Training Cisco 200-125 CCNA v3.0. Day 12. Advanced VLAN
- Transfer
- Tutorial
Today's lesson will be dedicated to advanced VLAN learning. Before starting, I remind you again so that you do not forget to share these videos with friends and like our YouTube channel and group on Facebook. Today we will explore three topics: Native VLAN, VTP (VLAN Trunk Protocol) and VTP Pruning. First, recall what trunking is, and touch on topics from the last two video tutorials.
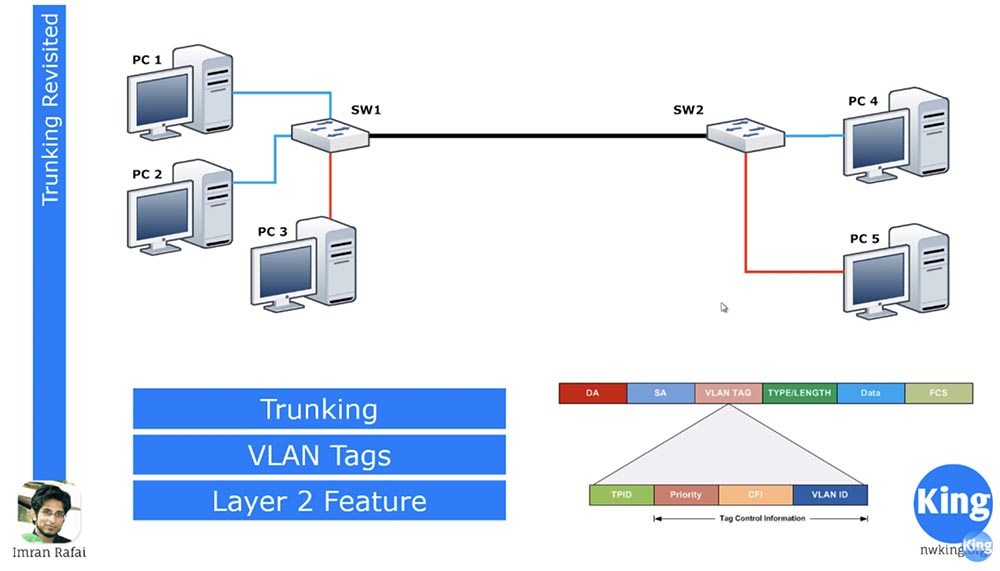
So, a trunk is a connection that we use to connect one switch with another switch. VLAN is a technology that is applicable only to switches, but any device that speaks the encapsulation language and is associated with a switch using the .1Q protocol understands everything about VLAN. Computers do not know anything about this technology.
In the figure above, PC1, PC2, and PC4 are part of the blue VLAN, as you remember from the previous lesson, this is VLAN10. The line itself, indicated in blue, has nothing to do with the VLAN, because the VLAN only touches the switch port. Thus, both ports of the left switch belong to VLAN10 and any incoming or outgoing traffic is associated only with this network. The switch knows that the traffic on these blue ports has nothing to do with the red port, because these are two different virtual lines.
VLAN is a concept for switches, so each switch supports the creation and storage of a database of virtual networks. This is a table that indicates which port corresponds to a specific VLAN. Thus, if the switch receives traffic for PC1, it checks whether this traffic is part of VLAN10 and forwards it to the computer. If the traffic from PC1 is for PC4, the switch will route it through the SW1-SW2 trunk. As soon as traffic enters the trunk port of the first switch, it supplies the frame with the VLAN TAG header, which contains the VLAN ID, in our case it is 10. After receiving this traffic, the second switch reads the frame information, sees that it is VLAN10 traffic, and routes it to the blue port for PC4.
Thus, trunking is the process of transferring traffic between two switches, and VLAN TAGS are frame headers that identify a specific virtual network and indicate which network this traffic should be directed to. If by mistake the blue traffic gets to the computer through the red line, he will not even know how to read it. It is as if someone is speaking a foreign language with a person who does not know this language. So, the computer is completely incapable of recognizing VLAN tags. The PC3 computer is connected to the switch through the access port, and the traffic we mentioned can be sent only through the trunk port.
