When the walls are not enough. How to protect endpoints
- Tutorial

Do you think the most important thing in the company is to ensure the security of the corporate network perimeter and server infrastructure? This is only partly true: it is now impossible in principle to create a secure perimeter only if the company does not apply the strictest IS rules, the “white list” of sites, only paper correspondence and the sealing of USB ports on computers, and the reception is not allowed further on with a smartphone. If this is not about your company, then keep in mind: today, end devices are becoming the main risk zone, and antivirus protection alone is not enough. Yes, the antivirus will block the unpacking of the archive with the dangerous file, and the browser will prevent you from visiting the compromised site, but there are many threats for which the basic protection packages are powerless. Next, we will talk about some of them - and how to protect them.
What a regular antivirus in a company cannot handle
- Fileless attacks . Malicious PowerShell scripts that fall directly into RAM cannot be detected by the antivirus at the stage of penetration into the system - these are not executable programs, but simply a text-based set of commands that runs in an existing shell like OS PowerShell. In order not to disappear when the computer is turned off, the trojans register their commands in the registry.
It is impossible to detect file-free attacks by traditional methods - a trojan can store a malicious script, for example, in TXT files of DNS resource records. According to Trend Micro 2018 Midyear Security Roundup, the number of fileless attacks in the world is growing: in January 2018, 24,430 incidents were recorded, and in June - more than 38 thousand.
- Exploits in non-updated OS . Operating system updates fix known vulnerabilities for which exploits can already be written. Before deploying updates to hundreds and thousands of computers, you should first test it - sometimes updates contain errors, due to which some computers temporarily fail. Shifting the task of installing updates onto users ’shoulders is a surefire way to create a network breach through the fault of an optional or inept employee.
The sensational WannaCry and NotPetya used to spread the vulnerabilities of Windows, which were closed to updates two months before the outbreak: the first WannaCry revision appeared on January 16, 2017, on March 14, Microsoft distributed the patch for the SMB protocol in all current versions of Windows, and the legendary epidemic only started 12 May. Having penetrated users' computers not updated, the ransomware spread inside corporate networks, paralyzing the activities of companies. Why hundreds of thousands of corporate computers in major companies for two months were left without a critical update of Windows - a serious question for the relevant services.
- Mobile devices. Despite checking applications before publishing in the Play Market and App Store, spyware and even miners are often screwed to supposedly useful programs. For example, an analysis of 283 VPN applications for Android revealed that 43% of them contain unwanted ads, and 17% have malicious functions, 29% are the source of Trojan modules, potentially dangerous software is contained in 6% VPN, and another 5% spy for their users .
- Employees who do not know the basic principles of information security . The main hole in the information security of any company remains employees, or rather, their ignorance of the principles of information security. No virus can take away important information and documents with the same elegance and efficiency as an employee who downloads a program for its own convenience in work, which as a result turns out to be malicious.
How to protect endpoints
The growing sophistication of threats makes traditional methods of defense ineffective. Antivirus alone is not enough to prevent data leaks or intruders from entering the network, and installing several highly specialized solutions often leads to conflicts and errors. In addition, setting up and maintaining the collaboration of several security programs is not an easy task. An integrated solution is required that will allow users to comfortably perform their work functions, but at the same time ensure the safety of the company's information assets.
An ideal set of protection should be:
- multi-platform - work on all popular desktop and mobile operating systems; This is especially important for companies with BYOD policies and the ability to work remotely.
- automatic - detect threats and respond to them without user intervention;
- intellectual - use not only traditional signature-based, but also behavioral analysis, ensuring the detection of both file and file-free malware;
- centrally managed - administrators should see the status of all protected devices in real time and be able to change security settings depending on the location of the device;
- provide integration with behavioral analysis systems and the ability to investigate incidents;
- Control applications on end devices to protect the corporate network from malicious programs and targeted attacks from devices on the organization’s network.
