Follow the money: how the RTM group began to hide the addresses of C & C servers in a crypto wallet
The cybercriminal group RTM has been stealing money from bank customers since 2015. Most of its victims are Russian companies. Malicious software used by cybercriminals is also commonly referred to as RTM in the information security community.
Quite a lot of technical reports have been written about this program, which describe in detail the general mechanism of the malware. In this article, we will focus on methods for obtaining the addresses of the managing (C&C) RTM servers. In each iteration of the program, attackers inventively approach this task: they distribute the address through blogs, use the system of alternative DNS servers and the Tor network. The other day, we found that RTM began to hide IP in transactions on a bitcoin wallet.
What is RTM?
At its core, RTM is a banking trojan. The main objective of the program is to allow attackers to manipulate payment orders of the victim company in order to quietly transfer its funds to the account of cybercriminals.
Typically, RTM is delivered to the victim’s computer via mailing lists, more rarely through hacked sites (such as news publications) or fake resources for accountants. Criminals attach a packed executable file to letters. As a means of packaging, attackers use both their own development and self-extracting archives. 
Examples of .exe executable files distributed by the RTM group
The sample files in the figure are arranged in order of distribution. Most of the time, RTM executables were packed with a custom packer and disguised as a PDF document. At the beginning of 2019, the first samples began to appear, which are a self-extracting RAR archive and are disguised as a file in the DOCX format. RTM is currently distributed as a self-extracting CAB archive. Binary representation of the “Payment 11.06.exe” file.
Once launched, the executable file copies the packed DLL to the disk and launches it using the rundll32.exe utility. As a rule, the internal name of this library is core.dll. Its subsequent operation occurs in the address space of the rundll32.exe process.
It is core.dll that provides the primary interaction with the RTM control server, through which the program receives commands and additional modules from the attackers.
The modules are delivered in encrypted form and can be launched in various ways. These components give attackers the ability to remotely control a compromised computer, substitute payment documents in the 1C system, etc.
Ways to find a management server
RSS feed
In the first versions of RTM, an RSS feed was used to update the addresses of control servers. Attackers created a blog in LiveJournal containing C&C addresses in encrypted form. To obtain new addresses of control servers, a request was sent to the address hxxps: //.livejournal [.] Com / data / rss / and the response was processed in the following format (for example, https://f72bba81c921.livejournal.com/data/rss/ ) : RSS feed content. The description field contains encrypted addresses of the management servers. Decrypted lines with the initial address of the management server and the address of the RSS feed

.bit
In March 2016, RTM began to use domains in the .bit zone as the addresses of control servers. They are supported by an alternative Namecoin DNS registrar based on blockchain technology. The system is decentralized, so .bit domains are difficult to block.
The IP addresses of the management servers on .bit RTM were obtained in one of two ways:
- through the Namecoin Block Browser API;
- through domain name resolution using special DNS servers.
