Notes on Apple's internal software that no one has seen
It so happened that yesterday, rummaging through the BSD wilds of the Darwin kernel and in VFS, I again came across a link like rdar ...
For those who don’t know: Apple has a public bug tracker (http://bugreport.apple.com, alternate login named radar.apple.com). But he is only public in sending and contemplating his own posts (and their permission statuses), which often turn out to be duplicates.
Read directly descriptions of all problems and their solutions can only Apple developers themselves or very cool external organizations.
As a rule, no one on the Internet heard how to access the radar error database for arbitrary reading, and in general few know what this system is.
Moreover, Apple is not profitable to give access to this database for at least the following reasons:
This note will not give you access to the radar database, but it will indicate in which direction you can go and what tools Apple has at the moment - magic tools that the company does not share even with paid members of ADC (Apple Developer Connection).
There is an alternative to the radar service: openradar.appspot.com (though it has nothing to do with Apple).
And it is unlikely that you will find the necessary problem descriptions from Apple Radar in it.
Our company is a member of ADC, including a paid subscription, but this story does not violate any NDAs, because it is based on information available (at the moment - early June 2010) without logins and passwords, to a simple Internet user.
Ironically, at the moment, Apple FTP access is open to an anonymous user!
Pay attention to the hidden folder '.shared'.
In the folder '.shared' there is also a hidden folder '.zzz_old_archives'.
They turned out to be a lot of tasty:
Programs were installed, tested, and some documentation shed some light.
So:
AppleConnect is special software for organizing VPN connections to Apple’s internal network, in particular, for gaining access to Apple’s internal resources. As I understand it, for authentication in AppleConnect previously used special keys (they are still in use) - eTokens, probably connected via USB. Now, in many cases, Apple ID authentication is acceptable (of course, every Apple ID has permissions for certain actions).
AppleConnect can live in the status menu next to the clock, and it’s easy to switch VPN and Apple ID settings for different inputs.
Of great interest to radar is the ray.apple.com server, whose ports are apparently only accessible from the VPN.
The tracker seems to be spinning on Oracle Application Server, Java, WebObjects, and, at least in the documentation, on IBM AIX servers.
I don’t have much faith in the latter, for the current day, given that Apple has its own good Xserve hardware. Or maybe they just don’t want to touch this ancient system.
In the process of reading the documentation, a certain IT&S company was also highlighted.
It is they who are invited to contact (by phone) for support via radar and on issues of connecting / receiving login.
Perhaps these are the guys from MIT that Apple is feeding.
Also, it is highly likely that this is their site: ist.mit.edu
Radar - a huge system (a la Xcode), with a logo (icon) in the form of a blue anteater catching an ant.
Designed for administrators, moderators and developers, as well as for readers from external organizations (oh, dreams).
Radar can work without a GUI from the command line.
Sonar - as I understood it at 4 nights, this is some rethinking of Radar, which contains mostly ready-made solutions to problems and allows you to add / edit solutions.
NFA - a virtual safe that protects various resources from prying eyes (useful when working with graphics, projects, documents).
In general, a very funny software - download, install, watch, read.
I still could not get access to the database - my logins in ADC do not have rights to connect to Apple VPN.
But the proximity of the sacred and the signature in the Apple Internal Use Only documents gave a hefty dose of adrenaline!
A few screenshots




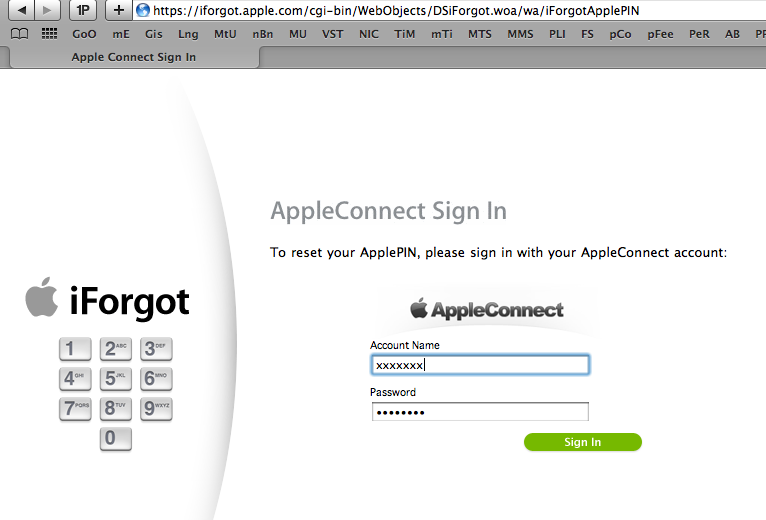
for starters : (for connecting external AppleConnect settings)
Download, try, write about your results in the comments.
Hurry up, after this article anonymous access is likely to be quickly hidden.
Now that a simple developer has learned more, maybe we can change something in this unfair world for us ...
