How I became vulnerable: scanning IT infrastructure with Qualys
Hello!
Today I want to talk about the cloud solution for searching and analyzing vulnerabilities Qualys Vulnerability Management, on which one of our services is built .
Below I will show how the scanning itself is organized and what information on vulnerabilities can be found out by results.
External services. To scan services with Internet access, the client provides us with their IP addresses and credentials (if you need a scan with authentication). We scan services using the Qualys cloud and, as a result, send a report.

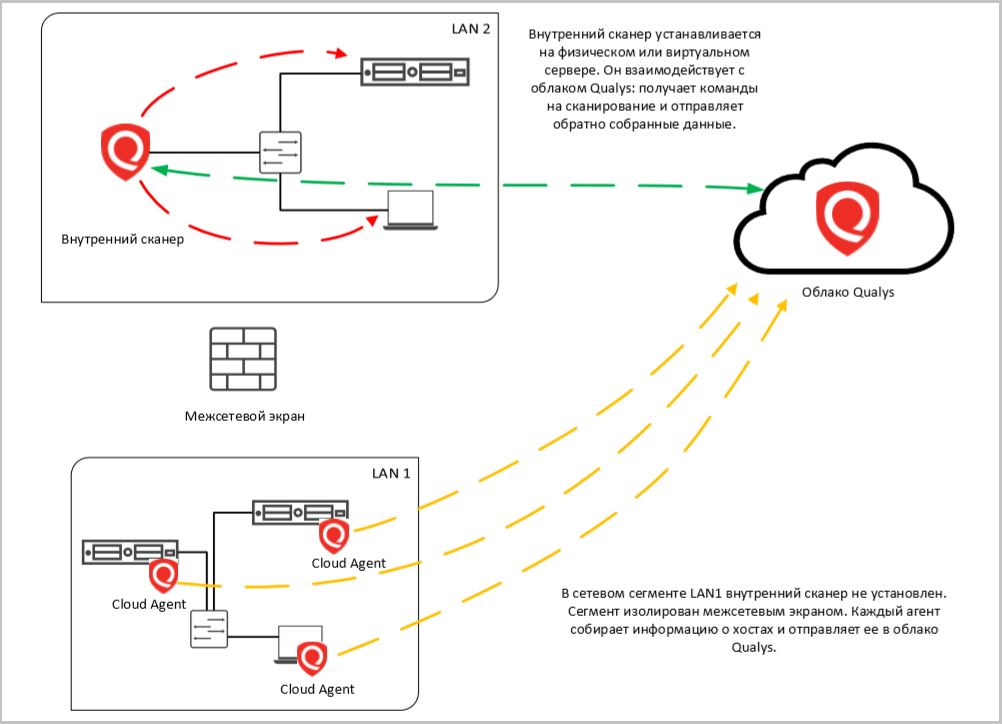
Internal Services In this case, the scanner looks for vulnerabilities on internal servers and network infrastructure. Using this scan, you can take an inventory of operating system versions, applications, open ports, and the services behind them.
To scan inside the client infrastructure, a Qualys scanner is installed. The Qualys cloud here serves as the command center for this scanner.
In addition to the backend server with Qualys, you can install Cloud Agents on scan objects. They collect information about the system locally, practically do not create a load on the network and on the hosts on which they work. The received information is sent to the cloud.
There are three important points: authentication and selection of objects for scanning.
Based on the results of the scan, the client receives a report in which there will be not only a list of all the vulnerabilities found, but also basic recommendations for their elimination: updates, patches, etc. Qualys has a lot of reports: there are default templates, and you can create your own. In order not to get confused in all the diversity, it is better to first decide for yourself on the following points:
If you have a task to show a brief but clear picture to the management, then you can create an Executive Report . All vulnerabilities will be laid out on shelves, severity levels, graphs and charts. For example, the top 10 most critical vulnerabilities or the most common vulnerabilities.


