Port scanner in the personal account of Rostelecom
Today, I accidentally discovered that the personal account of Rostelecom is engaged in completely malicious activity, namely, it scans local services on my computer. Since it is almost impossible to get responsible information from Rostelecom, I decided to point out this problem on Habré, so that the Habrovsk residents would be aware that you can expect very dubious behavior even from large and serious players.
And now, actually the details.
When he came to work that morning, I found in the system log remarkable line of VNC:
Ie someone from a localhost is trying to get on port 5900, then this is a virus or something worse. Of course, a cold sweat struck me, and I went to look for this pest. A quick analysis showed that there was a sweep every 10 minutes and 11 attempts were made to connect. It remains to find out who does this.
Once the connection is blocked, you need to make sure that someone is sitting on it. The easiest way for me was to raise an intelligent tcp server on the node, which does nothing and just keeps the connection.
I looked who connected there, it turned out to be Firefox:
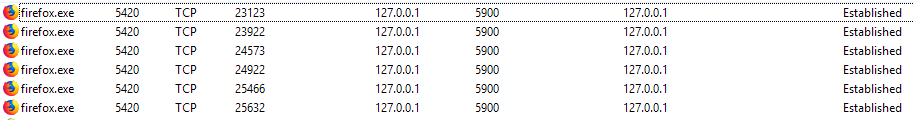
Then I went to find out which of the tabs or firefox extensions it does. It turned out that neither about: peformance nor about: networking show the id of a process that can make network requests. But I found out that this is the main browser process, and not an additional one for tabs or extensions, which made it difficult to identify the pest (yes, as always, I have a bunch of tabs open and finding the right one is quite difficult).
But with the help of patience, I found a wonderful tab, in the development console of which there were wonderful lines:

And this tab turned out to be the personal account of Rostelecom. After that, it turned out that the requests were as follows:
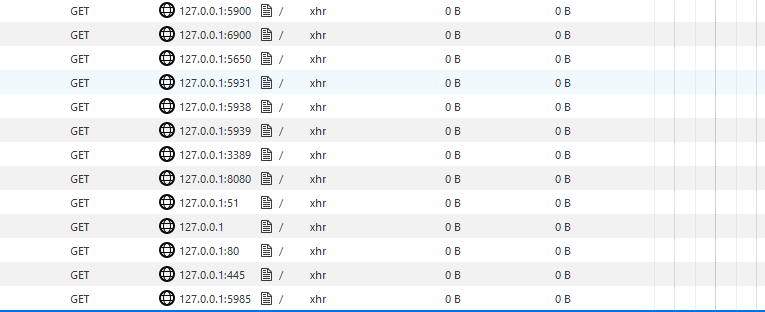
14 interesting enough ports:
Most ports are tools for remotely controlling a computer. It turns out, then we should expect attempts to penetrate these ports from the outside. Why could this be?
I have the following options in my head:
At the same time, my computer is not on the Rostelecom network, so these actions look very, very dirty.
UPD: Supplement from sashablashenkov
UPD2: runalsh clarified that this is not Dynatrace, but group-ib Some
more details. The script is located at:
i.e. it’s not some external counters or analytics, but its own script.
This script is obfuscated and the function that accesses the ports looks something like this:
The Ye array contains just the data of 14 ports, it is initialized in this way:
Those. in addition to minification, obfuscation was also added in Rostelecom, which means they suspected that they were doing something not very good, and it would be necessary to hide it.
What to do next, I do not know. It’s clear that it’s worth setting up browsers to protect against this (surprisingly, Firefox for some reason missed port 5900, although it decided to block others). There is no point in writing to Rostelecom, because their answers are always the same and do not differ in any kind of rationality.
Well, everyone else should know that port scanning can be not only on suspicious sites, but also on decent ones like Rostelecom. Rostelecom
answer :
And now, actually the details.
When he came to work that morning, I found in the system log remarkable line of VNC:
Connections: rejecting blacklisted connection: 127.0.0.1::22715Ie someone from a localhost is trying to get on port 5900, then this is a virus or something worse. Of course, a cold sweat struck me, and I went to look for this pest. A quick analysis showed that there was a sweep every 10 minutes and 11 attempts were made to connect. It remains to find out who does this.
Once the connection is blocked, you need to make sure that someone is sitting on it. The easiest way for me was to raise an intelligent tcp server on the node, which does nothing and just keeps the connection.
server.listen(5900, function () {});I looked who connected there, it turned out to be Firefox:

