How dangerous is DRM protection, or Video virus part 2
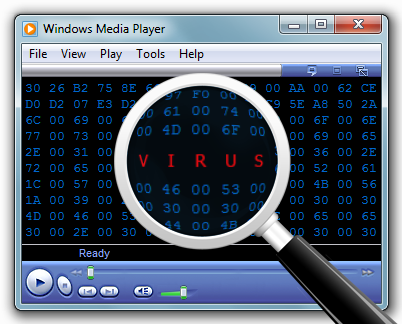
Flashbacks
After I read a post about TipTop being unable to watch a movie , I immediately remembered a similar case. Somehow opening a regular mp3 file, instead of starting playback, to my surprise, an unknown web page opened. The most interesting thing is that the page was opened in Internet Explorer (despite the fact that another browser was installed by default), and after all, on that page, the author of the file could add some special exploit for IE.At that moment, I was not thinking about the exploit page, and instead of carefully analyzing the file and sorting out what the problem was, I simply deleted it. The only thing I thought about when I saw the unusual behavior of the system is that someone is quite original in spinning up their site. Several years have passed, but since then I have not seen such cases. After reading the article about the video virus, I decided that at least this time I should not miss the opportunity to find out how safe some of the most harmless and common files are in the whole world.
Video file
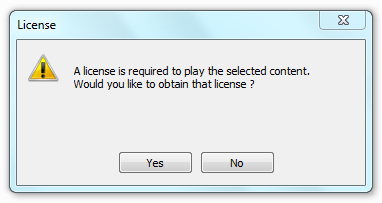
And since the respected TipTop, left a comment indicating the link to the file, I did not waste time and quickly downloaded the torrent file. But I was not alone - at the same time with me the same video file was downloaded by about 15 more people who, I thought, also want to analyze it. But now I realized that most of them most likely had different intentions and they did not know that today there would be no kin ©.After the download was completed, knowing that other players cannot play this file, I immediately opened it in Windows Media Player, and the first thing I saw was the message: “Download media usage rights”:

After that, a more convincing message appeared, offering to download the License-Installer file which, by the way, was already checked by the antivirus and turned out to be 100% clean:
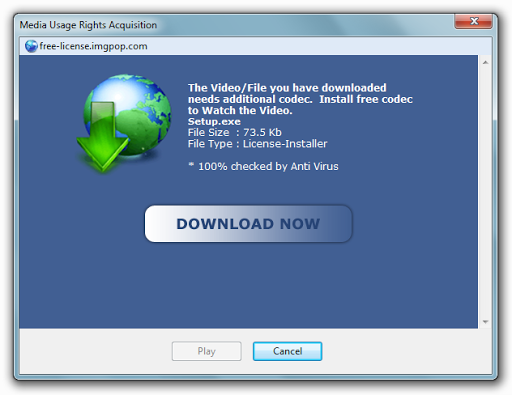
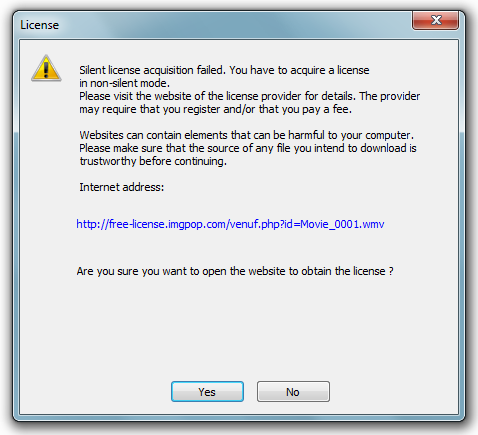
After carefully reviewing the message, I clicked on the 'Download Now' button and, in anticipation of any reaction from the antivirus, I saw a familiar window that suggested downloading the file from the license.compress.to server :

And then the first question arose, if the free-license.imgpop.com server is indicated on the first window , then why does this wonderful file offer to download a license from license.compress.to ? To find out what the problem was, I visited both sites, hoping to find something tasty there, but as expected, I did not find anything there.