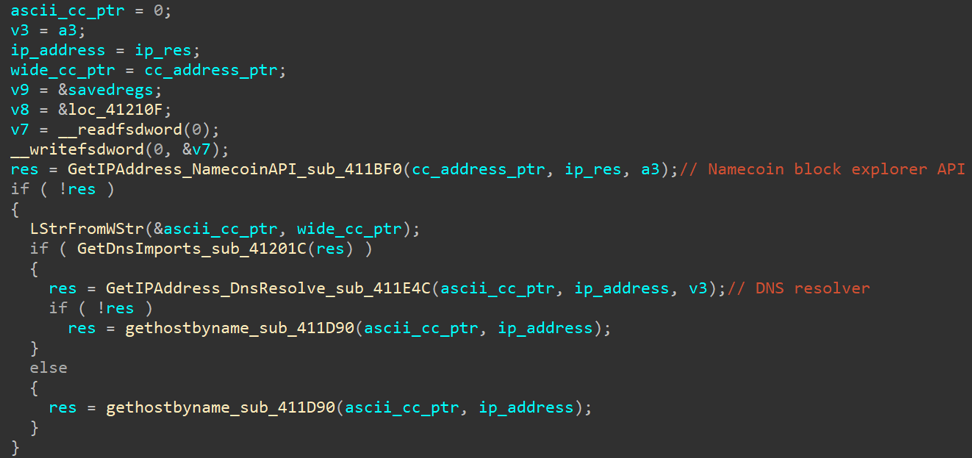
Function for obtaining IP addresses of control servers
In the function for obtaining IP addresses of control servers through the Namecoin block browser API, the content is processed at the address hxxps: //namecoin.cyphrs [.] Com / api / name_show / d / stat-counter-7 (using the domain stat-counter-7 [.] bit as an example): The function of obtaining IP addresses of control servers via the Namecoin block browser API The
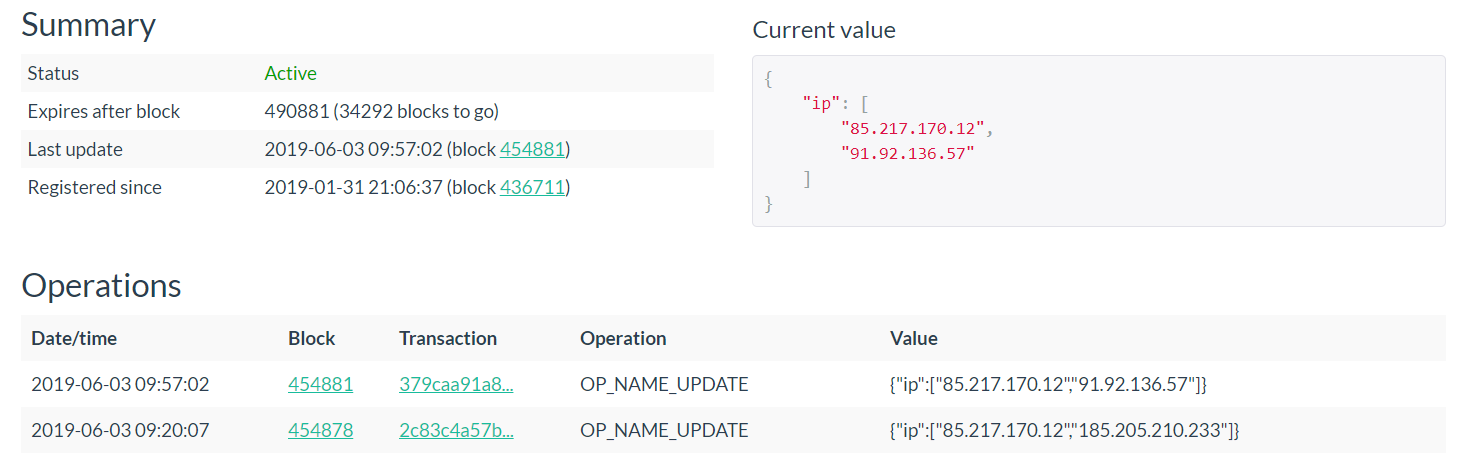
IP addresses of the control server are obtained from the response body. In addition to requests to hxxps: //namecoin.cyphrs [.] Com / api / name_show / d /, attackers also used requests to hxxps: // namecha [.] In / name / d /, processing the “Current value” field: Web content pages at the URL hxxps: // namecha [.] in / name / d / stat-counter-7
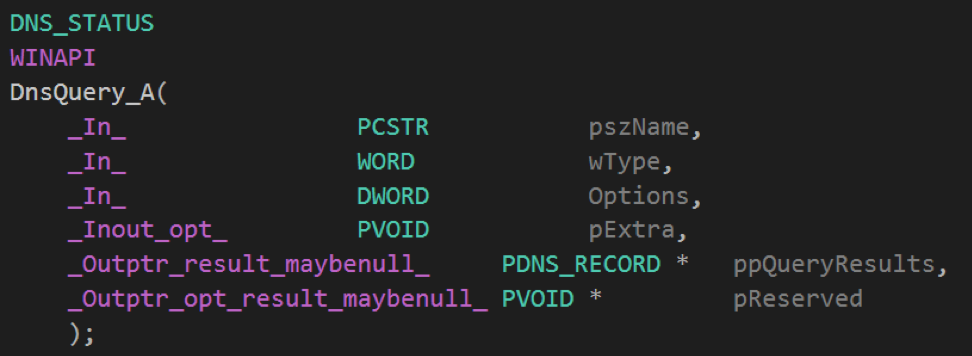
If it was not possible to obtain an IP address in this way, the attackers resolve the domain name of the control server with the DnsQuery_A function using special DNS servers (taken, for example, from here ).
