Message Encryption in SecureDialogues
Encryption, digital signature, data protection are terms quite common among IT professionals.
Already written a lot of interesting publications, articles and books on these topics. After reading one of them, I decided to try my hand at practice. And so the project was born, which will be discussed below.
Application Brief
The SecureDialogues application adds a level of encryption to messages that are transmitted through services such as Gmail . The application itself performs authorization for the configured services using the OAuth2 protocol , receives and sends messages. At its core, it is a regular messenger that provides cryptographic protection to messages, unless one of several third-party services can be used for transfer .
Data on the hard disk is encrypted using the AES algorithm with a 256- bit key, which is extracted from the password entered at startup, RSA is used for digital signature . User messages are encoded with a 256- bit AES session key .
Source codes are available at the link , project wiki .
Launching the application in the docker container is available , more on the link .
Purpose of creation
The application was created for a very specific purpose - it was interesting for me to work with cryptography on a practical project. And not in some simple one, like “insert the text here, but here take the encoded message”, but in such that there is a digital signature , and asymmetric encryption , and session keys and other interesting things. Therefore, the messenger project was chosen.
In the absence of all the necessary infrastructure for sending messages, this function is delegated to existing services like Gmail or VKontakte .
Interface Description
When you first start the application will ask you to enter a password:
This password is used to encrypt data stored on the hard drive, such as: RSA keys , authorization tokens for OAuth2 , data on services and contacts.
Messages and information about dialogs are not saved , that is, at the end of the application, data about received messages and open dialogs are lost.
On subsequent launches, the application also asks for a password in order to decrypt and download previously saved data.
View of the main application window:
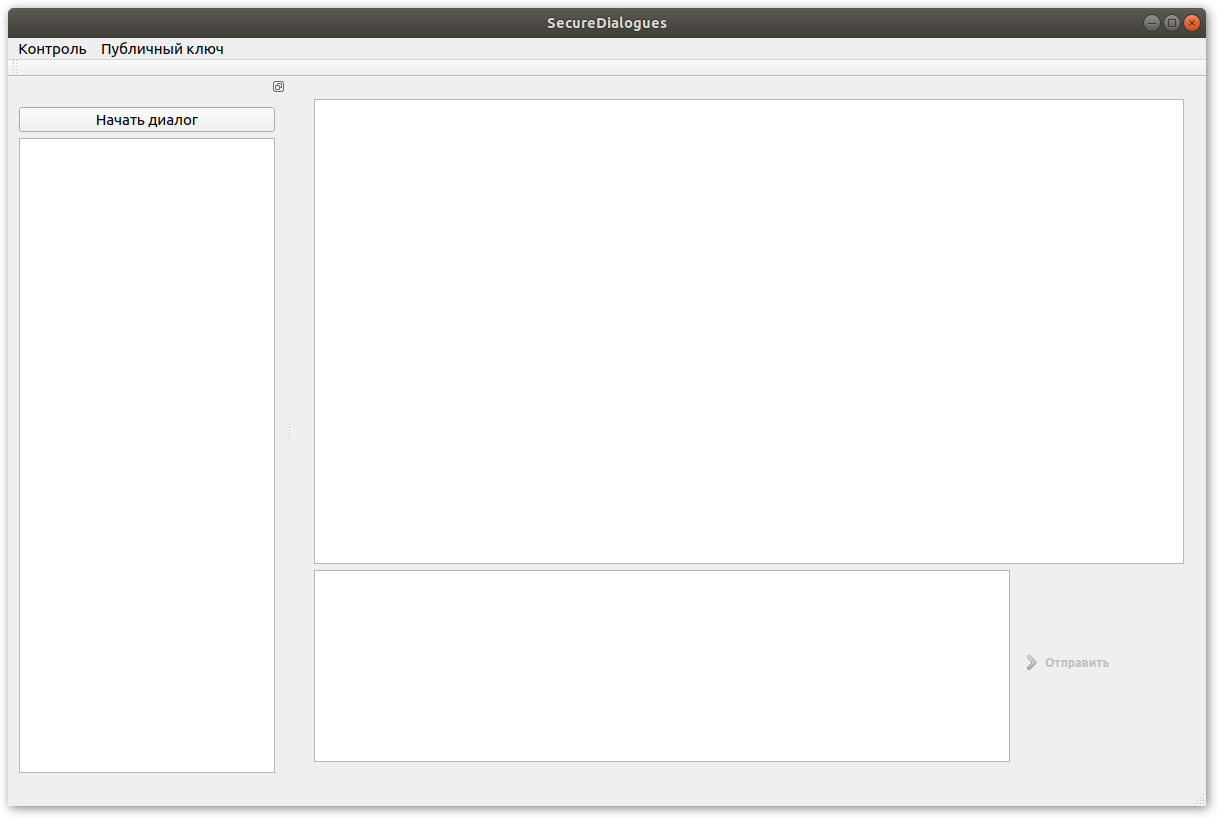
Before you can send the first message, you must complete two steps:
- Set up a connection to the service for sending messages ( more on the wiki );
- Add contact person ( more on the wiki );
The most important thing, because of which the contact is added before the start of the exchange, is the public key . Each message that is sent between users must be signed by the sender. If the recipient was unable to verify the digital signature using the public key, then such a message is discarded.