All these are features of the 2nd level of the OSI model to which switches belong. In order to better understand the essence of VLAN and tags, we must think like a switch. Suppose a switch is a room with 5 people in it, and you are the owner of this room. Three people under numbers 1,2 and 4 belong to the same group, and two people under numbers 3 and 5 belong to the other, and your duty is to make sure that only people belonging to the same group can talk to each other.
We continue the discussion of the concept of native VLAN. As already mentioned, each switch port is associated with a specific VLAN.

For example, two ports of the first switch are connected to VLAN10, a third access port is with VLAN20, and the fourth is a trunk port. In the same way, SW2 is connected to PC4 through the VLAN10 port, to PC5 through the VLAN20 access port and to the hub through the trunk port. However, we have one problem - switches are expensive, so a scheme is often used in which two switches are connected to each other through a hub. Two switches are connected to the hub using trunks, but the hub itself does not know anything about the concept of VLAN, it simply copies the signal. As we already said, if VLAN traffic is sent directly to the computer, it will drop it, because it does not understand what it is. How do we deal with a PC6 computer that is directly connected to the hub if it is going to establish a connection with the PC4 computer?
PC6 sends traffic that goes to switch SW2. Having received this traffic, the switch sees that the frame does not have a VLAN tag and does not know which network to send it to - VLAN10 or VLAN20. For this case, Cisco has created a technology called Native VLAN, and by default VLAN1 is Native VLAN.
Suppose we have another computer, I will draw it over the switch SW2, and this PC is connected to the switch through the port VLAN1. The same computer is located above SW1 and is also connected to it via VLAN1. I will draw another computer under the right switch.
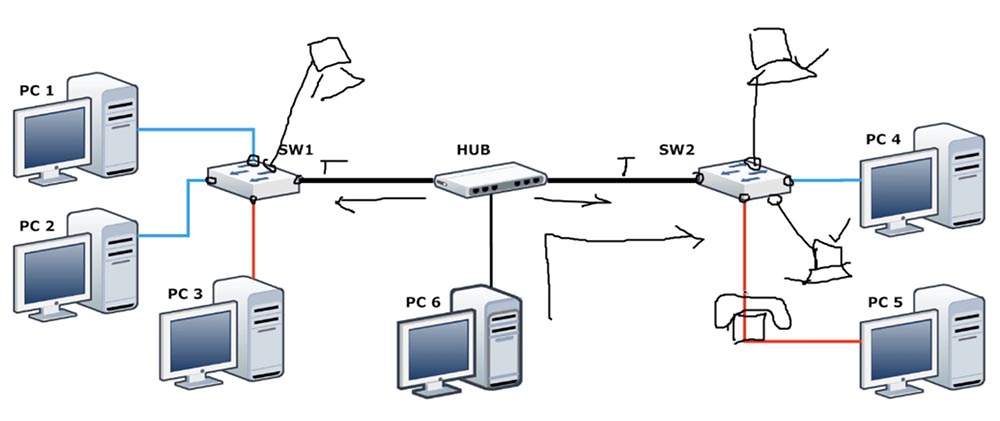
Two computers connected to switch SW2 via VLAN1 can communicate with each other, but are not able to communicate with other computers. When a switch receives untagged traffic through a trunk, it considers that this traffic is addressed to VLAN1, or Native VLAN, and forwards it to computers connected to VLAN1 ports. Similarly, when a switch receives untagged PC6 traffic, it addresses its VLAN1 network.
What happens if we have a Cisco IP phone on the red line of VLAN20 that is connected to PC5 and switch SW2? This is a typical layout of office networking equipment. In this case, the Native VLAN concept is also used. As I said, the computer does not know what VLAN is, and the phone knows. The question is whether we can send data and voice over the same VLAN. This is a very dangerous situation, because if the computer is on the same line of communication with the IP phone, the hacker can easily connect to such a communication channel and use Wireshark to intercept voice packets. Then he can convert these voice packets into an audio file and eavesdrop on any telephone conversation. Therefore, in practice, voice and data traffic are never transmitted over the same VLAN.