The use of the DnsQuery_A function in the core.dll library program code looks like this: The function of obtaining IP addresses of control servers via domain name resolution using special DNS servers
The DnsQuery_A function has the following prototype: The prototype of the DnsQuery_A function, declared in the WinDNS.h header file
4 the argument to the DnsQuery_A function passes the address of the _IP4_ARRAY structure on the stack. It contains an array of IP addresses of special DNS servers: Structure _IP4_ARRAY on the stack
. If the DnsQuery_A function succeeds, the IP address of the managing server can be obtained by reading the following value: pDnsRecord -> Data.A.IpAddress.
It can be seen from the decompiled code of one of the instances that a special DNS server 188.165 [.] 200.156 is used to resolve the C&C domain name. And in case of failure, a list of three DNS servers is used: 91.217 [.] 137.37, 188.165 [.] 200.156, 217.12 [.] 210.54.
Tor
On February 15, 2019, we first discovered RTM samples whose management server is located on the Tor network (hxxp: // [.] Onion / index [.] Php). The address of the management server on the Tor network among the decrypted strings The portion of the disassembled code in which the URLs of the management server are parsed.
These samples were sent until April 9, 2019, after which RTM switched to using the .bit domain zone again.
Bitcoin
On June 10, 2019, we discovered an RTM sample that receives the IP addresses of C & C servers from transactions on a specific crypto wallet. Each IP address is hidden in the number of listed bitcoins in two transactions.
To obtain IP addresses, C&C VPO makes a request at hxxps: // chain [.] So / api / v2 / get_tx_received / BTC /. The response contains a set of transactions to the crypto wallet account. The example is shown in the screenshot:
Consider the section of code in which the IP addresses of the control server are
obtained : In the FindValue function, the fractional part of the transfer amount is searched. The search is carried out from the end of the buffer, and with each subsequent function call, data is processed, starting from the current index. That is, with successive calls to the FindValue function, the values 8483, 40030, 14728 and so on will be obtained. The program generates two IP addresses: each address is hidden in two consecutive translations. Disassembled code for obtaining an IP address from transfers to a crypto wallet