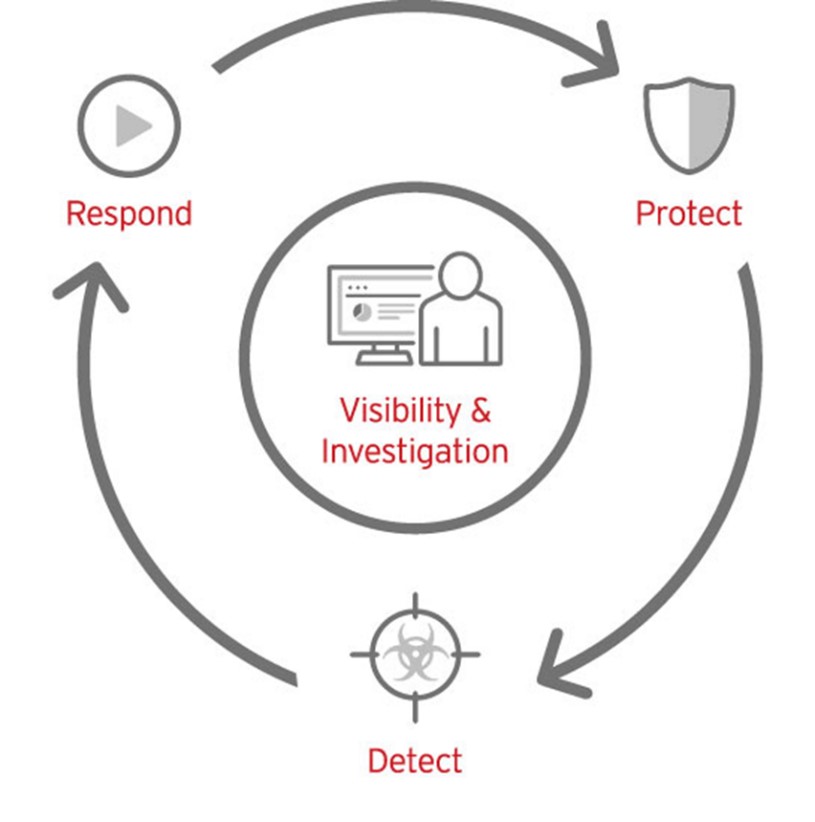
Traditional solutions of the EPP (Endpoint Protection Platform) class protect the user devices well from known threats, but they deal much worse with the latest types of attacks. They successfully cope with fixing incidents on separate devices, but, as a rule, they are not able to reveal that these incidents are fragments of a complex integrated attack, which in the future can cause serious damage to the organization. The capabilities of automatic incident analysis are almost absent. Therefore, companies have developed solutions of the class EDR (Endpoint Detection and Response).
How a modern EDR solution works
Let's look at how the endpoint protection solution works using the Trend Micro Apex One as an example. This product is a significant rebirth of the already well-known OfficeScan endpoint security solution.
One of the key features of Apex One is just multi-stage endpoint protection that does not allow malware to spread across the network, affect the performance of the computer and steal sensitive data. The solution instantly blocks zero-day threats on physical and virtual desktops, as well as laptops, both on the network and beyond.
What exactly does the Apex One do?
- Protects against advanced threats:
- prevents the possibility of using known and unknown vulnerabilities to penetrate systems before the release of fix packs;
- Protects unsupported and legacy operating systems for which fix packs are no longer available.
- automatically evaluates risks and recommends the activation of virtual patches required for each individual device;
- dynamically changes security settings depending on the location of the device;
- Protects end devices with minimal impact on network bandwidth, user productivity and productivity.
- Blocks invalid types of network traffic:
- applies filters to notify about certain types of traffic and block it, for example, instant messages and video streaming;
- uses in-depth packet inspection to identify traffic that could be harmful to applications;
- filters out prohibited network traffic and checks allowed traffic by monitoring the status of connections;
- detects malicious traffic that is hidden by using well-known protocols on non-standard ports;
- prevents backdoors from entering the corporate network.
- Makes protection timely:
- provides protection until the release and installation of official fix packs;
- Protects operating systems and typical applications from known and unknown attacks.
- Facilitates deployment and management in existing infrastructure:
- a simplified control panel makes it convenient to conduct detailed control and monitoring of the environment, in the context of each individual user.
- vulnerability assessments are based on Microsoft security bulletins, CVE data, and other sources.
And now we’ll tell (and show) how it works.
All information about the status of endpoints and threats is collected in a single Apex Central panel. Analysts get the opportunity to monitor in detail, in the context of each individual user, and manage policies. A single panel allows you to control local, cloud and hybrid environments. It also provides access to operational information from the local “sandbox” or from the Trend Micro Smart Protection Network infrastructure, which uses cloud-based threat data from around the world and provides real-time information security by blocking threats before they reach computers.