We turn the port to which the IP phone is connected into a trunk port, and we believe that any traffic passing through this port is VLAN30 voice traffic. Any Cisco IP phone uses the 802.1q encapsulation protocol, commonly referred to as .1Q or Dot 1Q. Thus, when the traffic from the phone falls into the corresponding port, the switch understands that this is VLAN30 voice traffic. We must have another phone that is connected to the SW switch, which is also part of VLAN30.
What happens in this case with a PC4 computer that is connected to the switch through the access port? After all, all the traffic that this computer exchanges with the switch belongs to the blue VLAN10. However, PC5 is connected to the switch via a trunk, and for the trunk we do not configure any VLAN! In this case, the port operates in trunk mode, not access mode, so we cannot use the switchport access VLAN # command. It uses the same concept as in the case of PC6 - if the switch receives untagged traffic, it routes it to the native VLAN port, by default it is VLAN1.
The question is whether native VLAN can be changed. The answer is yes, you can do this, for example, in the case of the red line, you can change the native VLAN to VLAN20, and then the switch will redirect the traffic from PC5 to the VLAN20 network. Since both switches are connected by trunk, the SW2 switch, having received the VLAN20 traffic, will consider it the native VLAN traffic and will send the SW1 switch as untagged.
Having received this traffic, switch SW1 recognizes it as untagged native traffic, and since its native VLAN is VLAN1, it will send this traffic to this network. If we change the native VLAN, we must do this with care to make sure that all the native VLANs in all switches have changed correctly, otherwise this can cause a lot of problems.
This was a brief overview of native VLAN, and now we will move on to the proprietary VTP Trunking Protocol (VLAN). First of all, you should remember that, despite its name, VTP is not a trunking protocol.
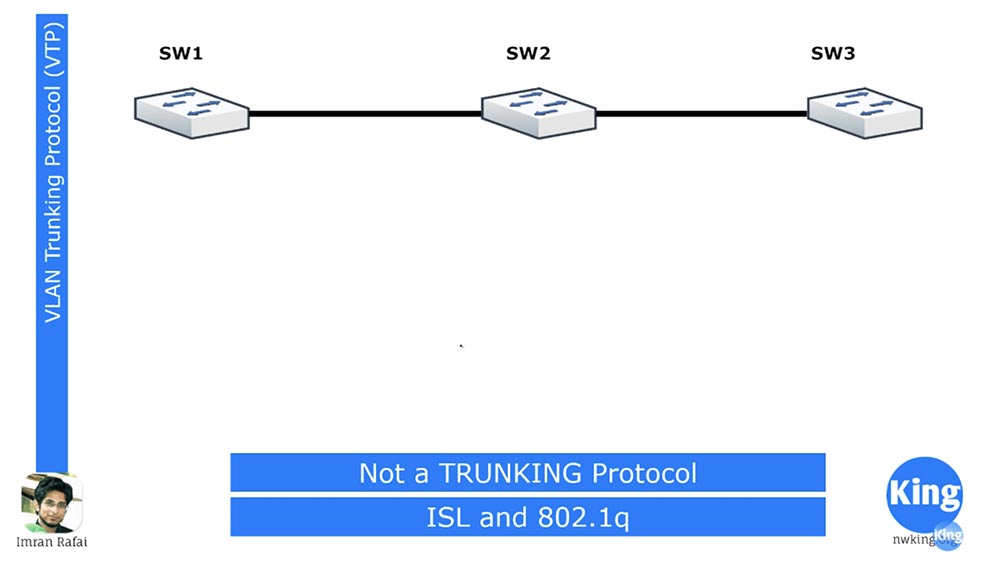
From previous lessons, we know that there are only 2 trunking protocols: the proprietary Cisco protocol called ISL and the generally accepted 802.1q protocol.
