Linux Kernel Security Card
Linux kernel protection is a very complex subject area. It includes a large number of complexly interrelated concepts, and it would be useful to have its graphic representation. Therefore, I developed a Linux kernel protector map . Here is the legend:
So, the map contains the following objects:
In turn, core protection technologies are heterogeneous. Some are part of the Linux vanilla kernel, others are shipped separately for various reasons (for example, there are commercial security features). There are kernel protection mechanisms that require hardware support.
Thus, the Linux kernel security topic is quite extensive, and the developed map helps in its study and analysis. Each line connecting the objects on the map indicates their mutual influence, the essence of which should be clarified in the documentation. This principle can be illustrated on a fragment of the general map. Figure 1 shows the security features of STACKLEAK technology.
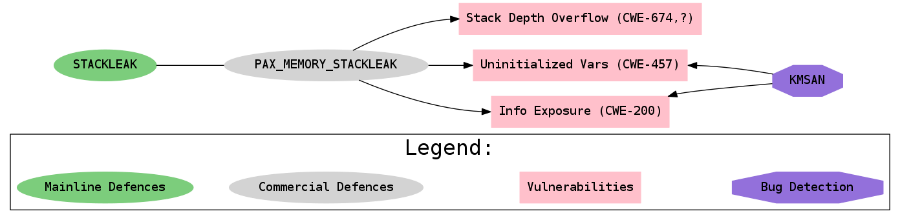
Diagram 1. Security features of STACKLEAK technology
PAX_MEMORY_STACKLEAK is a commercial Linux kernel protection technology that counteracts the exploitation of the following types of vulnerabilities: stack overflow in depth, use of uninitialized variables, and information leakage into user space. The map contains identifiers for these vulnerability classes (CWE, Common Weakness Enumeration). STACKLEAK
technology was introduced into the Linux vanilla kernel, which is reflected in the diagram. There is also a KMSAN debugging mechanism that allows you to detect when testing the kernel the use of uninitialized variables and information leakage into user space.
It is worth noting that this card does not address the issue of reducing the attack perimeter for the core. In fact, disabling almost any functionality that reduces the size of the executable also reduces the attack perimeter. And in this project, the main focus is on security tools that provide self-defense of the Linux kernel against exploitation of vulnerabilities.
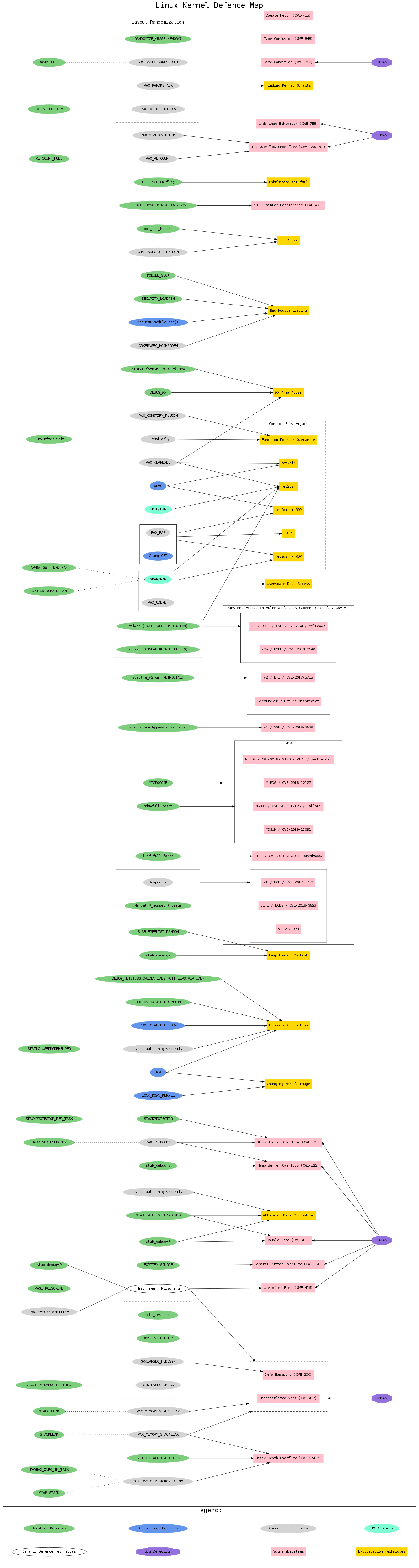
Figure 2 shows the full map for the kernel version 5.1 (by clicking on the image the full size will open). Diagram 2. Linux v5.1 kernel security features map
The map is constantly evolving, it needs to be updated at least every kernel release. Therefore, it is convenient to have the source in text form and maintain it in the version control system. In addition, in order to not have to manually arrange objects with a minimum number of intersections of connections, the DOT language was chosen to create the map, and the scheme is automatically generated by the GraphViz package using the following command:
The Linux Kernel Security Card is an open source project licensed under the GPL v3.0. The repository is located on GitHub . This project is extremely useful for:
In addition, the Linux kernel security features map is designed to help you learn about source code, documentation, and other sources of information on this topic:
And to automate the verification of security options in the Linux kernel configuration file, I created the kconfig-hardened-check project , which is actively developing thanks to open collaborative work. The utility supports x86_64, arm64, x86_32 and arm architectures.
I invite you to participate in the development of the Linux kernel security features map and the kconfig-hardened-check utility .

