GSM base station hidden in an office printer

GSM base station
Intelligence and intelligence services around the world use fake base stations (IMSI traps, called StingRay for Americans), which operate in passive or active mode . In passive mode, the fake station simply analyzes the signal from the surrounding base stations. Much more interesting when the device is switched to active mode. In this case, the IMSI trap forces the surrounding client devices of the cellular communication to connect to themselves, disconnecting them from the operator’s base station (MTS, VimpelCom, etc.). The task is carried out with the help of broadcasting a more powerful signal than the surrounding stations (for more details on the operation of fake base stations, see the article "The Brave New World of Cell-Site Simulators" (Albany Law School: 11–12. Doi: 10.2139 / ssrn.2440982).
Fake base stations are used not only by special services, but also by other people. For example, in the last season, Mr. Robot hackers installed a femto cell (low-power and miniature cellular communication station) right in the FBI office, having the opportunity to listen to their conversations. In business, competitors can use such a device to quietly listen to the other party’s conversations. In Russia, Natalya Kasperskaya offers to install spy femtocells in the offices of commercial companies so that management can safely record conversations of employees and visitors.

The device connected to a fake cellular station PRISM: The Beacon Frame. As part of a research project, the station sends a notification of the connection to the subscriber’s phone. The real infrastructure of special services works without sending notifications.
Such gadgets are very much in demand in the modern era, because so many people constantly use cellular communication, transmitting confidential information through these channels, without using end-to-end encryption. It is very convenient to identify people by their phone numbers.
Heroes of the show Mr. Robotput a femtocell under the table next to the router. Obviously, in this form, it cannot work for a long time, because sooner or later the “extra” device will be noticed by a cleaning woman or an occasional agent who will bend down. In addition, the femtocell has a very small radius of action, so it is unlikely that it will be able to kill the signal of a real base station for subscriber devices on adjacent floors. It is guaranteed to work except in the same office, and then - as lucky.
To correct this deficiency, an office needs to install a more powerful base station. But how to disguise it? A great solution was proposed by New Zealand engineer Julian Oliver. He designed the base station design disguised as an HP office printer .
On the streets, base stations are disguised as objects of the environment - trees or lanterns .

Cellular station, poorly disguised as a palm tree. Marrakesh, Morocco

Cellular station, disguised as a lantern, for some reason, put next to this lantern. Milton Keynes, UK
The Hewlett-Packard Laserjet 1320 laser printer for office space looks as natural as a street lamp. He will not cause suspicion. At least as long as it continues to work properly. For demonstration purposes in the Oliver project, the printer is set to automatically print metadata about intercepted calls and SMS messages, along with the text of these messages.