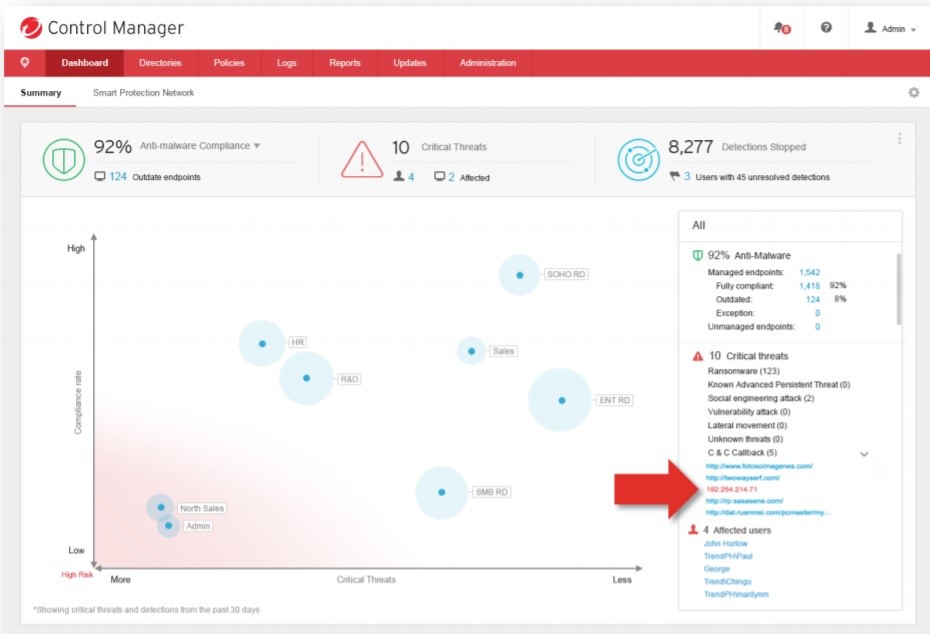
A single panel allows you to not switch between control panels. Here you can see how integrated detection and reaction are reflected in a single manager. It also provides unified integration with EDR investigations, automated detection and response to threats.
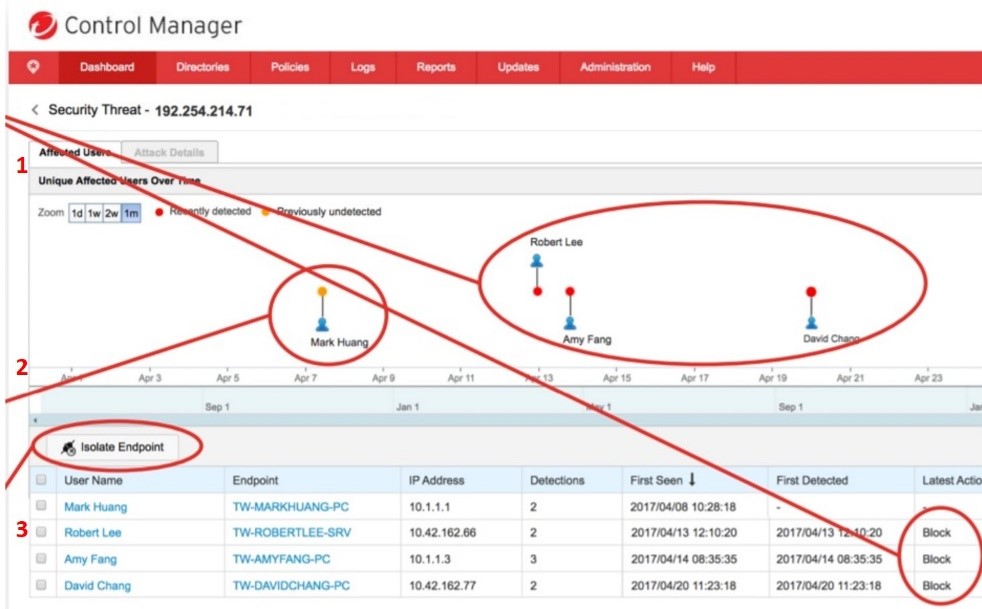
Impact Scale Analysis:
- Malicious IP blocked because it has already been detected (red) (1)
- "Zero patient." Not known (orange) and was not blocked (2)
- The “zero patient” is isolated and the search for the root cause begins (3)
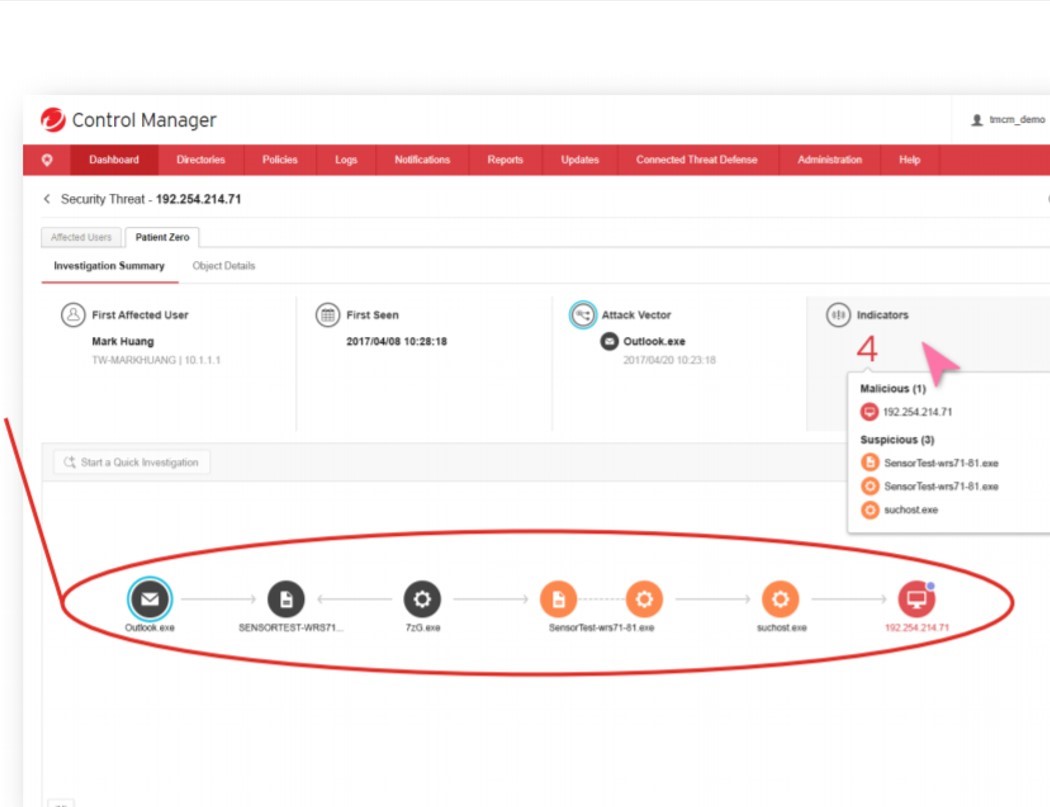
Search for the root cause using global Trend Micro threat information:
- Red (“bad”);
- Orange (“suspicious”);
- Black ("satisfactory")
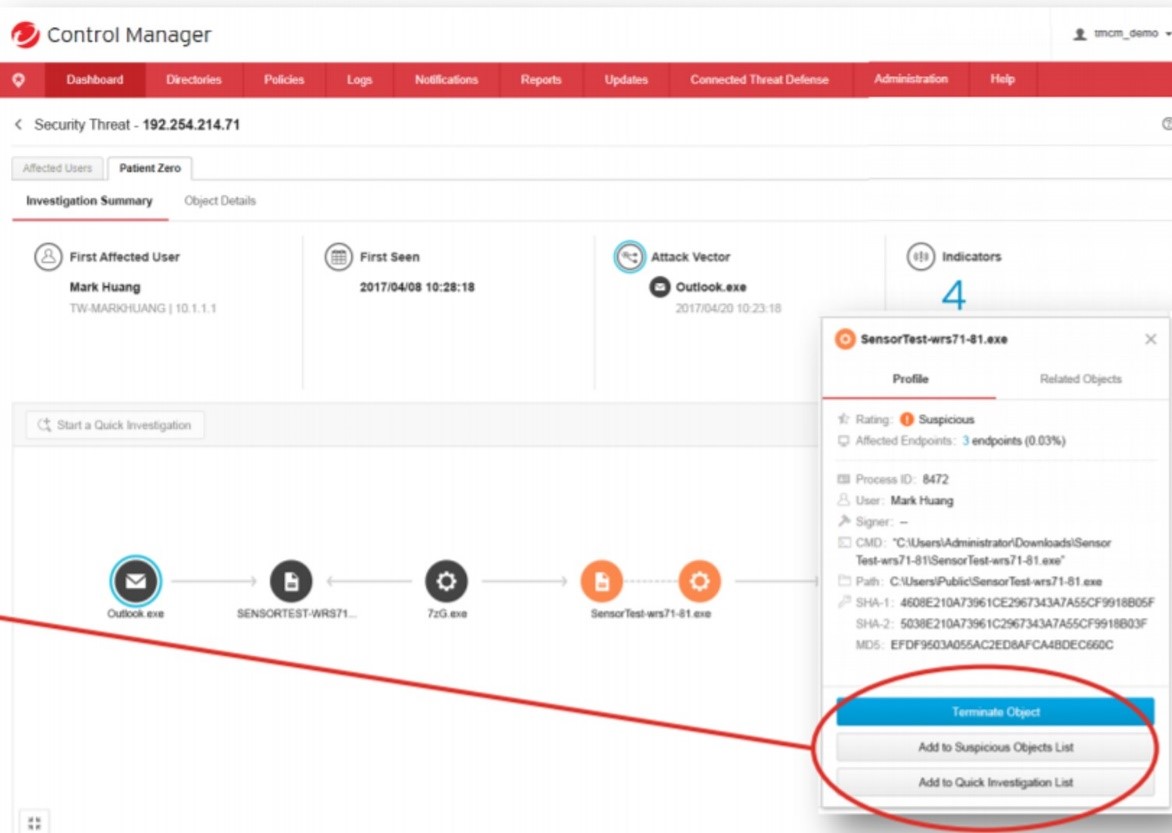
There are reaction options:
-stop execution;
-Distribute threat information;
- Perform an investigation of the
Endpoint Sensor from the Apex One package monitors the security status on the end device, taking into account the context, logs actions at the system level and generates reports for security guards,so that you can quickly assess the scale of the attack on the network. Including Endpoint Sensor monitors advanced threats, such as the notorious file-free attacks. Using EDR, you can perform a multi-level malware search on all end devices using criteria such as OpenIOC, Yara and suspicious objects. Also provides protection against fileless attacks.