DRM protection
After that, the first thing that came to mind was to “launch the sniffer”, but abstained (and did it right) - deciding to open the file in the Hex editor. I opened a file in the Hex editor that weighed 150 MB and, fortunately, everything was very simple, as already on the 20th line I found this piece of text: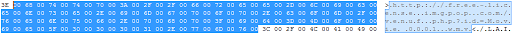
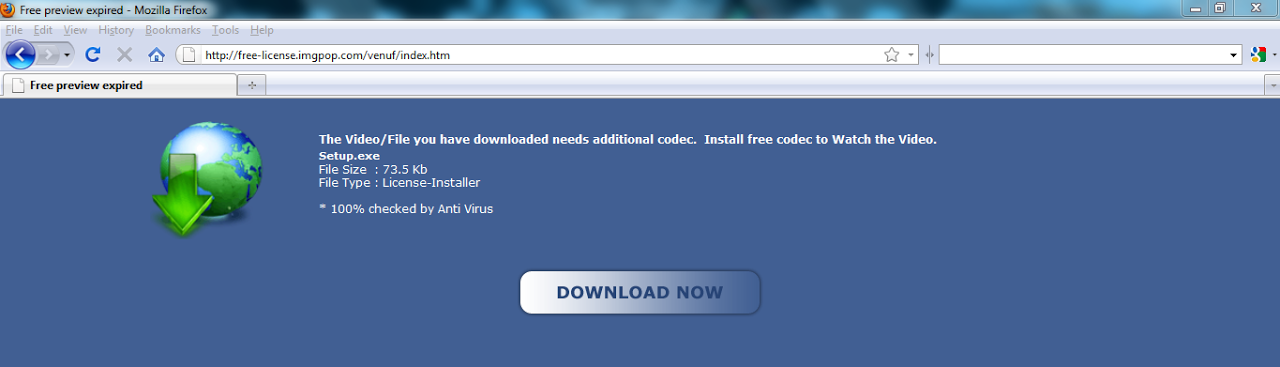
It has become much more interesting. Opened the page http: //free-license.imgpop.com/venuf.php? Id = Movie_0001.wmv , which redirected (HTTP / 1.1 302) to the page: http: //free-license.imgpop.com/venuf/index .htm , and there I saw a familiar picture, only a little bigger, and even in the browser:
While everything was going well and wanting to experiment a little, I decided to change the link from the video file to my own. But, having seen that even after changing the line, even WMP cannot open the file and not knowing what to do, asked Google if he could tell what the line is, WRMHEADER version = '2.0.0.0' , which (among many others) found using a hex editor?
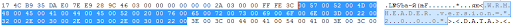
The answer was short and clear as daylight - I am dealing with DRM-protection of video files. That is, I discovered how, using legal and fairly convincing methods, attackers can successfully and confidently spread malicious files, because: firstly, no antivirus will detect that the video file is infected, and secondly, most users trust Microsoft will definitely run such files.
Moreover, WMP is not the only player that can open DRM protected files. I did not find a complete list of players, but I can confidently say that Nero ShowTime supports DRM, but unlike WMP, it reacts more carefully ... only if you confirm the license download, the web page opens in IE (despite the fact that it is not a browser default).
And now the most interesting: if you change the file extension from .wmv to .asf or .wma , nothing changes, that is, players will still play the media file and, most dangerous, in most cases .wma files will be opened on Windows Media Player By the way, I forgot to say that after I opened the video file in the Hex editor, for convenience, I deleted the unnecessary bytes and as a result the file size became 5.31KB.
Internet explorer
Probably, many people think that “There is no danger in this! I won’t download any licenses! Anyway, where does Internet Explorer, WMP and video files? ” At first, I also thought so, because there is a “Cancel” button, but as it turned out, the danger is not small, and “Cancel” will not save anyone if the file was opened in WMP. And Internet Explorer is the same browser, software for viewing websites ...I found information that it is possible to crack DRM protection, but did not do this. Firstly, I did not know whether it would be possible to change the link, and secondly, I chose an easier way. In the hosts file, added the line:
127.0.0.1 free-license.imgpop.comTo the root of the local server, created the venuf.php file and using WMP opened the video clip - a few seconds later the following message appeared:
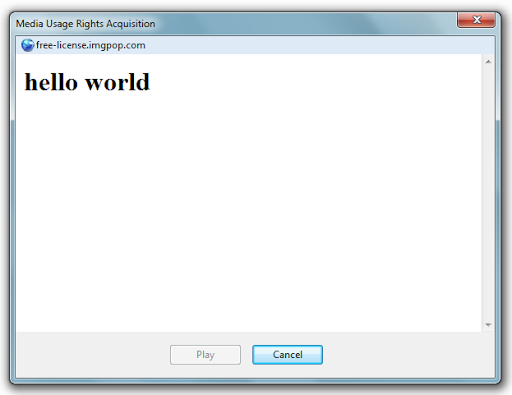
Then, using alert () , I decided to try whether it supports JavaScript - as a result, I got a blank page. I thought that it really didn’t work, but having connected my intuition, I quickly changed the alert () function to document.write () . The result caused a smile: this time the page was not empty, which means Windows Media Player supports JavaScript.