For the technician there is a Technical Report with all the details and details. The following reports can be generated:
Host report . A useful thing when you need to take an inventory of the infrastructure and get a complete picture of the vulnerabilities of hosts.
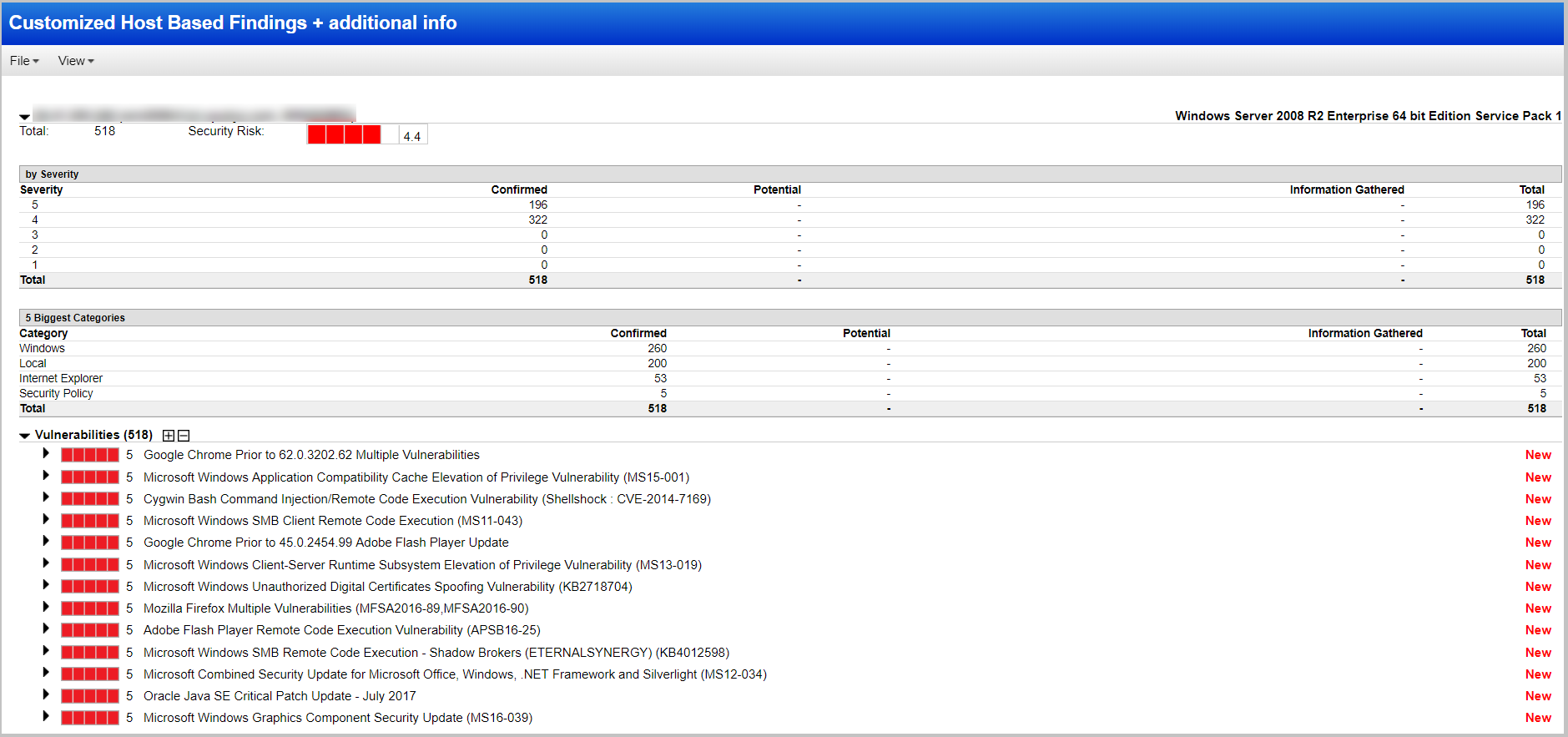
Here is a list of analyzed hosts with an indication of the operating systems running on them.

Let's open the host of interest and see a list of 219 vulnerabilities found, starting from the most critical, fifth level:

Next, you can see the details for each vulnerability. Here we see:

If this is not the first scan - yes, you need to scan it regularly :) - then using Trend Report you can track the dynamics of working with vulnerabilities. The status of vulnerabilities will be shown in comparison with the previous scan: vulnerabilities that were found earlier and closed will be marked as fixed, open - active, new - new.
Vulnerability Report. In this report, Qualys will build a list of vulnerabilities, starting with the most critical, indicating on which host to catch this vulnerability. The report is useful if you decide to deal with the moment, for example, with all vulnerabilities of the fifth level.
You can also make a separate report only on vulnerabilities of the fourth and fifth levels.