Even if the malware has penetrated server-side scanning systems, Trend Micro User Protection technology will examine the executable file before it is run using machine learning. When you start, the analysis of behavior based on machine learning begins. Then the analysis in the “sandbox” is used - according to the results of the checks, the application either starts its work or is blocked. Moreover, for security purposes, the entire computer may automatically be blocked on the network in order to localize the malware and prevent it from penetrating the network.
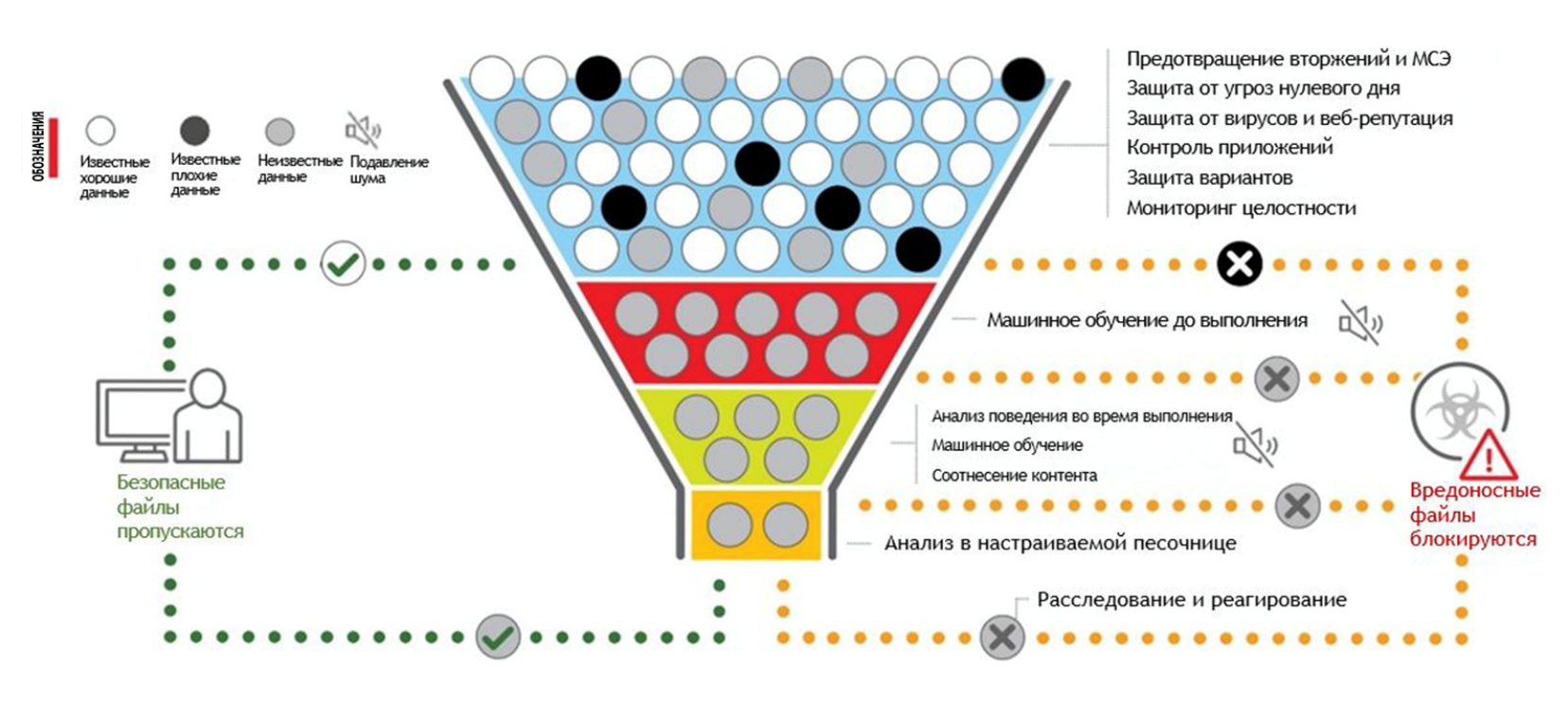
Apex One uses Trend Micro Vulnerability Protection technology, which protects all network end devices from exploits even if they do not have patched updates. To do this, Apex One centrally analyzes traffic for exploits / vulnerabilities, service attacks, web malware and illegal traffic. At the same time, scanning takes place at high speed, the work of Apex One practically does not affect the speed of the network itself.
How leakage protection is provided
