Online Password Manager
I am pleased to introduce the online password manager - KeyMemo.com .
Immediately I hasten to answer the question - “How can I store my passwords on some website?”
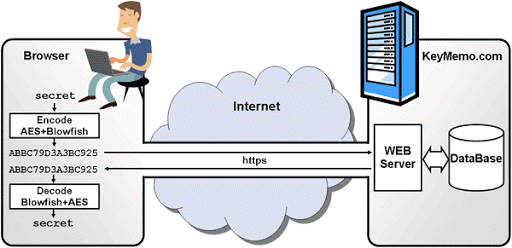
Everything is very simple, all passwords are encrypted on the client side, in the browser, using AES256 and Blowfish algorithms implemented in JavaScript. Only after encryption is your data transferred via https to the server. The encryption keys for the algorithms are different and are not transmitted to the server. All fields of each password (name, tags, note, etc.) are encrypted, the user login is also encrypted. As a result, only anonymous “garbage” is stored on the server; breaking the server for it is pointless. Question - why? I went the full way of storing passwords:
a piece of paper -> notepad with you -> file -> password manager -> portable password manager -> online password manager -> your password manager .
I will not even discuss the first two storage methods, it is a time bomb.
I administer two offices and manage to work for at least 3 computers in a day, so the offline password manager has a problem of synchronizing data between computers.
Portable password manager requires you to carry a USB flash drive. But the flash drive may get lost or fail. The flash drive must be connected to all computers. And the manager himself must run on all OSs.
There are managers who synchronize the password file through the ftp server, but this does not remove the cross-platform problems and the need to install the client on the machines for which I am for the first and last time this year.
The advantages of the online manager are obvious: it works on all platforms, it does not require installation, it does not require connecting flash cards, all data is synchronized through the server, everything is automatically backed up.
So for a while I was sitting on the online manager clipperz.com, but after a while he got me his brakes. Sometimes you need to quickly peek at a forgotten password, while clipperz.com boots up, already forgot what it wanted to remember. There was another problem that bothered me. Backup your passwords with clipperz.com should not forget to download manually. A person does not forget to do something regularly only the first three days.
Therefore, I wrote my password manager, where I solved the backup problem very elegantly, as it seems to me.
After each new password is added to KeyMemo.com, after 10 minutes, the server sends an html file to your several mailboxes, in which your encrypted passwords and decryption algorithms. If KeyMemo.com disappears once or the Internet disappears, just find the last letter from KeyMemo.com to open the attached file with your browser and enter your master password. The zip archive file weighs only 35 kb (for comparison, clipperz backup weighs 500 kb). As mailboxes, it is useful to specify mailboxes that are checked offline by email programs on your work, home computer or laptop. You will only need letters if KeyMemo.com is not available.
You no longer need to think about connecting a flash drive, installing a client, its compatibility with the OS, etc. It is enough to write down your password on KeyMemo.com and in 10 minutes it will be in all your mail programs. You just won’t be able to lose your passwords. Even if you want to get rid of them, you will have to clean all mailboxes, free mail services and backups of mail servers, and the admins of these servers will not let you do this. Of course, the KeyMemo.com database is also automatically backed up.
I consider such a backup system a distinctive feature of my service.
I consider the second feature lightness, speed and simplicity of my service.
The plans are for the next version with sharpening for HTML5, with data storage on the client and the ability to view it offline.
How it works?
To explain the operation of the system “on fingers” I’ll show you how anyone can make a reliable password storage system for themselves, which will allow you to encrypt everything, automatically backup it, and give access from anywhere.
Write all the passwords in an ordinary text file. Archive it with a password (long and complex password), send the Archive to a special (possibly free) mailbox. Forwarding to several of your other mailboxes (home, work, free) should be configured in this box. The archiver can use portable and store it in a free mailbox too. As a result, everything is reliable, transparent, only inconvenient.
KeyMemo.com does exactly the same thing, only in a convenient way. Instead of an archiver, JavaScript is used for encryption. Not all passwords are encrypted in one file, but each password is separate. The received "garbage" is sent not to the mail, but to the KeyMemo.com server, and it already sends them to your 5 mailboxes.
