EDR technology as an element of the SOC nuclear triad
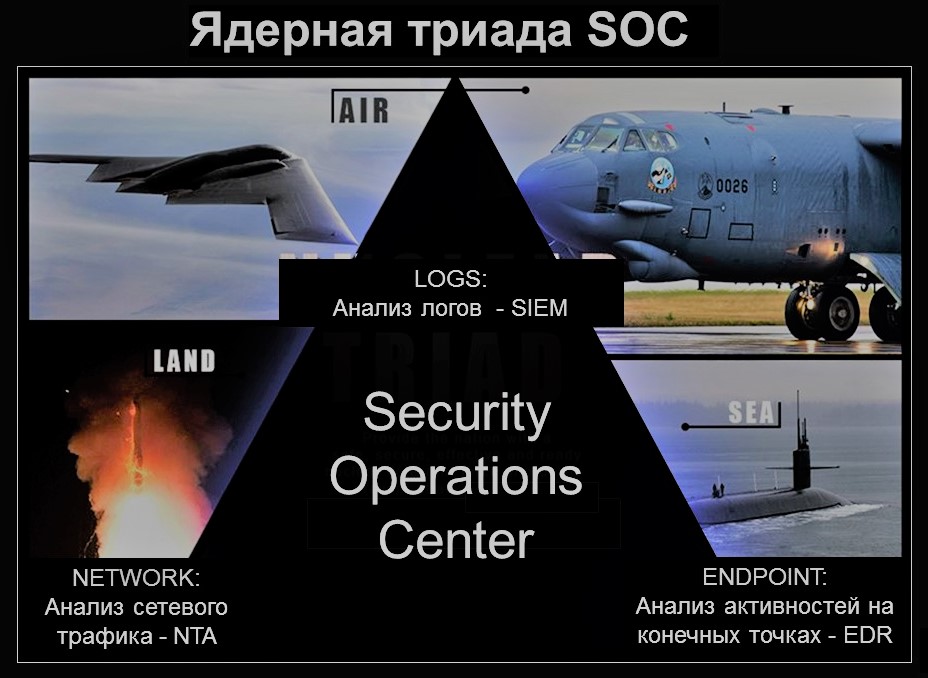
To begin with, recall what a nuclear triad is. This term refers to the strategic armed forces of a state equipped with nuclear weapons. The triad includes three components: air - strategic aviation, land - intercontinental ballistic missiles, sea - atomic submarine missile carriers.
Dear Gartner, made an analogy of the strategic armed forces of the state with the center for monitoring and operational response to incidents (SOC), highlighting the following elements of the SOC triad: Security information and event management (SIEM), Network Traffic Analysis (NTA), Endpoint Detection and Response (EDR). Looking at this analogy, it becomes obvious that SOC can be maximally effective only if it is equipped with all protection components: in the “air”, on the “land” and in the “sea”.
Unfortunately, today most organizations use only “strategic aviation” - SIEM systems. Rarely enough, “intercontinental ballistic missiles” - NTA, replacing the full analysis of network traffic only by collecting logs from standard network security tools. And it’s quite infrequent that “nuclear submarine missile carriers” - EDR.
In my today's article, according to Gartner's testament, I want to highlight the main reasons for the importance of including EDR technology as one of the elements of a modern center for monitoring and rapid response to incidents.
In the world of information security, EDR technology is much more than just advanced protection of workstations and servers from complex threats. From year to year, jobs remain the key goal of attackers and the most common entry points into the infrastructure of organizations, which requires due attention and appropriate protection. And telemetry is valuable information necessary for a high-quality incident investigation, the importance of access to which increases even more with the advent of the new TLS 1.3 encryption protocol and its active distribution.
EDR is rapidly becoming the driving force behind increasing the maturity and effectiveness of modern SOCs.
Let's see why?
Additional visibility
First of all, EDR technology is able to give the SOC team visibility where most organizations remain blind today, as most of them are focused on monitoring activities on the network. Such companies, within the framework of the functioning of the monitoring center and operational response to incidents, rarely or only partially connect endpoints as event sources in the SIEM system. This is due to the high cost of collecting and processing logs from all endpoints, and also because of the generation of a huge number of events for analysis with a sufficiently high level of false positives, which often leads to overloading of specialists and inefficient use of expensive resources in general.