Also, the public key is used to encrypt the session key.
After all the preliminary steps are completed, you can start the dialogue. To do this, there is a corresponding button in the main application window ( more on the wiki ). When creating a conversation, a session key is generated that will encrypt all messages within this conversation.
All dialogs are displayed in the main window on the left. After your interlocutor has confirmed the creation of a dialogue, you can send and receive messages in it:
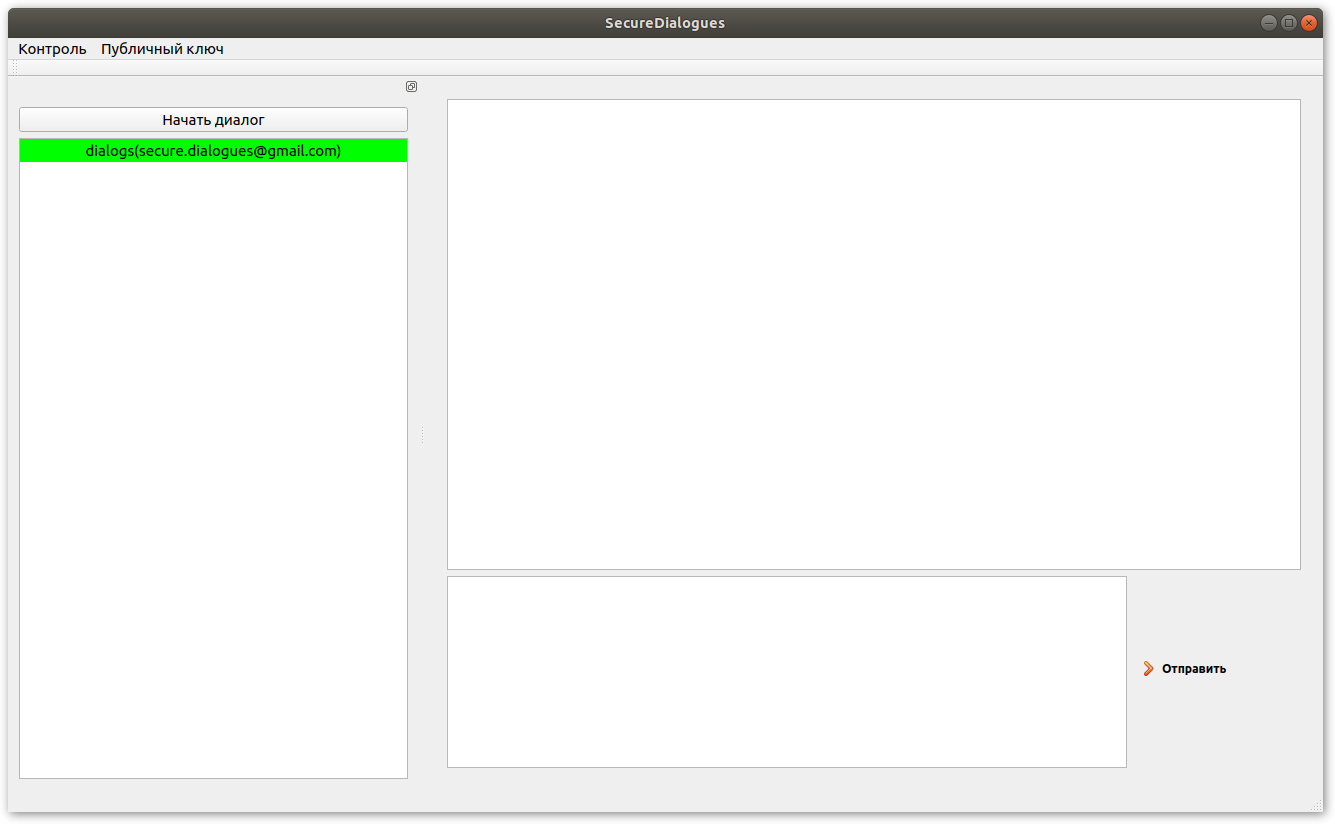
To send or read messages in the desired dialog, you need to select it by clicking the left mouse button.