Details for the curious
About the encryption scheme looks like this: (non-essential details are omitted)
You enter two values
Hashing: All this is repeated 4 times with a different salt and it turns out: - the key for the AES256 algorithm (not transmitted over the network, not stored on the server) - the key for the Blowfish algorithm (not transmitted over the network, not stored on the server)
In practice, these values look something like this: they are overwritten. and sent to the server, the server returns wrong_login, or your garbage set. (Well, I say, garbage!) This garbage is decrypted first with Blowfish: Then AES256: You see your valuable secret Encryption before sending any information to the server is performed in the reverse order. Information is exchanged using the https protocol and before sending, the browser encrypts everything for the third time :-) After all, I'm paranoid. And of course there is an ssl certificate, etc., in short, everything is adult. Therefore:
Are JavaScript algorithms implemented correctly?
In this standard, test cases begin at page 27.
http://www.csrc.nist.gov/publications/fips/fips197/fips-197.pdf
The results of the AES used in KeyMemo.com in these test cases are the same as those specified in the standard.
MD5 is even easier to check. It is in Linux and in SQL, i.e. almost everywhere. The results are also consistent.
Blowfish did not check. Hoped on the authors of the implementation of Andre Mueller and Rainer Wollmann.
PS Do not kick much for the design. I am not a designer.
Immediately I hasten to answer the question - “How can I store my passwords on some website?”
Everything is very simple, all passwords are encrypted on the client side, in the browser, using AES256 and Blowfish algorithms implemented in JavaScript. Only after encryption is your data transferred via https to the server. The encryption keys for the algorithms are different and are not transmitted to the server. All fields of each password (name, tags, note, etc.) are encrypted, the user login is also encrypted. As a result, only anonymous “garbage” is stored on the server; breaking the server for it is pointless. Question - why? I went the full way of storing passwords:

a piece of paper -> notepad with you -> file -> password manager -> portable password manager -> online password manager -> your password manager .
I will not even discuss the first two storage methods, it is a time bomb.
I administer two offices and manage to work for at least 3 computers in a day, so the offline password manager has a problem of synchronizing data between computers.
Portable password manager requires you to carry a USB flash drive. But the flash drive may get lost or fail. The flash drive must be connected to all computers. And the manager himself must run on all OSs.
There are managers who synchronize the password file through the ftp server, but this does not remove the cross-platform problems and the need to install the client on the machines for which I am for the first and last time this year.
The advantages of the online manager are obvious: it works on all platforms, it does not require installation, it does not require connecting flash cards, all data is synchronized through the server, everything is automatically backed up.
So for a while I was sitting on the online manager clipperz.com, but after a while he got me his brakes. Sometimes you need to quickly peek at a forgotten password, while clipperz.com boots up, already forgot what it wanted to remember. There was another problem that bothered me. Backup your passwords with clipperz.com should not forget to download manually. A person does not forget to do something regularly only the first three days.
Therefore, I wrote my password manager, where I solved the backup problem very elegantly, as it seems to me.
After each new password is added to KeyMemo.com, after 10 minutes, the server sends an html file to your several mailboxes, in which your encrypted passwords and decryption algorithms. If KeyMemo.com disappears once or the Internet disappears, just find the last letter from KeyMemo.com to open the attached file with your browser and enter your master password. The zip archive file weighs only 35 kb (for comparison, clipperz backup weighs 500 kb). As mailboxes, it is useful to specify mailboxes that are checked offline by email programs on your work, home computer or laptop. You will only need letters if KeyMemo.com is not available.
You no longer need to think about connecting a flash drive, installing a client, its compatibility with the OS, etc. It is enough to write down your password on KeyMemo.com and in 10 minutes it will be in all your mail programs. You just won’t be able to lose your passwords. Even if you want to get rid of them, you will have to clean all mailboxes, free mail services and backups of mail servers, and the admins of these servers will not let you do this. Of course, the KeyMemo.com database is also automatically backed up.
I consider such a backup system a distinctive feature of my service.
I consider the second feature lightness, speed and simplicity of my service.
The plans are for the next version with sharpening for HTML5, with data storage on the client and the ability to view it offline.
How it works?