Patch Report.Here is a complete list of patches that need to be installed in order to eliminate the vulnerabilities found. For each patch, there are explanations of what vulnerabilities it treats, on which host / system you need to install, and a direct download link.


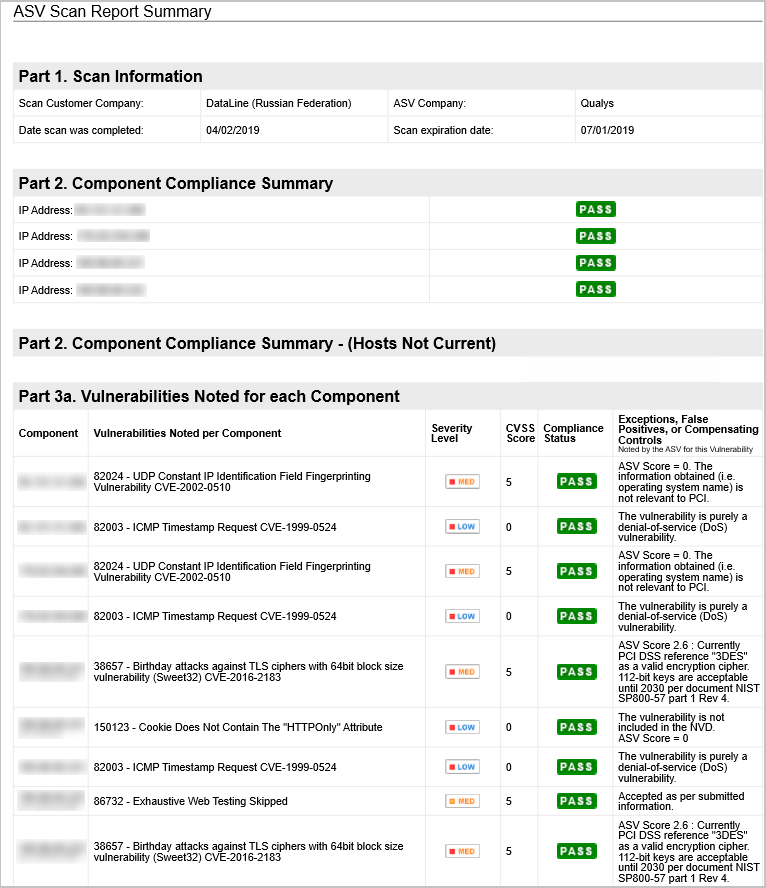
PCI DSS Compliance Report . The PCI DSS standard requires scanning information systems and applications accessible from the Internet every 90 days. After the scan, you can generate a report that shows that the infrastructure does not meet the requirements of the standard.

Vulnerability Fix Reports . Qualys can be integrated with the service desk, and then all the vulnerabilities found will be automatically translated into tickets. With the help of this report, it will just be possible to track the progress of completed tickets and fixed vulnerabilities.
Open Port Reports . Here you can get information on open ports and the services running on them:

or generate a vulnerability report on each port:

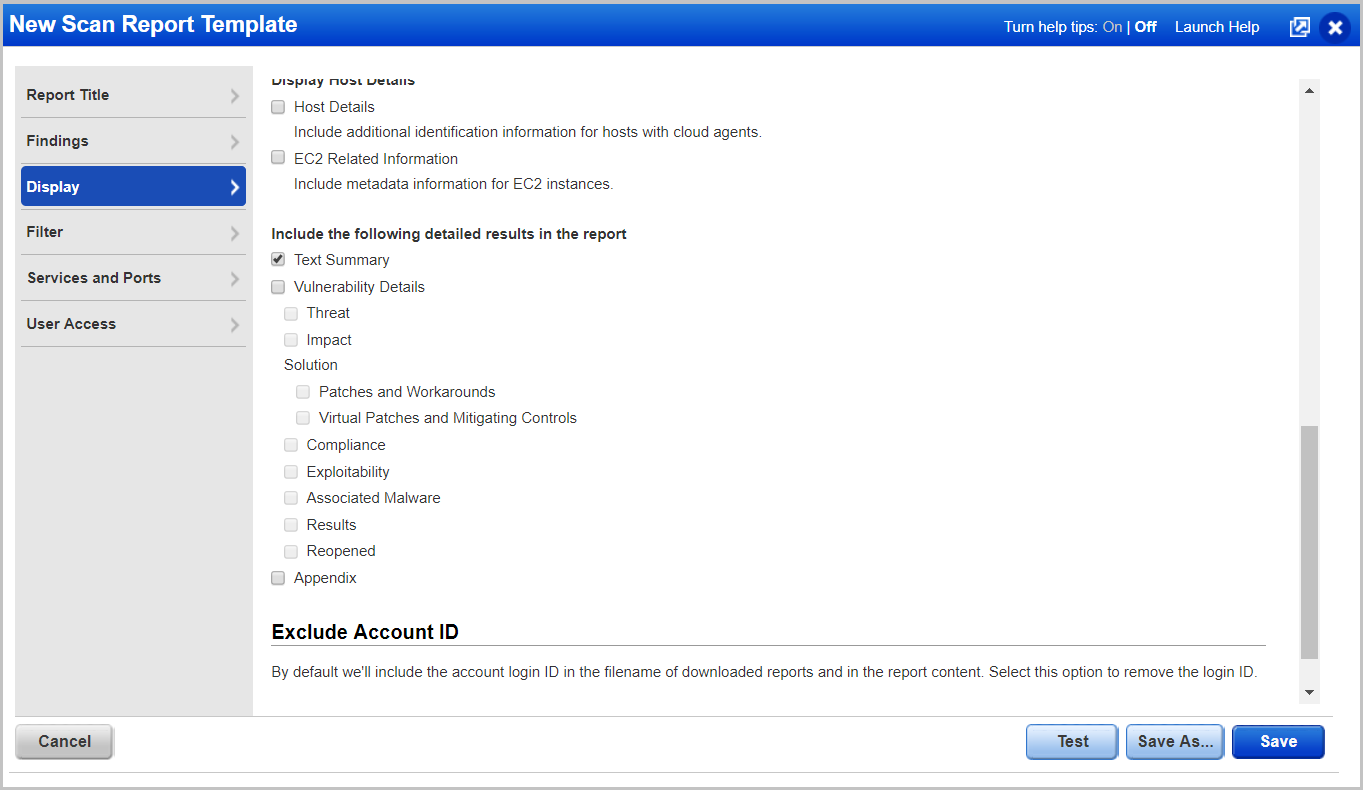
These are just standard report templates. You can create your own for specific tasks, for example, show only vulnerabilities not lower than the fifth level of criticality. All reports are available. Report format: CSV, XML, HTML, PDF and docx.
And remember: security is not a result, but a process. A single scan helps to see the problems in the moment, but this is not a complete process for managing vulnerabilities.
To make it easier for you to decide on this regular work, we have made a service based on Qualys Vulnerability Management.
For all readers of Habr the action is valid:when ordering a scanning service for a year, two months of scans are free. Applications can be left here , in the "Comment" field write Habr.
Today I want to talk about the cloud solution for searching and analyzing vulnerabilities Qualys Vulnerability Management, on which one of our services is built .
Below I will show how the scanning itself is organized and what information on vulnerabilities can be found out by results.

What can be scanned
External services. To scan services with Internet access, the client provides us with their IP addresses and credentials (if you need a scan with authentication). We scan services using the Qualys cloud and, as a result, send a report.

Internal Services In this case, the scanner looks for vulnerabilities on internal servers and network infrastructure. Using this scan, you can take an inventory of operating system versions, applications, open ports, and the services behind them.
To scan inside the client infrastructure, a Qualys scanner is installed. The Qualys cloud here serves as the command center for this scanner.
In addition to the backend server with Qualys, you can install Cloud Agents on scan objects. They collect information about the system locally, practically do not create a load on the network and on the hosts on which they work. The received information is sent to the cloud.

