Certification of information systems on the principle of standard segments. Myths and Reality
Good day, Habr! Today we would like to consider various myths related to the certification of objects of informatization (OI) for information security requirements on the principle of standard segments. And also we will figure out how to do such certification correctly.
Myths must be said about this a lot of circulating and often they contradict each other. For example, there is an opinion that, according to the principle of standard segments, you can certify all ISPDs in a country (although certification is not mandatory for ISPDs), but on the other hand, there is an opinion that you need to certify information systems only the old fashioned way, and all these your “typical segments” from crafty.
Introduction
Certification of the object of informatization is perhaps one of the most regulated and conservative stages in the construction of an information protection system.
Conservatism lies in the fact that the certification is subject to a specific system with a specific list of technical means, which are neatly rewritten in the technical passport to the object of informatization and in the certificate of conformity itself. Replacing, for example, a burned-out computer from a certified information system may entail at least lengthy correspondence with the organization that conducted the certification, and at the very least additional certification tests (that is, costs).
This was not a big problem, while the certification of information security requirements were either free-standing computers that process the protected information, or small dedicated local area networks.
But progress does not stand still. Now, for state information systems, the 17th decree of the FSTEC determines their mandatory certification prior to commissioning. And state information systems today are not a static computer or a small lokalka, but large dynamically changing systems, often of regional or even federal scale.
So what to do in this case? Attestation is required, but it is impossible to certify a static system, since there almost every day new elements are added and old ones are removed. "Typical segments" come to the rescue.
This concept was introduced by the 17th order of the FSTEC and the standard GOST RO 0043-003-2012 “Information protection. Certification of objects of informatization. General Provisions ”in 2013. Unfortunately, GOST is marked “chipboard”, unlike the FSTEC order, so the standard cannot be quoted here. But nothing will be lost from this, since the order of the FSTEC in the order for the extension of the certificate of conformity to typical segments is described in much more detail (section 17.3), and a couple of short paragraphs are devoted to this in the standard.
Myths around Type Segment Certification
There are many myths around typical segments. Here we will analyze those that we ourselves have encountered. If you have examples of similar myths or questions (you are not sure if this is a myth or not), welcome to comment.
Myth number 1. One certificate on the principle of standard segments can certify all information systems in the Russian Federation
Theoretically, this is not directly prohibited by regulatory documents, but in practice this will not be possible. One of clauses 17 of the FSTEC order on model segments states that the execution of organizational and administrative documentation for information protection should be ensured in standard segments. So, the big problem is precisely in the development of such documentation, which will take into account different technological processes of information processing, different protected information, different requirements of regulators, etc. As a result, documentation developed for one system will not be relevant for another.
Myth number 2. "Typical segments" are provided only for state information systems
This is not true. Firstly, the 17th order of the FSTEC itself allows its provisions to be applied in the development of information protection systems in any other information systems. Secondly, GOST RO 0043-003-2012 uses the broader concept of “informatization objects” instead of “state information systems”.
Myth number 3. If they give us a certificate that can be extended to standard segments, then we can apply it to anything
This is not so, under the spoiler the full text of paragraph 17.3 of the FSTEC order No. 17 for typical segments, then we will consider cases where the issued certificate cannot be distributed. Here we have to stay in more detail.
Text from the order of FSTEC No. 17
Certification of the information system is allowed on the basis of the results of certification tests of a selected set of segments of the information system that implement the full technology of information processing.
In this case, the distribution of the certificate of conformity to other segments of the information system is carried out provided that they correspond to segments of the information system that have passed certification tests.
A segment is considered appropriate for the segment of the information system in respect of which certification tests were carried out if the same security classes, threats to information security were established for the indicated segments, the same design solutions for the information system and its information protection system were implemented.
The conformity of the segment covered by the certificate of conformity with the segment of the information system in respect of which the certification tests were conducted is confirmed during acceptance tests of the information system or segments of the information system.
In the segments of the information system to which the certificate of conformity applies, the operator ensures compliance with the operational documentation for the information system information protection system and organizational and administrative documents for information protection.
The features of certification of an information system based on the results of certification tests of a selected set of its segments, as well as the conditions and procedure for distributing a certificate of conformity to other segments of an information system, are defined in the program and methods of certification tests, conclusion and certificate of conformity.
In this case, the distribution of the certificate of conformity to other segments of the information system is carried out provided that they correspond to segments of the information system that have passed certification tests.
A segment is considered appropriate for the segment of the information system in respect of which certification tests were carried out if the same security classes, threats to information security were established for the indicated segments, the same design solutions for the information system and its information protection system were implemented.
The conformity of the segment covered by the certificate of conformity with the segment of the information system in respect of which the certification tests were conducted is confirmed during acceptance tests of the information system or segments of the information system.
In the segments of the information system to which the certificate of conformity applies, the operator ensures compliance with the operational documentation for the information system information protection system and organizational and administrative documents for information protection.
The features of certification of an information system based on the results of certification tests of a selected set of its segments, as well as the conditions and procedure for distributing a certificate of conformity to other segments of an information system, are defined in the program and methods of certification tests, conclusion and certificate of conformity.
