In Australia, they spread malicious software by throwing flash drives into mailboxes

These are the flash drives found in some regions of Australia in their mailboxes.
What does a person who finds a flash drive lost by someone usually do? Of course, he is happy with the free gift and hurries to connect his find to his PC. In most cases, these flash drives are someone's photos and documents. In this case, other people's files are usually viewed, then erased and the drive is used for its intended purpose by the new owner.
But it also happens that someone else's flash drive damages the PC or laptop. It can be a specially designed device, the purpose of which is to cause a breakdown of the computer to which it is connected. This was written several timeson Habré. In addition, the flash drive can be harmless to iron, but dangerous to the software of the new owner. In other words, malware can be on such a drive.
Now the attackers from Australia are practicing an unusual way of spreading malicious software. Flash drives are thrown into the victim's mailbox. The calculation is based on the fact that, having found the device in its box, the potential victim will immediately run to check what kind of device it is and what files are written on it. When the drive is connected to the computer, the autorun is triggered and the malware penetrates the victim's PC.
“USB drives are a significant danger, citizens should avoid plugging such flash drives into their computers and other types of devices,” the police said. After the victim connects the flash drive, malicious software offers to visit some streaming service with video, other problems are also observed (which ones, the police do not report).
On the web for several monthsThere are tweets and other messages from users from Australia who received a similar "gift." Probably, some users are more knowledgeable than others, and do not connect such flash drives to their computers. But many more users are in a hurry to immediately try out the donated device.
“Someone threw a flash drive in my inbox. No notes, nothing, just a flash drive. I wanted to see what was on it, ”wrote another user.
This Twitter user did not succumb to temptation and did not check what was there on the flash drive from the mailbox. Hearing that the Australian police are now conducting an investigation, he said that he still has a flash drive, and that the content on it is unknown.
Not so long ago, a special study showed that many people are ready to immediately begin checking the contents of the found flash drive. Curiosity outweighs all cons. This character trait was displayed on the screen in Mr. Robot. This was shown in the sixth series of the first season. Here, one of the characters, a member of the F-Society community, leaves several flash drives in the prison’s parking lot, hoping that someone from the guards or guides will pick up the flash drive, insert it into the PC, after which the hackers can take control of the network infrastructure of the building.
Does it really work? Yes, it works, and not bad. A group of researchers from the University of Illinois last year conducted a special experiment. The authors of the project left 29 flash drives in different places of the Urbana-Champaign campus. 48 percent of people who found such flash drives inserted them into their computers. And almost all those students who found flash drives (98%) took them with them or moved them to another place. Very few users, in fact, are guided by security considerations when working with their computers. About 67% of users do not use any protection measures at all, be it an antivirus or a firewall.
“I think my Macbook is well protected against viruses,” said one respondent interviewed by network security experts. And this point of view is quite common among users of Apple laptops. They are confident that their system is well protected from viruses and users of Windows and Linux PCs.
Of the 297 flash drives, 135 were connected to a computer. Researchers who left flash drives on campus did not write malware onto these media. Instead, they placed in the root of the HTML file, which when launched sent the authors a warning that someone was interested in the contents of the drive when trying to open this file. Of course, to send such a message was needed internet.

These flash drives were left on campus (they were thrown on the ground, "forgotten" on tables and chairs). Source: University of Illinois
“This problem has no simple solution. The problem is that an ordinary person is subject to the influence of emotions, momentary mood. There is also a difference between warning users about the danger of any actions and showing them the consequences of such actions, ”said one of the study participants.
Australian cybercriminals who distribute flash drives with malware are well aware of people's weaknesses, and take advantage of these weaknesses. No matter how many people would warn about the danger of opening found flash drives, there will always be someone who picks up the drive and immediately connects it to your computer. And it is good if there is no secret data on such a PC. But such a curious user may be an employee of the bank or the military.
Flash drives can be dangerous not only because with their help someone distributes malicious software. There are devices that can burn the USB port or even the motherboard of the computer to which they are connected. A typical example is USB Killer. This is a special device in the form factor of a flash drive, which leads to the inoperability of systems with a Type-C port (this is a specialized version of USB-Killer).
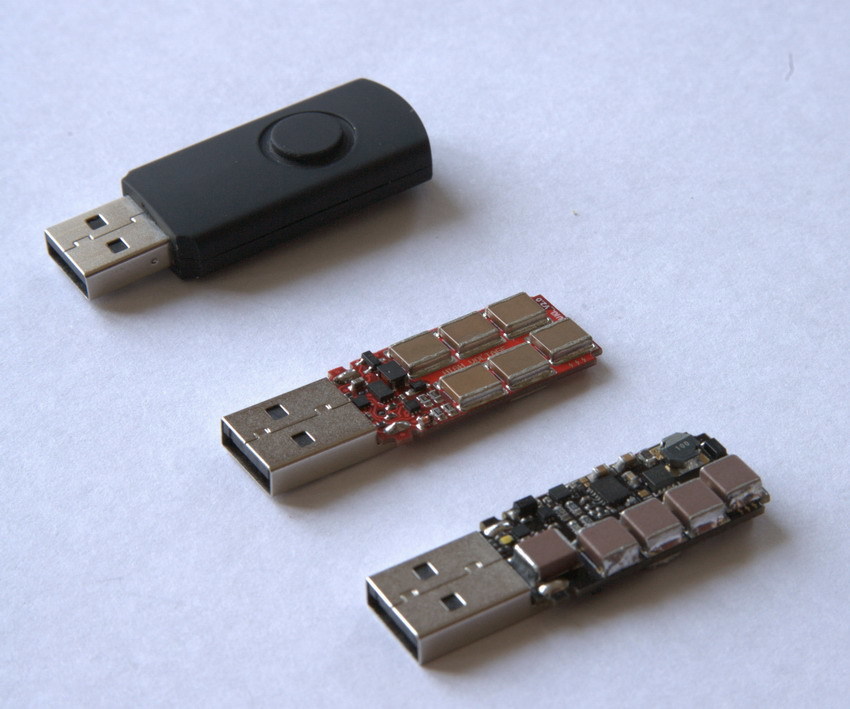
There are other versions of the "killer computers and laptops." For example, USB killer v2.0 (and the features of the first version can be found here). A feature of the device is double the “output” voltage of 200V. As soon as the "killer" is connected to the USB port, the operation of the voltage converter starts up, the capacitors are charged up to 220V. As soon as the capacitors are fully charged, the converter shuts off, and the energy of the capacitors is supplied to the contacts of the USB interface.
Here are the consequences of using USB Killer.
As you can see, experimenting with a flash drive found somewhere can be deadly for a PC or laptop. If the computer does not “die”, the victim can get malware that can clear the user's bank account or make the compromised PC a distributor of malicious software on the Web.
Only registered users can participate in the survey. Sign in , please.
