins / passwords from a popular social network, thereby obtaining confidential information of subscribers of a mobile operator.
Naturally, many can say that I did not say anything new in this article, because any system administrator in a large company can also easily compromise any user by putting them “in pencil,” but I just wanted to say that you should not forget about precautions when transferring important information to you, even if you use packet data transfer using technologies GPRS / EDGE ...
PS: the whole article is based only on my fantasies and has nothing to do with reality, but is intended only to become familiar with the possible methods of removing traces from the Gn interface. I do not urge to commit unlawful actions aimed at the collection and disclosure of confidential information relating to both the mobile operator and information relating to the personal data of subscribers.
Small helper:
BSC - Base Station Controller
BTS - Base Transceiver Station
EDGE - Enhanced Data rates for GSM Evolution
GGSN - Gateway GPRS Support Node
GPRS - General Packet Radio Service
IMEI - International Mobile Equipment Identity
IMSI - International Mobile Subscriber Identity
ISDN - Integrated Services Digital Network
L2TP - Layer 2 Tunneling Protocol
MS - Mobile Station
MSISDN - Mobile Station ISDN Number
PPTP - Point-to-Point Tunneling Protocol
PS - Packet Switched
P-TMSI- Packet TMSI
SGSN - Serving GPRS Support Node
TMSI - Temporary Mobile Subscriber Identity
VPN - Virtual private network

Yes, it doesn’t really matter what secrets the main thing is that they almost everyone has it. With today's frantic pace of life, more and more have to use data transfer on the road, often through mobile devices. It’s good if a relatively “safe” BlackBerry is used as a mobile terminal, but what if it is a “regular” phone with access via GPRS / EDGE.
Intro
Have you ever wondered how safe is the data transfer via GPRS / EDGE technologies through the operator’s mobile network?
We will not say that the operator can disable interface encryption for the duration of the tests, or the operator can use the weaker encryption protocol [GEA - GPRS Encryption Algorithm], which will allow the use of flaws in the encryption of the radio interface and intercept and analyze data transmission. In this article, we will talk about one at first glance unlikely, but in a completely realistic threat - an insider invasion.
So what do we have ...
Scheme
A simplified connection diagram for the GPRS / EDGE packet architecture is presented in the diagram below:

Suppose, purely hypothetically, that the operator has an “insider” who is very interested in collecting confidential information from users of mobile data transmission.
We also admit. that our insider has access to the Gn interface. The Gn interface is a direct link from SGSN to the GGSN , the bandwidth is selected based on the current load, usually these are two (to provide duplication) 1000-fullduplex Ethernet links.
For more specificity, we set additional initial conditions:
- The operator uses encryption of the radio interface from the subscriber to SGSN, the GEA-1,2,3 algorithms.
In principle, in this situation, it does not matter if the encryption algorithm up to SGSN is applied, because our insider will try to "catch" information on the Gn interface, which in most cases is not encrypted.
- The subscriber transfers data without encrypting the stream, i.e. connects NOT via VPN [L2TP, PPTP, IPSec].
This moment is quite important to our insider, because if the subscriber encrypts the data stream by software, then the insider will “see” the encrypted stream on the Gn interface. This measure, of course, does not give a 100% guarantee of the security of data transfer, but the methods that our insider will use will be much more complicated and ultimately will be based on the value of the possible information. Consideration of these methods is beyond the scope of this article.
- An insider has direct access to SGSN or GGSN.
One of the conditions necessary for our insider is access to one of the network elements inside the PS Core Network (packet network) - SGSN or GGSN. What will this provide to the insider? The simplest thing that comes to mind is to set up duplication of the data stream via the Gn interface [port SPANing] on the Ethernet interface, which can be connected using a laptop, as SGSN’s “overseas” operator’s “abroad” abroad. A more sophisticated method is to configure filters on the network element itself for a specific subscriber. Subscriber identification can be performed by IMSI , TMSI , P-TMSI, IMEI , MSISDN , or by IP / X.25 addresses assigned to the subscriber in the operator’s mobile network.
Let’s now consider a non-trivial situation in order to understand what an insider can do in the operator’s network, having access to one or more network elements and taking into account the initial conditions set by us.
Collection of confidential information from the online stream
The insider connection diagram for the operator’s network is presented in the diagram below (the diagram shows several insider laptop connection diagrams, but only one connection will be sufficient to collect confidential information):

Let's say that our insider will use the console utility from Wireshak'a - tshark.
An approximate filter, “concocted” in a hurry to intercept subscriber packages intended for one of the popular social networks, will look like this:
tshark.exe -i 6 -B 16 -n -R "(http.host == "login.vk.com") && (http.request.method == "POST")" -V -l -T text -w d:\dump -a filesize:16000 -b filesize:16000 -b files:2 -S >> d:\vpass_db.txtDescribe the parameters of the tshark.exe utility, I think it makes no sense who can be found here . We’ll clean the file a little:
type vps.txt | findstr /I /L "email %40 pass" | findstr /V "Referer" | sort >> passdb.txtIf the insider has access to one of the SGSN or GGSN network elements, then after completing all the above steps, he can carry out a kind of MITMattack, duplicating part of the stream to another port, connecting the laptop to this port. Thus, having carried out such an attack, our insider will collect logins / passwords from a popular social network, thereby obtaining confidential information of subscribers of a mobile operator.
Outro
Naturally, many can say that I did not say anything new in this article, because any system administrator in a large company can also easily compromise any user by putting them “in pencil,” but I just wanted to say that you should not forget about precautions when transferring important information to you, even if you use packet data transfer using technologies GPRS / EDGE ...
PS: the whole article is based only on my fantasies and has nothing to do with reality, but is intended only to become familiar with the possible methods of removing traces from the Gn interface. I do not urge to commit unlawful actions aimed at the collection and disclosure of confidential information relating to both the mobile operator and information relating to the personal data of subscribers.
Small helper:
BSC - Base Station Controller
BTS - Base Transceiver Station
EDGE - Enhanced Data rates for GSM Evolution
GGSN - Gateway GPRS Support Node
GPRS - General Packet Radio Service
IMEI - International Mobile Equipment Identity
IMSI - International Mobile Subscriber Identity
ISDN - Integrated Services Digital Network
L2TP - Layer 2 Tunneling Protocol
MS - Mobile Station
MSISDN - Mobile Station ISDN Number
PPTP - Point-to-Point Tunneling Protocol
PS - Packet Switched
P-TMSI- Packet TMSI
SGSN - Serving GPRS Support Node
TMSI - Temporary Mobile Subscriber Identity
VPN - Virtual private network