To explain the operation of the system “on fingers” I’ll show you how anyone can make a reliable password storage system for themselves, which will allow you to encrypt everything, automatically backup it, and give access from anywhere.
Write all the passwords in an ordinary text file. Archive it with a password (long and complex password), send the Archive to a special (possibly free) mailbox. Forwarding to several of your other mailboxes (home, work, free) should be configured in this box. The archiver can use portable and store it in a free mailbox too. As a result, everything is reliable, transparent, only inconvenient.
KeyMemo.com does exactly the same thing, only in a convenient way. Instead of an archiver, JavaScript is used for encryption. Not all passwords are encrypted in one file, but each password is separate. The received "garbage" is sent not to the mail, but to the KeyMemo.com server, and it already sends them to your 5 mailboxes.
Details for the curious
About the encryption scheme looks like this: (non-essential details are omitted)
You enter two values
loginand masterkey. Hashing: All this is repeated 4 times with a different salt and it turns out: - the key for the AES256 algorithm (not transmitted over the network, not stored on the server) - the key for the Blowfish algorithm (not transmitted over the network, not stored on the server)
temp_val=MD5(login+salt1+ masterkey)+ MD5(login+salt2+ masterkey)
temp_key=MD5(login+salt3+ masterkey)+ MD5(login+salt4+ masterkey)
TargetValue1=AES256_Encode(temp_key, temp_val)TargetValue1TargetValue2TargetValue3- login for the server (transferred to the server for authorization) TargetValue4- password for the server (transferred to the server for authorization) In practice, these values look something like this: they are overwritten. and sent to the server, the server returns wrong_login, or your garbage set. (Well, I say, garbage!) This garbage is decrypted first with Blowfish: Then AES256: You see your valuable secret Encryption before sending any information to the server is performed in the reverse order. Information is exchanged using the https protocol and before sending, the browser encrypts everything for the third time :-) After all, I'm paranoid. And of course there is an ssl certificate, etc., in short, everything is adult. Therefore:
TargetValue1=46592074424B97EDFEBEB259A1B20390343C282C2D0B2154D5FF7E10BD0B5065
TargetValue2=721A6DD94327E53079D340CB563D94C389319262FA2E8F293BAD4EE4D2031B7D
TargetValue3=277567FD786E432F9762B33FDA8808A31933149573D1C84A8C1795CAC0FE6178
TargetValue4=DC7AF573B283F97017E91480611D9B0EFBF44F33AF0A03C8D00FA97DD7E16B4Clogin, masterkey, temp_val, temp_keyTargetValue3TargetValue4trash_from_server=C0ED5E324AD7DD3959493F4EFFE056C59AC6EC120C6123EF2D78A8202BF0F3F5A90BE8E0FE393C63B13D9CC95ADAC1DF8582B867220F5E2CCF416A23FDC22CE05C1BD0F5A7DE35D3C21BF2D0E4243348….. tmp=Blowfish_Decode(TargetValue2,trash_from_server);secret=AES256_Decode(TargetValue1,tmp);
alert(secret); // show bla-bla-bla :-)- I don’t even know your logins :-) and especially all the rest.
- A forgotten master password cannot be recalled. It is simply not stored anywhere.
- All algorithms are duplicated. Double hashing, double encryption. This is in case if tomorrow some algorithm is recognized as not stable. After all, I'm paranoid.
- You can’t press F5 in the browser, otherwise the values of TargetValue3 and TargetValue4 will be lost, but I don’t store them on the server, in cookies, or in the URL.
- To change the username and / or password, you have to upload all the passwords to the client, decrypt with the old password, encrypt with the new one, and send it to the server again.
Are JavaScript algorithms implemented correctly?
In this standard, test cases begin at page 27.
http://www.csrc.nist.gov/publications/fips/fips197/fips-197.pdf
The results of the AES used in KeyMemo.com in these test cases are the same as those specified in the standard.
MD5 is even easier to check. It is in Linux and in SQL, i.e. almost everywhere. The results are also consistent.
Blowfish did not check. Hoped on the authors of the implementation of Andre Mueller and Rainer Wollmann.
PS Do not kick much for the design. I am not a designer.