VTP is also Cisco’s proprietary protocol, but doesn’t do trunking in the sense of creating trunk connections. Suppose we created VLAN10 on the port of the first switch to which the computer is connected. Further we have trunk SW1-SW2 and trunk SW2-SW3. When trunk port SW1 receives computer traffic, it knows that it is VLAN10 traffic and forwards it to the second switch. However, the second switch does not know what VLAN10 is, because nothing except the trunk is connected to it, therefore, in order to receive this traffic and send it further, it creates VLAN10 on its ports. Switch 3 will do the same - after receiving traffic on the trunk, it will create VLAN10.
You can create two access ports on SW3, and both will be VLAN10. Suppose that on all 3 switches I want to create another network - VLAN20. This will only be possible after the ports for VLAN20 are created. The more devices, computers, and switches that are added to your network, the more difficult it becomes to create new VLANs, which is why Cisco automated this process by creating a VTP.
If we create a new VLAN, let's call it VLAN30, on one of the switches, then on all other switches connected by a trunk, the same VLAN30 network is automatically created.

The updated, updated VLAN database is simply sent out to all switches, after which you just have to create an access port for the computer. Without this protocol, you will have to manually reconfigure all switches. The disadvantage of VTP is that if you make changes to the VLAN database, it changes the revision number - the revision number. Usually, when you use a switch right out of the box, all settings have a zero revision number. When you add a new VLAN, such as tenth, database SW1 gets revision number # 1. In this case, the second switch says: “ok, you have revision 1, and I have revision 0, so I have to change my revision number to 1 and copy all the data from your VLAN table to my table.” The third switch does the same.
Suppose now 2 switches adds VLAN20 and changes the revision number to 2, then the first and third switches must do the same. Each time you change the revision number, the protocol checks who has this number higher and changes all other revision numbers to this number, while updating its VLAN table. Moreover, VTP unconditionally trusts the switch with the highest revision number.
Imagine this situation. A new employee comes to the company and discovers somewhere in the corner a switch that is used to train staff. He does not know anything about this, sees that this switch looks newer, and decides to connect it to a shared network. He configures this switch, connects it, for example, to the SW2 switch and creates a trunk. And as soon as it turns it on, your entire network drops! Everything stops working, because the connection between computers and switches completely disappears.
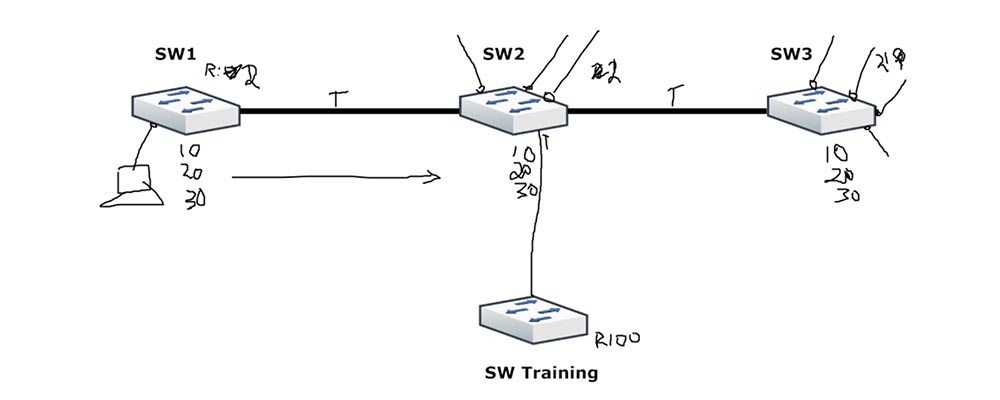
Why did this happen? The maximum revision number of the switch company is 50, because the company has only 5 VLANs - 10,20,30,40,50. The new switch was used for training, more networks were connected to it, a lot of changes were made to the settings, as a result of which its revision number increased to 100. At the same time, it has only one network at number 105 in the VLAN database.
After SW Training connected to SW2 via a trunk, the second switch saw that the beginner had a higher revision number, and decided to change his number to a higher one. At the same time, he copied to himself the VLAN table of the new switch, automatically deleting all of his existing VLAN10,20,30 networks ...., replacing them with one VLAN105, which had not existed in the existing network before. The first and third switches did the same, changing the revision number from 50 to 100 and deleting the old networks from the database, because they were not contained in the VLAN table of the SW Training switch.