Another useful module in Apex One is Data Loss Prevention. It monitors and controls the transfer of content over all possible communication channels to prevent data leakage. You can log or restrict the use of USB sticks, CD / DVDs, exotic IR transmitters, PCMCIA devices, modems, cloud storage, and mail servers. Data forwarding is controlled both when working with the mail client, and through the web-based mail interface, in instant messengers and in most network protocols such as HTTP / HTTPS, FTP and SMTP.
Data Loss Protection has templates for recognizing more than three hundred file types, including in archives, and the rest of the data types are determined by specific templates, formulas and location. You can also create a data identifier yourself.
And finally, protection from the “smartest” controls the clipboard, the paste from it and the generated screenshots. After correctly setting up Data Loss Protection, the likelihood that valuable data will be removed from the company is significantly reduced.
Bonus: MDR - Subscription Security Service
In the current environment, maintaining a large information security team is becoming a luxury. At the same time, it is extremely important to correctly assess the damage caused by a cyber attack, to formulate an action plan to eliminate the threat and prevent repeated attacks - the employees remaining after the “optimization” are unlikely to find time for such investigations.
Trend Micro Managed Detection and Response comes to the rescue, the Apex One threat detection and response management service. MDR is a remote team of Trend Micro professionals who can monitor security on a customer’s network around the clock. This is an excellent solution for those companies that do not have the ability to maintain a large staff of security personnel or lack a staff of high competence.
The MDR service monitors logs to identify critical notifications, examines them, and reports threat information to the customer. Using the data from the endpoints, the MDR team will detect the root causes and attack vector, as well as evaluate its consequences. The customer can always ask questions to a team of experts to get clarifications and explanations. MDR will draw up a detailed plan of action for recovering from an attack.
The subscription includes tracking both endpoints and the network, servers, even printers and the Internet of things.
In fact, Trend Micro MDR does everything that professionally equipped information security departments do. But remotely, around the clock and by subscription.
