"Runet Isolation" or "Sovereign Internet"

On May 1, the law on “sovereign Internet” was finally signed , but experts almost immediately dubbed it isolation of the Russian segment of the Internet, so from what? (in simple language) The
article aims to inform the Internet users in general without diving into excessive jungle and abstruse terminology. The article explains for many simple things, but for many it does not mean - for everyone. And also dispel the myth of the political component of criticism of this law.
How does the internet work?
Let's start with the basics. The Internet network consists of clients, routers and infrastructure, works through the IP protocol

(v4 address looks like this: 0-255.0-255.0-255.0-255)
Clients are user computers themselves, the one you are sitting at and reading this article. Have a connection with neighboring (directly connected) routers. Clients send data to the address or address range of other clients.
Routers - Connected to neighboring routers and can be connected to neighboring clients. They do not have their own unique (only for redirection) IP addresses, but are responsible for a whole range of addresses. Their task is to determine whether they have clients with the requested address or if they need to send data to other routers, here they also need to determine which of the neighbors is responsible for the desired range of addresses.
Routers can stand at different levels: provider, country, region, city, district and even at home you most likely have your own router. And they all have their own address ranges.
Infrastructure is the points of traffic exchange, communication with satellites, continental entrances, etc. they are needed to combine routers with other routers that belong to other operators, countries, types of communications.
How can I transfer data?
As you understand, clients and routers themselves are connected by something. It can be:
Wires
- On the ground The backbone network of Rostelecom

- Under the waterTransoceanic submarine cables
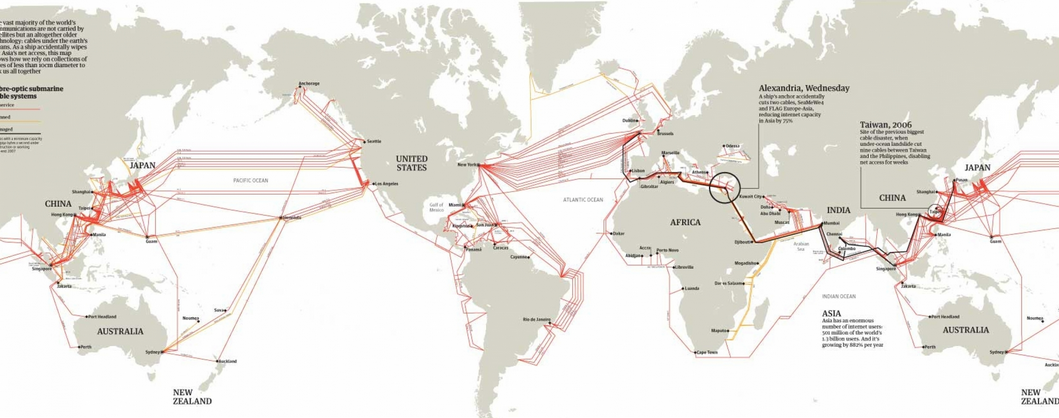
Air
These are Wi-Fi, LTE, WiMax and radio bridges of operators who use where it is difficult to conduct wires. Full-service provider networks are not built from them; they are usually a continuation of wired networks.
Space
Satellites can serve both ordinary users and be part of the infrastructure of providers.
ISATEL satellite coverage map

Internet is a network
As you can see, the Internet is solid neighbors and neighbors of neighbors. At this level of networking, there are no centers and red buttons for the entire Internet. That is, evil America cannot make traffic stop between the two Russian cities, between the Russian and Chinese cities, between the Russian and Australian cities, no matter how much they would like. The only thing they can do is drop bombs on routers, but this is no longer a network threat level.
in fact, there are centers, only shhhh ...
but these centers are extremely informative, that is, they say that this is the address of such and such a country, such and such a device, such and such a manufacturer, etc. Without this data, nothing changes for the network.
Void little people are to blame for everything!
A level above the net data, is our visited with you, World Wide Web. The principle of protocols in it is human-readable data. Starting from the addresses of sites, for example, google.ru differs from the machine 64.233.161.94. And ending with the Http protocol itself and the JavaScript code, you can read all of them, not in your own, but in human language without any conversions.
This is the root of evil.
To convert human-readable addresses to router-friendly addresses, registries of these same addresses are needed. Just as there are state registries of administrative addresses by type: Lenin St., 16 - Ivan Ivanovich Ivanov lives. So there is a common global registry where it says: google.ru - 64.233.161.94.
And it is located in America. So, here’s how we are disconnected from the Internet!
In fact, everything is not so simple.