Switch SW1 created access ports for the VLAN10 network, but after updating the revision, this network disappeared. The switches are arranged in such a way that if the access port is configured to work with a network that is not in the VLAN database, this port is programmatically disabled. The same thing happened with the VLAN20 and VLAN30 networks - the switches did not find them in the updated database of virtual networks and simply disabled the corresponding access ports, after which the existing local network of the company failed.

I assure you that this often happens in practice. Personally, I have twice witnessed an event when the network stopped working due to the fact that someone connected a new switch. So be careful, because VTP is a very powerful thing. Cisco believes that because of the potential for this type of problem, VTP is best avoided.
There is a mechanism to prevent network failure caused by a VTP usage error. This is the mechanism of VTP domains, working in this way: if the domain of one of the switches on the network differs from the domain of other switches running the VTP protocol, this switch will not be replicated in the VLAN database. However, despite this mechanism, Cisco does not recommend using this protocol without special need.
However, if you are sure that VTP will help you when creating a network and that you can responsibly approach the configuration of switches, you can try to use it. VTP has 3 modes: Server, Client and Transparent.
VTP Server mode allows you to make changes to the network, that is, create, delete and modify VLANs from the switch command line. By default, this mode is set in all Cisco switches.
I drew three switches, the first of them is in Server mode, and the other two are in Client mode. You can create a new VLAN only on the first switch, after which the database will be replicated on the second and third switch. If you try to do this with the second switch, you will get the answer: "I am not a server, so you cannot make such changes in my settings." This is the mechanism that prevents changes. Thus, you can select one of the switches by the server, make changes to its settings, and they will be repeated on the switches - clients. However, what if you do not intend to use VTP?
To completely abandon the use of this protocol, you need to put the switch in Transparent mode. At the same time, you do not disable VTP mode, just the switch no longer generates VTP advertisements, does not update the VLAN databases, and always uses configuration revision number 0.
Suppose we use Transparent mode for the second switch. Upon receipt of the VTP information, he will see that this protocol does not apply to him, and simply transfer this information to the next switch, which is in Client mode, without updating anything in his own settings. Thus, Transparent mode means refusing to use VTP with a specific switch.

So remember that Server mode allows you to make changes, Client mode allows you to receive these changes, and Transparent mode prevents the changes from being applied over the VTP protocol, transferring them further over the network.
Now let's talk about a concept called VTP Pruning. Assume that on switch SW1 there are two VLAN30 networks, a red VLAN20 network and two blue VLAN10 networks.

Switch SW2 does not have a port for VLAN30. However, by default, SW1 transmits tagged VLAN10,20 and 30 traffic over the trunk. As a network administrator, you know that the switch SW2 does not have VLAN30, however, you must ensure the correct transfer of any traffic. To do this, you use additional information for traffic originating from SW1 using VTP Pruning. You configure the first switch in such a way that it can only transmit traffic of VLAN10 and VLAN20 networks via a trunk, excluding the possibility of transmitting traffic of VLAN30 network via a trunk. This is what the VTP Pruning concept is all about. In the next video tutorial, we will look at how to make the settings that I talked about today.
So, we discussed three concepts: Native VLAN, VTP and VTP Pruning. I hope you understand everything from what you heard. If this is not the case, review the lesson as many times as you see fit, and feel free to ask me questions by email or in the comments on this video.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read aboutHow to build the infrastructure of the building. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

So, a trunk is a connection that we use to connect one switch with another switch. VLAN is a technology that is applicable only to switches, but any device that speaks the encapsulation language and is associated with a switch using the .1Q protocol understands everything about VLAN. Computers do not know anything about this technology.
In the figure above, PC1, PC2, and PC4 are part of the blue VLAN, as you remember from the previous lesson, this is VLAN10. The line itself, indicated in blue, has nothing to do with the VLAN, because the VLAN only touches the switch port. Thus, both ports of the left switch belong to VLAN10 and any incoming or outgoing traffic is associated only with this network. The switch knows that the traffic on these blue ports has nothing to do with the red port, because these are two different virtual lines.