Now, the thought that the media player can open web pages, and even supports JavaScript, haunted me. Wanting to find out what this unusual player is, I added the line in the venuf.php file:
echo $_SERVER['HTTP_USER_AGENT'];and despite the fact that I have MSIE 8.0 installed, I received the following message:
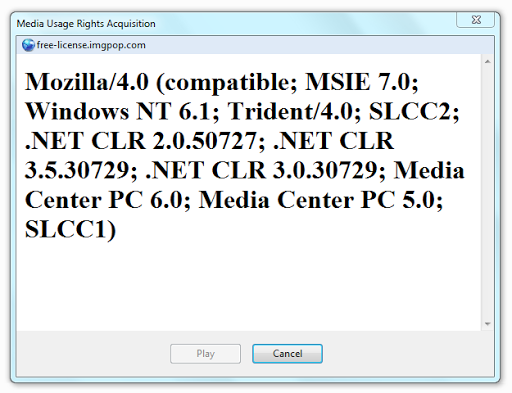
Finally, I decided to check one exploit for MSIE, written in JavaScript, causing a browser denial of service. I added an exploit to the page, opened the video file, and I didn’t have time to blink when Windows claims that “Windows Media Player has stopped working”:
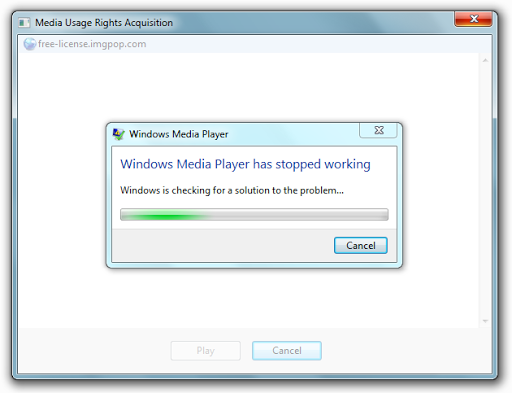
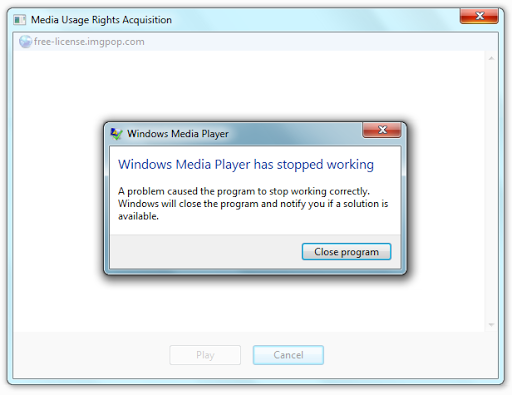
As you understand, when trying to play a video file, WMP was forced to disconnect, which means that it is vulnerable to an exploit designed for MSIE. I checked only one exploit, but that was enough to change my understanding of the security of media files .