So, the map contains the following objects:
- Vulnerability classes
- techniques for their operation for conducting attacks;
- error detection mechanisms;
- protection technology.
In turn, core protection technologies are heterogeneous. Some are part of the Linux vanilla kernel, others are shipped separately for various reasons (for example, there are commercial security features). There are kernel protection mechanisms that require hardware support.
Thus, the Linux kernel security topic is quite extensive, and the developed map helps in its study and analysis. Each line connecting the objects on the map indicates their mutual influence, the essence of which should be clarified in the documentation. This principle can be illustrated on a fragment of the general map. Figure 1 shows the security features of STACKLEAK technology.

Diagram 1. Security features of STACKLEAK technology
PAX_MEMORY_STACKLEAK is a commercial Linux kernel protection technology that counteracts the exploitation of the following types of vulnerabilities: stack overflow in depth, use of uninitialized variables, and information leakage into user space. The map contains identifiers for these vulnerability classes (CWE, Common Weakness Enumeration). STACKLEAK
technology was introduced into the Linux vanilla kernel, which is reflected in the diagram. There is also a KMSAN debugging mechanism that allows you to detect when testing the kernel the use of uninitialized variables and information leakage into user space.
It is worth noting that this card does not address the issue of reducing the attack perimeter for the core. In fact, disabling almost any functionality that reduces the size of the executable also reduces the attack perimeter. And in this project, the main focus is on security tools that provide self-defense of the Linux kernel against exploitation of vulnerabilities.
Figure 2 shows the full map for the kernel version 5.1 (by clicking on the image the full size will open). Diagram 2. Linux v5.1 kernel security features map

The map is constantly evolving, it needs to be updated at least every kernel release. Therefore, it is convenient to have the source in text form and maintain it in the version control system. In addition, in order to not have to manually arrange objects with a minimum number of intersections of connections, the DOT language was chosen to create the map, and the scheme is automatically generated by the GraphViz package using the following command:
dot -Tsvg linux-kernel-defence-map.dot -o linux-kernel-defence-map.svgThe Linux Kernel Security Card is an open source project licensed under the GPL v3.0. The repository is located on GitHub . This project is extremely useful for:
- monitoring the current state of kernel security,
- developing threat models of IP based on GNU / Linux,
- selection of appropriate remedies.
In addition, the Linux kernel security features map is designed to help you learn about source code, documentation, and other sources of information on this topic:
- Grsecurity security properties
- Linux kernel security documentation
- Kernel Self Protection Project Documentation
- The current status of migrating grsecurity features to the Android Open Source Project
- Overview of OS Security Trends from Microsoft Research Center (MSRC)
- Linux Kernel Runtime Guard Threat Model (LKRG)
And to automate the verification of security options in the Linux kernel configuration file, I created the kconfig-hardened-check project , which is actively developing thanks to open collaborative work. The utility supports x86_64, arm64, x86_32 and arm architectures.
I invite you to participate in the development of the Linux kernel security features map and the kconfig-hardened-check utility .