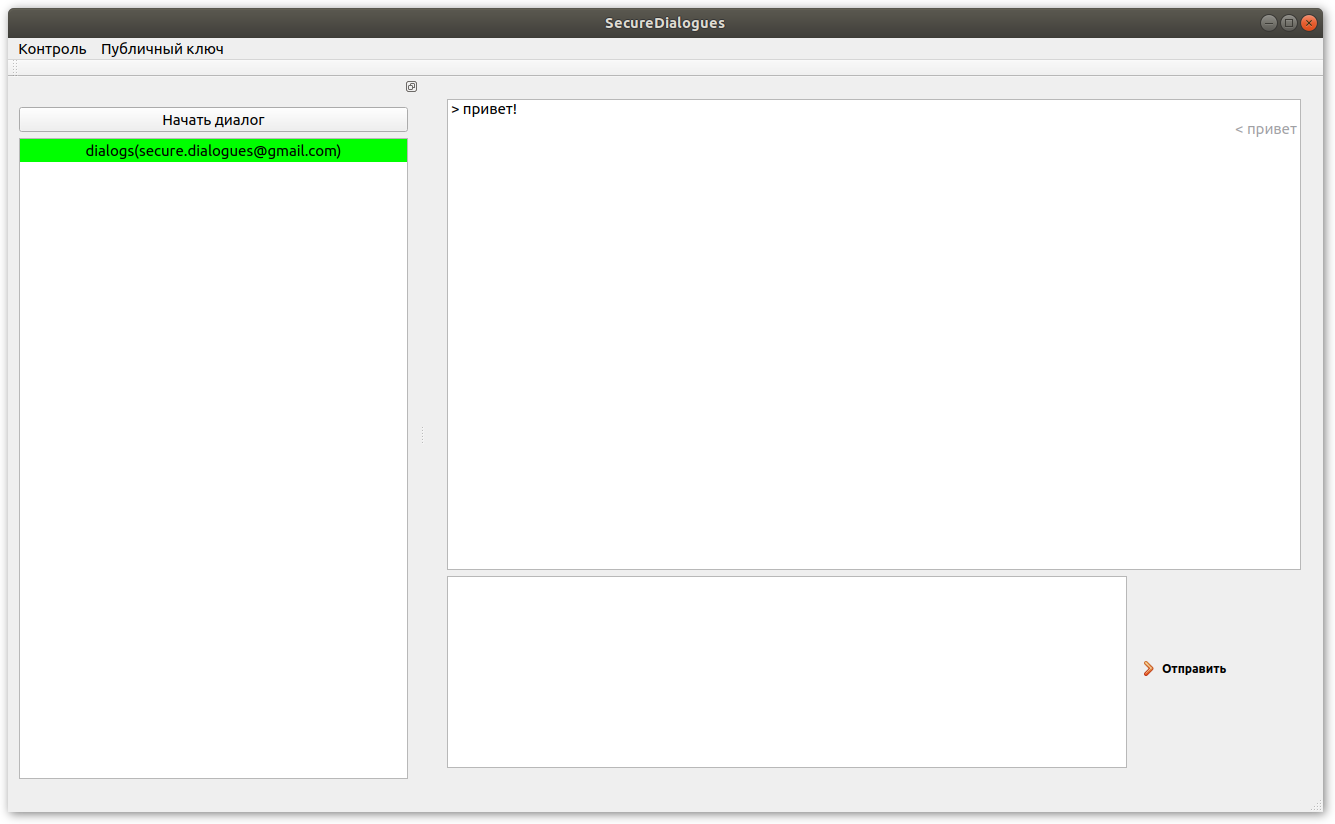
Messages of the remote user are displayed on the left, and yours on the right. If the message has not yet been delivered, it is displayed in gray:
The application sorts the list of dialogs in the following order - at the very top there will be active dialogs for which sending messages is allowed, and at the very bottom there will be closed ones. Also, the order is affected by the time the dialog changes. The active dialogue that the last message received will be above all, and the first closed one will be at the bottom. For each dialogue, an indicator of the number of unread messages is displayed, if any:

The dialogue status is highlighted in color:
- closed dialogs are red
- active dialogs are shown in green , it is possible for them to send messages
- gray dialogs are in the making.