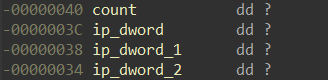
This code does the following: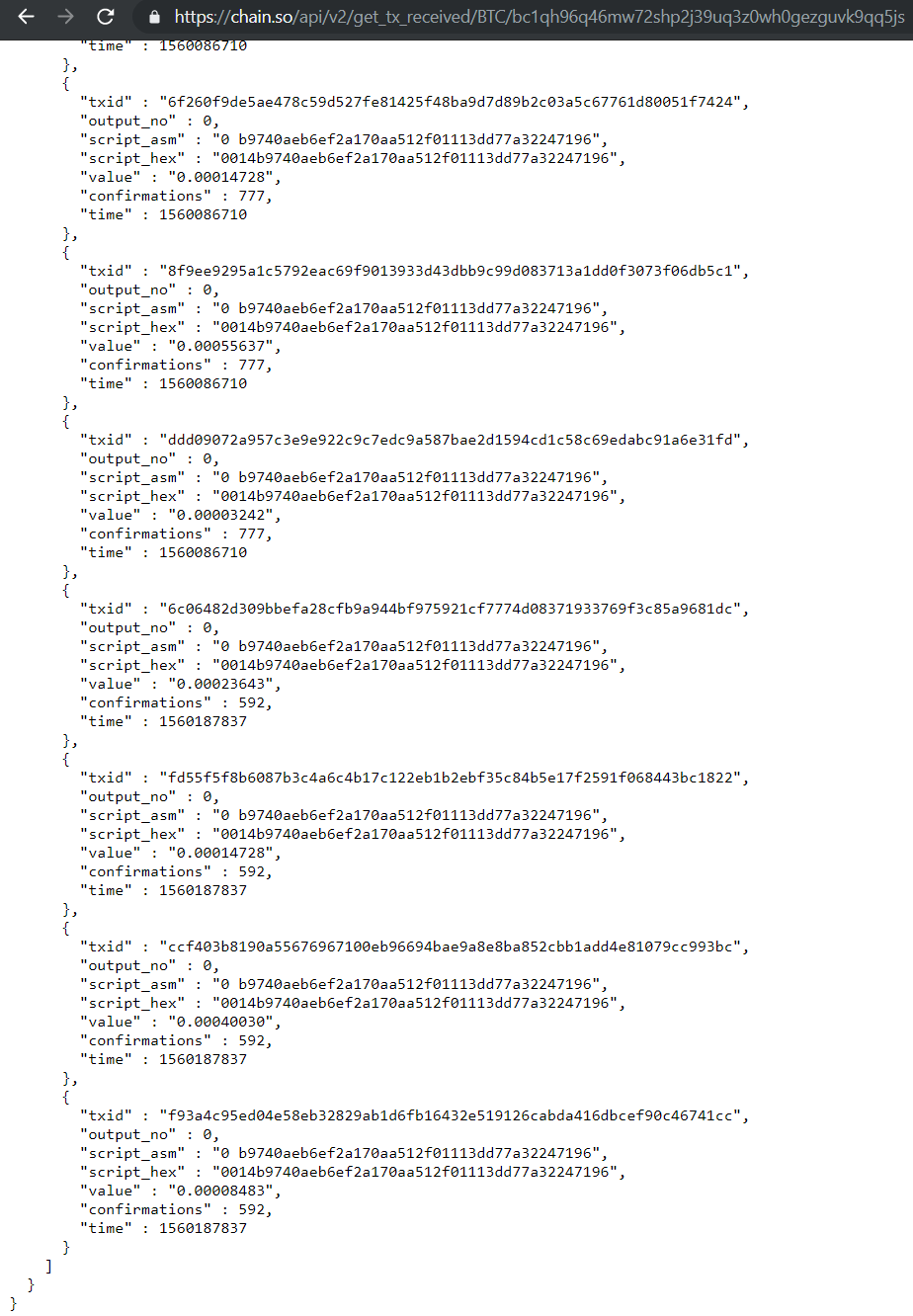
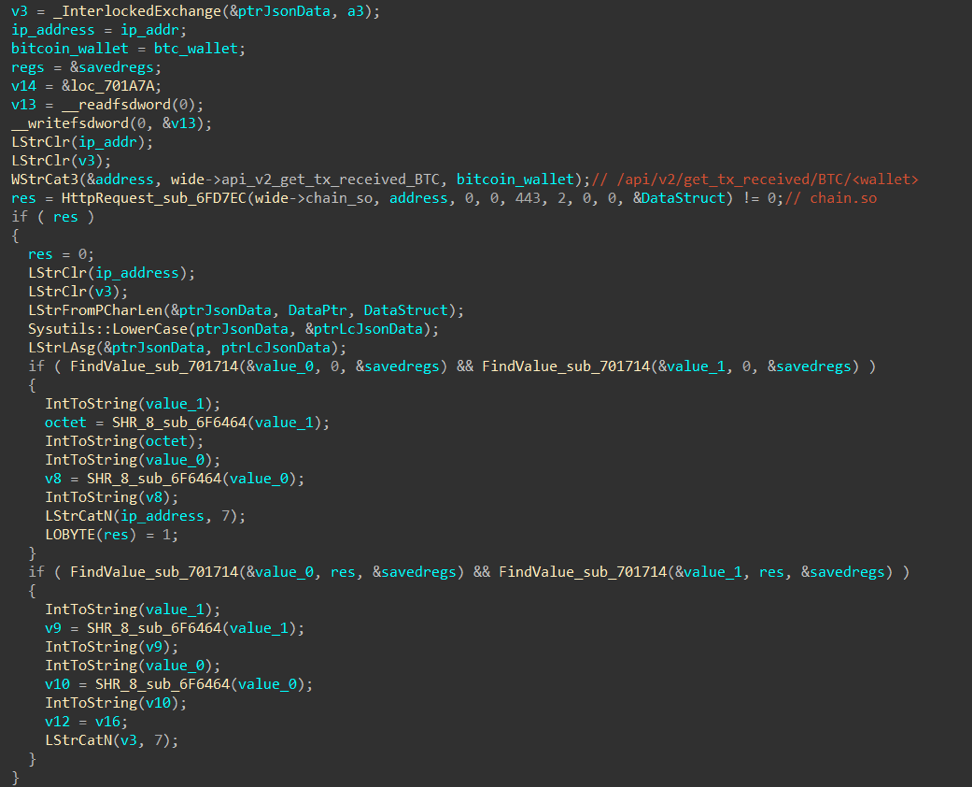
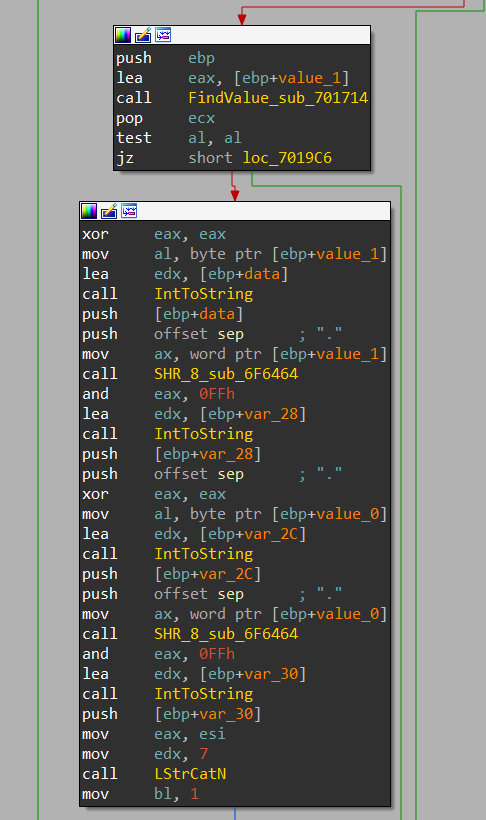
ip_address = str(value_1 & 0xff) + "." + str(value_1 >> 0x8) + "." + str(value_0 & 0xff) + "." + str(value_0 >> 0x8)That is, by listing 0.00008483 BTC and then 0.00040030 BTC, the attackers hid the IP address 94.156 [.] 35.33 for their program. Similarly, from the previous two transactions, RTM obtains the second IP address of the management server.
As such, RTM malware is being sent out to this day.
Conclusion
You may notice that when organizing the transfer of the C&C server address, RTM likes to use approaches that allow you to dynamically change IP without modifying the source code of the malware.
On the one hand, this makes life easier for attackers and can lead astray analysts. On the other hand, it allows specialists to predict the addresses of control servers before malicious mailings are carried out.
