Experiment: we use proxies as a tool to combat DoS attacks

Image: Pexels
DoS attacks are one of the large-scale threats to information security on the modern Internet. There are dozens of botnets that cybercriminals rent out to carry out such attacks.
Scientists from the University of San Diego conducted a study on how the use of proxies helps to reduce the negative effect of DoS attacks - we present to your attention the main points of this work.
Introduction: proxy as a tool to combat DoS
Such experiments are periodically carried out by researchers from different countries, but their common problem is the lack of resources for modeling attacks that are close to reality. Tests at small stands do not allow answering questions about how successfully proxies will counteract attacks in complex networks, which parameters play a key role in the ability to minimize damage, etc.
For the experiment, scientists created a model of a typical web application - for example, an e-commerce service. It works using a cluster of servers, users are distributed across different geographical locations and use to access the Internet service. In this model, the Internet serves as a means of communication between the service and users - this is how web services work from search engines to online banking tools.
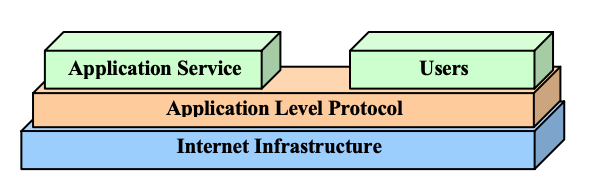
DoS attacks make normal interaction between the service and users impossible. There are two types of DoS: attacks at the application level and at the infrastructure level. In the latter case, the attackers directly attack the network and the hosts on which the service is running (for example, they flood the entire network bandwidth with flood traffic). In the event of an attack at the application level, the goal of the attacker is the user interaction interface - for this they send a huge number of requests in order to achieve the application crash. The described experiment concerned attacks at the infrastructure level.
Proxies are one of the tools to minimize the damage from DoS attacks. In the case of using a proxy, all requests from the user to the service and the answers to them are transmitted not directly, but through intermediate servers. Both the user and the application do not “see” each other directly; only proxy addresses are available to them. As a result, attacking the application directly is impossible. On the edge of the network are the so-called edge proxies - external proxies with available IP addresses, the connection goes first to them.
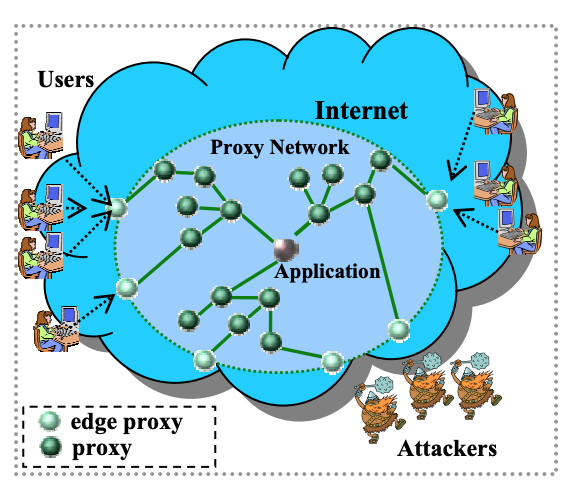
In order to successfully resist a DoS attack, a proxy network must have two key capabilities. Firstly, such an intermediate network should play the role of an intermediary, that is, you can only “get through” to the application through it. This will eliminate the possibility of a direct attack on the service. Secondly, the proxy network should be able to provide users with the opportunity to continue to interact with the application, even during the attack.
Experiment Infrastructure
The study used four key components:
- implementation of a proxy network;
- Apache web server
- tool for web testing Siege ;
- tool to attack Trinoo .
The simulation was carried out in a MicroGrid environment - it can be used to simulate networks with 20 thousand routers, which is comparable to the networks of Tier-1 operators.
A typical Trinoo network consists of a set of compromised hosts running the program daemon. There is also monitoring software to control the network and the direction of DoS attacks. After receiving a list of IP addresses, the Trinoo daemon sends UDP packets to the targets at a given time.