VLAN is a concept for switches, so each switch supports the creation and storage of a database of virtual networks. This is a table that indicates which port corresponds to a specific VLAN. Thus, if the switch receives traffic for PC1, it checks whether this traffic is part of VLAN10 and forwards it to the computer. If the traffic from PC1 is for PC4, the switch will route it through the SW1-SW2 trunk. As soon as traffic enters the trunk port of the first switch, it supplies the frame with the VLAN TAG header, which contains the VLAN ID, in our case it is 10. After receiving this traffic, the second switch reads the frame information, sees that it is VLAN10 traffic, and routes it to the blue port for PC4.
Thus, trunking is the process of transferring traffic between two switches, and VLAN TAGS are frame headers that identify a specific virtual network and indicate which network this traffic should be directed to. If by mistake the blue traffic gets to the computer through the red line, he will not even know how to read it. It is as if someone is speaking a foreign language with a person who does not know this language. So, the computer is completely incapable of recognizing VLAN tags. The PC3 computer is connected to the switch through the access port, and the traffic we mentioned can be sent only through the trunk port.
All these are features of the 2nd level of the OSI model to which switches belong. In order to better understand the essence of VLAN and tags, we must think like a switch. Suppose a switch is a room with 5 people in it, and you are the owner of this room. Three people under numbers 1,2 and 4 belong to the same group, and two people under numbers 3 and 5 belong to the other, and your duty is to make sure that only people belonging to the same group can talk to each other.
We continue the discussion of the concept of native VLAN. As already mentioned, each switch port is associated with a specific VLAN.

For example, two ports of the first switch are connected to VLAN10, a third access port is with VLAN20, and the fourth is a trunk port. In the same way, SW2 is connected to PC4 through the VLAN10 port, to PC5 through the VLAN20 access port and to the hub through the trunk port. However, we have one problem - switches are expensive, so a scheme is often used in which two switches are connected to each other through a hub. Two switches are connected to the hub using trunks, but the hub itself does not know anything about the concept of VLAN, it simply copies the signal. As we already said, if VLAN traffic is sent directly to the computer, it will drop it, because it does not understand what it is. How do we deal with a PC6 computer that is directly connected to the hub if it is going to establish a connection with the PC4 computer?
PC6 sends traffic that goes to switch SW2. Having received this traffic, the switch sees that the frame does not have a VLAN tag and does not know which network to send it to - VLAN10 or VLAN20. For this case, Cisco has created a technology called Native VLAN, and by default VLAN1 is Native VLAN.
Suppose we have another computer, I will draw it over the switch SW2, and this PC is connected to the switch through the port VLAN1. The same computer is located above SW1 and is also connected to it via VLAN1. I will draw another computer under the right switch.

Two computers connected to switch SW2 via VLAN1 can communicate with each other, but are not able to communicate with other computers. When a switch receives untagged traffic through a trunk, it considers that this traffic is addressed to VLAN1, or Native VLAN, and forwards it to computers connected to VLAN1 ports. Similarly, when a switch receives untagged PC6 traffic, it addresses its VLAN1 network.
What happens if we have a Cisco IP phone on the red line of VLAN20 that is connected to PC5 and switch SW2? This is a typical layout of office networking equipment. In this case, the Native VLAN concept is also used. As I said, the computer does not know what VLAN is, and the phone knows. The question is whether we can send data and voice over the same VLAN. This is a very dangerous situation, because if the computer is on the same line of communication with the IP phone, the hacker can easily connect to such a communication channel and use Wireshark to intercept voice packets. Then he can convert these voice packets into an audio file and eavesdrop on any telephone conversation. Therefore, in practice, voice and data traffic are never transmitted over the same VLAN.