Then I went to find out which of the tabs or firefox extensions it does. It turned out that neither about: peformance nor about: networking show the id of a process that can make network requests. But I found out that this is the main browser process, and not an additional one for tabs or extensions, which made it difficult to identify the pest (yes, as always, I have a bunch of tabs open and finding the right one is quite difficult).
But with the help of patience, I found a wonderful tab, in the development console of which there were wonderful lines:

And this tab turned out to be the personal account of Rostelecom. After that, it turned out that the requests were as follows:

14 interesting enough ports:
| Port | Description |
|---|---|
| 5900 | Vnc |
| 6900 | Bittorrent |
| 5650 | Pizza trojan |
| 5931 | ? |
| 5938 | Teamviewer |
| 5939 | ? |
| 3389 | Rdp |
| 8080 | HTTP |
| 51 | F ** k Lamers Backdoor |
| 443 | Https |
| 80 | HTTP |
| 22 | Ssh |
| 445 | SMB |
| 5985 | Microsoft Windows Remote Management |
Most ports are tools for remotely controlling a computer. It turns out, then we should expect attempts to penetrate these ports from the outside. Why could this be?
I have the following options in my head:
- My account is hacked, and an attempt is being made to find out vulnerable computers and to plant a user a trojan
- This is a deliberate decision of Rostelecom and an attempt to do something bad to the user
- This is a deliberate decision of Rostelecom and an attempt to collect user data
At the same time, my computer is not on the Rostelecom network, so these actions look very, very dirty.
UPD: Supplement from sashablashenkov
Judging by this page, this is some kind of Dynatrace Real user monitoring
Dynatrace is the only vendor to capture the full visibility of customer experience across every digital transaction. No sampling of data, Dynatrace gives you a complete picture, from the frontend to the backend.
Monitor user journeys
Replay individual customer transactions for rapid problem handling
Dynatrace provides a single problem notification that identifies the root cause of the problem
Identify and resolve technical issues proactively
But why does it scan ports - don't understand
UPD2: runalsh clarified that this is not Dynatrace, but group-ib Some
more details. The script is located at:
https://lk.rt.ru/ruxitagentjs_ICA2SVfhqrux_10169190521113456.jsi.e. it’s not some external counters or analytics, but its own script.
This script is obfuscated and the function that accesses the ports looks something like this:
Aa: function () {
var a = this.Tg();
this.Qh(a);
for (var e = 0; e < this.Ye.length; e++) (function (c, f) {
if (!d.F.N(f.Gg, c) || !d.T.jh() || d.T.wb() || d.T.dc()) {
var e = (newDate).getTime(),
g = d.D.mb(Oa(1939), window.location[Ma(1402)] + $e(1358) + c),
k;
g.then(function () {
clearTimeout(k);
f.Ec(c, ua(1117), (newDate).getTime() - e, a)
}).then(void0, function () {
clearTimeout(k);
f.wc[c] ? delete f.wc[c] : f.Ec(c, Lb(1430), (newDate).getTime() - e, a)
});
k = G(function () {
f.wc[c] = !0;
g.te().abort();
f.Ec(c, Mc(1251), (newDate).getTime() - e, a)
}, f.$e || 10000)
}
}) (this.Ye[e], this)
},The Ye array contains just the data of 14 ports, it is initialized in this way:
this.Ye = b[Uh(1218)];Those. in addition to minification, obfuscation was also added in Rostelecom, which means they suspected that they were doing something not very good, and it would be necessary to hide it.
What to do next, I do not know. It’s clear that it’s worth setting up browsers to protect against this (surprisingly, Firefox for some reason missed port 5900, although it decided to block others). There is no point in writing to Rostelecom, because their answers are always the same and do not differ in any kind of rationality.
Well, everyone else should know that port scanning can be not only on suspicious sites, but also on decent ones like Rostelecom. Rostelecom
answer :
The press service of Rostelecom said that the script is used as an “anti-fraud system to prevent online fraud” by analyzing the user session. This system really collects data on user activity and searches for “indicators of compromise of their devices”.
The company explained that the antifraud system had to be introduced in connection with the recent attempts at fraud in relation to personal accounts of subscribers and bonus programs of Rostelecom.