Instead of postscript
After writing the last lines of this article, I suddenly had one idea: download, install and test one of the most popular multimedia players - Winamp . Which I did ... And when I tried to play the file, the following message appeared: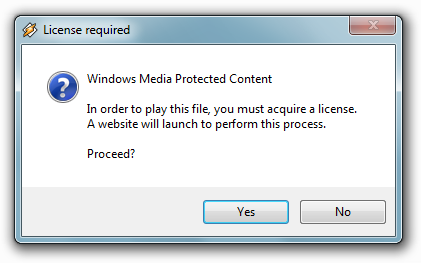
I was

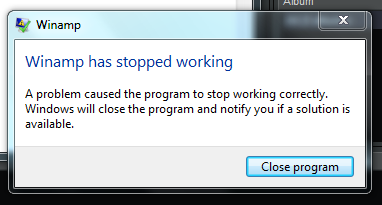
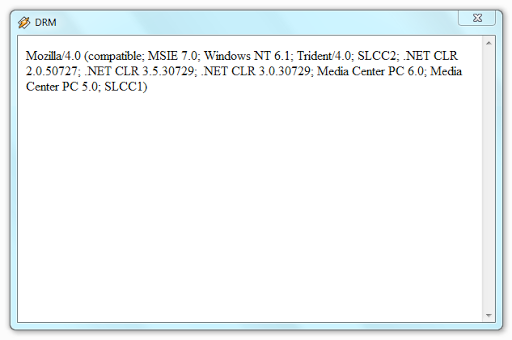
I did not immediately understand what the problem was, thinking that anything could happen, but after a few seconds, I remembered that the exploit code for MSIE remained in the venuf.php file . Then, using the $ HTTP_USER_AGENT variable, I found out that, like WMP, Winamp uses
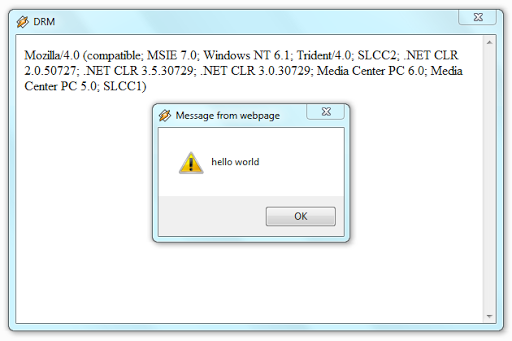
True, unlike Windows Media Player, Winamp does not warn where the license file will be downloaded from, but allows you to use the right click and see the source code of the page ... and also alerts work for it:
Conclusion
At first glance, not everything is as scary as it seems, but I want to draw your attention to the fact that by opening such a file the user will not be able to stop the exploit from launching, and the antivirus program is not able to help, since if it is a new exploit, then, most likely, it has not yet been added to the antivirus database.Just do not forget that not all users have other audio and video players installed. And yet, I do not believe that a user who waited 2 hours (at best) to download a long-awaited file, seeing that it is not playing, will just delete it, and no “do not open files in this player!” - will not help .
UPD:
Protection
To significantly reduce the risk of possible attacks, I recommend disabling in WMP the automatic licensing for DRM-protected files. To do this, open the Options (Options) tab and Privacy (Privacy) remove the check mark from the " Acquire licenses automatically for protected content '(Download usage right automatically when I play or sync a file):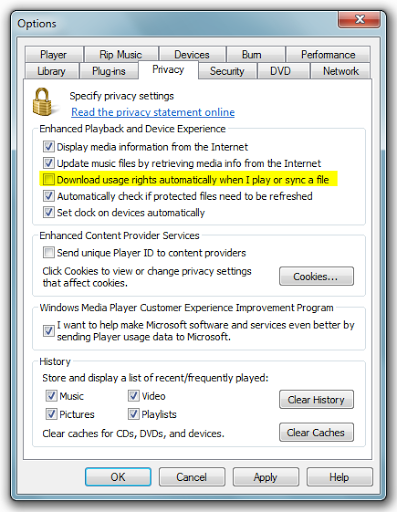
Now, when you open the file, WMP will ask if 'You really want to open a web page to get a license':
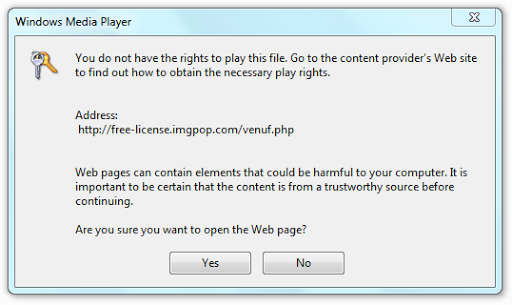
Despite the fact that developers warn of danger and know that “web pages may contain elements that may be dangerous for the computer” - they still turned off this option by default. Strange, isn't it?
UPD 2: ( Many thanks to the Dragonizer Habraiser for commenting )
Despite the fact that the User Agent is defined as MSIE 7.0, in fact it is not. The fact is that WMP opens web pages in compatibility mode, which means that:
• In the browser version line, the web browser is indicated as MSIE 7.0, not MSIE 8.0;
• Conditional comments and version vectors recognize the web browser as IE 7, not IE 8;