According to open data
ICANN is the contractor of the international community to perform the IANA function without government control (primarily the US government), so the corporation can be considered international, despite being registered in CaliforniaMoreover, even though ICANN manages management, it does so only with requirements and decrees, and another non-state company, VeriSign, is responsible for execution.
Next come the root servers, there are 13 of them and they belong to different companies from the US Army to institutes and non-profit companies from the Netherlands, Sweden and Japan. There are also full copies of them around the world, including in Russia (Moscow, St. Petersburg, Novosibirsk, Rostov-on-Don).
And most importantly, these servers contain a list of trusted servers around the world, which in turn contain another list of servers around the world that already contain the registries of names and addresses.
The real goal of root servers is to say that the registry of such and such a server is official, not fake. On any computer, you can raise the server with your list, and for example, when you contact sberbank.ru, they will not send you its real address - 0.0.0.1, but 0.0.0.2, on which the exact copy of the Sberbank website will be located, but all data will be stolen. In this case, the user will see the desired address in a human-readable form and in no way will be able to distinguish a fake from a real site. But the computer itself needs only an address and it works only with it, it does not know about any letters. This is when viewed in terms of potential threats. For some reason we are introducing a law?
* one recognizable ncbi - what it costs
The same goes for the common root of the https / TLS / SSL certification - which is already purposefully dedicated to security. The plan is the same, but the rest of the data is sent along with the address, including public keys and signatures.
The main thing is that there is an endpoint serving as a guarantor. And if there will be several such points with different information, then organizing the substitution is easier.
The main goal of address registries is to maintain a common list of names in order to avoid two sites with one address visible to a person and different IPs. Imagine the situation: one person publishes a link to the magazine.net website on a page with the study of the protection against drug addiction of amphetamine stimulants with the help of amphonelitic acid, another person became interested and clicked on the link. But the link is just the text itself: magazine.net, contains nothing but. However, when the author published the link, he simply copied it from his browser, but he used Google DNS (the same registry), and he has the address 0.0.0.1 under the magazine.net entry, and one of the readers who clicked on the link uses Yandex DNS and it stores in itself another address - 0.0.0.2, on which the electronics store and the registry do not know anything about any 0.0.0.1. Then, the user will not be able to view the article he is interested in. Which basically contradicts the whole meaning of links.
Who is particularly interested: in fact, registries contain a whole range of addresses, and sites can also change the final IP for various reasons (Suddenly, the new provider provides great speed). And so that links do not lose relevance, DNS provides the ability to change addresses. It also helps with increasing or decreasing the number of servers serving the site.
As a result, with any decision by the American side or military attacks, including the seizure of non-state institutions, falsification of root centers or the complete destruction of ties with Russia, it will in no way be able to bring the stability of the Russian segment of the Internet to its knees.
Firstly, the main encryption keys themselves are stored in two bunkers on different edges of the United States. Secondly, the administrative management is so distributed that it is necessary to agree with the whole civilized world on the disconnection of Russia. That will be followed by a long discussion and Russia will just have time to establish its infrastructure. At the moment, no such proposals in history have even been made in theory. Well, there are always copies anywhere in the world. It will be enough to redirect traffic to the Chinese or Indian copy. As a result, you have to agree with the whole world in principle. And again, on the territory of Russia there will always be the last list of servers and it will always be possible to continue from where you left off. Or you can simply replace the signature with another.
You can don’t check the signature at all - even if everything happens instantly, and the Russian centers are destroyed, providers can ignore the lack of communication with the root servers, this is purely for added security and does not affect routing.
Operators also store the cache (the most popular ones requested), both the keys and the registries themselves, and on your computer a piece of the cache of the websites you have popular is stored. As a result, at first you will not feel anything at all.
There are also other WWW centers, but they often work on a similar principle and are less necessary.
Everyone will die, and the pirates will live!

In addition to the official root servers, there are alternative ones, but they usually belong to pirates and anarchists who oppose any censorship, so providers do not use them. But the chosen ones ... Even then, if the whole world conspires against Russia, these guys will still continue to serve.
By the way, the DHT Torrent peer-to-peer network algorithm can live peacefully without any registries; it does not request a specific address, but communicates with the hash (identifier) of the desired file. That is, the pirates will live in general under any circumstances!
The only real attack!
The only real threat can only be a conspiracy of the whole world, with cutting all the cables leading from Russia, knocking down satellites and installing radio interference. True, in this case, the world blockade, the last thing that will interest is the Internet. Or an active war, but everything is the same there.
The Internet inside Russia will continue to function. Just with a temporary decrease in security.
So what is the law about?
The strangest thing is that the law in theory describes this situation, but offers only two real things:
- Make your own WWW centers.
- Transfer all the Internet transition boundary points to Roskomnadzor and install content blockers.
No, these are not two things that solve the problem, they are basically two things that are in the law, the rest is of the type: “you need to ensure the stability of the Internet”. No methods, fines, plans, distribution of responsibilities and those responsible, but simply a declaration.
As you already understood, only the first point is related to the sovereign Internet, the second - censorship and only. Moreover, this can reduce the activity of building border networks, and, ultimately, reduce the stability of the sovereign Internet.
The first point, as we have already found out, solves the problem of an unlikely temporary and less dangerous threat. This will already be done by network participants when threats appear, but here it is proposed to do so in advance. You need to do this in advance, only in one very depressing case.
The results are disappointing!
To summarize, it turns out that the government allocated 30 billion rubles to a law that would solve an unlikely non-dangerous situation, which in the best case would not harm. And the second part will establish censorship. We are offered the introduction of censorship so that we are not disconnected. With the same success, you can offer to drink milk on Thursdays throughout the country to avoid killing. That is, both logic and common sense say that these things are not connected and cannot be connected.
So why is it that the government is preparing to proactively total censorship ... censorship and war?

UFO Care Minute
This material could cause conflicting feelings, so before writing a comment, refresh something important in your memory:How to write a comment and survive
- Do not write offensive comments, do not get personal.
- Refrain from obscene language and toxic behavior (even in a veiled form).
- To report comments that violate the rules of the site, use the "Report" button (if available) or the feedback form .
What to do if: minus karma | blocked an account
→ Code of authors Habr and habraetiket
→ Full version of site rules