We turn the port to which the IP phone is connected into a trunk port, and we believe that any traffic passing through this port is VLAN30 voice traffic. Any Cisco IP phone uses the 802.1q encapsulation protocol, commonly referred to as .1Q or Dot 1Q. Thus, when the traffic from the phone falls into the corresponding port, the switch understands that this is VLAN30 voice traffic. We must have another phone that is connected to the SW switch, which is also part of VLAN30.
What happens in this case with a PC4 computer that is connected to the switch through the access port? After all, all the traffic that this computer exchanges with the switch belongs to the blue VLAN10. However, PC5 is connected to the switch via a trunk, and for the trunk we do not configure any VLAN! In this case, the port operates in trunk mode, not access mode, so we cannot use the switchport access VLAN # command. It uses the same concept as in the case of PC6 - if the switch receives untagged traffic, it routes it to the native VLAN port, by default it is VLAN1.
The question is whether native VLAN can be changed. The answer is yes, you can do this, for example, in the case of the red line, you can change the native VLAN to VLAN20, and then the switch will redirect the traffic from PC5 to the VLAN20 network. Since both switches are connected by trunk, the SW2 switch, having received the VLAN20 traffic, will consider it the native VLAN traffic and will send the SW1 switch as untagged.
Having received this traffic, switch SW1 recognizes it as untagged native traffic, and since its native VLAN is VLAN1, it will send this traffic to this network. If we change the native VLAN, we must do this with care to make sure that all the native VLANs in all switches have changed correctly, otherwise this can cause a lot of problems.
This was a brief overview of native VLAN, and now we will move on to the proprietary VTP Trunking Protocol (VLAN). First of all, you should remember that, despite its name, VTP is not a trunking protocol.

From previous lessons, we know that there are only 2 trunking protocols: the proprietary Cisco protocol called ISL and the generally accepted 802.1q protocol.
VTP is also Cisco’s proprietary protocol, but doesn’t do trunking in the sense of creating trunk connections. Suppose we created VLAN10 on the port of the first switch to which the computer is connected. Further we have trunk SW1-SW2 and trunk SW2-SW3. When trunk port SW1 receives computer traffic, it knows that it is VLAN10 traffic and forwards it to the second switch. However, the second switch does not know what VLAN10 is, because nothing except the trunk is connected to it, therefore, in order to receive this traffic and send it further, it creates VLAN10 on its ports. Switch 3 will do the same - after receiving traffic on the trunk, it will create VLAN10.
You can create two access ports on SW3, and both will be VLAN10. Suppose that on all 3 switches I want to create another network - VLAN20. This will only be possible after the ports for VLAN20 are created. The more devices, computers, and switches that are added to your network, the more difficult it becomes to create new VLANs, which is why Cisco automated this process by creating a VTP.
If we create a new VLAN, let's call it VLAN30, on one of the switches, then on all other switches connected by a trunk, the same VLAN30 network is automatically created.

The updated, updated VLAN database is simply sent out to all switches, after which you just have to create an access port for the computer. Without this protocol, you will have to manually reconfigure all switches. The disadvantage of VTP is that if you make changes to the VLAN database, it changes the revision number - the revision number. Usually, when you use a switch right out of the box, all settings have a zero revision number. When you add a new VLAN, such as tenth, database SW1 gets revision number # 1. In this case, the second switch says: “ok, you have revision 1, and I have revision 0, so I have to change my revision number to 1 and copy all the data from your VLAN table to my table.” The third switch does the same.
Suppose now 2 switches adds VLAN20 and changes the revision number to 2, then the first and third switches must do the same. Each time you change the revision number, the protocol checks who has this number higher and changes all other revision numbers to this number, while updating its VLAN table. Moreover, VTP unconditionally trusts the switch with the highest revision number.
Imagine this situation. A new employee comes to the company and discovers somewhere in the corner a switch that is used to train staff. He does not know anything about this, sees that this switch looks newer, and decides to connect it to a shared network. He configures this switch, connects it, for example, to the SW2 switch and creates a trunk. And as soon as it turns it on, your entire network drops! Everything stops working, because the connection between computers and switches completely disappears.