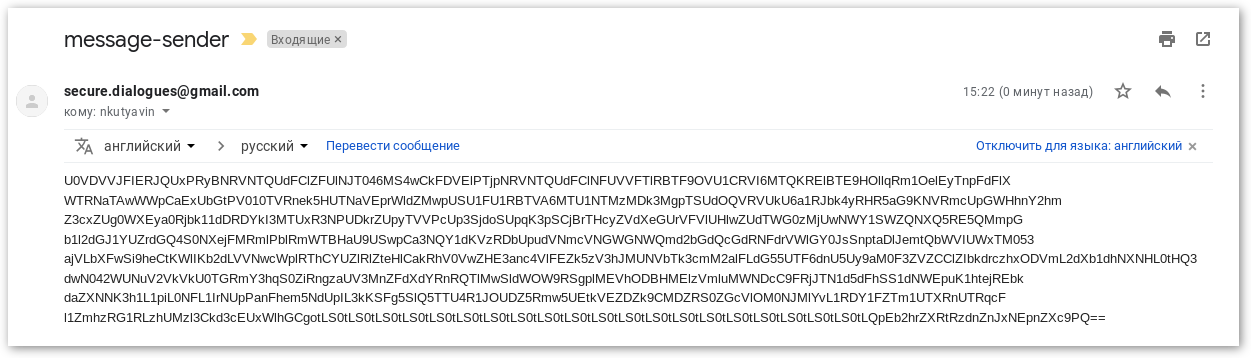
Here's an example of what a simple message with hellow world text looks like ! :
Signal exchange
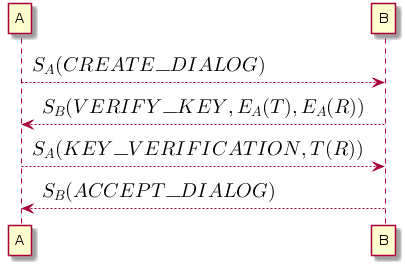
The exchange of messages between interlocutors A and B consists of the following steps:
- side A generates a command to create a dialogue (
CREATE_DIALOG) and signs it with its private key; - party B asks the user for consent to create a dialogue, and if the user agrees, a session key T and a random string R are generated , which are individually encrypted with public key A and placed in the message body (
VERIFY_KEY). All message signed by a private key Bed and . - side A decrypts the session key and random string, encrypts the random string with the session key, adds the result to the message body
KEY_VERIFICATION. Signs the entire message with his private key. - side B decrypts the random string, check if the result matches the string R , if everything is correct, then a signed message is sent
ACCEPT_DIALOG, which means that the dialogue is established and further message exchange is possible.
Successful dialogue establishment and signal exchange are shown in the figure:
Further development of the project
At the moment, the application already provides basic capabilities for message encryption and authentication through digital signature. But the list of supported services is extremely small.
In the future, it is planned to increase it. Work is already underway to include VKontakte into it .
Also in the project is an increase in the information content of the user interface, such as adding a status for connecting to a service (active, connection error, etc.).
The algorithm for checking duplicate messages does not work in the best way, it is planned to be finalized.
