History of one NOT vulnerability
Some time ago, I was given the opportunity to experiment with the settings of one ordinary router. The fact is that the first of April obliged me to play my comrades from the university. The university had a Wi-Fi network. I decided to raise a fake network on my router (set a name, password and set the MAC address of one of the legitimate access points), start my own DNS, web server on the laptop. Everyone who accidentally connected to my network and tried to access any site should be redirected to my page with an April Fools picture. But the story is not about that. When I was poking around in the settings of the router, I found an interesting bug, I’ll tell you about it today.
At the setup stage, the router was connected to the Internet. But for some reason, devices connected to Wi-Fi did not receive Internet. I got to understand. There was a tab in the panel of the router with the ability to use the ping utility, so telnet can not be turned on (I hope all readers understand the danger of telnet open to the outside?). The form looked like this:
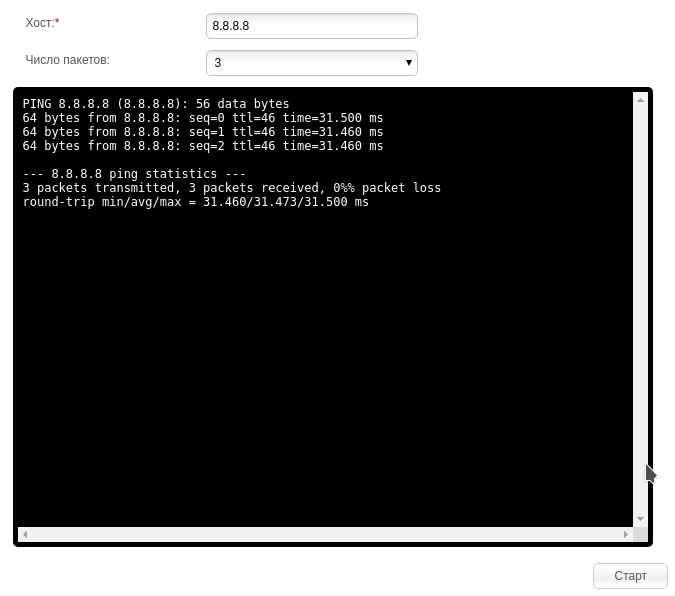
This feature is implemented as follows. The router program receives from the user a string containing the address, then substitutes the ping command into the call string:
How well does the router check the string containing the address? It was this question that arose in my head. Then I substituted the ampersand and the ls command . I got this:
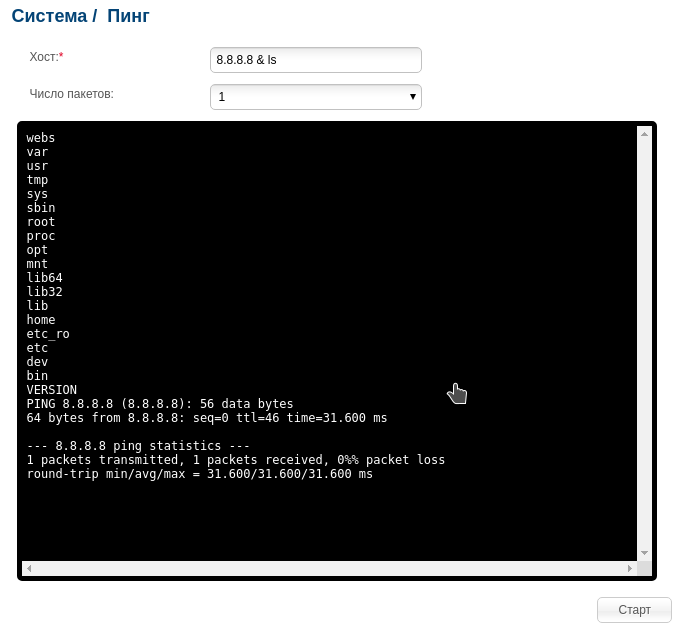
On UNIX systems, we can force bash to execute a command in the background, substituting an ampersand after it. At the same time, we can substitute a command after the ampersand, and it will be executed simultaneously with the first. What I used in this case. Substituting "8.8.8.8 & ls", I got "ping -c 3 8.8.8.8 & ls". The router executed the ping and ls commands simultaneously. Then brought the result.
If this bug was allowed elsewhere, it would become a very serious threat. After all, such a vulnerability would help an attacker force the router to execute any command, or even gain complete control over the device. Such vulnerabilities are classified as CWE-78 (OS Command Injection) .
I did not sit still, and I hastened to write to the manufacturer about the bug found. I described in detail the model of the router, the firmware version and the script for playing the bug. To which I received an interesting answer:


At the setup stage, the router was connected to the Internet. But for some reason, devices connected to Wi-Fi did not receive Internet. I got to understand. There was a tab in the panel of the router with the ability to use the ping utility, so telnet can not be turned on (I hope all readers understand the danger of telnet open to the outside?). The form looked like this:

This feature is implemented as follows. The router program receives from the user a string containing the address, then substitutes the ping command into the call string:
ping -c <число пакетов> <хост>
How well does the router check the string containing the address? It was this question that arose in my head. Then I substituted the ampersand and the ls command . I got this:

For those in the tank
On UNIX systems, we can force bash to execute a command in the background, substituting an ampersand after it. At the same time, we can substitute a command after the ampersand, and it will be executed simultaneously with the first. What I used in this case. Substituting "8.8.8.8 & ls", I got "ping -c 3 8.8.8.8 & ls". The router executed the ping and ls commands simultaneously. Then brought the result.
If this bug was allowed elsewhere, it would become a very serious threat. After all, such a vulnerability would help an attacker force the router to execute any command, or even gain complete control over the device. Such vulnerabilities are classified as CWE-78 (OS Command Injection) .
I did not sit still, and I hastened to write to the manufacturer about the bug found. I described in detail the model of the router, the firmware version and the script for playing the bug. To which I received an interesting answer:

Translation (verbatim)As it turned out, they did not take into account what I was writing from Russia. This model of the router was distributed only in our country. The correspondence ended with a new firmware being sent to me, which eliminated all the shortcomings of the previous one and added a lot of features, but for some reason it was not in the public domain.
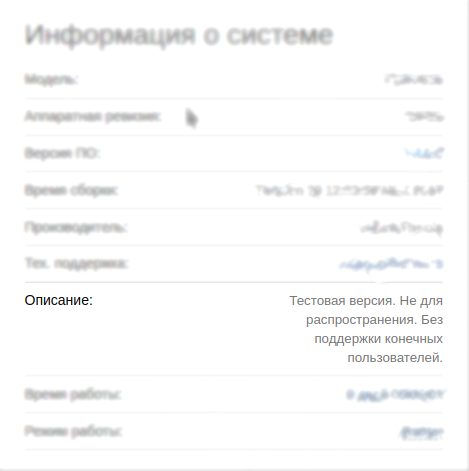
Could you check the hardware version on the bottom label of the product?
We do not have Rev. Px. Do you know the source or place of purchase of this device?