Why did this happen? The maximum revision number of the switch company is 50, because the company has only 5 VLANs - 10,20,30,40,50. The new switch was used for training, more networks were connected to it, a lot of changes were made to the settings, as a result of which its revision number increased to 100. At the same time, it has only one network at number 105 in the VLAN database.
After SW Training connected to SW2 via a trunk, the second switch saw that the beginner had a higher revision number, and decided to change his number to a higher one. At the same time, he copied to himself the VLAN table of the new switch, automatically deleting all of his existing VLAN10,20,30 networks ...., replacing them with one VLAN105, which had not existed in the existing network before. The first and third switches did the same, changing the revision number from 50 to 100 and deleting the old networks from the database, because they were not contained in the VLAN table of the SW Training switch.
Switch SW1 created access ports for the VLAN10 network, but after updating the revision, this network disappeared. The switches are arranged in such a way that if the access port is configured to work with a network that is not in the VLAN database, this port is programmatically disabled. The same thing happened with the VLAN20 and VLAN30 networks - the switches did not find them in the updated database of virtual networks and simply disabled the corresponding access ports, after which the existing local network of the company failed.

I assure you that this often happens in practice. Personally, I have twice witnessed an event when the network stopped working due to the fact that someone connected a new switch. So be careful, because VTP is a very powerful thing. Cisco believes that because of the potential for this type of problem, VTP is best avoided.
There is a mechanism to prevent network failure caused by a VTP usage error. This is the mechanism of VTP domains, working in this way: if the domain of one of the switches on the network differs from the domain of other switches running the VTP protocol, this switch will not be replicated in the VLAN database. However, despite this mechanism, Cisco does not recommend using this protocol without special need.
However, if you are sure that VTP will help you when creating a network and that you can responsibly approach the configuration of switches, you can try to use it. VTP has 3 modes: Server, Client and Transparent.
VTP Server mode allows you to make changes to the network, that is, create, delete and modify VLANs from the switch command line. By default, this mode is set in all Cisco switches.
I drew three switches, the first of them is in Server mode, and the other two are in Client mode. You can create a new VLAN only on the first switch, after which the database will be replicated on the second and third switch. If you try to do this with the second switch, you will get the answer: "I am not a server, so you cannot make such changes in my settings." This is the mechanism that prevents changes. Thus, you can select one of the switches by the server, make changes to its settings, and they will be repeated on the switches - clients. However, what if you do not intend to use VTP?
To completely abandon the use of this protocol, you need to put the switch in Transparent mode. At the same time, you do not disable VTP mode, just the switch no longer generates VTP advertisements, does not update the VLAN databases, and always uses configuration revision number 0.
Suppose we use Transparent mode for the second switch. Upon receipt of the VTP information, he will see that this protocol does not apply to him, and simply transfer this information to the next switch, which is in Client mode, without updating anything in his own settings. Thus, Transparent mode means refusing to use VTP with a specific switch.

So remember that Server mode allows you to make changes, Client mode allows you to receive these changes, and Transparent mode prevents the changes from being applied over the VTP protocol, transferring them further over the network.
Now let's talk about a concept called VTP Pruning. Assume that on switch SW1 there are two VLAN30 networks, a red VLAN20 network and two blue VLAN10 networks.

Switch SW2 does not have a port for VLAN30. However, by default, SW1 transmits tagged VLAN10,20 and 30 traffic over the trunk. As a network administrator, you know that the switch SW2 does not have VLAN30, however, you must ensure the correct transfer of any traffic. To do this, you use additional information for traffic originating from SW1 using VTP Pruning. You configure the first switch in such a way that it can only transmit traffic of VLAN10 and VLAN20 networks via a trunk, excluding the possibility of transmitting traffic of VLAN30 network via a trunk. This is what the VTP Pruning concept is all about. In the next video tutorial, we will look at how to make the settings that I talked about today.
So, we discussed three concepts: Native VLAN, VTP and VTP Pruning. I hope you understand everything from what you heard. If this is not the case, review the lesson as many times as you see fit, and feel free to ask me questions by email or in the comments on this video.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read aboutHow to build the infrastructure of the building. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