There are three important points: authentication and selection of objects for scanning.
- The use of authentication . Some customers ask for a blackbox scan, especially for external services: they give us a range of IP addresses without specifying a system and say "be like a hacker." But hackers rarely act blindly. When it comes to attack (not intelligence), they know they are hacking.
Blindly, Qualys might stumble upon blended banners and scan them instead of the target system. And without understanding what exactly will be scanned, it is easy to miss the scanner settings and “attach” the service being checked.
Scanning will be more useful if you perform authentication checks before the scanned systems (whitebox). So the scanner will understand where it came from, and you will receive complete data about the vulnerabilities of the target system.
Qualys has many authentication options. - Group assets . If you start scanning everything at once and indiscriminately, it will be long and will create an extra load on the system. It is better to group hosts and services into groups according to importance, location, OS version, critical infrastructure and other features (in Qualys they are called Asset Groups and Asset Tags) and select a specific group when scanning.
- Select a technical window for scanning. Even if you have all planned and prepared, scanning creates an additional load on the system. It does not necessarily cause the degradation of the service, but it is better to choose a certain time for it, as for backup or rollback updates.
What can be learned from the reports?
Based on the results of the scan, the client receives a report in which there will be not only a list of all the vulnerabilities found, but also basic recommendations for their elimination: updates, patches, etc. Qualys has a lot of reports: there are default templates, and you can create your own. In order not to get confused in all the diversity, it is better to first decide for yourself on the following points:
- Who will watch this report: manager or technical specialist?
- what information do you want to receive according to the results of the scan. For example, if you want to find out if all the necessary patches are installed and how the work is being done to eliminate previously found vulnerabilities, then this is one report. If you just need to take an inventory of all the hosts, then another.
If you have a task to show a brief but clear picture to the management, then you can create an Executive Report . All vulnerabilities will be laid out on shelves, severity levels, graphs and charts. For example, the top 10 most critical vulnerabilities or the most common vulnerabilities.


For the technician there is a Technical Report with all the details and details. The following reports can be generated:
Host report . A useful thing when you need to take an inventory of the infrastructure and get a complete picture of the vulnerabilities of hosts.
Here is a list of analyzed hosts with an indication of the operating systems running on them.

Let's open the host of interest and see a list of 219 vulnerabilities found, starting from the most critical, fifth level:

Next, you can see the details for each vulnerability. Here we see:
- when the vulnerability was fixed for the first and last time,
- Vulnerability numbers
- patch to fix the vulnerability
- Are there any problems with compliance with the PCI DSS, NIST standard, etc.,
- is there an exploit and malware for this vulnerability
- Is a vulnerability detected when scanning with / without authentication in the system, etc.

If this is not the first scan - yes, you need to scan it regularly :) - then using Trend Report you can track the dynamics of working with vulnerabilities. The status of vulnerabilities will be shown in comparison with the previous scan: vulnerabilities that were found earlier and closed will be marked as fixed, open - active, new - new.
Vulnerability Report. In this report, Qualys will build a list of vulnerabilities, starting with the most critical, indicating on which host to catch this vulnerability. The report is useful if you decide to deal with the moment, for example, with all vulnerabilities of the fifth level.
You can also make a separate report only on vulnerabilities of the fourth and fifth levels.

Patch Report.Here is a complete list of patches that need to be installed in order to eliminate the vulnerabilities found. For each patch, there are explanations of what vulnerabilities it treats, on which host / system you need to install, and a direct download link.


PCI DSS Compliance Report . The PCI DSS standard requires scanning information systems and applications accessible from the Internet every 90 days. After the scan, you can generate a report that shows that the infrastructure does not meet the requirements of the standard.


Vulnerability Fix Reports . Qualys can be integrated with the service desk, and then all the vulnerabilities found will be automatically translated into tickets. With the help of this report, it will just be possible to track the progress of completed tickets and fixed vulnerabilities.
Open Port Reports . Here you can get information on open ports and the services running on them:

or generate a vulnerability report on each port:

These are just standard report templates. You can create your own for specific tasks, for example, show only vulnerabilities not lower than the fifth level of criticality. All reports are available. Report format: CSV, XML, HTML, PDF and docx.

And remember: security is not a result, but a process. A single scan helps to see the problems in the moment, but this is not a complete process for managing vulnerabilities.
To make it easier for you to decide on this regular work, we have made a service based on Qualys Vulnerability Management.
For all readers of Habr the action is valid:when ordering a scanning service for a year, two months of scans are free. Applications can be left here , in the "Comment" field write Habr.