During the experiment, two clusters were used. The MicroGrid simulator worked in a 16-node Xeon Linux cluster (2.4GHz servers with 1 gigabyte of memory on each machine) connected through a 1 Gbps Ethernet hub. Other software components were located in a cluster of 24 nodes (450MHz PII Linux-cthdths with 1 GB of memory on each machine), united by a 100Mbps Ethernet hub. Two clusters were connected by a 1Gbps channel.
The proxy network is located in a pool of 1000 hosts. Edge proxies are evenly distributed throughout the resource pool. Proxies for working with the application are located on hosts that are closer to its infrastructure. The remaining proxies are evenly distributed between the boundary proxies and proxies for the application.
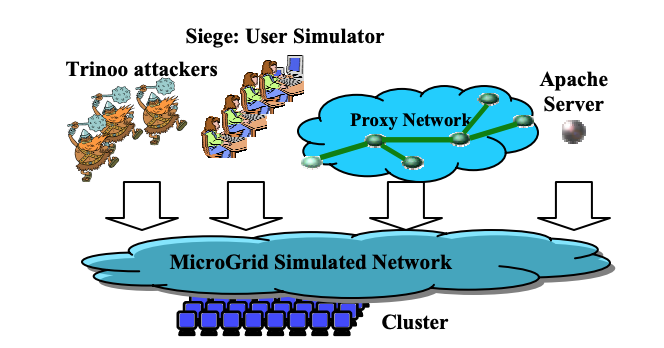
Simulation Network
To study the effectiveness of proxies as a tool to counter DoS attacks, researchers measured the productivity of the application under different scenarios of external influences. There were 192 proxies in the proxy network (64 of them were border proxies). To conduct the attack, a Trinoo network was created, including 100 demons. Each of the daemons had a 100Mbps channel. This corresponds to a botnet of 10 thousand home routers.
The effect of the DoS attack on the application and proxy network was measured. In the experimental configuration, the application had an Internet channel of 250Mbps, and each border proxy had 100 Mbps.
Experiment Results
According to the analysis, it turned out that the attack at 250Mbps significantly increases the response time of the application (about ten times), as a result of which it becomes impossible to use it. However, when using a proxy network, the attack does not significantly affect the performance and does not impair the user experience. This is because border proxies blur the effect of the attack, and the total amount of proxy network resources is higher than that of the application itself.
According to statistics, if the attack power does not exceed 6.0Gbps (despite the fact that the total bandwidth of the channels of the border proxies is only 6.4Gbps), then 95% of users do not experience a noticeable decrease in performance. Moreover, in the case of a very powerful attack exceeding 6.4Gbps, even the use of a proxy network would not allow degradation of the level of service for end users.
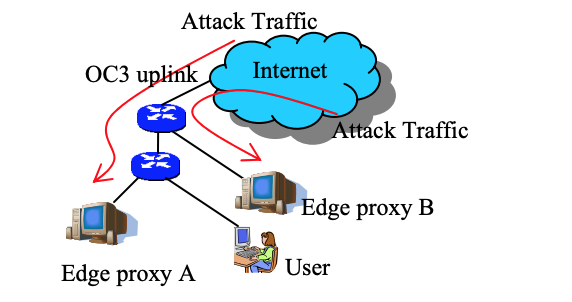
In the case of concentrated attacks, when their power is concentrated on a random set of border proxies. In this case, the attack clogs part of the proxy network, so a significant part of users will notice a drop in performance.
conclusions
The experimental results suggest that proxy networks can improve the performance of TCP applications and provide the usual level of service for users, even in the case of DoS attacks. According to the data obtained, proxy networks are an effective way to minimize the consequences of attacks, more than 90% of users during the experiment did not feel a decrease in the quality of the service. In addition, the researchers found that with an increase in the size of the proxy network, the scale of the DoS attacks that it is capable of carrying out increases almost linearly. Therefore, the larger the network, the more efficient it will be against DoS.
Useful links and materials from Infatica :
- Research: creating a blocking proxy service using game theory
- The history of the fight against censorship: how the flash proxy method created by scientists from MIT and Stanford works
- How to understand when proxies are lying: verification of physical locations of network proxies using the active geolocation algorithm
- How to disguise yourself on the Internet: compare server and resident proxies