Further we will take specific examples of errors, and cite only the appropriate quotes from this normative act as a justification why this cannot be done.

Example No. 1
Only the server part is certified, but I want to extend the certificate to workstations (AWS). Can this be done?

Not! Allowed certification of the information system based on the results of certification tests highlighted a set of information system segments, implementing full of information processing technology .
Information transfer via communication channels is also a processing technology. Plus, in this example, not a single workstation is certified, so we can not extend the certificate to another standard workstation.
Example No. 2
Here we took into account the previous error and included data transmission channels and a typical workstation in the certificate. Suddenly, we had a need to organize a laptop for a big boss with a connection to a certified system (via secure channels, of course). Can we extend the certificate of conformity to this laptop?
Not! A segment is considered to correspond to the segment of the information system for which certification tests were carried out if the same security classes and threats to information security were established for these segments ...
Here for mobile technical means new information security threats appear that are not relevant for stationary workstations and most likely are not taken into account in the threat model for a certified system.
Example No. 3
Well, we took this jamb into account and added threats to the growth model, threats to mobile devices. Now can I extend the certificate to the laptop of a big boss?
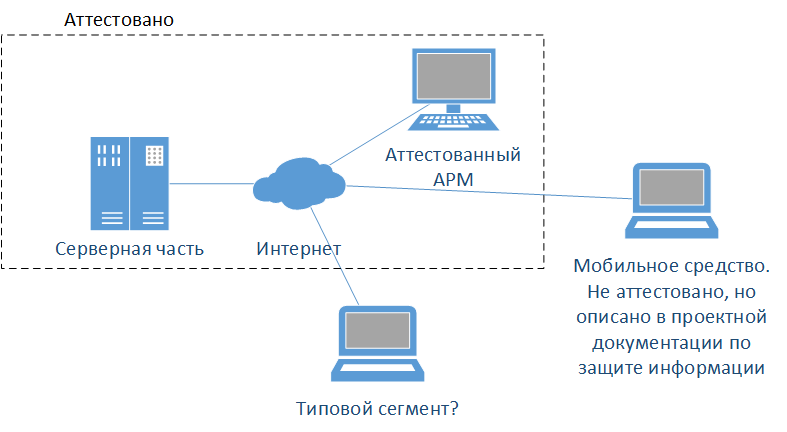
Not! A segment is considered to be relevant to the segment of the information system for which certification tests were conducted ...
Despite the fact that the mobile tool was described in the design documentation for the information security system and the threat model took into account threats associated with mobile technical means, in relation to such a tool certification tests were conducted.
Example No. 4
How complicated it is! But this situation: there is a medical institution, there are two information systems - with employees and a medical information system (MIS) with patients. Can we save, certify the information system with employees and extend this certificate to IIAs?
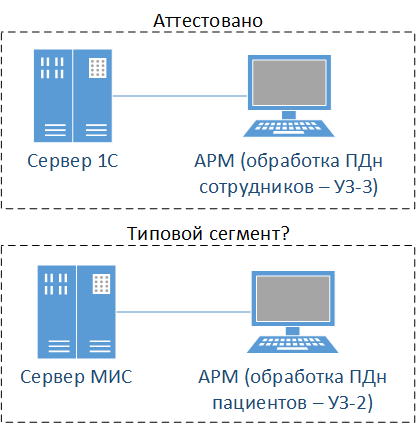
Not! A segment is considered appropriate for the segment of the information system in respect of which certification tests were carried out if the same security classes were established for the indicated segments ... the same design solutions for the information system .

Although it seems that everything is complicated here, in fact, you just need to think about the possible options for typical segments in preparation for building a protection system. But in fact, if you take everything into account (and there are not so many requirements), then there will be no problems with the distribution of the certificate.
Myth number 4. Typical segments must be described in the design documentation for the protection system, starting with the threat model
There is no such requirement. Although this is not directly prohibited, this approach may lead to some problems in the future. What are we talking about this 17 th order FSTEC:
Features certification information system based on the results of certification tests selected set of its segments, as well as the conditions and procedures for the spread of the certificate of conformity to other segments of the information system defined in the program and methods of certification tests, the conclusion and the certificate of conformity .
That is, we have the right to mention typical segments only at the stage of certification. In this case, your segments will be typical by default, if the conditions of section 17.3 of FSTEC order No. 17 are met. But we met cases when typical segments were tried to describe already at the stage of threat modeling, almost indicating the serial numbers of the equipment of such segments. The problem with this approach is that if a hardware replacement occurs or something changes in the processing technologies (for example, a virtualization environment appears), the segments into which the certificate is already distributed may become, let's say, illegitimate typical. And in this case, it may be necessary to carry out not “additional certification tests”, but to conduct the entire set of tests according to the new one.
In general, our advice is not to mention typical segments in the design documentation at all. Indeed, under the current legislation, any segment that meets the established conditions will be typical.