For those who don’t know: Apple has a public bug tracker (http://bugreport.apple.com, alternate login named radar.apple.com). But he is only public in sending and contemplating his own posts (and their permission statuses), which often turn out to be duplicates.
Read directly descriptions of all problems and their solutions can only Apple developers themselves or very cool external organizations.
As a rule, no one on the Internet heard how to access the radar error database for arbitrary reading, and in general few know what this system is.
Moreover, Apple is not profitable to give access to this database for at least the following reasons:
- Some information can damage the reputation of the system and provide food for hackers when writing an exploit, until the vulnerability is fixed
- Bypassing bug fixes Apple sells to developers for money
This note will not give you access to the radar database, but it will indicate in which direction you can go and what tools Apple has at the moment - magic tools that the company does not share even with paid members of ADC (Apple Developer Connection).
There is an alternative to the radar service: openradar.appspot.com (though it has nothing to do with Apple).
And it is unlikely that you will find the necessary problem descriptions from Apple Radar in it.
Our company is a member of ADC, including a paid subscription, but this story does not violate any NDAs, because it is based on information available (at the moment - early June 2010) without logins and passwords, to a simple Internet user.
Ironically, at the moment, Apple FTP access is open to an anonymous user!
MBP15: ~ $ ftp ftp.apple.com
Trying 17.254.0.79...
Connected to ftp.apple.com.
220 17.254.0.79 FTP server ready
331 Anonymous login ok, send your complete email address as your password.
230 Anonymous access granted, restrictions apply.
Remote system type is UNIX.
Using binary mode to transfer files.
200 Type set to I
ftp> ls -la
227 Entering Passive Mode (17,254,0,79,241,177).
150 Opening ASCII mode data connection for file list
drwxrwxrwx 7 ftpprod ftpprod 238 Nov 17 2009 .
drwxr-xr-x 15 ftpprod ftpprod 510 Nov 17 2009 ..
drwxrwxrwx 14 ftpprod ftpprod 476 May 22 18:28 .shared
drwxrwxrwx 3 ftpprod ftpprod 102 May 7 2003 Apple_Support_Area
drwxrwxr-x 20 ftpprod ftpprod 680 Aug 20 2007 developer
drwxrwxr-x 37 ftpprod ftpprod 1258 May 18 2004 emagic
drwxrwxr-x 11 ftpprod ftpprod 374 Mar 9 2004 filemaker
226 Transfer complete.
ftp>
Pay attention to the hidden folder '.shared'.
In the folder '.shared' there is also a hidden folder '.zzz_old_archives'.
They turned out to be a lot of tasty:
- Appleconnect
- Radar client
- Sonar client
- Nfa
- All sorts of useful PDF & HTML files
Programs were installed, tested, and some documentation shed some light.
So:
AppleConnect is special software for organizing VPN connections to Apple’s internal network, in particular, for gaining access to Apple’s internal resources. As I understand it, for authentication in AppleConnect previously used special keys (they are still in use) - eTokens, probably connected via USB. Now, in many cases, Apple ID authentication is acceptable (of course, every Apple ID has permissions for certain actions).
AppleConnect can live in the status menu next to the clock, and it’s easy to switch VPN and Apple ID settings for different inputs.
Of great interest to radar is the ray.apple.com server, whose ports are apparently only accessible from the VPN.
The tracker seems to be spinning on Oracle Application Server, Java, WebObjects, and, at least in the documentation, on IBM AIX servers.
I don’t have much faith in the latter, for the current day, given that Apple has its own good Xserve hardware. Or maybe they just don’t want to touch this ancient system.
In the process of reading the documentation, a certain IT&S company was also highlighted.
It is they who are invited to contact (by phone) for support via radar and on issues of connecting / receiving login.
Perhaps these are the guys from MIT that Apple is feeding.
Also, it is highly likely that this is their site: ist.mit.edu
Radar - a huge system (a la Xcode), with a logo (icon) in the form of a blue anteater catching an ant.
Designed for administrators, moderators and developers, as well as for readers from external organizations (oh, dreams).
Radar can work without a GUI from the command line.
Sonar - as I understood it at 4 nights, this is some rethinking of Radar, which contains mostly ready-made solutions to problems and allows you to add / edit solutions.
NFA - a virtual safe that protects various resources from prying eyes (useful when working with graphics, projects, documents).
In general, a very funny software - download, install, watch, read.
I still could not get access to the database - my logins in ADC do not have rights to connect to Apple VPN.
But the proximity of the sacred and the signature in the Apple Internal Use Only documents gave a hefty dose of adrenaline!
A few screenshots





for starters : (for connecting external AppleConnect settings)
Download, try, write about your results in the comments.
Hurry up, after this article anonymous access is likely to be quickly hidden.
Now that a simple developer has learned more, maybe we can change something in this unfair world for us ...