A special tool for detecting complex threats on hosts
Complex threats and targeted attacks using unknown malicious code, compromised accounts, fileless methods, legitimate applications and actions that do not carry anything suspicious require a multi-level detection approach using advanced technologies. Depending on a particular vendor, EDR can usually include various detection technologies that work in automatic, semi-automatic mode, and built-in tools that require setting tasks manually, involving highly qualified personnel. For example, it can be: an antivirus, a behavioral analysis engine, a sandbox, a search for compromise indicators (IoC), work with IoA attack indicators, a comparison with MITER ATT & CK techniques, as well as automatic interaction with Threat Intelligence and manual queries to the global threat database, retrospective analysis, the ability to proactively search for threats (Threat Hunting). EDR is an additional tool for SOC analytics with an intuitive interface for real-time threat hunting, which allows you to make complex requests to search for suspicious activities, malicious actions, taking into account the features of the protected infrastructure.
All of the above allows organizations to detect complex threats aimed at bypassing traditional host protection tools, such as conventional antiviruses, NGAV, or EPP (Endpoint protection platform) class solutions. The latter today work very closely with EDR solutions and most manufacturers of this class of products provide EPP and EDR functionality within a single agent, without overloading the machine and at the same time providing an integrated approach to protecting endpoints from complex threats, from automatically blocking simpler ones threats, ending with the detection and response to more complex incidents. The advanced detection mechanisms used in EDR allow teams to quickly identify threats and respond quickly, preventing possible damage to the business.
Additional context
Data on host events with EDRs is a significant addition to the information generated by other security elements and business applications of the protected infrastructure, which are compared by the SIEM system in the center for monitoring and rapid response to incidents. EDR provides quick access to endpoint infrastructure data already enriched in additional context, which allows, on the one hand, to quickly identify false positives, and on the other hand, use this data as a precious pre-processed material in the investigation of complex attacks, that is, EDR provides relevant logs to correlate with events from other sources, thereby improving the quality of global investigations in the SOC.
Additional automation
For organizations that do not have EDR, the detection of complex threats on the infrastructure of endpoints, which includes: collecting, storing and analyzing data, as well as carrying out various actions at the stages of investigation and response to complex incidents, seems a rather laborious task without the use of automation tools.
Today, many analysts spend a lot of time on routine operations that are necessary and important, but can be automated. Automating these routine manual tasks will allow organizations not only to save the analyst’s expensive work time, but also to reduce their workload and allow them to focus on analyzing and responding to truly complex incidents. EDRs provide a fully automated incident management workflow, from threat detection to analysis and response. This allows the SOC team to perform daily tasks more efficiently without wasting time on manual work, thereby reducing the cost of analyzing unnecessary logs.
Quick access to data and their visual representation of information
Organizations may encounter some difficulties to obtain the data necessary for an investigation, such as the inability to quickly access workstations and servers with a distributed infrastructure or the inability to obtain contextual information from specific machines due to their destruction or encryption of data by attackers. This, of course, makes it impossible to obtain the necessary data for an effective investigation process and further response to incidents. When the incident has already occurred, the use of EDR technology, including continuous and centralized recording, eliminates guesswork and saves analyst time.
An attacker often destroys their tracks, but the EDR, as already mentioned, records every attacking action. The entire chain of events is recorded and securely stored for future use. When a warning of any kind is triggered, EDR provides a convenient tool with which SOC analysts can quickly request information to check for threats, eliminate false positives, and make requests to re-scan retrospective data to increase the effectiveness of the investigation and response.
All actions on the hosts are presented in the interface in the form of an event tree, thereby helping analysts to see the whole picture of the attack, as well as look for the information they need to investigate and take operational measures to prevent the threat.
The centralized storage of telemetry, objects and previously generated verdicts allows analysts to work with retrospective data as part of an investigation of threats, including attacks that are extended over time. EDR today is a source of valuable data for today's SOC.
Centralized response
When an incident is detected, EDR provides advanced options for taking action at different stages of its investigation: for example, quarantining a file, executing arbitrary commands on a host, deleting an object, network isolation of hosts, and other actions. EDR allows you to immediately respond to incidents through the visual presentation of information and centralized task setting, which does not require trips to the crime scene to find evidence and take response measures. EDR is a tool for optimizing the labor costs of SOC specialists. Organizations significantly reduce the number of routine manual operations, save the time of SOC analysts and reduce the response time from hours to minutes.
Conclusion
EDRs are an invaluable source of data for SOCs, providing powerful threat search capabilities and centralized incident response, while maximizing the automation of processes for collecting, analyzing and responding to detected threats.
Using EDR within the SOC will allow organizations to:
- to increase the efficiency of the processing of complex incidents due to the additional visibility of the endpoint level, the possibility of proactive search for threats and the visual presentation of information about detected events on hosts;
- enrich SOC with pre-processed relevant data from workstations and servers, for comparison with logs provided by other sources for effective investigation;
- significantly reduce the number of hours spent by analysts on tedious but necessary tasks associated with analyzing data from workstations and servers, as well as responding to incidents.