IMPORTANT! If you are an operator of an information system and plan to certify an information system with the ability to extend the certificate to standard segments, be sure to discuss with your certification body so that this possibility is reflected in the certification documents, as required by the 17th order of the FSTEC!
Myth number 5. FSTEC does not understand "typical segments" and if we are certified like this, we will be punished
This myth sounds very strange, given that typical segments are described in more detail in the regulatory documentation from FSTEC. This idea is most often heard from the security guards of the so-called “old school”.
In general, except for “this is not true” we have nothing to say here. On the contrary, the regulator is promoting this certification system of information systems in every possible way and quite recently we even came across a claim from the FSTEC that a huge regional-level information system was certified NOT by the principle of standard segments. There I had to explain that in that particular case it was not optimal.
Myth number 6. Typical segments only work when the certified part and segments are the property of one organization
It is not true. This is not explicitly stated in the legislation, but everything that is not prohibited is allowed. But, of course, there are certain differences when the certified part and model segments are the property of one organization, and when the model segments belong to third-party legal entities, there are.
In cases where everything belongs to one organization, this organization can independently carry out measures to protect information on a standard segment, appoint a commission and extend the certificate to a standard segment.
In cases where there is a central operator of the state information system (for example, a regional Information Technology Center) and segments of other legal entities (as an example, a regional document management system of state institutions), then everything is a little more complicated. The difficulty lies in the fact that according to the law, the operator of these GIS is responsible for the protection of information in state information systems. Therefore, so that the next test does not heat up the operator for the fact that somewhere in the school 400 km from the regional center, information protection measures are not taken, he needs to document this process at least at the stage of connecting a typical segment. First of all, the rules for connecting to the information system are created, where the operator clearly and clearly describes the requirements for protecting information, to be performed on the connected segment. This usually includes the appointment of those responsible, the approval of internal documents for information protection (especially confused operators can even develop and provide a standard set), the purchase, installation and configuration of the necessary information protection tools, vulnerability analysis, etc. Further, the organization wishing to connect performs all requirements and in the manner specified in the regulations confirms this.
On the other hand, all the difficulties described are an approximate plan of action that we already invented together with one of such operators. If the operator of a distributed GIS is not afraid to bear responsibility for not proving the fact of fulfilling the requirements for protecting information on the remote segment at least at the connection stage, then he can go along a simplified path (how “simplified” this operator can decide).
Unfortunately, some operators do so because they sincerely believe in the following myth.
Myth number 7. The certification authority is responsible for extending the certificate to segments that do not meet the requirements.
It is very important for us, as a certification body, to understand the boundaries of our responsibility. Since the law does not answer clearly the question “who is responsible for extending the certificate to non-conforming segments”, we wrote a letter to the FSTEC.
FSTEC replied that the certification body is only responsible for the quality of the certification tests themselves. The organization-operator of the information system is responsible for the correct distribution of the certificate to typical segments.
Myth number 8. Typical segments will not give us anything. Anyway, you have to attract a licensee and pay him money
This is not true. At least in cases where the staff of the operator of the information system has specialists who are able to carry out all the activities described above.
On the other hand, we often encounter the fact that we are asked to help with connecting standard segments. Anyway, in such segments, at least, you need to work out internal documentation, install and correctly configure information security tools. Plus, many information system operators trust the conclusions on the conformity of a typical segment written by a third-party organization more than the report of the applicant for connection to the system.
But even in this case, typical segments allow the operator to save money, since at least there is no need to develop a separate threat model and design documentation for the information protection system for attachable elements. There is also no need to carry out full-scale certification tests.
Myth number 9. In typical segments, only the same technical means should be used (for example, computers with the same motherboard, the same processor, the same RAM, up to the type, manufacturer and model)
This issue is also clearly not spelled out in the legislation. On an intuitive level, it is clear that full compliance of the iron of the certified and connected segment is not required, otherwise the whole thing is worthless. And when we need to clarify a similar question, what do we do? That's right - we are writing a letter to the regulator. FSTEC expectedly replied that identical (one manufacturer, one model, etc.) technical solutions should not be used in typical segments.
In order for a segment to be considered appropriate for the certified one, it is necessary that the same security class be established for it, the same threats to information security are identified and the same design solutions are implemented for the system itself and for the information protection system. As actually written in the 17th order.
Myth number 10. For each attachable type segment, you need to create your own threat model.
Not. In the typical segment, the same threats should be relevant as in the certified part of the information system. Accordingly, the threat model is one for the entire system. If any significant technological changes occur in the certified information system that could lead to the emergence of new threats to information security, it is necessary to revise the general threat model and, if necessary, conduct additional certification tests of the system as a whole.
Myth number 11. Data of attached standard segments does not need to be reflected in the technical passport for the information system
On this issue, we also asked the FSTEC. The answer is that the data of new segments must be entered in the technical passport. But whether to enter new data into the general data sheet for the system or to make a separate document for the segment is up to the operator. In our opinion, it is more convenient to make a separate technical passport for a typical segment.
That's all. If you still have questions about the topic - welcome to comment. We hope that our publication will be useful and make life easier for operators of certified information systems.