The author explained in detail how the fake base station works. A BladeRF programmable SDR transceiver was placed in the printer case (this wonderful device was told on Habré). In the photo it is fixed at the top right. The transceiver connects to a miniature Raspberry Pi 3 card (bottom left), and all the hacker electronics is connected to the printer motherboard (the largest board in the photo).
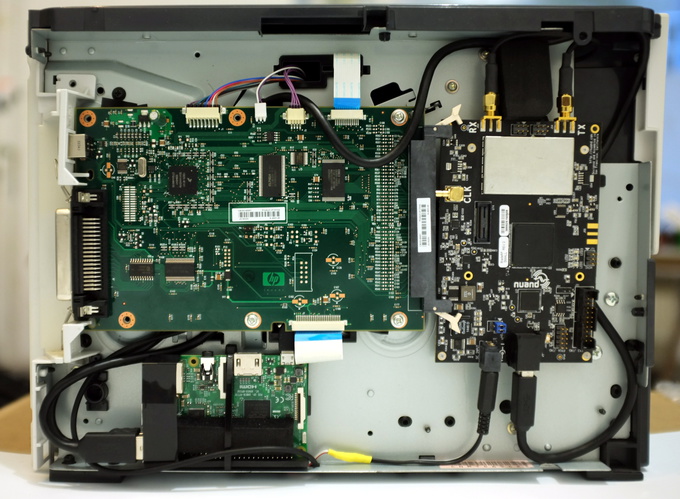
For power, a car USB adapter is used that converts the printer 21−22 V to 5 V necessary for the transceiver and the “raspberry”. Such adapters are usually inserted into the vehicle's cigarette lighter (12−24 V) to power portable electronics.
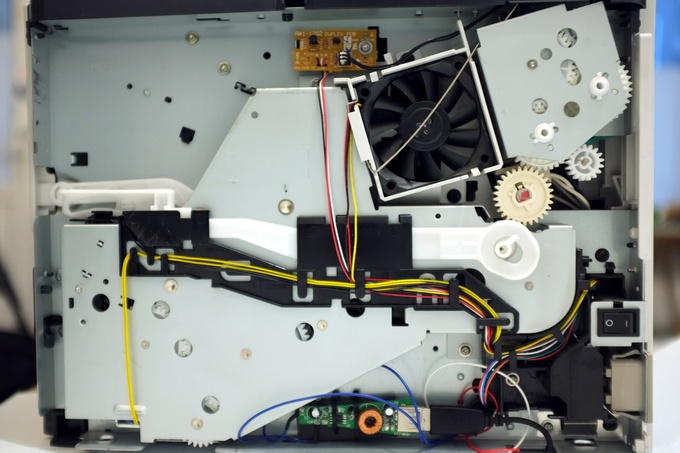
The cartridge compartment is slightly modified to fit two omnidirectional antennas (TX and AX) connected via an SMA cable to a BladeRF transceiver.
The author of the paper says that they chose a Hewlett-Packard Laserjet 1320 printer for several reasons. First, it has a strikingly inconspicuous appearance - a completely faceless design that does not attract attention. Secondly, the internal cavities in the housing are ideal for accommodating all electronics and cables. No detail comes out and is not visible from the outside, except for the standard power cable. When the USB adapter is plugged into a standard connector, the Hewlett-Packard Laserjet 1320 functions normally as a regular office printer.
Raspberry Pi 3 was chosen after unsuccessful attempts to ensure the stable operation of the YateBTS base station controller programunder Intel Edison, Beaglebone Black and even the I-MX6 Marsboard. Unlike ancient OpenBTS, the YateBTS program is more demanding on processor performance.
The fake base station software in the printer runs on top of the open YateBTS code. For demonstration purposes, developed several scripts. For example, one of them filters the log, forms a PDF document and sends it to print.
#!/bin/bash
readonly FH=/home/pi/yate.log
rm -f $FH# Start the BTS, log to $FH and background
yate 2>&1 -l $FH &
sleep 1
echo"Starting up..."
last=" "whiletrue;
do# Poll every 10 seconds
sleep 10
# Check log for new sniffed 'call route' entries and do some subbing
cur=$(cat $FH | grep -A 16 "Sniffed\ 'call.route'" | sed -e "s/param\['//" \
-e "s/'\]//" -e 's/thread.*//' -e 's/time\=[0-9].*//' \
-e 's/\ data=(.*//' -e 's/\ retval=.*//' \
-e 's/\ tmsi.*//' -e 's/ybts/Stealth\ Cell\ Tower/' \
-e 's/Sniffed/Monitored\ =/' -e '/^\s*$/d' \
-e 's/^\s*//' | tail -n 13)
if [ "$cur" != "$last" ]; thenif [ ${#cur} -gt 1 ]; thenecho"New SMS events detected"# Test to see if an IMSI is in the string. If not, look it up and put it inif [[ $cur != *imsi* ]]; thencaller=$(echo"$cur" | grep "caller" | awk '{ print $3 }' | sed "s/'//g" \
| tr -cd'[:print:]')
imsi=$(cat /usr/local/etc/yate/tmsidata.conf | grep "$caller" \
| cut -d '=' -f 1)
cur=$(echo"$cur" | sed -e "s/\ called\ .*/imsi\ =\ '$imsi'/" )
fi# Make it all uppercase
event=$(echo -e \\n"$cur" | tr 'a-z''A-Z')
echo"printing file..."echo"$event" > printme
# Format a postscript file with enscript
enscript -r --header='SMS EVENT RECORD|%W|%* UTC' -i2cm --margins=10:10:30:10 \
-o printme.ps -f Courier@15/12 printme
# Convert to PDF
ps2pdfwr printme.ps printme.pdf
# Send it to the print queue for immediate processing
lp -U pi -o a4 -q 100 -d hp_LaserJet_1320_2 printme.pdf
fi
last=$curfidoneAnother script randomly selects one of the phone numbers that connected to the base station, calls it and reproduces the classic hit Stevie Wonder "I Just Called To Say I Love You" .
#!/bin/bash
readonly HOST=127.0.0.1
readonly PORT=5038
readonly DATA=/usr/local/share/yate/sounds/stevie.au
readonly TMSI=/usr/local/etc/yate/tmsidata.conf
readonly CC=49 #MSISDN prefix, matching that of definition in yate conf.callone () {
# Play "I Just Called To Say I Love You" by Stevie Wonder, on pickup echo"call wave/play/$DATA$mt" | netcat -i 1 -q 1 $HOST$PORT# Or, setup channel and route to IAX/SIP# echo "call 'iax/iax:$PORT@11.22.33.44/$PORT' $mt" | netcat -q 1 $HOST $PORT
}
callall() {
for mt in${UES[@]}#override $mtdoecho"calling $mt"
callone
done
}
whiletrue;
do
tmsilen=$(wc -l $TMSI | awk '{ print $1 }')
ues=($(cat $TMSI | grep -A $tmsilen ues | sed 's/\[ues\]//' | cut -d ',' -f 3))
if [ ! -z $ues ]; then
ueslen=${#ues}
RANGE=$ueslen
select=$RANDOMlet"select%=$RANGE"
mt=${ues[$select]}
callone
fi
sleep 30
doneCompiled binaries for Raspberry Pi 3: yate_r-pi3_4.4.11-v7_debian-8.0.tar.gz .
Good luck with your experiments!
